DDoS attacks have always been a problem in the past, and to no one’s surprise, are still a big problem today. Recently, hackers have begun to amplify their DDoS attacks by weaponizing TCP Middlebox Reflections. This made it easier for hackers to do a lot more damage using DDoS attacks, causing lots of problems for tech companies.
What is a DDoS attack?
A distributed denial-of-service (DDoS) attack is a method used by cybercriminals to slow down or stop networks from operating. This is done by flooding a network with malicious traffic to the point that it cannot operate normally. DDoS attacks are usually used to stop people from being able to use a website, causing problems for both the owner and users of the website.
What is a Middlebox and TCP?
Before talking about why weaponizing TCP middle box reflections is such a big deal, lets take a look at what it is exactly. A middlebox is a device that is in between two communicating end hosts. It is used to inspect, filter, and transform packet streams being transported. Middleboxes are widely used all over the world, and often used by countries who wish to censor the internet. Transmission Control Protocol (TCP) is used to organize data such that there is a secure transmission between a server and a client.
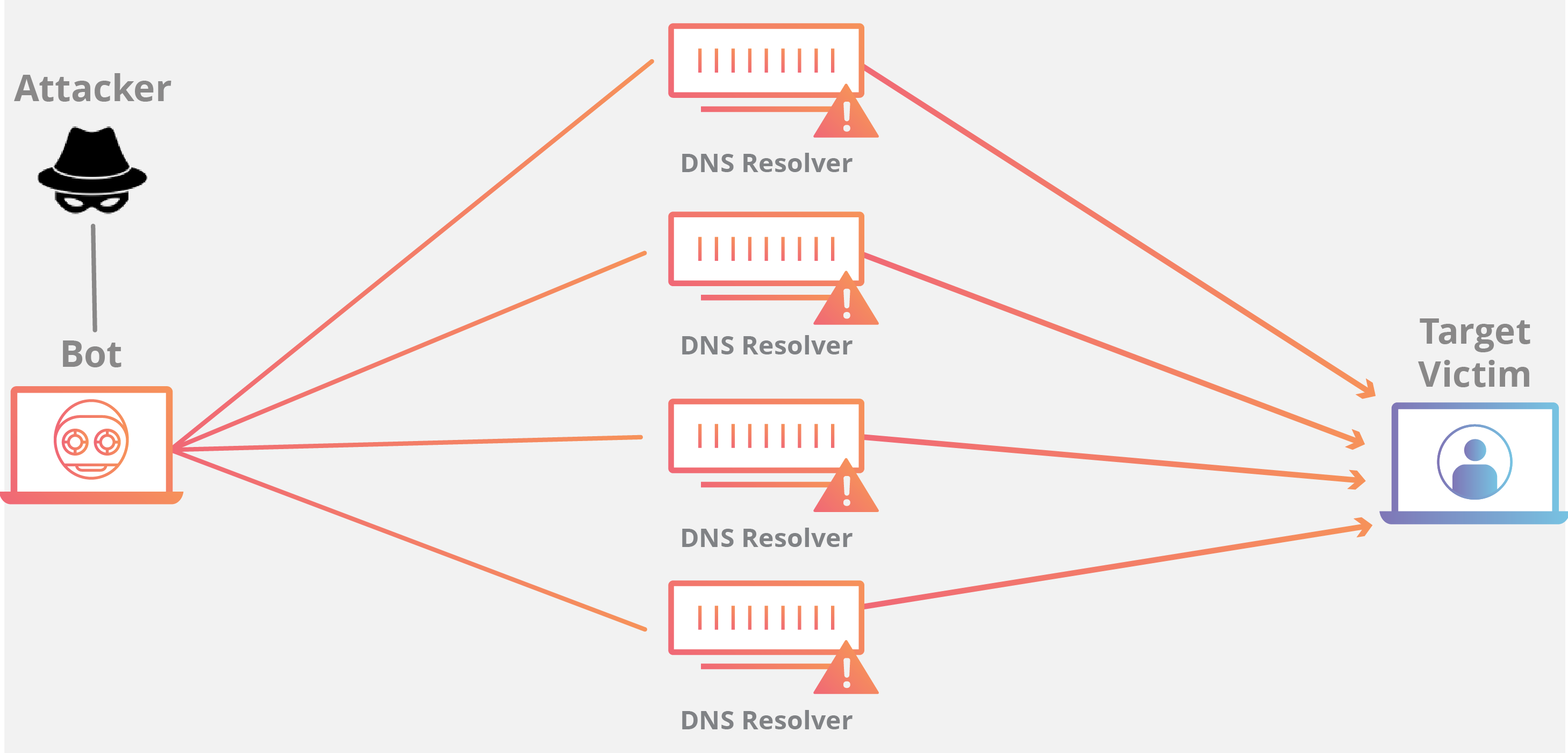
How are TCP Middlebox Reflections being used to attack?
