
What are Apple AirTags and How Do They Work?
Apple advertised the AirTags as a smart tracking device. It is an easy way to keep track of your belongings and help those who have misplaced or had their items stolen. These devices can be attached to your personal belongings, some of the most common options being important assets such as keys, luggage, and valuables. The AirTags are linked via Bluetooth signal, where its location can be actively tracked and detected by nearby Apple devices through the iOS app called Find My [2].
How Are AirTags Being Misused?
Rather than being used for their primary advertised function of locating personal goods, they are falling into the wrong hands and being exploited to stalk and track people, locate cars to steal, and conduct phishing attacks.
How are people figuring out that they are being tracked by an Apple AirTag? An individual would receive a phone notification stating that an unidentified AirTag is found moving with them and be informed that the location of the AirTag can be seen by the owner. Some people have found AirTags that they were unaware of attached to their belongings and cars without their acknowledgement or consent. The only way they discovered the device was through the phone notification informing them about it, and or a beeping noise alert from the AirTag if the phone notification goes unnoticed [3].
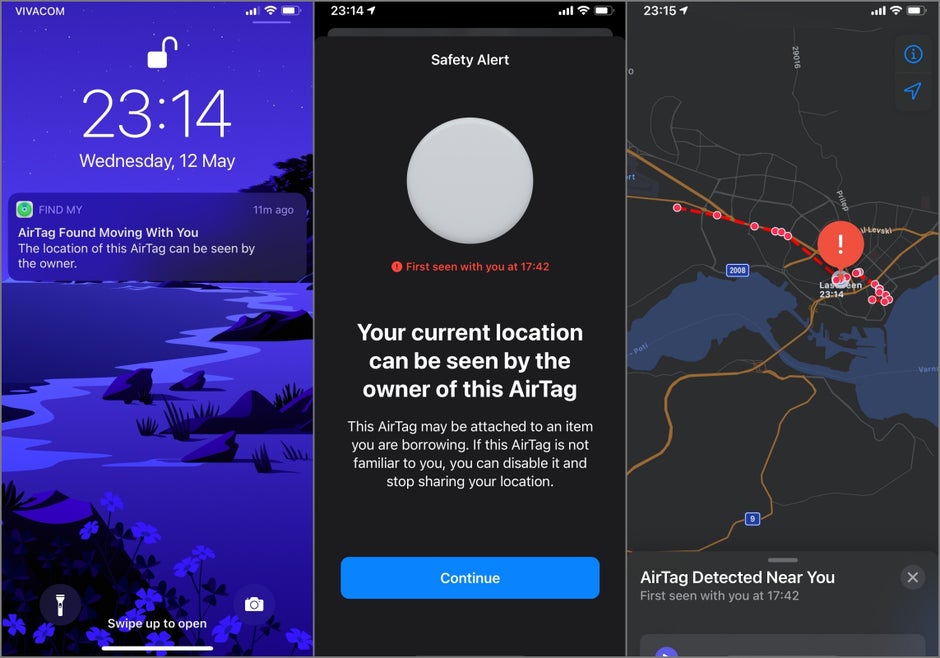
Another misuse in Apple AirTags is that hackers can modify them to perform malicious functions other than those originally intended [4]. Hackers can put AirTags into “Lost Mode” and inject a malicious URL into the contact phone number field, and intentionally drop the AirTag somewhere for an unsuspecting individual to pick it up and scan it. From there, the URL could direct users to a payload which distributes malware, phishing websites, or a site asking for credentials.
What Does This Mean for Cybersecurity and Privacy?
The misuse of these devices demonstrates that people’s cybersecurity and privacy can be easily compromised. These devices can be exploited to track and monitor people’s locations, which shows that the victims of these cases have had their personal privacy breached. Such as where they live, work, and frequent are all subject to monitoring without their permission, and this information can be used for various potentially dangerous means.
Regarding the hackers injecting malicious URLs into the contact number field in attempts of phishing, this puts the victim’s personal information and saved credentials at risk, and much more if the URL directs to a malware distribution.
How Is This Issue Being Address by Apple?
Apple claims that privacy is built-in and that the AirTags are designed to discourage unwanted tracking [2].
- Apple has created safeguards that would protect people from being tracked. Individuals with iPhones would be notified if an unregistered AirTag was moving with them. However, rather than the notification being immediate, it comes hours later [3].
- Another safeguard that was implemented if the phone notification went unnoticed was that people who had an unregistered AirTag moving with them would hear a beeping noise. A sound at 60 decibels [3], which could be easily muffled if hidden in an area that would make the sound difficult, if not impossible to hear.
- There could be individuals who are unaware they are being tracked if they do not own an iPhone, such as Android and non-Apple users. Apple has released an app for such users called, Tracker Detect [6], which allows users to be notified if they are being followed by AirTags, but only if the app is open. There are around 100k+ downloads [3], so only a small number of people are aware of the exploitation/misuse of AirTags. Hopefully, soon, Android and non-Apple systems will implement a feature to protect its users.
Furthermore, are these safeguards enough to protect people? What do you think Apple can do to ensure the safety of their customers?
What Can You Do to Protect Yourself from Being Tracked and Phished?
Here are a few ways [7]:
- Manually search yourself and check your belongings on a regular basis.
- Invest in a Bluetooth tracker especially if you own an Android or non-Apple device.
