The increase of companies transitioning to online/remote work over the past few years have led to a massive increase of companies online presence. This fast expansion has made it hard for companies to ensure there are no exploits or blind spots in their systems which has given cyber attackers a much larger area to find opportunities to exploit and attack. This has led to many more successful cyber attacks, which is why many companies have implemented Attack Surface Management (ASM) to combat these security threats.
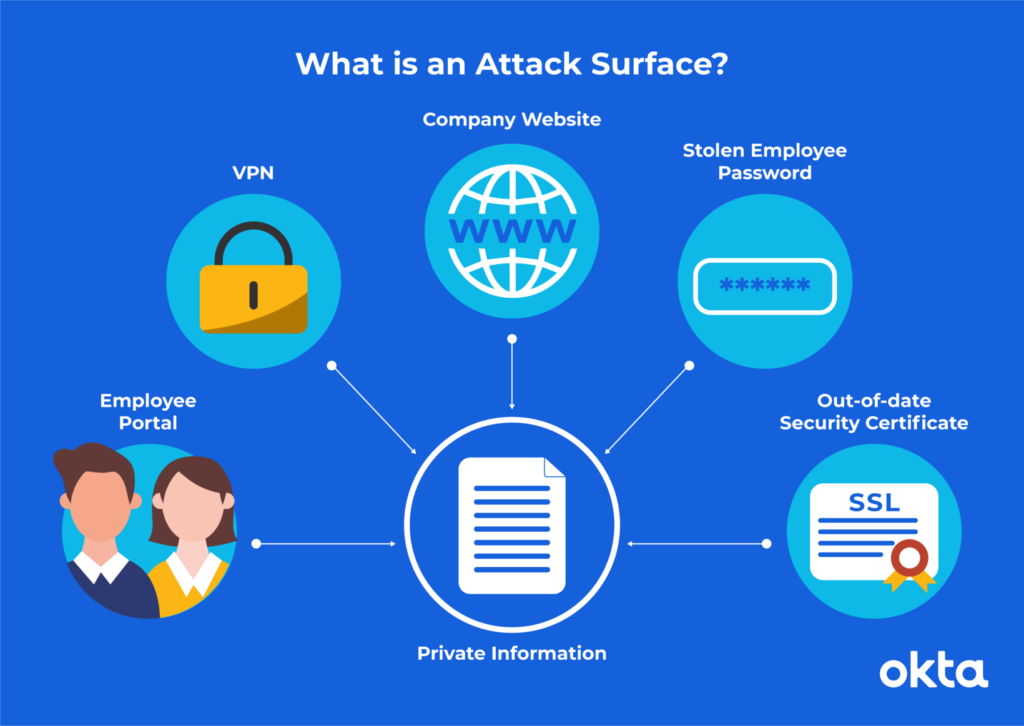
What is Attack Surface Management?
An Attack surface is the many different ways an attacker can get into a company’s system and steal or change data/assets. ASM is the process of monitoring, evaluating, and analyzing a company’s online infrastructure/systems from an attacker’s perspective so they are able to mitigate or remove the risks involved with the system before attackers are able to find and exploit them. There are 2 types of ASM that companies need to be aware of:
- External ASM which is the management of internet exposed data/assets and reducing the blindspots that are vulnerable to attack. These are usually found by scanning through the system and using cyber attack techniques and tools.
- Internal ASM which is the management of data and assets that only people within the company have access to, which is usually not online but within the server or company itself.
ASM starts by discovering areas of concern because it is impossible to manage and fix something that people are unaware of. Next a company should start prioritizing the vulnerabilities by severity because there is no reason to spend a lot time and money on a minimal threat. Then a company should attempt to continuously monitor while attempting to resolve the issues.
Why Is ASM Important?
Ransomware costs businesses more than $75 billion per year, according to one report, and it is well known that data breaches and hacks are usually caused by an overlooked area in security instead of sophisticated exploits which is why many companies should implement ASM and be more vigilant about their cyber security. With companies rapidly expanding, attack surfaces constantly changing, and the number of remote work increasing has led to the implementation of ASM necessary and on the rise as well. ASM can be used as a tool to find vulnerabilities in email records and systems, website security and infrastructure, operating systems, as well as things like outdated hardware, software and weak passwords. This information can then be used to fix the vulnerabilities or at the minimum allow companies to become aware and monitor the situation which helps mitigate the risk of attacks, data breaches/leaks, etc. ASM is a tool that should be implemented throughout a company to help bring awareness to security issues so they can be handled properly and deter cyber criminals from attacking your network because there are no easy entry points in the system.
