
Microsoft recently announced that effective April 2022 all VBA macros retrieved from the web will now be disabled by default for the following five Windows applications: Excel, Word, Access, Powerpoint, and Visio.
What is a VBA Macro?
A macro is a way to record, store, and run a series of commands, most often used to automate repetitive tasks in Office apps. Visual Basic for Applications (VBA) is a programming language used to write Office macros.
Lots of office workers use VBA macros regularly, including me. At my current job I recently wrote some simple code that links a data entry form to a spreadsheet. The macro is embedded in the actual file and runs whatever code is saved on it, once enabled by the user.
What’s the Big Deal?
Malicious agents can take advantage of this feature by embedding malware in any document that supports VBA.
The document is then typically shared online or via email in a phishing/spearphishing1 campaign. Once the user opens the file and enables macros, the malware executes in the background. This can allow the threat actor access to the user’s stored files, network, personal information, and even gain remote access to their machine.
Since the malware exists within the Office file, it can spread and embed into other files, and compromise all of the user’s Office documents. Since VBA is compatible with all five Office apps, it can also spread across platforms.
The Weakness
While Microsoft already provides a security prompt to users about macros:
This doesn’t seem to be enough of a deterrent. All a threat actor needs to do is convince the unknowing (non-technical) user to Enable Content via some Social Engineering. Once the file is downloaded, the last line of defence between the user and the threat becomes the single click of a mouse.
This creates a huge population of vulnerable users since the Office Suite is a common preference for many organizations, public and private. Too often, many users (and some organizations) are not even aware of this risk, making it (in my opinion) the developer’s responsibility to ensure proper safety measures are enacted.
Microsoft’s Solution
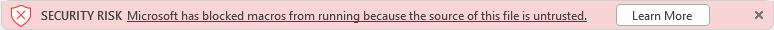
As of Version 2203 (incoming this April), all macros in files retrieved from the internet will be blocked by default.
Users will no longer be able to easily Enable Content, and will be notified with the following prompt:
Clicking Learn More 4 links to a web page informing users about the security risks from downloading macros, some safe practices, and how to enable macros once the user is certain the file contents are safe.
Mark of the Web (MOTW)
Any file retrieved from an untrusted source like the internet will be labelled as having the MOTW, automatically blocking all Macros from running. To run Macros, a user must save the file and manually remove the MOTW.
To end on some general tips Microsoft offers4:
- Only open file attachments that you are expecting
- Only open files from Trusted Locations/Trusted Publishers
- Be suspicious of files encouraging you to Enable Content
- If you download a file with macros, and you’re unsure what they do, just delete that file
With this new feature, Microsoft hopes to simultaneously deter malicious agents while educating end-users.
Sources
- 1: https://www.cynet.com/attack-techniques-hands-on/office-macro-attacks/
- 2: https://therecord.media/microsoft-blocks-internet-macros-by-default-in-five-office-applications/
- 3: https://techcommunity.microsoft.com/t5/microsoft-365-blog/helping-users-stay-safe-blocking-internet-macros-by-default-in/ba-p/3071805
- 4: https://support.microsoft.com/en-us/topic/a-potentially-dangerous-macro-has-been-blocked-0952faa0-37e7-4316-b61d-5b5ed6024216
- 5: https://thehackernews.com/2022/02/microsoft-disables-internet-macros-in.html




Amazing post!! It was really fun to read your post because we were just taught about macros in class and it is great to see a real life example of it. The graphics made the blog even more interesting and informative. To be honest I did not know about this type of malware before this course and I can say with confidence that I know a lot more after reading your blog. I believe all students daily use microsoft apps for school work and all of us do indeed click on “Enable Content”. Leaving us vulnerable to attacks. However, it is great to see that a new update is on its way which can help keep us safe. As students we truly do not want to lose all the assignments and notes so in my opinion this update is the right thing to go with.
Thanks Munhib,
It’s easy to spot attempts at malware attacks via typical means (sketchy websites, phishing attempts etc…), but when the malware is embedded into a legitimate software that is widely used and trusted it becomes more difficult to sniff out.