- Find the AirTag’s serial number: once you have located the AirTag, you can find the serial number underneath the battery. Removing the battery will make it so the owner cannot see your location. This information can be used if you end up needing to go to law enforcement.
- Disable the AirTag: Can be disabled by removing the battery.
- When scanning an AirTag, make sure the URL is the intended site.
- Call for help if you think you are in immediate danger.

Sources:
- “Apple AirTag Concept.” Twitter, Apple Tomorrow, twitter.com/AppleTomorrow2.
- “AirTag.” Apple (CA), www.apple.com/ca/airtag/.
- James Clayton & Jasmin Dyer. “Apple AirTags – ‘a Perfect Tool for Stalking’.” BBC News, BBC, 20 Jan. 2022, www.bbc.com/news/technology-60004257.
- Then, Ewdison. “Apple AirTag Lost Mode Bug Turns Helpers into Phishing Victims.” SlashGear, 29 Sept. 2021, www.slashgear.com/apple-airtag-lost-mode-bug-turns-helpers-into-phishing-victims-28693075/.
- Kateliev, Preslav. “Notification: AirTag Found Moving With You.” PhoneArena, www.phonearena.com/reviews/apple-airtags-review_id5072.
- Bonifacic, Igor. “Apple Releases Tracker Detect to Protect Android Users from AirTags Stalkers.” Engadget, 13 Dec. 2021, www.engadget.com/apple-detect-tracker-android-release-193850566.html.
- Rayome, Alison DeNisco. “Apple AirTags Can Be Used to Track You. How to Protect Yourself.” CNET, CNET, 31 Dec. 2021, www.cnet.com/tech/services-and-software/apple-airtags-can-be-used-to-track-you-how-to-protect-yourself/.
- “How to Find the Serial Number of an AirTag – Apple Support.” Apple, support.apple.com/en-us/HT211658.

It is frightening that how easy it is now days being hacked and lose you privacy and you don’t have any security. On the top of that big brands are competing with each other making devices and making it available for everyone which is not good for us and making hackers and scammers life easy to do their work without maintaining any privacy and security precaution.
I actually heard my friend talking about airtags and how they wanted to get some as well haha. It’s really interesting and scary how things that were made with the thought of improving daily life can be misused to stalk and track people. I wonder if companies like Apple think about how their products could be used in these ways before they launch. I also find it quite messed up how they only have iPhones that have the feature to detect if there is an unwanted airtag following the user and only give out a very poor app for android users, almost as if its a statement that only iPhone users can have protection.
Wow! Interesting read. It is great to know how the AirTags can be used for malicious activities instead of the good purpose it is designed for. I personally believe whenever we use a technology that is designed for performing good things, we must be aware that it can turn otherwise if it is passed on to a wrong hand. The choice of using AirTag should be a personal choice at the end of the day, but a little bit of concern and awareness should reduce the risk significantly. Additionally, the steps taken by the companies are laudable too.
This is so interesting considering I was about to buy an AirTag since its been used more frequently recently but I never thought they could have so many disadvantages and would steal our data. considering that apple is one of the companies which have higher sales every year and they come up with new products every year, I hope they are aware of their actions and how its affecting their users, I hope they realize this and provide more protection to their users.
Great Post!
I really never thought about how dangerous a device like this could be and how easy it is to be misused. This is a great post and it brings to light the dangers of tracking devices.
Great post! This could also play a part in human trafficking, which will only worsen that situation too 🙁
While yes, this is quite the issue, Apple is not the first ones to make such a product. This issue has been around for as long as trackers have been around and I do have to give apple some props for doing something, even if it is not enough. The fact that this has recently been popularized really shows that most of these issues have always existed, just that for anything to happen, they need to popularized.
Great post Jessica! As an AirTags user I find it convenient and helpful in my daily life but never thought someone could use it to stalk and track my every step. The notion of exploitation makes me uncomfortable. This makes me realize how advancement in technology compromises our privacy and safety. Although Apple has implemented safeguards to increase security, there is no guarantee they can’t be circumvented. Consequently, Apple and other tech companies need to be careful next time when developing and designing a product. I don’t think I can ever use AirTag the same way I used to.
Great Post!
I watched a recent Youtube video covering the same topic. It is actually scary how easy it is for these adversaries to plant an airtag into your belongings or in a nook of your car and follow you home. I feel like more work on Apples part needs to be done to help reduce the amount of misuse the apple airtags is getting. The points you made about how to protect ourselves from being tracked are really well thought of.
It was a great read!
It isn’t surprising to see that a product which was designed to make our life easier is being used for malicious activities. But what’s surprising is that the company, Apple, isn’t doing enough to prevent these malicious activities. Although Apple have addressed this issue, but I don’t think their efforts are up to the mark.
Thanks for an interesting post! I have been seeing so many cases where new products and services that were developed with good purpose are being misused and abused by people with malicious intent. After reading that the AirTags can also be used for several malicious activities, I realized Airtags also improved attackers’ convenience since they can easily track/hack innocent people without much knowledge. This post also highlights the importance of considering all case scenarios when developing and designing a product.
Very interesting topic. Many products designed to improve daily life are used for malicious activities such as mobile phones, drones and so on. It would be very scary for this product to be used by hackers or terrorists for malicious activities. The invention of AirTags brings convenience to people’s lives, while allowing hackers to take advantage of it. I think Apple should pay more attention to product security.