References
https://thehackernews.com/2022/02/how-attack-surface-management-preempts.html
https://www.makeuseof.com/what-is-attack-surface-management/

This was a good introduction into what ASM is. I also agree that this is an area which will see a lot of demand in the next few years, especially with the popularity of working from home. With new innovations comes new ways to be vulnerable after all. Would you say that there are particular industries that should seek using ASM or would this be method that should be applied to every company that uses such a network?
From reading your blog post, ASM seems a lot like red-teaming (or pentesting) where individuals or groups are paid by a company to attempt to break into their system and find vulnerabilities (typically within a scope). I myself find this to be the most fun part of cybersecurity, where you actually get to apply your knowledge hands-on and find different ways to exploit a system. ASM might just be a smaller subset of red-teaming. This is a great post!
This is a new term that I’ve never heard of and it’s interesting to see that companies who had no choice but to transition to remote work are now paying more attention to protect their sensitive data. I believe due to COVID, there are now more companies who are willing to invest and pay for penetration testing, or perhaps hire consultants/3rd party contractors to perform ASM related analysis to better protect their information. Some companies may have neglected ASM related practices due to IT not being a function that generates revenue, but are now waking up to the idea that prevention is priceless.
An unintended consequence of remote work is the security flaws through employee portals. Where an attacker would have to infiltrate a system that was mostly local before remote work, an attacker now has a defined target and a level of guaranteed privileges when surface level security measures have been bypassed. Even worse, how can someone tell if sabotage was done by an outside attacker, or a disgruntled employee? Perhaps the employee gave away someone else’s credentials after leaving the company or being fired. Another potential of harm of remote work in terms of security i the fact that employees themselves could be targets. Where an attacker would have to target the company specifically before, now employees have access to company information from their homes. This puts them in danger of being targeted personally which also puts their own information at risk. Keystroke malware could be discretely installed on an employees computer, even from a file not related to work, and now both the company and the individual are in danger. Just some food for thought on how remote work probably makes company and personal security less secure, thank you for the insightful post.
As you mentioned, since working at home is becoming more popular, it is important for companies to take steps to protect themselves and their data. $75 billion per year is a crazy high number, showing the importance of protection against ransomware. One thing that is important to mention to employees is new security training. Since employees may use stuff like portals and terminals from home, they need more knowledge and expertise on what types of attacks they need to look out for and what to be weary of. I think it is very important for companies to not only implement ASM, but also help increase employee awareness to prevent these attacks.
I agree with everyone on here. This is new terminology to me as well. I think everyone should implement ASM to their highest capabilities. The continuous monitoring of an organization’s digital assets should be prioritized and thoroughly examined. If companies are not capable of implementing an ASM system for themselves, they should definitely hire people who makes ASM systems for a living, and there are plenty of them.
It’s good to hear ASM is becoming more common. With the statistic of $75 billion per year lost to ransomware the implemented defenses should be getting more sophisticated. Hopefully as time goes on it continues it’s prevalence, evolving alongside the attacks. With more awareness of blind spots and weak points, threats would be dealt with more efficiently, putting time and money towards more important matters.
Hey, great post. I think ASM would be a great tool for corporate espionage. With many countries entering a state of the cold war, outright aggression and hostility are frowned upon. However, if a country or individuals wanted to harm a corporate or a crown enterprise (i.e. Canadian Railway), they could utilize ASM to achieve their ends. I think you also mentioned remote work because ever since COVID, remote work has become a modus operandi for many companies and with that more money should be invested in counter ASM. Finally, I have not heard of this before and I think you did a great job at shedding some light on the process and the consequences associated with a successful ASM. Good job overall!!!
Great post Nathaniel, I had never heard of ASM but it seem like the type of product that I will start to become more familiar with. As you mentioned that people are working from home more, so there is just too much time and effort for companies to try and keep everyone safe at all times, from everywhere, from ever evolving threats. Sounds like there could be lots of potential for ASM style systems, as security gets more and more advanced and companies looks to specialists to fill the void.
