A prominent Italian art gallery has been in the center of a recent scam, as individuals associated with the gallery had been receiving emails with offers that seemed “too good to be true”—and indeed, it was.
An offer difficult to come by
T293, an art gallery based in Rome, Italy is well-known for housing some of the art world’s most prevalent and in-demand artists. One such artist—Anna Park, was the focus for a German art collector. He had made attempts over the past two to three years to buy Park’s work from the gallery with no success, stating that it was almost impossible to get ahold of.
However, after consistently keeping in contact with the art gallery, he received an email in early January from who he believed to be Marco Altavilla—one of the gallery’s co-founders with an offer for two of Park’s drawings. After several correspondences, the German art collector had finalized the deal, agreeing on a total price of $33,000, which he stated was a “very good primary market price”. It was only when the gallery had offered to pay the shipping—something that never happens, did the art collector realize that something was off. At this time however, it was too late—the money had already been sent out.
What the German art collector failed to recognize was that the email address which he had been in contact with was a fake—info@t292.it, one digit off from the gallery’s real address.
An art advisor’s fortunate realization
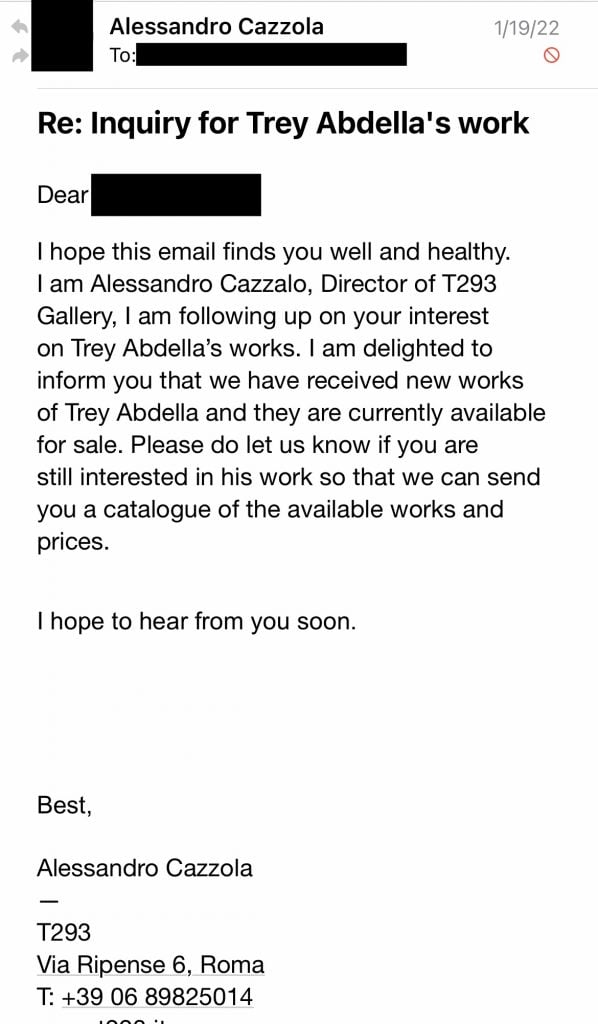
An art advisor from the U.S. was another individual contacted by the perpetrators. She had received an email claiming to be from T293’s director, Alessandro Cazzola. With the email came an offer of $28,500 with a 5 percent discount for three of the works of Trey Abdella—another artist represented by the gallery. “This is too good to be true, I thought, but I played it out” she said.
The art advisor hadn’t been in touch with the gallery since 2020, when she inquired about pieces from both Park and Abdella. The sudden offer had only fueled her suspicions, which were confirmed after looking over the details from an invoice.
The private account listed was not located in Rome, but was for a Wells Fargo account in Mills Valley, California. It was only then that she noticed that she was in contact with a “t292” email account, not “t293”.
In attempts to contact the actual art director, she scrolled back through her emails and messaged the proper address—requesting that Cazzola calls her as soon as possible. To her surprise she received an email shortly after from the person posing as Cazzola. She was informed by them that “t292” was a secondary email used alongside the “t293” address. From this she determined that her email had been intercepted by a hacker, preventing her from falling victim to the scam.
“Someone would have had to go deep into the email history to find out I had requested work,” she said. So, how exactly were the perpetrators able to compromise and intercept emails between T293 and their clients?
What is a Man-in-the-Middle attack?
