A deadly banking virus was just identified, spreading through an apparently innocent-looking Android app, and if you are not aware of it, you are most likely a prospective victim of losing your own money. By posing as an antivirus software, the threat actor behind a fledgling Android banking malware known as SharkBot was able to get past Google Play Store security restrictions recently [1]. Researchers from the NCC Group issued a report earlier this week that detailed how SharkBot operates and how it was able to circumvent Play Store security protections.
What is SharkBot?
SharkBot is a malicious piece of malware that targets Android devices. SharkBot, like its malware cousins TeaBot, FluBot, and Oscorp (UBEL), belongs to a class of financial trojans capable of syphoning passwords and initiating money transfers from infected computers by bypassing multi-factor authentication methods. Therefore, the primary purpose of SharkBot is to gather and abuse financial data by deceptively diverting and starting money transactions from users’ devices [2]. In November 2021, it initially appeared on the scene, found by the Cleafy Threat Intelligence Team.

How does it work?
SharkBot, like other Android-targeting harmful apps, takes control of a smartphone by exploiting the operating system’s Accessibility Services. These features are designed to help in reading and interacting with the device. SharkBot obtains this level of control over compromised devices since the Android Accessibility Services encompass reading the screen (including written data) and simulating/interacting with the touchscreen. If Android Accessibility Services are not enabled, this virus shows pop-up windows asking permission to utilise these services on a constant basis. It can resume operations after being granted permission.

The malicious programme works as a three-tier poison pill, with one layer impersonating antivirus and the second layer impersonating a scaled-down version of SharkBot, which finally upgrades by downloading the full-fledged malware. That’s when it starts robbing victims’ bank accounts via a number of methods [3]. SharkBot differs from TeaBot in that it can carry out unlawful transactions through Automatic Transfer Systems (ATS), as opposed to TeaBot, which requires a human operator to interact with infected devices in order to carry out harmful operations.
“The ATS features allow the malware to receive a list of events to be simulated, and they will be simulated in order to do the money transfers. Since these features can be used to simulate touches/clicks and button presses, it can be used to not only automatically transfer money but also install other malicious applications or components.”
Alberto Segura and Rolf Govers, malware analysts at cybersecurity firm NCC Group, said in a report published last week [4].
SharkBot’s hidden techniques to get what it needs
SharkBot may steal banking credentials from Android users using one of the following methods, the majority of which need victims to activate Accessibility Permissions & Services [5] :
- Injections (overlay attack): When SharkBot detects that the legitimate banking app has been used, it can steal credentials by displaying a WebView with a false log in URL (phishing).
- Keylogging: By monitoring accessibility events (such as text field updates and button clicks) and forwarding these logs to the command-and-control server, Sharkbot may steal passwords (C2).
- SMS intercept: Sharkbot is capable of intercepting and hiding SMS messages..
- Remote control/ATS: Sharkbot has the capacity to take complete control of an Android smartphone through remote control (via Accessibility Services)
Wait, what is the name of the app spreading SharkBot?
One of most viral apps named Antivirus-Super Cleaner is found to be carrying SharkBot inside its operations. The current version of SharkBot, which was discovered on the Google Play Store on February 28, includes a number of dropper applications that use Android’s Direct Reply capabilities to spread to other devices, making it the second banking trojan to intercept notifications for wormable assaults after FluBot.
