
What is Maze ransomware team?
For ransomware Maze ransomware can be considered a trendsetter. Most of the ransomware currently available on the Internet encrypts files on the victim’s computer after infection, and then will require the victim to pay money to a designated account within a certain period of time, or the files will be deleted or unrecoverable. And the Maze ransomware team was the first of all ransomware teams to threaten to publish sensitive information about their victims on their website if they didn’t pay the ransom. Maze starts its crime from May 2019 to its November 1, 2020 when they announce their official retirement.
The cyber crime operation published large amounts of documents filched from Xerox, LG, Southwire, Canon and the city government of Pensacola among other targets that refused to pay up. Maze would often publish tens of gigabytes of these files on its dark web “leak site” Maze News in retaliation for a failure to pay the ransom by a specified deadline. Sensitive information that it published included employee information files, proprietary information about products and internal source code.[1]
Retirement?
Back to retirement, the Maze team officially announced their official closure on their website on November 1.
At the time there were many websites that covered it and most of them mentioned several issues.
Firstly, the Maze ransomware team’s retirement was fraught with problems, and most people felt that they didn’t really recognize the wrongness of their actions. Even they themselves believe that their actions were justified. Here are the responses from the Maze team.
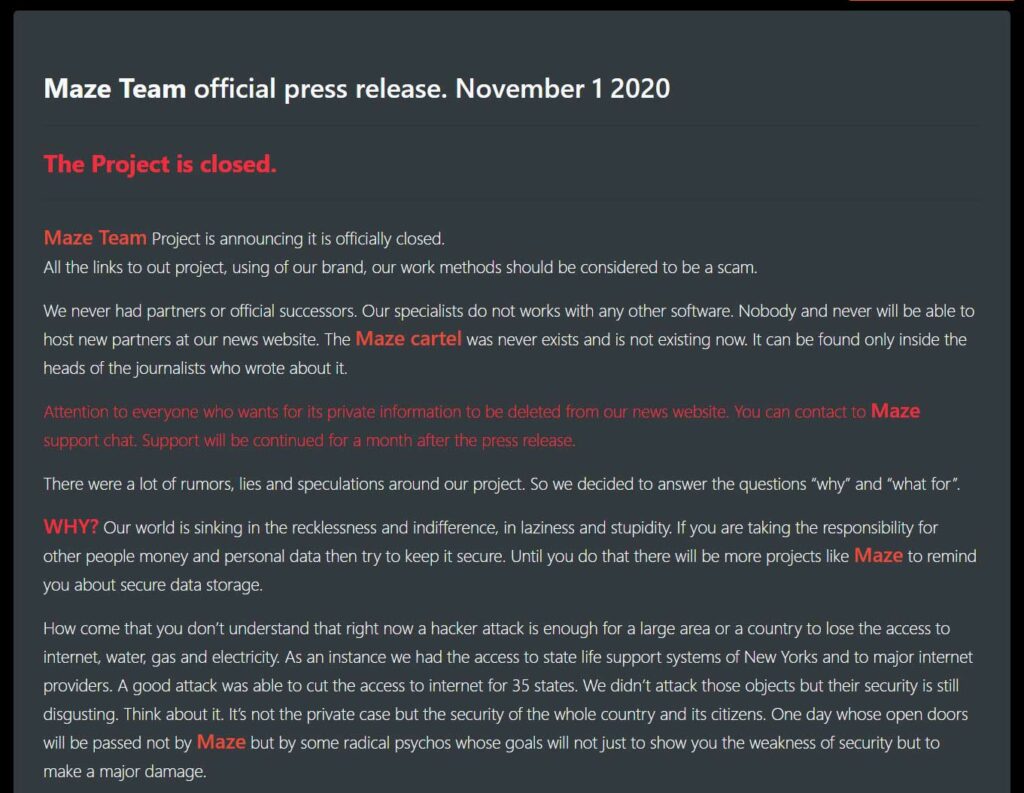
For this reason, most of the news writers believe that the retirement of the Maze ransomware team is probably just a ruse, and that they have probably just abandoned Maze in favor of the new ransomware Egregor, which has a lot of similar code.
Secondly, Maze team announced that they stopped their activities and deleted the private sensitive files posted on the internet. For those users whose files were encrypted, they did not provide the key to the general public, while most other ransomware organizations release the key to the public after a complete shutdown.
