Cyclops Blink is a malware developed by the Sandworm Group that sets up a botnet by attacking Network Devices. It is the more advanced framework the group, that is affiliated with the Russian Government, deployed in June 2019 after their VPNFilter malware got exposed. Cyclops Blink mostly targeted network devices by WatchGuard (a network security vendor) but Sandworm Group is considered to be capable of adapting the malware for other architectures and firmware.

Who are Sandworm Group?
Sandworm Group, also known as Voodoo Bear, is a hacker group that is considered to be working for the Russian Government. The group has been active since at least 2008 and has been known to target Ukrainian companies and government agencies. One of their most famous actions was the BlackEnergy disruption in 2015, where they targeted electrical utilities in the Ukraine, thereby destroying entire networks and causing power outages. Furthermore, right before the recent Russian Invasion in Ukraine the group attacked multiple Ukrainian bank and government websites with Distributed Denial of Service (DDoS) attacks, leading to approximately 70 websites crashing and the Ukrainian IT infrastructure being compromised.
History of Cyclops Blink
Before deploying Cyclops Blink, Sandworm Group was using the so called VPNFilter malware that got exposed in 2018 by Cisco. VPNFilter attacked small office/home office (SOHO) network devices and network attached storage (NAS) and enabled monitoring of the Modbus SCADA protocol, which is often seen with Sandworm Group’s attacks. The malware had no specific target apart from a spike in activity in Ukraine in May 2018 and ever since its exposure the activity has significantly decreased as the hacker group started focusing on the development of the newer framework, Cyclops Blink.
How is Cyclops Blink distributed?
Cyclops Blink is installed as a fake firmware update and thereby achieves persistence to reboots or legitimate firmware updates, therefore once installed extra steps are necessary to get rid of the malware. The (most commonly targeted) WatchGuard appliances are only vulnerable if they were manually configured to allow unrestricted management from across the internet. This obviously always poses a security risk and is therefore disabled in the default settings. WatchGuard published guidance on their website on how to detect and remove the malware and patched the vulnerability in May 2021, after an estimated 1% of their devices were affected.
What does it do?
Once installed, Cyclops Blink can enable files to be downloaded and executed using the Linux API (Unix Shell) and in order to remain undetected the program poses as a Linux Kernel Thread Process. The malware can also add new modules while it is running, which allows for some additional capability to be implemented during runtime, as needed. Furthermore, the infiltrated device itself might not be the main target of the attack but can be used to conduct attacks on others.
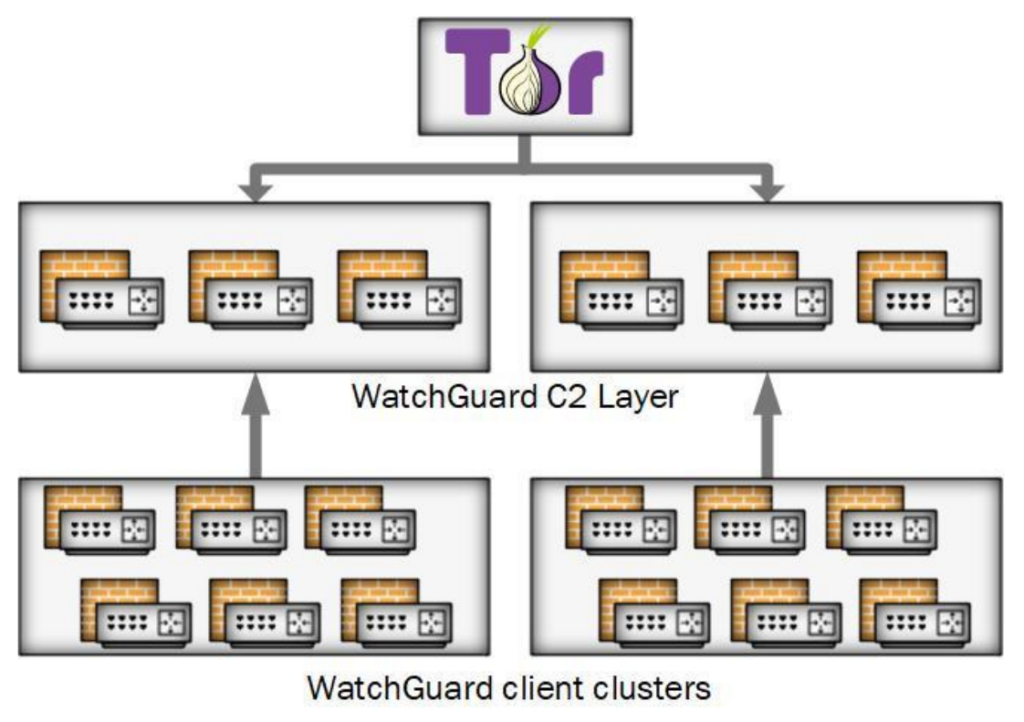
The affected devices are organized into clusters and each device has a list of IPv4 addresses and port numbers for command and control (C2) communication. The device randomly selects a C2 server from the list and beacons device information to the server, this communication is enabled by a modification of the Linux system firewall. Communication between the clients and servers is protected under Transport Layer Security (TLS) with individual keys and certificates, that are encrypted with the AES-256-CBC standard. Then Sandworm Group manages the botnet by connecting to the C2 server layer through the Tor network.