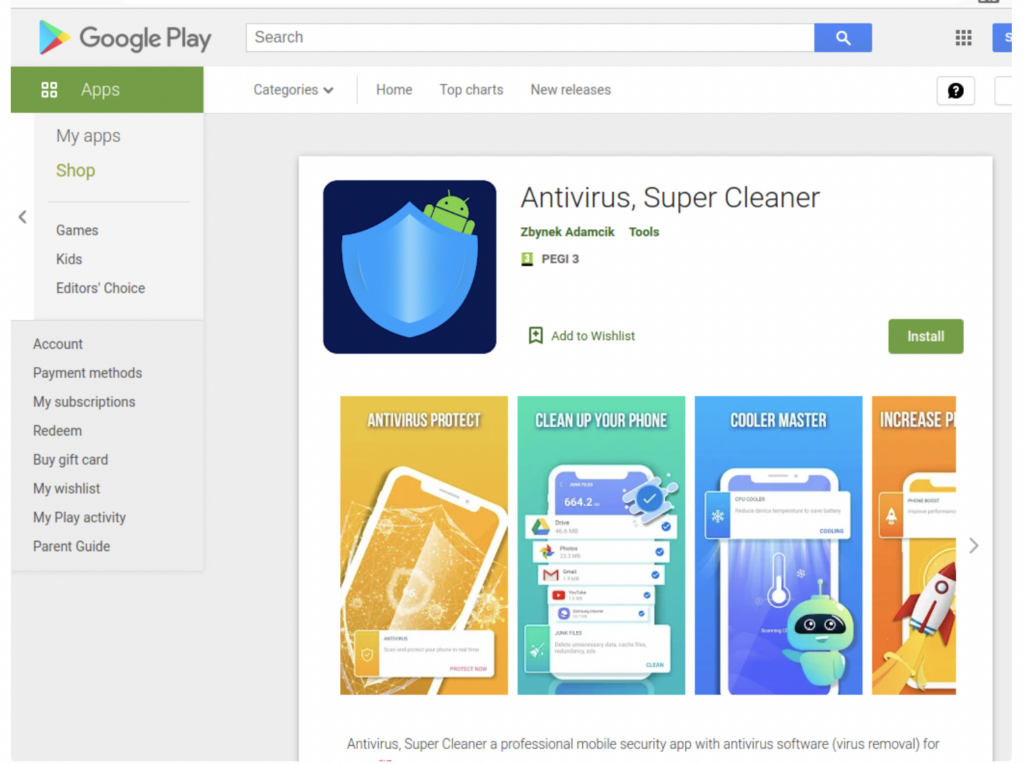
However, Antivirus, Super Cleaner is not the only app that spreads SharkBot as researchers found the following android apps that are highly suspicious of spreading SharkBot as well.
- Antivirus, Super Cleaner (com.abbondioendrizzi.antivirus.supercleaner) – 1,000+ installs
- Atom Clean-Booster, Antivirus (com.abbondioendrizzi.tools.supercleaner) – 500+ installs
- Alpha Antivirus, Cleaner (com.pagnotto28.sellsourcecode.alpha) – 5,000+ installs, and
- Powerful Cleaner, Antivirus (com.pagnotto28.sellsourcecode.supercleaner) – 50,000+ installs
How to protect yourself from installing this type of malware?
Well, if you are using an iOS device, you might have a slightly higher security built-in in the ecosystem. However, regardless of what OSs your device based on, you should always follow the recommendations below to be on the safe side.
- Download from official and verified sources only.
- All programmes should be enabled and updated using genuine tools received from authorised sources.
- Emails that are suspicious or irrelevant should not be opened.
- Install and keep up-to-date an anti-virus programme.
References
[1] https://thehackernews.com/2022/03/sharkbot-banking-malware-spreading-via.html
[2] https://www.pcrisk.com/removal-guides/22402-sharkbot-malware-android
[5] https://securityaffairs.co/wordpress/128765/malware/sharkbot-trojan-google-play.html

Thanks for letting us know! I personally don’t have an Android device, but something trying to track my banking information and transfer out my money is a scary thought. It’s worrying that more than 50,000 people have downloaded some variant of the fake antivirus software propagating SharkBot, and I hope that they are in the process of being removed from the store, if they haven’t been already.
Yes, exactly! People should be more aware of basic security concepts in information technology. That might reduces the victims considerably.
Thanks for sharing! I’m astounded that SharkBot was able to get through the security restrictions in Google’s Play Store. I also find it remarkable that SharkBot (along with other financial Trojans of its kind), is able to bypass multi-factor authentication methods (i.e., how you mentioned its capacity for intercepting SMS messages). This post is definitely going to change how I go about randomly downloading apps from the Play Store – I think its time for me to be more careful!
Yes! Although I don’t use an android device, still this news just demonstrates that there are malware out there that can even bypasses to get into the app stores regardless of android, iOS, or windows. So it’s time be more cautious when downloading apps randomly.
its ironic how an antivirus was the virus all along but its kinda scary how hard it is to identify and verify that apps are legitimate in this era. I hope that google will ramp up their protection of their play store with being able to identify malware before it gets posted for the general public and do some more routine cleaning so malware like this. Also, I didn’t know that malware like sharkbot could use injections, I thought that was a thing for like rootkits to do. It seems like the malware targeted people who wanted anti viruses with 4 of your listed apps being anti viruses. Does that mean anything significant? like does impersonating an antivirus give additional permissions? or are they targeting people wanting an antivirus on their phone? All in all thanks for sharing such an interesting article on malware.