Great post, but I think this raises an important question, and that is “Why hasn’t this always been popular?” I mean surely corporations have always wanted to prevent these mass data losses, and/or transferring money to someone who they can’t possibly think has good morals. Obviously, with the unfortunate COVID era we are currently in, it makes sense as to why it is now getting popular (due to many transitioning pains corporations are having). However, I would argue that such a simple concept, that yields (hopefully) good results, shouldn’t have been ignored for so long by all these corporations who are just now adopting it. Either way, you explained ASM very well, and I can now add this to the things I know about security practices!
With the growing popularity of ASM to account for the increase in remote jobs, this article does a good job giving an introduction into the concept as well as the reasons why it is needed or recommended. This post does a good job in provide insight on the strengths of ASM and how it can compensate for the lack of foresight people may have when providing the necessary security for workers who complete their tasks remotely. Additionally, with the current world political tensions rising and the increase in government sponsored cyberattacks, ASM becomes more important in order to protect and fight against the increasing cyber threats to which the article does a brilliant job in pointing out the need to increase awareness against the growing security issues.
This is the first time that I heard of the term ASM and I completely agree that ASM should be implemented to prevent attacks. Since everything had transitioned to mostly online and ransomware being on the rise, this ability to scan for security weaknesses would be beneficial. I am also glad that ASM is becoming more common because I do not want any security weaknesses in the networks that I connect to.
This is a very good post! With a reported annual loss of $75 billion due to ransomware, deployed protections should be becoming more complex. And I agree that every other thing nowadays is online and thus these attacks are becoming more common and other vulnerabilities are coming in front of us. I remember people didn’t trust zoom because of their security reasons. But it is nice to see that ASM is becoming more used as it covers those loopholes of cyber-security. Nice Read!
Nice explanation of ASM, this is the first time I am seeing the term but it makes a lot of sense. I like how ASM allows companies to efficiently focus on where their security focuses should be- I guess the only weakness I see in this is if the hackers are able to find an attack surface that the company was not able to find. (Although I guess no matter what kind of security protocols one has this will be a problem haha)
Your article makes an apt observation about companies being forced to pay more attention to security as a result of the work-from-home shift due to the pandemic. While this may be one of the few beneficial developments resulting from otherwise dire times, it reveals huge security gaps in most company servers and might make way for new methods of exploitation. ASM may prevent common cybersecurity attacks, however, the attackers may also develop improved and more attack surfaces to bypass system protections. A security breach may not just be some unknown attacker trying to steal data. It could even be as simple as an oblivious higher-level employee clicking a phishing link and giving away their information. I think, along with ASM, companies could also host cybersecurity workshops to prevent data breaches caused by human error.
This article does an excellent job of defining ASM. Cybersecurity concerns are on the rise, especially with the popularity of working from home. ASM is a fantastic tool for detecting vulnerabilities in systems, allowing companies to become more aware of the situation and monitor it, reducing the danger of an attack. ASM will surely be popular since it is a crucial security tool for companies.
Thank you for sharing this topic. In recent years, more and more companies have begun to try online office due to COVID, and home office has become common. I think even if the situation improves and people start to return to the office, some online office methods will still be used by companies. In the future, how to protect the network and information security when working online has also become a very important issue
Good post! I have read multiple posts on Ransomware and in general it seems like one of the biggest threats online, for companies but also individuals. I like that you go into a bit more detail on possible defenses against ransomware for companies. Especially with the amount of remote work during the pandemic it is integral for companies to protect themselves from such attacks. And ASM seems like a great way, to monitor your systems in a way similar to attackers so you can hopefully find critical problems before the attackers.
Great post !! i like the way you used photos to explain the concepts more . As ransomware attacks grow stronger , there was a need of a service that will keep itself vigilant against those attacks .
One thing that this post makes me curious about it how much we still have to learn about good ASM practice. If companies are embracing remote work far more than they did before, then would they not do their due diligence about the attendant cybersecurity risks before they fully commit to this direction? If so, then perhaps an important part of remote work ASM strategies should be the careful documentation of every attack and issue faced by the company. That way, companies learn from their mistakes and get better at navigating this new reality faster. This process would work much better if companies shared their experiences with one another. I wonder if there would be market incentives to keep this information secret. Overall, that would probably be counterproductive for the companies themselves.