Anyone who keeps up to date with technology is likely very familiar with software updates. Generally speaking, updates are considered good things, delivering new features, fixing glitches, optimizing how a program runs, or closing security exploits. It follows of course that malicious software also receives updates, although coverage of those is more sparse, partially due to disinterest, but mostly due to the fact that those who maintain malware don’t try to publicize their changes. This blog post will cover recently discovered updates to KONNI.

What is KONNI?
KONNI is a remote administration tool (RAT) that has been linked to North Korean hackers and has been used for at least 8 years. RATs are often used to grant a technician access to a device remotely to facilitate troubleshooting, as they allow for remote control of another device. Unfortunately, they are also commonly exploited and used as ransom or spyware. Analysis of KONNI attacks over the years has led to the belief that KONNI is intended as spyware, specifically targeting government agencies. KONNI is a trojan, meaning it is generally disguised as a legitimate file, with known examples being screensavers and office documents. When the file is opened, multiple steps are executed to grant privileges, evade detection, and initialize needed files. The goal of the attack is to install Konni RAT, a .dll file supported by a .ini file.
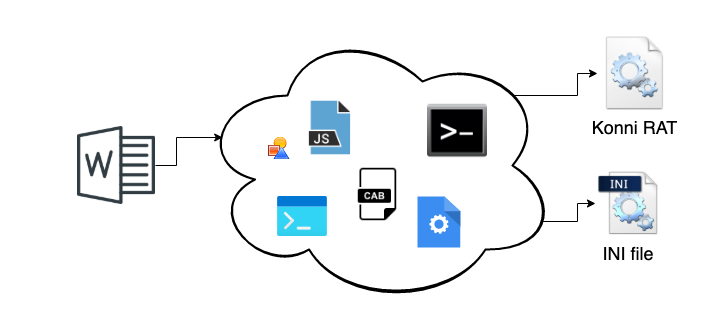
Why is KONNI still relevant?
As mentioned, KONNI has been around for over 8 years, more than enough time for the exploits it uses to be patched, and for security software to learn to detect it. In spite of this, KONNI attacks remain a threat and have been discovered as recently as January 2022. Analysis of recent attacks has found that the current iteration of KONNI being used in attacks has significant differences from previous ones. This is not the first time updates to KONNI have been discovered, in August 2021, it was discovered that an attack that had taken place a month prior used a newer variant of KONNI. KONNI is clearly an actively supported piece of software that has to be monitored. Each update it receives seeks to make it more efficient at infiltrating, and harder to detect.
Improved Encryption
For the most part, KONNI’s functionality remains unchanged. One major change is how strings in KONNI’s files are encrypted. Previous iterations featured custom alphabets (frequently changed) encoded in Base64 to protect strings. The strings are now AES encrypted, and the service names they hold are the keys for decryption, so analyzing the code is complicated by the need for the service name as well. Files have also been AES encrypted.
As filenames are also generated according to timestamp, the keys are different with every request, as are the contents of the requests. This may allow malicious activity to fly under the radar.
Removal of RunDLL functionality
Prior versions of KONNI allowed for execution through the windows RunDLL file. This functionality has been completely removed, and attempting to use RunDLL to run KONNI will cause an exception to be thrown. In all recent attacks, KONNI Rat was launched by creating a windows service. The removal is thus partially to eliminate redundancy, but also has the benefit of potentially throwing off sandbox analysis of code samples.
Ramifications of Changes
These changes were not arbitrary choices, all of them were made to mitigate the chances of detection. Execution varying from what is produced in sandbox environments, stronger encryption that also covers crucial parts of the program, and dynamic requests all present a risk. Security software that may have previously detected KONNI may fail to detect the newest iteration, and if not, they must be wary of the next, as KONNI shows no signs of being abandoned.

This was an engaging post. I think the title is spot on. Even though advancements can be made in security, hackers can also improve their methods. This means that security will be an issue for an extremely long time, maybe forever. As advanced as our security systems may be, KONNI always has the potential to one up these systems. This puts pressure on security systems to continue to make progress, because if they slow down for too long, KONNI will continue to find flaws and ways to exploit them.
This is a very detailed analysis blog that covers Konni and some of the possible directions. Network security is really relevant to life, because for any organization, the security of information will be very important. Individuals, businesses, and even nations. Security-related software should provide more frequent updates to fix bugs in real time, countering increasingly powerful malware.
Very interesting topic. Now with the progress of science and technology safety has become very important. I like your post very much, it is very detailed. Cyber security and people’s lives are closely linked. While security software updates vulnerabilities to combat malware, people should also be more careful about their information online, beware of various phishing sites, ransomware and so on.