What is homomorphic encryption?

Encryption is useful for communication when 3rd parties are present. A key pair(or sometimes one key) is used to encrypt and decrypt messages/information so that these malicious 3rd parties cannot read the information, or get any hints about what the information can contain. We still see developments in this field, from both attackers and defenders.
Homomorphic encryption is one type of encryption, it is not too common these days though. It allows for users to perform operations on the encrypted data without decrypting it. That is, after the information is encrypted into ciphertext, operations can be done on this ciphertext before decrypting it back into information. This limits the number of possible algorithms which is probably why it is not common; few effective methods exist. It does have useful applications though just because you do not need the key to decrypt the message if you want to change it.
What’s the problem?

Researchers from North Carolina State University and Dokuz Eylul University have found a way to gather information while it is being encrypted. They called it a first side channel attack. Essentially, they look at power consumption by the computers encrypting the data to gather clues about the data. They were able to fine tune their analysis until they were able to directly read all the encrypted data.
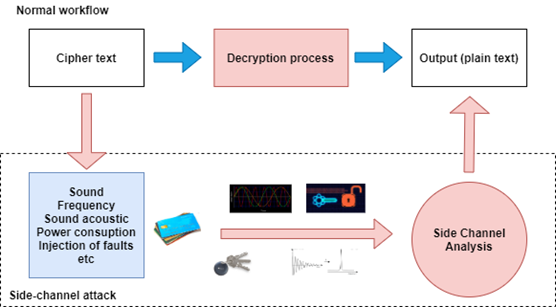
This is quite clever, because they are not directly looking at the encrypted data. With infinite possible keys that could encrypt a specific message into a specific ciphertext, it is quite difficult to get any information about the encrypted message by observing the ciphertext. However, looking at the power consumption of the encrypting device does tell you how many steps the algorithm takes, and diving deeper tells you when the algorithm takes the most steps. Since homomorphic encryption is limited in terms of possible algorithms, it is more vulnerable when any information about the algorithms are leaked. This type of attack could certainly help against other encryption methods too; it reveals some information and that’s all an attacker needs. As an attacker, you could combine a first side channel attack with another strategy, and the two combined might give enough info. Attackers can and will try anything.
Who is at risk?
The big companies are at risk here, because homomorphic encryption is most common when large databases are involved. This makes sense because it is not efficient to decrypt a large amount of information just to tweak it, homomorphic encryption is much faster. These companies will have to change something about their encryption practices, because they are huge targets with lots of cash on hand.
References
https://thehackernews.com/2022/03/researchers-demonstrate-new-side.html

I find it interesting that attackers are able to read encrypted data without manipulating the encrypted data at all.
In terms of our analogy that we discuss in class, Eve could uncover the contents of the box by standing outside Alice’s house. The amount of noise Alice makes and the amount of time Alice spends packing the box could help Eve reveal what’s in the box.
Wow very cool post. This reminds me of the Alice and Eve analogy discussed in class recently- If Eve can just shake the box to figure out what is inside, there is no need for Eve to obtain the key to the box.
The whole idea of the side-channel attack is really quite ingenious, props to those researchers for thinking of this and getting it to work.
Companies who use homomorphic encryption are now in a bit of a conundrum, as they must now double check that their systems are secure in light of this new possible attack, and possibly come up with new security solutions for their data.
It’s crazy to think that hackers are merely looking at power consumption to determine what’s going on inside these machines. I wonder what these companies will come up with instead of homomorphic encryption to protect their data.
Interesting to see the cat and mouse game that security personnel and attackers deal with on a daily basis. Every time a vulnerability gets fixed/patched and the security of a company tightens the attackers always seem to become more creative with the methods of attacks. This makes me wonder if it will ever be possible to have a truly secure system, especially considering patches/updates often will create new vulnerabilities while attempting to fix an old/current vulnerability. This attack also reminds me of an attack I had read about prior which utilized the vibrations of a PC fan to obtain confidential data on air-gapped computers.
It is kind of crazy to me how seemingly irrelevant details like power consumption can be used to attack a system. It almost seems like hacking regression in a sense; rather than using sophisticated computer techniques to bypass security, you can monitor physical changes to get an idea of what’s going on. Who knows, maybe a similar break could be done with a thermometer and observing PC temperature over time, it seems like the change in conditions is more telling than one might think.
I do wonder to what extent this can be protected against though. Unless I’m misunderstanding things, the breach is based on changes to the properties of the system to get data, and those properties don’t seem easy to prevent (although I guess you could just always be drawing more power than you need to mask things). I’m very curious to see what they come up from a defenders point of view.
Great post! it’s scary to see that hackers can see the data without encrypting it and can put us all at risk especially the big companies as they use homomorphic encryption and its easier for hackers to decrypt it and get into companies databases and exploit it so I hope these bug companies find another way to protect their data.
Interesting post! It’ll be interesting to see what big companies will do with their information now that it can be stolen without great effort. Something like power usage did not even occur to me as a way to track information and manipulation methods but hopefully security companies will be able to find a way to better protect data. I wonder if the power usage of the machines can somehow be masked and hidden to protect the data or if companies are going to have to abandon this style of encryption as a whole.
Good Post! It is very interesting (and rather impressive) to see that attackers need only look at a system’s power consumption to be able to breach it. The fact that large companies that use these types of vulnerable systems now know about this type of attack is good, and their response to these types of attacks is going to be interesting, as another commenter pointed out. Whether or not these companies are going to implement measures to mask the power usage of their systems is up for grabs (if a way to mask power consumption of systems like these can be made at all). And if the companies behind these systems do end up finding a way to close up this vulnerability, all any potential attackers need to do is bypass or breach the power masking system, and we’re back to square one.
Neat post! So in your opinion, is this form of encryption better/worse than other forms, or is it more a case of it being just another tool in the encryption toolbox, and different instead of better or worse.
Interesting post! This reminds me of something that was talked about in another cybersecurity course I took where if the algorithm that was being used to check a password was not efficient, and the more letters that the hacker has been able to guess correctly, then the longer it takes for the system to reject the password. Then with this, it would be easier for the hacker to brute force since they can funnel their guesses.
Thanks for sharing the post! It is scary to see that cyber-attackers only need the power consumption to hack into it. It is also impressive (well along with scary) that hackers have found more and more approach to break into a system.