In my opinion, we as users, at least most of us, get easily hooked by apps claiming that they clean out our devices from viruses, trojans, and perhaps speeding up our seemingly slow devices. The hackers take these thoughts into considerations while publishing an application that can potentially be downloaded many people and thus more chances to get the desired exploited informations from the users. These mentioned antivirus applications are such kinds of applications that are easily attracted by many android users. So I believe their primary intention is to get these malware installed to as many people’s phone as possible in order to perform the malicious activities mentioned.
Really interesting post! I am familiar with “Sharkbot”, and if I recall correctly, it was first identified by researchers in November 2021. It has been determined that Sharkbot is capable of stealing sensitive banking information, current balance, and even has the capability to perform gestures on an infected device. Sharkbot however, is distinct from likewise banking Trojans, in that it uses an Automatic Transfer System (ATS) technique to automate the process of stealing funds from a user’s account. ATS is an especially concerning process, as it affords attackers the ability to automatically fill in fields on an infected device with minimal human input. As a result, ATS allows Sharkbot to bypass biometric checks, behavioural analytics, and even multi-factor authentication. In addition, once the app has been installed, no icon will be displayed on the device, and consequently, Sharkbot is able to gain access to all necessary permissions due to the enabled Android Accessibility Service. Even when we believe our financial information is secure, due to the installation of small provisions such as multi-factor authentication and biometric checking in our banking applications, it really is not, thanks to the nefarious Sharkbot!
Yes, you are totally right! While SharkBot was initially identified in last November, the discovery of these SharkBot via android devices and in play store is recent, that SharkBot bypassed to the Google Play Store. And as latest as on Feb 28, several online news portals published a list of apps which are potentially spreading SharkBot, especially the one mentioned in the blog post. I believe it’s time for us, take serious cautions when installing random innocent looking apps. In fact, I think we should not install apps that we don’t use or are not necessary for us at all. In that way, we may reduce the chances of being victims via these types of malware.
Thank you for sharing your knowledge! SharkBot’s ability to get around the security constraints in Google’s Play Store astounds me. I also think it’s amazing that SharkBot (and other financial Trojans of its sort) can get beyond multi-factor authentication . This article will undoubtedly affect the way I approach downloading apps from the Play Store at random — I believe it is past time for me to be more cautious!
You are welcome! SharkBot’s ability is insane. However, if one has a basic sense of security, this type of malware can easily be avoided from installation or even giving the unnecessary –and suspicious–permissions to our devices when the apps prompt with access permissions. We should be always aware about what type of permissions an app is trying to get. If it seems suspicious, we should stop using and uninstall the app to be on safe side. At the end of the day, it’s us who is giving all the permissions to do such things. A partial responsibility is on us too, in my perspective.
Thanks for this informative post, Zaman! I found it interesting that hackers were able to use accessibility features on android phones to accomplish malicious tasks. This is quite clever. I’m always impressed at the creative approaches that hackers take to gaining elevated privileges. I’m also surprised that this was allowed onto the play store, and furthermore that 50, 000 people downloaded a variation of it! You would think that people would noticed that it’s a scam and leave a bad review of it. You would also think that Google would have better control over what it lets on to the app store. You can bet that I will only download the most trusted antivirus software on any of my devices!
Yes you are absolutely right! It’s interesting to me as well that how hackers are coming out with new tricks and approaches to hook people and perform malicious activities. Personally, the victims are mostly the people who do not have the minimum understanding of potential security breaches they might get into. I think it’s important now to educate mass people about the basics of information security to survive in this upcoming technology heavy world.
Terrifying malware you’re showing us here. The ability to disguise itself as an antivirus and use the Accessibility Services to remain completely undetectable while bypassing multi-factor authentication is very dangerous. Crazy that these programs source code is not reviewed more carefully, especially with numerous copies of the same attack being disguised as different applications. Hopefully the Play Store reviewers can handle applications like these in the future by tightening their security. Will be interesting to see how this advances as I’ve seen an increasing amount of attacks that are mass distributed via app stores.
I totally agree with you. And I think it is nothing new however that the Google’s lenient policy for publishing any application to the Play Store comes with a cost. That’s why I personally like the strategy of Apple. They will not let your application published in the apple store without some sort of rigorous scrutiny. I think Google should adopt this strategy too.
That was a fascinating post! I believe that malwares started to be everywhere as malware started to be hijacking your phone’s components in order to perform background tasks. It felt unsafe imagining that someone can track your bank account information and starts to do transactions and transfer money. I believe that people should start to be more secure and should be aware of security concepts. Overall, a very well-written post.