The biggest challenge here is that lots of people are not aware that VBA macros have this capability, since there is an option to record macros without writing any code in most Office apps. Since so many templates for typical office documents (ex: an annual income sheet) exist online and are downloaded on a daily basis, the risk becomes very real. In general, most VBA code used for the typical operations of an organization will be easy enough to decipher. So, if you notice anything weird in the code, it’s best to not use the document.
Great post, I believe this is an issue that more people should be aware of. I also work at a job where we use macros and I didn’t quite understand the dangers behind “enable content” until this post! The malware that can be possibly embedded into VBA would be hard to find for the average person. Even as someone with decent coding experience, VBA is like torture syntactically which further adds to the layers it can hide behind, especially in a complex macro. Given how widespread MS Office is, I’m surprised this type of malware isn’t being talked about more.
This is a very good post. I believe that most people are not very familiar with VBA macros. For me it’s often just curious why every file someone sends me has a security warning. But after I clicked Enable Content, nothing changed on my computer and files, so in my mind this security warning is irrelevant, because nothing changed even if I clicked it. But after reading this post, I deeply realize that every day there are very many computers infected with computer viruses, not because the computer viruses are too powerful, but because people always judge a thing that they do not even know the principle with the information they have. This arrogance and lack of care will one day bring a bad end.
Good post! I remember not knowing anything about what enabling macros could do until we were taught about it in class, so it is good that companies like Microsoft are at least making an attempt to make it less of a mindless habitual action to just click enable every time you use their software. Hopefully they can keep the annoyance to a minimum by keeping their list of acceptable and trusted software up to date.
I remember reading how macros in a file could steal like you passwords a while back, this seems like a great step in the right direction for Microsoft’s cybersecurity. I liked how you talked about what a VBA macro is and how it could cause malware to be run on an individuals computer. But I also believe that this is very good for consumers as I think most people when they download something like excel, I don’t think that they’re intending on running macros like for student they may just want to see the data in excel not run any macros, this seems like it’ll protect a lot of people from losing their information through malware from macros. I really liked how you talked about the macros and the protocols that will be implemented to prevent this sort of malware.
With the regular and increasing use of macros, I’m really glad Microsoft took this into consideration and created this security feature. As you stated, many people and organizations don’t recognize the risks of downloading insecure macros and it really just takes a single click before disaster ensues. In fact, I was one of these people who didn’t know of these risks with downloading macros (thankfully I haven’t been infected yet) but this post really increased my awareness of them. So thank you!
This post is a great read! I’m in business analytics so we have to have some familiarity with VBA so it’s cool to see Microsoft address some of the issues that were brought up in our classes. Our profs continuously told us to not blindly download excel VBA files (.xlsm files) to learn how to do different processes however there never was really a deterrent as you mentioned. It is very easy for people to just click the “enable macros” button without realizing the potential security risks involved. It sucks to see that there are person preying upon people’s ignorance, especially with a program like Excel which so many companies use, but it is nice to see Microsoft doing their part and trying to protect their users.
Nice post! I’m really glad that Microsoft is finally taking steps to more effectively mitigate macro-based attacks. As I recall from past years, macros have always been a pretty significant security hole in the Microsoft Office suite of products. They used to be enabled by default on any file – regardless of the source – until that old warning prompt was added. For the most part, I don’t think any organization should be allowing a macro that was not written in-house to be run on any computer on their network.
Great post, I have not used a ton of VBA macros but I have heard a lot about them and wanted to look into them for numerous tasks. I did not know about malware being embedded in them and being able to spread to all the other office systems and files. It is nice to see Microsoft doing something to try and help fix the problem, and I will definitely have to be cautious when it comes to enabling content in office apps, something that I have not really been concerned with in the past.
Interesting post! I honestly had no idea about macros and after reading about it, I am surprised like pretty much all of us use Microsoft apps for school, work etc. and we are required to open some files to view them and then sometimes we just enable content and we don’t even try to learn more about it and there is a chance it might be a malware and lead us to attacks but now I will try to be more cautious.