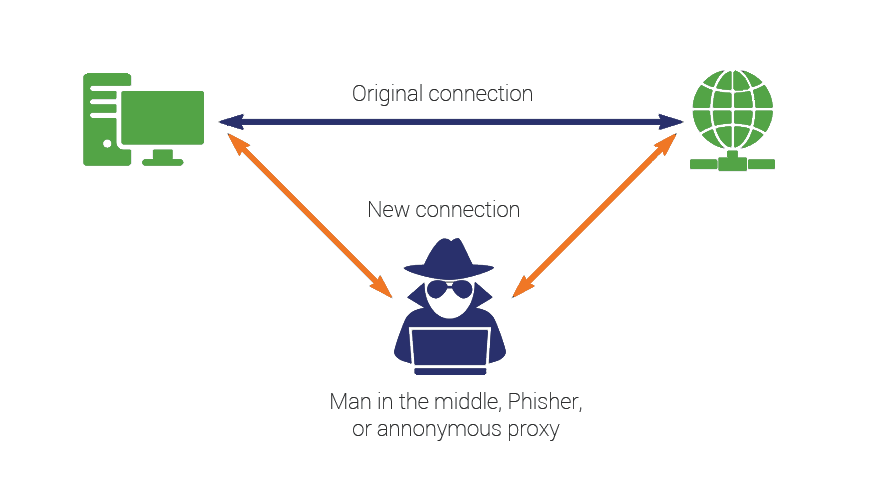
The art gallery and it’s customers were caught up in something known as a man-in-the-middle (MITM) attack—a type of session hijacking where attackers interrupt an existing conversation or data transfer. The perpetrator inserts themselves into the “middle” to either eavesdrop or impersonate one or both of the parties [3], thus, it grants the illusion that a normal exchange of information occurs.
In a sense, it is similar to if your mailman opens up your confidential mail and either writes down the information for himself or changes the contents of the mail, sealing it back then delivering it to you (very not cool of them). Of course, however, it is probably easier to tell whether or not a paper envelope has been tampered with compared to something online.
The appearance of a normal exchange of information often makes these attacks unnoticeable on the surface, which can result in the compromise of:
- personal information
- login credentials
- financial information
- etc.
In emails, this can take the form of malicious links or altered information being sent to either of the parties involved. With MITM attacks, unlike receiving emails with links or information from unknown senders (clearly very suspicious), both parties are under the impression that they are in contact with an individual or organization that they are familiar with. This makes it easy to go undetected until it is too late.
MITM Attack: Basics
MITM attacks have two distinct phases: interception and decryption
Interception:
- This phase involves intercepting user traffic through an attacker’s network before it reaches its intended destination [4]
- The easiest way this is done is through free, malicious wifi hotspots set up by an attacker—allowing attackers full visibility to any online exchange
- More active approaches include: IP spoofing, ARP spoofing, and DNS spoofing [4]
Decryption
- Following interception, two way SSL traffic needs to be decrypted without alerting the user or application
- Methods include: HTTPS spoofing, SSL BEAST (browser exploit against SSL/TLS), SSL hijacking, and SSL stripping [4]
Examples of MITM attacks

Intercepting data transfer between a client and a server:
- An example scenario may involve an attacker analyzing network traffic for unsecured communications
- Through this, an attacker can retrieve a user’s information and redirect them to a fake site that mimics the real one
- The attacker can then use information gathered (e.g., login credentials) from the user to access the user’s information on the real site

Intercepting a conversation, passing along altered parts of a discussion between the legitimate participants, or eavesdropping:
- Besides the example with individuals associated with T293 receiving emails (where eavesdropping took place, and the information was used to deceive customers), fake chat services are another example
- An attacker could set up a chat service that mimics that of a bank
- Using the information gained through interception similar to the first scenario, the attacker can chat with the target while starting another chat with the real bank
- Pretending to be the target, they can use information provided by the target to access the target’s information and account
How to prevent MITM attacks
Fortunately, the German art collector’s private bank account was deactivated on January 31st, and his money was returned to him. Currently the scheme is being investigated by law enforcement with the cooperation of T293. But what can people do to avoid occurrences such as these?
There tends to be certain interactions more susceptible to MITM attacks, such as:
- internet messaging systems
- ecommerce sites
- financial sites
There are certain actions that can be taken to help prevent these attacks from occurring.
For individuals:
- Avoid wifi connections that aren’t password protected
- Pay attention to browser notifications that report websites as unsecured
- Log off immediately from secure applications when not in use
- Avoid public networks when conducting sensitive transactions
- Pay attention possible to suspicious links and information
For website operators:
- Use secure communication protocols, including TLS and HTTPS—this encrypts and authenticates data transmitted [4]


Great post. There are some fantastic takeaways here that more people should know. I wonder how much data somebody could incept just sitting in a Starbucks or McDonalds for a couple hours? I highly doubt those companies really care about the protection of your data on that network. They just set it up so they can put a sign out to bring you in the door. If nothing else I’m going to make sure that I stay off those types of networks if at all possible. There really isn’t any reason I should need to view my banking information and send sensitive emails while waiting for my coffee after all. If a *really* need to, I’ll just use my cellular data. No reason to get my information stolen over something silly like saving a couple MB’s of data.
