Twitter appears to be distancing themselves from their two-factor authentication provider, Mitto AG, following recent controversy regarding Mitto AG’s COO selling access to their network to surveillance companies.
Mitto AG is a communications company, lucrative for their expansive network spanning across over 100 countries gained through deals with companies already established in these countries. They’ve had many high profile customers such as Google, WhatsApp, Twitter, TikTok, and Telegram. Many of their work involves the delivery of two-factor authentication through SMS messages. If you’ve set up 2FA with any of the aforementioned companies then chances are you’ve witnessed Mitto’s work without realising.
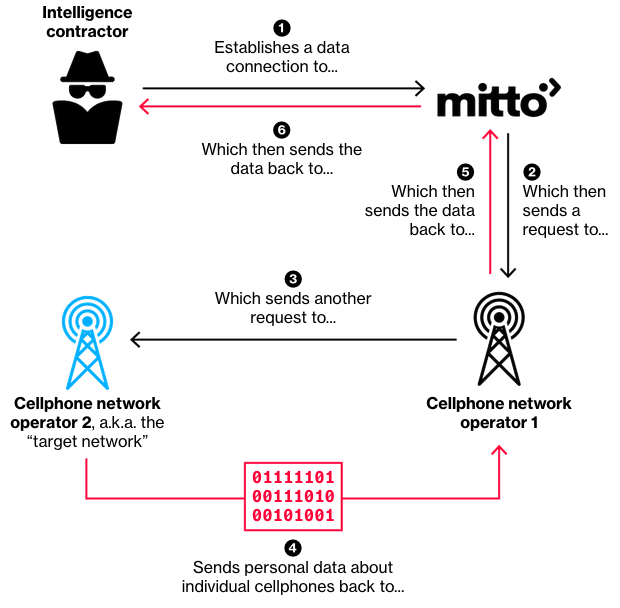
The Switzerland based communications company is currently facing allegations of running a secret surveillance service, allowing surveillance companies to exploit the vast telecommunications network they have access to. Using custom software, people with this access could track someone’s location, or even access one’s call logs through vulnerabilities present in the outdated protocol “Signaling System 7” that many networks use.
Mitto claims that this cartel wasn’t a company scheme, but rather the work of a few select people with chief operating officer Ilja Gorelik as the ringleader. Evidence of this has piled up since the collaborative investigation carried out by Bloomberg News and Bureau of Investigative Journalism, with the final nail in the coffin being Gorelik’s resignation. Twitter’s decision to distance themselves from Mitto only further solidifies this.
Although it isn’t fully known how much surveillance has been carried out through Mitto, we can get a general idea. Possible clients include but are not limited to: an unnamed national spy agency based in the Middle East, and Cyprus-based firm “TRG Research and Development” who offer surveillance services to intelligence contractors. It is possible that a senior U.S. State Department official was targeted in 2019, although it is unclear who the client was.
What does this mean for us?
Judging from the information so far we could come to the conclusion that as long as we didn’t use the phone number based 2FA system of any of Mitto’s clients we should be safe, right? Wrong. Mitto’s surveillance is done through its access to many major telecommunications networks, their 2FA services only gives them the reputation to gain access to many of these networks. If you’re a part of any of the numerous networks Mitto has access to, Mitto could very well just scoop up your location and call logs.
“The private sector surveillance industry is growing fast, but it’s operating in the dark, without any accountability or transparency, and there have been real human rights implications because of that”
Jonathon Penney, a research fellow at Citizen Lab
For us plebeians, we probably don’t need to worry since the chances of a surveillance company having an interest in us at an individual level is akin to the idea of an FBI man tracking our every move. However, regardless of whether or not we’ve been directly affected, there is still a massive breach of privacy at play here. The fact that there is the potential that we’ve been tracked is very concerning.
Sources:
- Bloomberg: Swiss Firm Executive Operates Secret Surveillance Operation, Sources Say
- Bloomberg: Mitto Tells Clients That Co-Founder Departed After Allegations of Phone Spying
- MalwareBytes: Twitter cans 2FA service provider over surveillance claims
- The Bureau of Investigative Journalism: Twitter cuts ties to Swiss tech company after Bureau investigation


Yeah, This is very knowledgeable post and I have read something related to this post on twitter so with this post I really got very impressive info about 2FA. Because a user can unintentionally authorise access to a request sent by a hacker without noticing it, 2FA can be subject to a variety of hacker attacks. This is due to the fact that the app may not send push notifications to the user informing them of what is being authorised.
This was an interesting read. I think that 2FA is an important topic to discuss, as someone who relies on 2FA for most accounts this is kind of scary to think about. But now that I think about it 2FA can be quite vulnerable at times as long as there is an established connection between us and the provider that allows the provider to steal our private information.
Its ironic how something meant to protect a users information and unauthorized access to their account is inadvertently allowing for people to track their data such as location and call logs. Surely there must be some more regulations put in place for these telecommunication companies as this tracking may lead people to not use 2FA, which would be detrimental to protecting their accounts. If not then potentially like you said the tracking could expand into more sensitive information being tracked.
Indeed, a matter we ‘plebeians’ face when the “patricians” get cocky with their authority. Based on this informing post, one possible way to minimize vulnerability would be to diversify security mechanisms (using 2FA some while using another system for others, like answering specific questions the owner would know). Unfortunately, this is as much that can be done against these kinds of crooks. Based on the cooperative work done by the media and the federal agency in the case mentioned by the blog, these criminals can still be brought down. But what this can also mean is that we should start discussing whether laws regarding punishments for such acts committed by the “patricians” should be updated and made more severe. It is unfortunate that people think they can take advantage of us plebeians, but as this blog post shows, these crooked dealings will come back like a boomerang.
I admire your way of structuring your post. It is very engaging. I have been thinking 2FA is a good way to protect social media accounts, but it is proven different. My concern is whether we should disable 2FA and back to the regular sign-in option or is there a alternative way to secure our accounts. Whenever a service provider exist, they can find ways to take advantage of our information.
This was a really interesting post. It’s normal to expect that companies who offer services that protect user information would protect that information. With a business network like Google, Twitter, Tiktok, and Telegram, it would be reasonable to expect that our information is kept private. However, this article is a brutal reminder to not trust nor expect such a thing, no matter who or what service uses it. Especially when that service’s motivation (money from information) is against your interests (privacy).
This post is really informative in the context of a “third party” which is involved in enabling the 2FA between the user and the software. As mentioned it is obviously not safe that there could be possibilities of a user getting tracked through these surveillance companies, as social media users would be facing the trauma of trusting the 2FA services. It is extremely difficult to monitor how and when the data is tracked as the notification arrives about the code arrives very quickly and some social medias also do not accept the codes that have sent to the user over a minute ago. This is obviously a violation in the privacy of the user since they trust the 2FA to be the most secure whenever there is an attempt to login from a different device. So far based on the initiative Twitter has taken, it will be really interesting to see what additional secured layer would they be coming up in providing these codes.
Good Post! You make a very good point regarding how even the potential that privacy-breaking tracking has been going on is concerning. I think that a large part of this concern is that we don’t know how many individuals have already been or are being tracked, and if this tracking has occurred, no one will know about it (nor will we know anything about its scale). This is a scary idea indeed. I can see Twitter’s reluctance to continue its partnership with Mitto AG, while the fact that Mitto AG is already partnered with so many other massive players in the communications realm is disturbing.
Very engaging post! This makes me wonder if we can actually do anything about this, since they can still get our private information even though we don’t use their service for 2FA, and as long as you have a phone, and you call people, then your privacy is compromised even though you aren’t on the internet.