Recently, security researchers from IBM have found out that TrickBot has implemented new improvements and defenses once again. To provide context, TrickBot is a Trojan that is capable of delivering malicious malware. It was originally created as a banking Trojan back in 2016 with the sole goal of stealing banking information.[1] Ever since then, TrickBot has continued to grow into a multi-purpose malware delivery service as well as collaborating with other malware developers to further extend their influence. As of December 2021, TrickBot was able to infect around 140,000 victims across 149 countries[1].
What are Trojans in general?

The term Trojan is derived from the story of Troy and for good reason. Essentially, a Trojan is designed to trick the user (YOU!) into downloading malware or viruses through deceiving cyber practices. These practices can include:[4]
- Downloading infected files which are made to look tempting or safe
- Visiting shady and unsecure websites
- Opening infected email attachments which can look important or legitimate
TrickBot is exactly this (as its name implies) and is one of many Trojans out there. What makes it a concerning threat, however, is its ability to adapt and bypass new security techniques which can be a threat to TrickBot itself. In other words, TrickBot is constantly evolving.[1]
So what are these improvements/defenses?
The new improvements/defenses of TrickBot were mainly created to prevent any further analysis of TrickBot’s code. This was done in an effort to hinder security researchers from figuring out how (or at least making it more difficult) to stop any future TrickBot attacks.
The improvement TrickBot adds involves injections. For those who don’t know, injections are a certain type of attack which is done by injecting code onto a computer or program. This would allow the attacker to execute remote commands in order to access or modify data.[5] These injections can either be fetched locally on the infected machine or from the attacker’s injection server (server-side injections). TrickBot uses server-side injections as local injections can be a risk since they need to be kept within the machine itself. Therefore, it’s more likely that the injection can be recovered and used for analysis by security researchers. With server-side injections, however, TrickBot can avoid this risk by implanting a downloader onto the machine. This downloader is then able to use encrypted communications (using HTTPS protocol) with the attacker’s command and control (C2) server in order to inject the malware at the right moment.[3] As a result, security researchers will not be able to retrieve the injection.
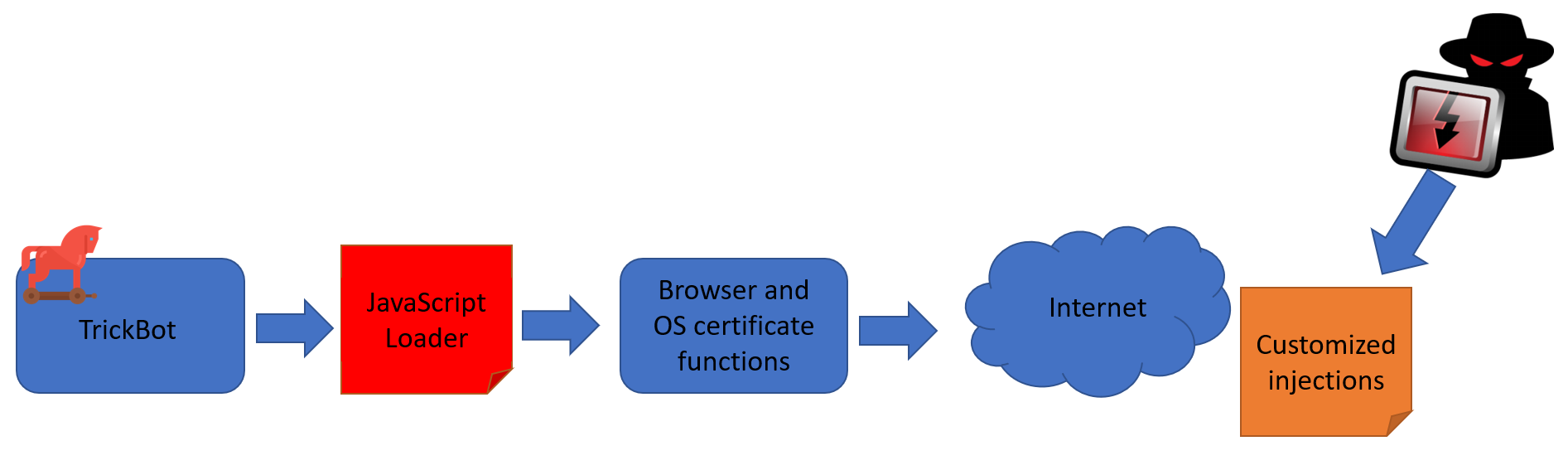
However, if there was a case that security researchers would somehow still get a hand on the injection code, TrickBot would make the analysis difficult or even prevent it from happening.[3] This is the intention of TrickBot’s new anti-debugging tool which was designed to prevent any attempts in “beautifying” the injected code. But why is there a need to “beautify” the code? Well, it’s because TrickBot deliberately made its code to be messy. This would essentially force security researchers to “beautify” it so they can actually do some analysis. But with the anti-debug tool, this became much more difficult as any attempt in “beautifying” the code would result in a browser crash.[2]
“TrickBot uses a RegEx to detect the beautified setup and throw itself into a loop that increases the dynamic array size on every iteration. After a few rounds, memory is eventually overloaded, and the browser crashes.”
