What is Ransomware?
Ransomware is a type of malware that prevents a user from accessing certain files until a ransom is paid. This is typically done via 2 types of ransomware:
- Crypto Ransomware: Ransomware that replaces your device’s files with encrypted data[3]
- Locker Ransomware: Ransomware that prevents you from logging into a device[3]
Unfortunately, as time has gone on these methods have developed into something more malicious.

What is Multi-layer Extortion Ransomware?
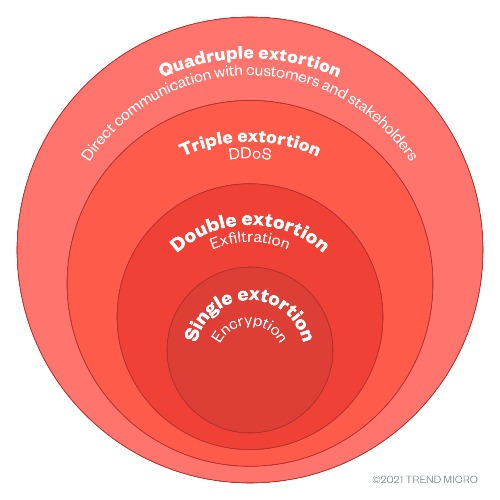
Multilayer extortion ransomware relies on the methods described above but adds other layers of extortion usually involving different stakeholders to get more money out of organizations and using multiple incentives to get them to comply in the first place. There has been documented cases of double, triple and quadruple extortion ransomware.
For double extortion, the second layer used is typically a threat of revealing sensitive information. This technique was introduced by Maze ransomware group in late 2019.[2]
For triple extortion, it builds upon double extortion by adding in a DDoS attack as a third incentive to get companies to pay up. This technique was first seen done by the Suncrypt and Ragnarlocker groups in the second half of 2020.[2]
Although not as popular (for now) quadruple extortion ransomware exists as well. On top of the extortion methods used in triple extortion ransomware, quadruple extortion builds on the concept by reaching out to customers and stakeholders of the attacked organization. For example, ransomware group Clop had emailed customers warning them that their information tied to the target organization would be posted on a website and that the customers should contact the organization.[2]
Who is Venafi and What Was Their Survey About?
Venafi is a cyber security company that recently conducted a survey on organizations to gain metrics on the current state of ransomware attacks. They found the following:
- 83% of successful ransomware attacks in the last year were double/triple extortion ransomware attacks[1]
- 38% of organizations attacked with ransomware received threats to extort customers using stolen customer data[1]
- 35% of organizations attacked with ransomware received threats to expose their data on the dark web[1]
- 32% of organizations attacked with ransomware received threats of telling customers that their data was stolen[1]
The above is quite unsettling when combined with other metrics in the survey suggesting that ransomware attacks are getting more aggressive and that companies are not guaranteed to get their data back after paying.[1]

How to Handle Double/Triple Extortion Moving Forwards?
Respondents in Venafi’s survey had the following to say regarding how extortion threats could be handled moving forwards:
- 67% of respondents agree that publicly reporting ransomware attacks will slow down attackers[1]
- 74% of respondents agree that ransomware should be treated as a matter of national security [1]
- 77% feel governments should provide more help to private companies defend themselves from ransomware moving forwards[1]
- 76% agree that going forwards, companies and governments need to work closer together to fight the threat of ransomware[1]
These findings suggest that organizations feel transparency regarding attacks and stronger government intervention are felt to be venues to explore the future. However, until these changes are made the best we have are guides for single-layered ransomware attacks. The Canadian Centre for Cyber Security has provided this guide for handling ransomware attacks.
Conclusion
It seems that as technology becomes more advanced we develop new and novel cybersecurity mechanisms. However, these mechanisms are always playing catch-up to the evolving landscape of cybercrime. Most recently double/triple extortion in ransomware attacks have gained traction in the last couple of years and the survey from Venafi has verified the efficacy of these attacks. I feel the rate of double/triple extortion ransomware will continue to increase if not move to quadruple extortion moving forwards.
References
- https://www.venafi.com/blog/venafi-survey-ransomware-evolves-double-and-triple-extortion-now-features-over-80-ransom
- https://www.trendmicro.com/vinfo/us/security/news/cybercrime-and-digital-threats/ransomware-double-extortion-and-beyond-revil-clop-and-conti
- https://cyber.gc.ca/en/guidance/ransomware-how-prevent-and-recover-itsap00099