End?
On February 10, 2022, it was reported that someone posted on the Bleeping Computer forum claiming to be the creators of the ransomware, Maze, Egregor and Sekhmet. The poster also posted keys for all three ransomwares and claimed that all those involved in the ransomware were out of the ransomware game for good.
Hello, It’s developer. It was decided to release keys to the public for Egregor, Maze, Sekhmet ransomware families.[2]
also there is a little bit harmless source code of polymorphic x86/x64 modular EPO file infector m0yv detected in the wild as Win64/Expiro virus, but it is not expiro actually, but AV engines detect it like this, so no single thing in common with gazavat. Each archive with keys have corresponding keys inside the numeric folders which equal to advert id in the config.[2]
In the “OLD” folder of maze leak is keys for it’s old version with e-mail based. Consider to make decryptor first for this one, because there were too many regular PC users for this version.[2]
The Maze ransomware team will not be the first ransomware team to announce its retirement, nor will it be the last. In just 18 months, this team has caused financial losses to too many people. Yet in their eyes it all seems like a game. Who can guarantee that they won’t come back. But I believe that in the future, as people’s awareness of cyber security increases, and the law improves, ransomware will slowly decrease!
Reference
[1] https://www.cpomagazine.com/cyber-security/maze-ransomware-group-infamous-for-adding-doxxing-threats-to-attacks-announces-it-is-shutting-down-its-cyber-crime-operation/
[2] https://blog.malwarebytes.com/malwarebytes-news/2022/02/ransomware-author-releases-decryption-keys-says-goodbye-forever/
[3] https://cisomag.eccouncil.org/maze-ransomware-retires/
[4] https://blog.malwarebytes.com/ransomware/2020/11/maze-ransomware-gang-announces-retirement/

Hey, I enjoyed reading this article. I understand that there are hackers out there that do try to expose the weaknesses in cybersecurity of major corporations in an ethical manner, namely ‘white hat hackers’, but I don’t believe any form of ransomware serves such a purpose. At least with ethical hackers, corporations can learn and improve security before any actual damage, such as ransomware, can occur to them. I suppose I can understand the message that Maze is trying to portray by demonstrating how much damage they did and could’ve done, they stress the importance of having good cybersecurity.
I think if they truly were ethical, then they wouldn’t have released the data they stole onto the black market. If their goal was only to serve as a warning, they wouldn’t demand a ransom, and they wouldn’t publish sensitive information.
I agree. Perhaps they started out as white hat hackers, but when they got to the point of having that power in their control, they couldn’t resist to use it. It certainly seems that if they were in fact white hat hackers, they could brought attention to their cause with more positive means. But then again, sometimes it takes something extreme to actually get peoples attention.
It does seem like the people at maze have a general disregard for their actions and feel vindicated as they think they’re highlighting security flaws. I if they committed attacks without demanding payment or threats then their actions could be justified, however they seem to have done crimes as a black hat hacker and tried to justify it as showing security flaws. I wonder if any of these people will be prosecuted in the future or if they simply will get away with previously doing these ransomware attacks.
It seems like individuals at maze have an overall dismissal for their activities and feel justified as they might suspect they’re featuring security defects. The chance that they perpetrated assaults without requesting installment or dangers, their activities could be advocated, but they appear to have done violations as a hacker and attempted to legitimize it as showing security blemishes. I still wonder whether any of these individuals will be caught later on or then again in the event that they essentially will pull off beforehand doing these ransomware assaults.
Interesting. One would think it is a bit counterintuitive to claim to be attacking to show the lack of care that big companies have for our personal data, to then also release all of the personal data gathered during the attack if the ransom isn’t paid. I wonder if they were truly striving to make the world better or were simply issuing an excuse for their actions before retiring from the ransomware business. I also find it weird that the keys for the encryption their software executed were released separately from their main statement of retirement. Maybe the original statement was a hoax?
Really interesting post! I wonder if this is the thought process of other hackers/ransomeware groups, where they think what they are doing is not wrong and they are just doing it to show flaws in the system. But them asking fr money really ruins their message, but then again maybe they think if they collect money from these businesses, then the businesses would take their cybersecurity seriously.