– IBM security researchers[3]
How do you prevent these attacks?
TrickBot (or Trojans in general) and its capabilities can be a scary thought but this doesn’t mean they aren’t preventable. In fact, most of these infections are usually caused by the user themselves (through trickery) as mentioned earlier[4]. So, I’ll add some of my suggestions and recommendations from other sources in order to better protect yourself[3][4]:
- Enable 2-factor authentication (2FA) or multi-factor authentication (MFA) whenever possible
- Use strong and unique passwords for all your accounts. I recommend using password managers like Bitwarden
- Run periodic diagnostic scans
- Avoid suspicious websites
- Have offline backups and a backup schedule
- Be wary of suspicious links and attachments in emails or online
- Keep your systems updated to ensure any security vulnerabilities are patched
References:
- https://thehackernews.com/2022/01/trickbot-malware-using-new-techniques.html
- https://threatpost.com/trickbot-crash-security-researchers-browsers/178046/
- https://securityintelligence.com/posts/trickbot-bolsters-layered-defenses-prevent-injection/
- https://www.malwarebytes.com/trojan
- https://www.ibm.com/docs/en/snips/4.6.0?topic=categories-injection-attacks
- https://www.eset.com/fileadmin/ESET/INT/Pages/Features_pages/trojan-horse.png

Wow, what an interesting topic. Before reading this blog, I had never heard of Trickbot but now I know a lot of information about it. I just find it so surprising that there are hackers out there that will go to such lengths and put so much effort into more and more of these scams and tricks. Trickbot seems like it is really dangerous, mainly because it seems so easy to fall for. The fact that it has been able to fool 140,000 people just goes to show how effective this trick is. As I learn more about these types of hacks and scams, I realize that we have a duty to consider. That duty is to make sure we take the necessary steps of caution to protect ourselves from these types of scams. Seeing how these types of tricks and scams keep evolving, it is also up to our computer-gifted individuals such as cyber security workers, to step up and adapt to these new challenges. Hopefully, more people are able to learn about this and not fall victim to Trickbot or other Trojans.
Great topic , i enjoyed learning about ” trick-bot ” again, and how it is evolving , i find that with the technology development nowadays, people really should keep in mind that there are hackers out there trying their best to get ( your) information . Also i would like to point that the last paragraph ” How do you prevent these attacks?” was critical in your post , since we are all looking to protect our information .
Great job !
Super interesting article! Its fascinating to read about the “tug-of-war” between new developments in malware vs in security, even if its a bit disconcerting. I had heard of the term “trojan” before, but I was unfamiliar with how they worked; reading about TrickBot’s use of both local and server-side injections was very informative. I also found it interesting how the article was able to articulate exactly what had been recently updated in TrickBot. The trojan had been improved, to be sure, however I found it impressive how security experts were so quickly able to identify how and where it had been improved, even if security measures are still being worked on to deal with it.
This was a very interesting read! Your suggestions help a lot with understanding how to avoid being affected by a trojan virus. Your post has made me more weary about the types of links I click and to make sure to double check my emails before doing anything that may harm my PC and my info. It is very interesting to see that it originally started off as a banking virus but is now being adapted to do other stuff as well. It is also great to see from a security stand point that there are people actively trying to counteract viruses like these, as they recognize the harm it does to a lot of people. It sucks that there are people that are making it more and more difficult for us to counter viruses, but posts like these keep us informed so we can tighten up our own security and avoid malicious outcomes.
