
At the low chance that you were considering attending the Beijing 2022 Olympics, you may want to reconsider. The reason: MY2022.
What is MY2022?
MY2022 is a smartphone application that is mandatory to use for all attendees of the Beijing 2022 Olympics, including press members, government agents, and athletes. While there currently does not exist proof that the application was designed for malicious purposes, it at the very least has major internal security flaws that can easily be exploited by adversaries.
The research laboratory “Citizen Lab” has done research on this application and, upon multiple discoveries, have pinpointed two major vulnerabilities.[3] This research was published on January 18th 2022. The result of these vulnerabilities could be potential data leakage of users of the app and spoofing of actual data transmitted through the application’s servers. Citizen Lab has even speculated that these vulnerabilities could have been purposely placed, as an act of surveillance by the Chinese government.
The Vulnerabilities
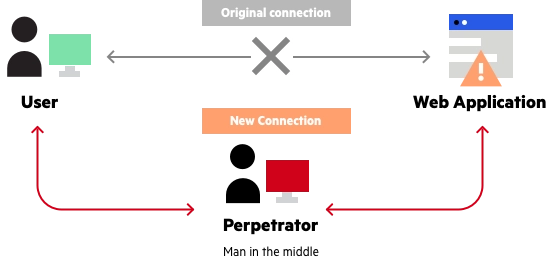
The main vulnerabilities are related to how MY2022 transmits user data. Applications will commonly use SSL, which is used to encrypt and digitally sign data to prevent data from being modified or read when being transmitted between client and server. However, MY2022 does not validate SSL certificates, and thus cannot know if it is sending data to the correct client or server.[3] This is a concern considering such data could include sensitive information which could be read by an attacker, or data sent from the app could be intercepted and modified by an attacker. One way an attacker can exploit this is by “spoofing” a trusted server of the application, which will allow them to be able to send fake information to clients. At the very least, Citizen Lab found five vulnerable SSL connections that could be exploited on the app:
my2022.beijing2022.cntmail.beijing2022.cndongaoserver.beijing2022.cnapp.bcia.com.cnhealth.customsapp.com
Citizen Lab notes in particular that, by spoofing the SSL certificate for health.customapp.com, an adversary could be able to acquire travel, passport, or medical information of victims.[3] Spoofing other servers could also allow for an adversary to read voice audio or file attachments of the victims. Furthermore, some sensitive data on the app is not encrypted at all when transmitted, and an eavesdropper could intercept such data in it’s plaintext form.[3]
The Aftermath?
While the data for this was disclosed to the Beijing Organizing Committee by December 3, 2021, Citizen Lab has not received a response as of January 18 2022.[3] The application has been recently updated on the Apple App Store, however this update has not fixed any of the vulnerabilities that were reported.[3]
As a word of caution, note that the same vulnerabilities in MY2022 are still possible for any application you install on your smartphone that involves connecting to a server. Since these application are closed-source, we cannot confirm that certain vulnerabilities such as non-existent encryption are not present. Unfortunately, since we cannot be sure as to how these sorts of applications operate at the micro level, the main advice I can give is be extra careful of what you install on your phone. If these sort of privacy vulnerabilities are shocking for you, I would recommend looking into how to root your smartphone to be able to take more control over it by being able to uninstall proprietary software and disable intrusive services.
References
[1] “MY2022.” App Store, 22 Mar. 2021, https://apps.apple.com/nz/app/my2022/id1548453616.
[2] “Figure 1: MY2022’s Splash Screen and Basic UI.” The Citizen Lab, https://citizenlab.ca/wp-content/uploads/2022/01/image3.png.
[3] Knockel, Jeffrey. “Cross-Country Exposure: Analysis of the MY2022 Olympics App.” The Citizen Lab, 18 Jan. 2022, https://citizenlab.ca/2022/01/cross-country-exposure-analysis-my2022-olympics-app/.
[4] “Man in the Middle Attack Example.” Imperva, https://www.imperva.com/learn/application-security/man-in-the-middle-attack-mitm/.

Wow, interesting article! It intrigues me that over a month later non of these security issues that you talk about have been fixed… In my opinion that seems to give more weight to the theory that they were put there on purpose.
Interesting article! I find it intriguing that over a month later, the security issues you talk about have not been resolved. This seems to give more credibility to the theory that these vulnerabilities were purposely placed in the app…
Hi Benjamin,
Very interesting post! It was a little shocking to read that something as big as the Olympics does not have a secure application for their athletes and that the application can indeed leak confidential information of the users of the app. I think this post goes to show that you should be mindful about the information you provide to an application…
This is an interesting and informative post, thank you! I think this event really just enforces the point that we really can’t fully ensure the security of our private information nowadays. You would expect (or trust) that an event of this size would have developed a secure app for users to use but unfortunately, this isn’t the case, which is a scary thought.
It’s intriguing to see poorly designed software being used in such a large event, yet personally I don’t find it surprising after seeing many organizations contract out jobs like these to the lowest bidder. I’m trying to give them the benefit of the doubt that these vulnerabilities weren’t intentional as I feel like if the Chinese government truly wanted to steal sensitive data they could probably access it from the servers. Regardless of the maliciousness, these vulnerabilities are still very large issues and hopefully they’ll get patched soon.
Hi Benjamin,
First of all, amazing post! You articulated the context and problem with MY2022 very well, especially with the pictures which I found very helpful. I agree with you and some of the people that have already replied below where this weak security with some of their SSL connections could be viewed as intentional on the part of the Chinese government. For me, it would not be surprising that they would “not account” for a vulnerability such as that. As if I did not have enough reasons to boycott this year’s Olympics. This post gave great insight on being mindful on what apps we download and I will for sure be wary of these kinds of vulnerabilities and more going forward.
Hi Ben! Thanks for the post, I liked the way you styled the post 🙂 Its such a shame to see app developers not improve on their vulnerabilities, especially with such sensitive things like someone’s data. Its a huge breach of privacy, and for an event so large I expected better from them.
Nice post!
I definitely agree with the prospect that these vulnerabilities were put here for a reason, because by not responding to the research done by Citizen Lab, I think that suggests that they don’t want the issues to be fixed. Further, these are all vulnerabilities that relate to listening in or intercepting SSL channels, and seeing that they all share that in common, it seems a bit too systematic for the same types of mistakes to happen multiple times.
Beyond the potential for purposefully placed surveillance, I think this article brings up an interesting topic about the security of phone apps in general. People complain a lot about Apple’s restrictive app store policy, but while it may contribute to anti-competitive digital practices, this type of vetting is the only way to ensure that the risk of predatory applications are minimized. Jail breaking devices, or otherwise getting unvetted apps on a phone, represents a significant security risk for this reason. What’s particularly bad about this app is, as you brought up, its officially approved and worse, mandated for use.
That being said, if you’re going to avoid the Olympics specifically for data protection, there’s more you could do. At the end of the day, given the amount of security risks one is exposed to through your phone, its probably best to avoid keeping super important information on it anyway, or using important services like banking. While convenient, other methods of securing information (safes, notebooks) put you at a much lower risk of destructive cyberattacks in general.
It’s strange to think even after the reports and lack of change in the update the app is still available for download. I guess I thought there was some kind of security requirement for apps to be on the app store but I suppose that would cause quite a process. Will definitely be more cautious downloading apps in the future!