Good post. Man-In-The-Middle attacks seem to be pretty common when applications / servers do not verify SSL certificates. It’s scary how these sorts of attacks can happen with no idea from the victim – as you mentioned, the victims believe that they are interacting with the correct client(s) / server(s). In this case, it is quite concerning that a single person could potentially lose such a large sum of money off the basis of a rather simplistic attack, and is a reminder as to why we need to be careful when using third-party services for exchange of goods or private information.
I think the most interesting bit of information from this article is how much of the negotiation process took place on e-mail. You would think that a large purchase would warrant a face-to-face meeting or at least a video call, at least before transferring the money but I guess not (lol). But even that’s not 100% secure. After reading this post, and a few others on this blog I have definitely learned to stay off public networks, especially ones that are unsecured.
This is my first time hearing about MITM attacks. I was honestly amazed when I read that these types of attacks could also happen on secure servers (https) by using various methods of browser exploitation such as HTTPS spoofing. I would expect these kinds of attacks to happen on unsecure networks or http servers, but never on https servers… the more you know I guess. This post definitely makes me question how much security we actually have when we interact with random people online and makes me question who I’m actually talking to. Great blog post!
First, this is probably the most well-written and comprehensive blog post I’ve seen so far, so kudos to you. I had already heard of man-in-the-middle attacks, but I hadn’t read about too many cases.
I find this specific case extremely interesting because of how pivotal interpersonal interaction was to the attack. This aspect seems to be relatively unique to MITM attacks. Aside from using a hijacked account to send out phishing links, most attacks don’t bother with this type of identity theft. Had this been a more traditional attack, the only possible human error would be from the victim, but in this case, the attack was foiled due to the attacker failing to properly impersonate the art gallery.
I would guess this is why MITM attacks seem to be rarer than traditional malware. Once a virus is installed, the attacker generally doesn’t have to do much more than letting the software carry on its work; an attack like this requires constant engagement from the attacker. The case highlighted here is also targeted specifically at people who interacted with the art gallery prior, meaning there are fewer potential victims. The high effort combined with the lack of potential victims probably means that this type of attack is rarely feasible from an economic standpoint.
This story is scary because the victim was essentially spied on to find out he was interested in this artwork. I do think he should have done more diligence on his part, such as asking for more photos, and perhaps a timestamp with it. Sending money sight unseen is one quick way to losing it, as this often happens on online marketplaces, where individuals send deposits only to be promptly blocked and the seller’s ad deleted.
This is the first I’m learning about middle man attacks, you explained the way it works very well. I thought the main issue to look out for was unrecognized emails, companies I have no association with and people I haven’t been in contact with before. I was aware it’s good practice to look for spelling mistakes or variations in email addresses but I hate to imagine it’s so easy to personalize these attacks. Weaponized email addresses and leaked information is a scary combo.
Although I do feel the art collector was a bit naïve believing the emails, it is understandable how he was convinced. I’m sure he was beyond excited to buy the piece. I could imagine there was a language disconnect too, as he was German and the gallery was based in Rome. That may have made any potential mistakes from the scammers more excusable.
In another post I mentioned how fake emails are becoming more accurate to the real ones and it can be easier to slip up and not notice it, and this post is the perfect example of that. I was also wondering while reading this about ways to combat being victim to a MITM attack and not give away information, so I am glad to see the guide and tips included and will make sure to follow them.
This was a very informative post! I had never heard of MITM attacks before, and you did a really great job explaining what they are! It’s fascinating (and a little scary) to me to see just how easily attackers are able to intercept and hijack a conversation and have the victim not notice. It’s a very good lesson on staying vigilant while online, and making absolutely certain you know who you’re dealing with, especially when money is involved. Although the art collector should have been more careful, with such an important sale and large sum of money on the line, I have to say I can understand not noticing one changed digit in an email address. I really appreciate you talking about ways individuals can protect themselves from these attacks, and will definitely be incorporating some of them into my life.
Thank you for sharing such an informative blog post. I have never heard about MITM scams until reading this post. It’s scary how easy it is for hackers to intercept and hijack information without giving the victim any clues. Scammers have become very intuitive on finding new ways to scam other individuals. This shows the importance of being careful in an online environment, especially if there is money involved. Great blog post!
Great post! You started off with a very interesting story that spiked my interest. It is very good to hear about such stuff as it could really happen to anyone, perhaps on a smaller level to most of us, but once again shows that one should really be cautious when trusting things online, especially when it comes to personal data or monetary transactions.
I also appreciate that you went into some more detail on how such an attack is executed and how the it works on a security level. There was some very interesting knowledge that helped me understand MITM attacks. Furthermore the inclusion of tips to prevent such attacks were good. I was always cautious when connecting to public networks but will do so even more in the future!