As we know technology has been increasing and there have been various advantages like you could save your information in security apps so next time when you open it ; it would be easily accessible and would save time and almost everybody would rely on their electronic gadgets by saving their bank information, personal data etc. These security apps have also made our life easier since we think it’s protecting our data. [1]

Microsoft’s MFA phishing attacks
Microsoft has recently uncovered a large-scale, multi-phase campaign that adds a novel technique to traditional phishing tactics by joining an attacker-operated device to an organization’s network to further propagate the campaign. We observed that the second stage of the campaign was successful against victims that did not implement multi factor authentication (MFA), an essential pillar of identity security. Without additional protective measures such as MFA, the attack takes advantage of the concept of bring-your-own-device (BYOD) via the ability to register a device using freshly stolen credentials.
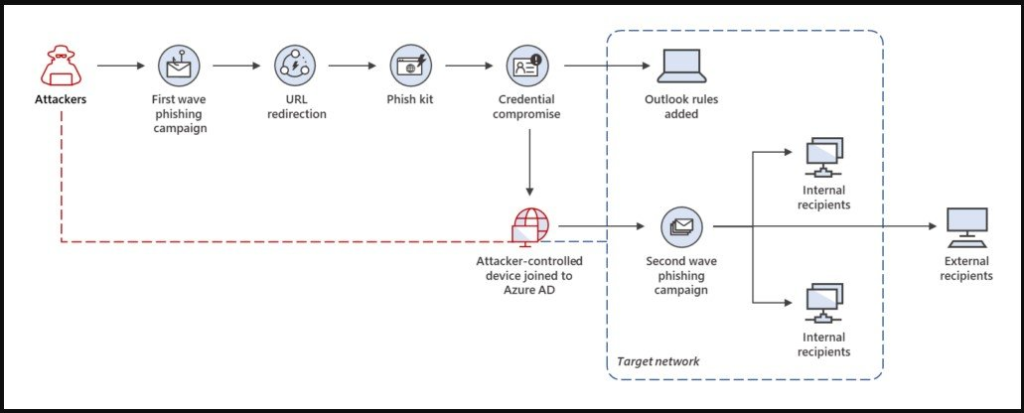
The attacks were carried out in two parts. “The first campaign phase involved stealing credentials in target organizations located predominantly in Australia, Singapore, Indonesia, and Thailand,” as stated by the Microsoft 365 Defender Threat Intelligence Team. “Stolen credentials were then leveraged in the second phase, in which attackers used compromised accounts to expand their foothold within the organization via lateral phishing as well as beyond the network via outbound spam.”
Users were sent a DocuSign-branded phishing bait with a link that, when clicked, took them to a fraudulent website impersonating the Office 365 login page, allowing the attackers to steal their credentials. The hack of over 100 mailboxes across several firms happened because of credential theft, allowing attackers to establish an inbox rule to avoid detection. The malicious messages were subsequently propagated by a second attack wave that leveraged the lack of MFA safeguards by enrolling an unmanaged Windows device in the company’s Azure Active Directory (AD) instance and exploiting the lack of MFA protections.
The unique approach allowed the attackers to expand their footing, secretly disseminate the attack, and move laterally throughout the targeted network by linking the attacker-controlled device to the network.[2]
How can we prevent phishing attacks?
Phishing continues to be the most dominant means for attacking enterprises to gain initial entry. This campaign shows that the continuous improvement of visibility and protections on managed devices has forced attackers to explore alternative avenues. The potential attack surface is further broadened by the increase in employees who work-from-home which shifts the boundaries between internal and external corporate networks. Attackers deploy various tactics to target organizational issues inherent with hybrid work, human error, and “shadow IT” or unmanaged apps, services, devices, and other infrastructure operating outside standard policies. In addition to enabling MFA, implementing best practices like strong credential hygiene and network segmentation might raise the ‘cost’ to attackers attempting to spread malware throughout the network. Microsoft explained that these best practices could limit an attacker’s ability to move laterally and compromise assets after an initial intrusion. They should be supplemented with advanced security solutions that provide visibility throughout domains and synchronize threat data across protection components.[3]
References:
- https://thehackernews.com/2022/01/hackers-using-device-registration-trick.html
- https://www.microsoft.com/security/blog/2022/01/26/evolved-phishing-device-registration-trick-adds-to-phishers-toolbox-for-victims-without-mfa/
- https://cyberintelmag.com/attacks-data-breaches/hackers-employing-device-registration-trick-to-launch-lateral-phishing-attacks-against-businesses/

Thanks for the tips on preventing phishing attacks!
Unfortunately, users often find MFA annoying as the additional steps in the process slow down workflow and are not always accessible. Some security experts recommend the implementation of adaptive multi-factor authentication, or aMFA, which triggers only when abnormalities are detected, such as a login attempt from a different country or a new device. MFA can be one of the strongest tools against cyberattacks, but the extra factors involved must be quick and effective for MFA to become more widely accepted.
Interesting post! This really shows how thought out some phishing attacks can be, but if users enabled something as simple as MFA, these attacks would not be a threat.