This was an interesting post. It makes sense that double/triple extortion attacks would be more effective. Since these are both direct attacks at the company, the quad extortion seems extremely scary for companies. Targeting customers would cause both reputation and revenue to plummet. Companies could also try ransomware on their competitors as a way of trying to direct more consumers their way.
Nice post! Ransomware should definitely be considered a national level threat, especially when considering the scope of those affected. It’s scary to think that just resolving the first layer of extortion is not enough to be free from the threat of attackers and that there may still be danger lingering afterwards. I hope in the future we gain the insight to be able to defend against these attacks.
Interesting to see how these attacks advance and the impact the advancements have on the success of the attack. Personally I haven’t seen a 3 layer attack prior but it makes a lot of sense why you’d attack this way. By denying services both the owners and users of the service are impacted and can cause significant loss for both parties. The 4 layer attack is definitely the most dangerous as it becomes nearly impossible to assure your users that your security is sufficient when they are personally being contacted by parties that have proved else-wise. Not only will this financially impact the victim of the attack but will definitely pose questions about the credibility of the services being offered to the consumer and can have lasting consequences.
Great post! Like most of respondents in Venafi’s survey I agree that ransomware should be treated as a matter of national security and government should provide more help to private companies defend themselves from ransomware moving forward. Ransomeware attack will continue to increase. Government and companies should work closer together to fight against ransomware and they should invest more money and time on cybersecurity. Ransomware is not only problem for comapnies but it is everyone’s problem, since everyone can be a victim of ransomware nowdays. Government need to educate companies, organizations, and individuals in order to minimize damages from ransomware attacks.
Nice post! Although ransomware is one of the most common cyber attacks, its damage should be held as a breach of national security. As a movie fan, I am more familiar with single and double extortion, but I had never thought there would be a quadruple one. To reach out to stakeholders and customers and ask for ransom, how bold would the hacker be? It makes me curious what kind of confidential and sensitive information they have to pay for. In a quadruple attack, not only does it cause financial damage, but also reputation damage, since customers are hacked and the company cannot cover up the incident from the media.
Good Post! I am intrigued (and a little scared) by the quadruple extortion attack. If I have this right, if successful the attack: prevents organizations from accessing their own sensitive information, threatens to reveal the captured information, fires a DDos attack, and reaches out to stakeholders and customers threatening to reveal their information. If successful, the combination and execution of these methods is quite a scary possibility and I would not blame any organization for paying the requested random (however costly) in order to have their information freed. This is not even including the losses (potentially great ones) incurred from the loss of access to sensitive information (I’m thinking of bank accounts and databases specifically), not to mention the PR disaster and loss of trust as a result of consumers being contacted (as another commenter mentioned). Altogether these types of attacks can be devastating and I agree that learning how to defend against them is a serious priority.
Thanks for your informative post! It seems single and double extortion ransomware may still threaten triple or quadruple level extortion. With ransomware attacks on the rise, anyone can become a victim, including small businesses and IT service providers as well as major corporations.
Great post! It is quite unsettling how 83% of successful ransomware attacks were double or triple extortion attacks, as it will surely become the new standard for attacks like these. Your link to the Canadian Centre for Cyber Security provides a lot of informative information regarding ransomware provision and recovery. I wonder how (or if) antivirus software will develop to better defend and defeat these ever evolving attacks.
Really interesting post! All the more reason for people to understand that you should never give in to what ransomware is demanding. If they encrypted your files once, and all you have is their word that they won’t do it again, then you probably shouldn’t be surprised when they encrypt your files again and demand more things to squeeze you for money.
This post brings up an interesting and disturbing trend in cyberattacks that I did not know about: now, cyberattacker are targeting multiple stakeholders in a single attack. This strategy is frightening because large organizations have many stakeholders. A tech company has its consumers, its suppliers, etc. They could all be targeted by a sufficiently sophisticated attack.
It’ll be interesting to see how these attacks progress and what effect these developments have on the attack’s success. Personally, I’ve never seen a three-layer attack before, but it makes sense why you’d do so. Denying services has an impact on both the owners and users of the service, and can result in severe financial loss for both sides. The 4 layer assault is the most dangerous since it is nearly hard to tell your users that your security is adequate when they are individually contacted by parties who have already shown otherwise. Not only would this have a financial impact on the victim of the attack, but it will also raise issues about the legitimacy of the services being given to the client, perhaps jeopardising their purchase. Great work.
Great post! This was very informative. I remember when I was in elementary my family computer had a ransomware and it totally shut everything down with our little knowledge of computers then. Now if you had multiple layers it would be difficult for even experts to retrieve their data.