TCP Middlebox Reflections are being used to abuse the Middlebox filtering system, and reflect traffic created by the Middlebox to a victim. The way that these attacks work is that an attacker sends requests containing an IP spoofed as the target victim to a server. The request is usually an HTTP address for blocked content. When the request reaches the middlebox, usually the connection would be blocked, however, many middlebox systems don’t take into account TCP streams when filtering content. Because they don’t take TCP streams into account, when a request is received through a TCP stream that would normally be blocked, the middlebox assumes that some packets got through. In order to prevent the user from accessing the restricted content that was not blocked, the middlebox will flood the client’s browser to prevent the user from getting to the restricted content. Since the attacker spoofed the IP on the request as the IP of a victim, all of the traffic is reflected to the victim’s browser, hence the use of reflection in the name. The middlebox floods the victims address in an amplified way that causes all the bandwidth to be exhausted. This is the reason that the attack can be so detrimental.
Researchers from Akamai claim that “This type of attack dangerously lowers the bar for DDoS attacks, as the attacker needs as little as 1/75th (in some cases) the amount of bandwidth from a volumetric standpoint.” This shows how much easier it is to DDoS using a TCP middlebox reflection than other methods such as a UDP attack.
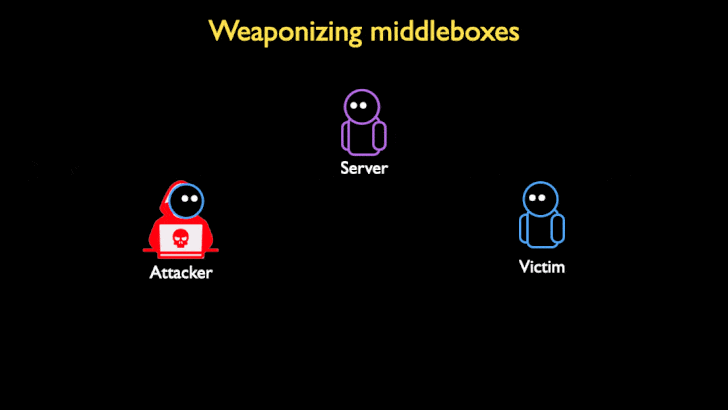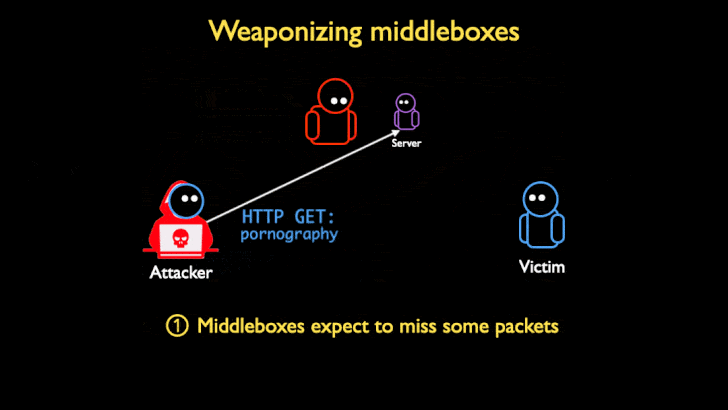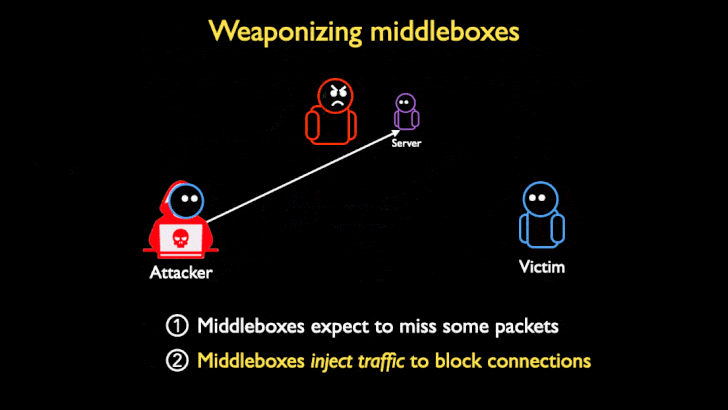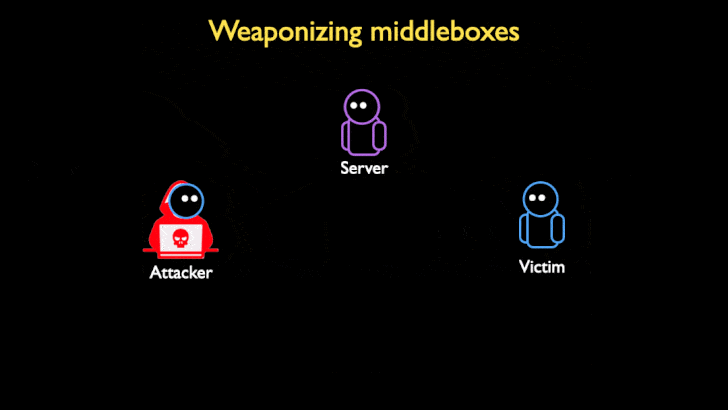
Who is being targeted, and how can it be stopped?