An excellent article explaining the strengths and weaknesses of a trojan attack. This post properly demonstrates how these attacks are formed and generally how manipulative they tend to be. Trojans as stated in this post are mainly only effective when the users it is targeting falls for its “Tricks”. These attacks and malwares very often find themselves on several computers and are often left undetected until it is too late. Additionally, because these attacks are simple in nature, the counter measures set in order to combat this is also fairly simple just by being aware of suspicious website and practice normal security procedures such as unique passwords and 2FA.
What an interesting post to read.
This is the first time I am reading about the TrickBots, it was definitely worth a read. I really like how your post covered everything, starting from its history to the latest updates. We don’t realize how easily one can be tricked. The last part of your post, in which you presented ways to prevent these attacks, was very much required.
Good work!
This was an interesting read!! I’ve never heard of trickbot before this, and it’s crazy how widespread it is, and how detailed it is. I didn’t know about the term “Trojan” to describe malware, however I did know about the story of the Trojan horse, and I’ve seen multiple hacking situations where they try to make it look normal, such as the common instagram one (when they say “I made this for you” and give you a link). It is quite scary that they made an anti-debug feature, that can ruin your electronics simply by trying to combat the malware. It is also unsettling how IBM is having to continuously monitor changes due to how adaptive Trickbot is proving to be at evading security (from a biological perspective, this does somewhat remind me of COVID).
Great post! I have never heard of Trojan before and was amazed of how they named it lol. Besides, the fact of making the codes messy to make it harder to analyze surprised me. Whoever created these TrickBot is a genius, so is the IBM researcher. He had done a great job in figuring out its tactics.
I find trojan viruses to be very very scary! I think it’s always a computer owner’s biggest fear is to have a trojan virus on their computer that can’t be found or removed. I do find it quite reassuring to know that most of the time the more dangerous viruses are ones that are downloaded by the user themselves when trying to access things in sketchy places on the internet!
Great blog! I have heard about the Trojans for many time since my childhood. But this is the first time I actually have a systematic understanding about this type of malware. The method that TrickBot used to make a browser crashed is quite tricky. Seems like hacker always works on loop to make device overload. It is nice to see there are some tips we can use to prevent this attack.
Hi Jayden this is a great blog. While searching for hacking, I often see Trojans on the list, but I never go into detail about them. I am amazed how it works and how the hacker intentionally makes the code “messy” and uses server-side injection to prevent security analysts from retrieving the QuickBot code. It is scary since we can’t fully retrieve the code to analyse, but gladly most of the attacks are effective only if the user is tricked into downloading the Trojan. We can raise community awareness to prevent potential Trojan attacks.
Thank you for your interesting post. It has been informative to learn how one of the most common hacking methods works, as I had never paid much attention to cyber security before enrolled CPSC 329. Occasionally, I see messages and emails with strange attachments that I consider scams, but I’ve never fully understood how clicking on the link can allow someone to hack into my device. Like me, there are likely other users of the Internet who do not know they can be targeted by malicious intentions. This is a great advantage for the hacker to exploit and we need to educate people for prevention
This is a very good post. I remember I was 6 years old when I first heard about the Trojan virus and I didn’t realize that after all these years, the Trojan virus is still spreading like crazy on the internet. As the post says, most of the viruses are downloaded by the users themselves. And nowadays firewalls I think are prompted after downloading a suspicious file to let the user delete that suspicious file. This then means that most computer infections are actually hardly caused by the user accidentally clicking on the download button to get infected. Having said that, I think everyone thinks about it when they download and install the software, do you really trust the software?
Thank you for sharing this topic. While the defense measures of technicians are being upgraded, the Trojan virus is also constantly being upgraded. I guess the only thing we can do is be careful. Try to log in to trusted websites and do not open strange websites and emails.
I have only heard of the trojans before but never got a chance to dig into it. After reading this article, this made me realize how Trojans are deceptive and harmful. One of the ways that prevents downloading trojan is we should download software from the trust website. We should increase network security awareness to prevent potential Trojan attacks.