With the current geopolitical situation in Ukraine, this is an important topic to watch, as the importance of Cyberwar has significantly increased in the past years and similar attacks are likely to happen more often. High awareness is highly recommended!
References:
[1] https://blog.malwarebytes.com/threat-spotlight/2022/02/cyclops-blink-malware-us-and-uk-authorities-issue-alert/
[2] https://www.watchguard.com/wgrd-news/blog/important-detection-and-remediation-actions-cyclops-blink-state-sponsored-botnet
[3] https://www.ncsc.gov.uk/files/Cyclops-Blink-Malware-Analysis-Report.pdf
[4] https://www.cisa.gov/sites/default/files/publications/AA22-054A%20New%20Sandworm%20Malware%20Cyclops%20Blink%20Replaces%20VPN%20Filter.pdf
[5] http://blog.talosintelligence.com/2022/02/threat-advisory-cyclops-blink.html

Crazy to see that a known attack route/vulnerability took nearly 3 years to patch. While this attack doesn’t look too scary on the surface it definitely poses the ability to be a very threatening attack. The ability to download files remotely onto devices connected via the network and deploy the malware in stages with the ability to execute changes live is frightening. This type of attack has the ability to infect a large amount of devices (despite the option being disabled by default) and do quite a bit of damage. Curious to see how attacks like these will play out in the future.
This post was very interesting. Issues relating to information security can have direct connection to political agendas. It is important for companies such as WatchGuard to constantly monitor their equipment for any vulnerabilities and attacks. Networking equipment in particular are common targets and WatchGuard did a good job of promptly communicating the information to its users and patching the vulnerability. In times of political crisis, there should be more money invested into securing information systems in the affected areas (e.g Ukraine) as malware like this can have devastating impacts on a country’s sovereignty.
Good Post! It is quite fascinating to know that there are “hacker groups” that are generally known to work for sovereign governments (although I doubt they would ever admit it), that deploy illegal cyberattacks against the software infrastructure of other nations. You mentioned that the Sandworm group attacked multiple Ukrainian bank and government websites with DDoS attacks, resulting in 70 websites going down and Ukrainian IT infrastructure being compromised. It is interesting (and kind of scary) to see that these attacks have literally taken down parts of essential Ukrainian infrastructures. The timing and severity of these attacks (along with the group’s soft association with the Russian government) points to these attacks being part of the Russian offensive against Ukraine. I am also curious to see how these attacks will be implemented in the future (as a previous commenter put it).
Great post! With the conflict going on between Russia and Ukraine, it wouldn’t be surprising if that hacker group is associating with the Russian Government. It is scary to think about how these hacker groups are attacking essential services that Ukrainians rely on. The use of malware can be very harmful, especially if essential services are being targeted.
Great post! With the conflict going on between Russia and Ukraine, it wouldn’t be surprising if that hacker group is associating with the Russian Government. It is scary to think about how these hacker groups are attacking essential services that Ukrainians rely on. The use of malware can be very harmful, especially if essential services are being targeted.
I always found botnets interesting, because while having more devices running your bots is obviously beneficial, actually acquiring these devices can pose the issues of cost, energy needs, storage. If an actor already plans on using said devices maliciously, it feels almost perfect to hijack some devices instead of actually buying or building them. As soon as I read that this malware is installed through a false firmware update, my thought was that it has to be a pain to remove. Not only that, but unlike some malware that threatens an individual or could potentially be extremely harmful, Cyclops Blink has already demonstrated it has the potential to cause major damage to a country’s infrastructure.