While there have not been many observed attacks, researchers believe that the number of attacks using a TCP middlebox reflection are going to greatly increase since these attacks are easy and effective. In the past few days, the main targets for this attack so far have been against banks, medias, and web-hosting companies, however, this list is likely to increase in the future.
There are many methods that could be used to stop this type of attack, such as removing all censorship of the internet everywhere. However, that might not be the most practical method (although I’m sure many people would like that). Some more realistic ways to mitigate attacks would be to use methods like anti-spoofing. That way, the middlebox would not flood the browser of the victim associated to the spoofed IP, since the spoof will get removed. Other DDoS mitigation methods can also be used since, although new, this is still a DDoS attack, so using specially designed networks to counteract DDoS attacks can be helpful.
References:
https://thehackernews.com/2022/03/hackers-begin-weaponizing-tcp-middlebox.html
https://www.akamai.com/blog/security/tcp-middlebox-reflection
https://usa.kaspersky.com/resource-center/preemptive-safety/how-does-ddos-attack-work

Interesting concept! It’s like an attacker is able to temporarily take hold of all of the bandwidth power of the server, equivalent to a botnet, without needing to go through the process of actually setting up a botnet. I wonder if attack amplification methods like these might actually bring up discussion around reducing the usage of internet censorship inside of organizations to make them less susceptible to DDoS attacks?
Good post! This is actually quite interesting, as I have heard people use the term “DDos attack” before and they have claimed that these attacks can be (and are) very damaging, but I never quite understood how these attacks worked under the hood until now. If I have this right: The attack works by the
attacker effectively mimicking and using a targets IP to send a large number of requests for blocked content to the server; the server receives them and assumes that some requests went through (due to the large number of requests) and then responds by blocking server access to the mimicked IP, effectively flooding the server and restricting access for the real user of the mimicked IP?
Thanks for your comment Jeremy. What you said is pretty much right, but for this specific type of DDoS attack, instead of just blocking server access to the mimicked IP, they flood the mimicked IP’s network with traffic to stop them from accessing restricted content, since some of the requests went through and it would be too late to block them. They basically said “if we can’t block you from having it, we will just overload your entire network so you can’t see anything”
This post was really cool to read. I never played too many video games growing up, however I remember a story from my cousin when he said someone had DDoS’ed him during a multiplayer video game. While I never really understood what it meant, your post brought up a memory from a long time ago and helped clarify what happened back then. DDoSing sounds like a very powerful tool to target individuals, and it unfortunate that there are those who use it for personal reasons. It is also interesting to see you mention removing all censorship to help prevent these attacks, as I think it would be cool to see the results of this.
Great post! I never really grasped what DDos meant despite hearing the term itself multiple times, but this post has clearly outlined a type of DDos attack. What’s interesting is that a Middlebox is being used to amplify this attack making it more dangerous along with harsh consequences. I’m curious to see how these attacks can be further prevented in the future.
I still remember when a DDoS attack could be performed from a command prompt in hopes of taking down a school’s wifi. However, I did not realize that such advancements have been made to the technology and roadblock that have been added to make a DDoS attack much more complicated. Nonetheless, after reading your post I realized that the simple attacks are getting much more lethal and more has to be done to prevent any future occurance
So from what I gathered from this post, Middleboxes are used by countries to censor the internet, but by using TCP you can easily bypass them. So, in retaliation, the middlebox “floods” the user with information. I suppose then the best way to counteract this from being abused by DDoS cyberattacks, is by replacing middleboxes with something that works better, either by being able to stop TCPs, or simply having a different solution to TCPs than flooding users. I think it’s rather interesting that such a solution to TCPs would’ve been used in the first place!
Good post. I never knew what a DDOS attack actually was, even though I’ve heard the term being thrown around. From what I understand, it appears that the middlebox is attempting to fix its supposed mistakes, and in turn, bombards the victim so they can’t access the “restricted” information. I believe that TCP is slower and less common than UDP, and in this case the attackers were able to use that fact to their advantage, simply by using TCP streams to send the infomation
Informative post! This is the first time I’ve read about DDos attacks explained. If I am understanding this right the attacker uses what is supposed to help and protect to bombard ultimately tricking and putting it against the victim. It’s a really interesting concept, I always find it so fascinating that people take out the time to find new ways of hacking in. Maybe it’s just the way I think but if they spent just as much time creating successful prevention software with their skills they could go so far in the field. I know there are IT specialists at all the places you mentioned are being attacked but maybe we need to put more focus or manpower in security.
Good Post! The attack abuses vulnerable firewalls and content filtering systems to reflect and amplify TCP traffic to a victim machine, creating a powerful DDoS.
Interesting post! This seems like a pretty obvious weak point in any network infrastructure. Is there any way for countries to actually get around this vulnerability if they want to keep their censorship alive, or is this just something that needs to be dealt with until middleboxes are replaced with something else?