Thanks Achraf Abdelrhafour for this post. The second image actually explains everything about the malware spreading in the the user’s computer as soon as the user clicks with the mouse. From my point of view, I think many people whoever are using office softwares including us, are not even aware of or ignores that security message that used to pop up whenever opening an unknown file. Relating to that I agree with the proposal of microsoft where they will be concisely validating and verifying the the file which will be coming from an unknown source. The plan seems sophisticated, so hopefully it would be reducing the number of possible malicious attacks that could be happening to a user’s computer.
Great article! I’m quite unfamiliar with the concept of macros but thanks to your comprehensive article, I understand it perfectly. Of course, most people aren’t aware of macros and VBA, let alone malware related to enabling macros. So, it’s good that Microsoft is introducing a default protection mechanism. Even if it might seem annoying to some users, it’s a step in the right direction on Microsoft’s part. Not only does it protect the user from phishing, it also educates them on how “enabling macros” has a lot more to it than clicking a button.
As someone that had to regularly work with VBA Macros at work I always found the old security prompt screenshotted above to be pretty annoying but ultimately pretty easy to get around. Considering how widely used the Office suite is I’m glad to hear that Microsoft is taking more action to protect users that may not be aware of these security issues. If anything, I’m surprised they didn’t issue something like this sooner. Maybe there’s been an increase in attacks with working from home during COVID.
Wow! I had no idea that something like this was possible. I was unaware of what VBA was, and how malware could be embedded in applications that support it.
Prior to Microsoft opting to block macros in files downloaded from the internet, I (and I assume many others) would always click the “enable content” button whenever prompted to in an Office application. This post served as an excellent reminder for me to be more cognizant when working with files downloaded from the internet, even if they are opened in an application that I have previously deemed to be trustworthy.
Instructive Post, We can use VBA macros to automate everything from simple tasks to complex reporting processes with multiple files. It’s really easy to use it to automate simple things in Excel and it’s pretty easy to create a user interface if you’re trying to build a tool for someone else to use. However, anything that requires matrix manipulation, storing lists, or even type-casting, is a pain in VBA. Also, VBA is slow and buggy.
Amazing , i like the way your post is easy to follow and to understand , especially with such a technical concepts that amazed me .
Also , i would like to stress that the use of interactive photos really improved the post’s readability . The solution provided looks good , especially that everyone uses microsoft services ( school , work … ) and we really need some kind of protection from malwares to feel safe while using the internet
It’s interesting to see that macro based malware are still prevalent nowadays, especially since a large portion of older malware used to come in the form of macros written for MS Word. For some reason I assumed that macro based malware died out around the same time Microsoft disabled the autorun off of usb feature, but I appear to have been mistaken. An informative read!
Good Post! While I denounce the actions of those who would create malware hidden inside VBA macros, I have to commend both the creators of the macros and Microsoft, for both coming up with clever ideas to combat one another. First, props to the creators of this type of malware, as hiding malware in simple VBA macros is a very clever and sneaky way of gaining access to a surprisingly wide amount of applications. Second, props to Microsoft for implementing the MOTW protocol, it allows experienced users to use the helpful VBA macros while automatically shutting down any forms of malware hidden in any macros found online; but in order for an individual to unlock a macro locked by this protocol, the user should know what they are doing and it ensures a degree of caution regarding the file that they’re opening.
Great post!
Even though I am a fourth-year CPSC student, I am still not familiar with macros. When I see the security warning about macros in the Microsoft Office files, I always choose to enable macros functions. This is because I always want to get full services from Microsoft Office applications, and I think if I disable macros functions, then I will not get that part of services. I know there might be some macro viruses hiding in the Microsoft Office files that can infect my computer easily if I enable macros functions, but I trust the anti-virus application installed on my PC that can detect and “kill” those viruses successfully. I must say I’m taking a fluke in this matter.
Your blog is very helpful for me to understand what the macros are and how they work in the Microsoft Office files. I will follow the tips that you provided to us while reading and editing Microsoft Office files in the future. Thank you for your useful tips!