Russian hacking is not a new topic, but with the recent escalation of the Russia-Ukraine conflict, it becomes even more relevant. Tools that have already been successfully used in a cyberattack against Ukraine warrant a lot of extra caution.
Russia sure has cornered the market on cyber espionage and cyber attacks. With the recent conflict with Ukraine, I would not be surprised if a variation or an improved version of this device came out. After reading your post, the malware appears to be very dangerous and if used effectively, it could result in untold damage to the Western economy and its people. I think the West needs to step up its cybersecurity and protect its citizens with much more fervour than usual. Also, the fact that the malware can take over a computer and download files is a cause for concern as well.
How effective is a fake firmware update though? Would you not need to trick someone into thinking they need it, meaning that anyone who is tech-savvy (and therefore has any valuable tech) wouldn’t fall for it? Obviously this is just a precursor to more powerful malware, as even if the infected devices are just used to attack other devices, I doubt enough devices would be infected to perform a botnet attack. Maybe I’m not seeing the whole picture, but I assume they made it a fake firmware update simply because accessing the firmware allows them to do these more powerful attacks, which in turn means it is more difficult to infect devices.
How effective is a fake firmware update though? Would you not need to trick someone into thinking they need it, meaning that anyone who is tech-savvy (and therefore has any valuable tech) wouldn’t fall for it? Obviously this is just a precursor to more powerful malware, as even if the infected devices are just used to attack other devices, I doubt enough devices would be infected to perform a botnet attack. Maybe I’m not seeing the whole picture, but I assume they made it a fake firmware update simply because accessing the firmware allows them to do these more powerful attacks, which in turn means it is more difficult to infect devices.
Sorry for making 6 comments, when I pressed post comment, it seemed like nothing happened, so I thought maybe it didn’t go through.
How effective is a fake firmware update though? Would you not need to trick someone into thinking they need it, meaning that anyone who is tech-savvy (and therefore has any valuable tech) wouldn’t fall for it? Obviously this is just a precursor to more powerful malware, as even if the infected devices are just used to attack other devices, I doubt enough devices would be infected to perform a botnet attack. Maybe I’m not seeing the whole picture, but I assume they made it a fake firmware update simply because accessing the firmware allows them to do these more powerful attacks, which in turn means it is more difficult to infect devices.
How effective is a fake firmware update though? Would you not need to trick someone into thinking they need it, meaning that anyone who is tech-savvy (and therefore has any valuable tech) wouldn’t fall for it? Obviously this is just a precursor to more powerful malware, as even if the infected devices are just used to attack other devices, I doubt enough devices would be infected to perform a botnet attack. Maybe I’m not seeing the whole picture, but I assume they made it a fake firmware update simply because accessing the firmware allows them to do these more powerful attacks, which in turn means it is more difficult to infect devices.
How effective is a fake firmware update though? Would you not need to trick someone into thinking they need it, meaning that anyone who is tech-savvy (and therefore has any valuable tech) wouldn’t fall for it? Obviously this is just a precursor to more powerful malware, as even if the infected devices are just used to attack other devices, I doubt enough devices would be infected to perform a botnet attack. Maybe I’m not seeing the whole picture, but I assume they made it a fake firmware update simply because accessing the firmware allows them to do these more powerful attacks, which in turn means it is more difficult to infect devices.
How effective is a fake firmware update though? Would you not need to trick someone into thinking they need it, meaning that anyone who is tech-savvy (and therefore has any valuable tech) wouldn’t fall for it? Obviously this is just a precursor to more powerful malware, as even if the infected devices are just used to attack other devices, I doubt enough devices would be infected to perform a botnet attack. Maybe I’m not seeing the whole picture, but I assume they made it a fake firmware update simply because accessing the firmware allows them to do these more powerful attacks, which in turn means it is more difficult to infect devices.
Nice Post ! Some types of malware contain files commonly identified as Trojan viruses. Others leave your computer vulnerable to viruses. Regardless of type, malware is notorious for being at the root, whether directly or indirectly, of virus infection, causing conflicts with legitimate software and compromising the security of any operating system, Windows or Macintosh.