It is undoubtedly crazy! We should be more aware of what risks we are dealing with especially when installing a new application without verifying its popularity or originality. We should not be just installing any software/applications we find online. We must have a second thought before installing any softwares. It is a good approach to look for online reviews first before doing anything risky.
I find having an antivirus on a smart phone to be a little strange to begin with. I mean, phones these days are still computers, so theoretically I guess it’s possible to get a virus on a phone, but it just feels weird for some reason. I was born in 1992, so I didn’t have my first phone until I was about 16, and even then it was a flip phone with very limited functionality. So getting some sort of malware on *that* seems impossible, so that might be where my ignorance is coming from. But in addition to that, if someone were to install an antimalware app on their phone, wouldn’t they go with a trusted name such as Malwarebytes or Kaspersky? I guess that’s all to say I may just be giving people (read: the general public) more credit than they deserve. I’ll also say, working in a couple IT related jobs in the past few years may have made me a little jaded when it comes to trusting people and their technology, so I realize this entire opinion is probably a little biased, but time and time again I am surprised by people’s ignorance about basic cybersecurity safety. It’s tough to educate someone on basic safety when all they want is for their system to “just work”, a line I have heard multiple times.
Yes totally agreed! I think it just takes a little bit of caution to be on the same side. I personally don’t prefer anti-virus softwares to be honest, as I feel like Antrivirus softwares are sometimes the malwares. Technically it’s not possible to get malware if we simply follow the basic security concepts in our daily usage of smartphones. For example, not visiting any suspicious website, not downloading pirated copies of applications, etc.
This SharkBot smells fishy… (sorry). But jokes aside, it’s crazy that these trojans are hiding themselves as anti-virus software, and that they would even be allowed onto the play store without being properly verified first. The fact that the SharkBot can gain nearly full control over your device is very scary, especially since it only needs permission to use accessibility settings. I’ve personally made it a habit to not allow apps permission to various things on my phone, unless they are absolutely necessary (such as allowing access to your location for a gps app). One thing that I noticed is that the anti-virus that contains SharkBot tries to make itself look “legit” by putting the android logo on the front. So another way you can verify if something is fake or not is to check things such as the author, reviews, etc. to make sure that it is real and not a virus. Great post, thanks for sharing.
I do the same exactly. Especially I can’t stand for any applications that ask me to allow certain permissions which they don’t suppose to ask in order to provide their services. A ph0to editing applications, for example, asking for your contact list access permission seems very fishy to me. In this case, it is always better to avoid this kind of apps in order to save oneself from potential security threats.
Thanks for sharing this informative post! I believe this SharkBot trojan virus is only possible to attack android devices because it is an open source operating system. As an apple user myself I am glad that something like this cannot occur. I am shocked that such a dangerous app would be allowed on the Google Play Store without any kind of screening or verification. Great post!
I think it’s because of the easy-to-publish scheme for anybody on google play store without any scrutiny. In this case, apple users are indeed comparatively safer than android users.
Hi Zaman great post! Your post reminds me of another post where some gaming apps contain hidden malware. However SharkBot is more ironic as it disguises itself as an anti-virus whereas it is the source of virus. In my opinion, the submission standards for those app stores have been degraded significantly and the review board does not take it seriously anymore. They do not test it extensively and review every line of code, that’s why malware is able to hide. Additionally, as the younger generation, who do not understand the importance of cyber security, become the major consumers of digital media, a better security standard is required to protect them from malicious malware.
Totally agreed! Speaking about gaming apps, I think the cracked version of games are well known for being adulterated with malicious codes and acted as virus for quite a while now. But yes, the scrutiny standards should be a higher degree of importance now as we are going for the 4th industrial revolution which is primarily based on technology. If we want a better technological future, we must establish rigorous software validation before accepting for publication.
Thank you for sharing. The post tells us in detail that the financial Trojan SharkBot, disguised as anti-virus Android Software, crosses the security restrictions of the play store to collect and abuse the financial data on the device. This made me realize that malware can also appear in device stores. Moreover, it also spreads this malware in multiple applications, and its hiding technology poses a serious threat to users’ information and finance. I think it is very necessary to download the software carefully and use effective anti-virus software to check and kill viruses and Trojans. This reflects that the ability of the security restrictions of the software store is not strong enough. We need to constantly improve the security restrictions to prevent this malware and protect the network security of users.
I absolutely agreed! To avoid malware infection, we should think twice before clicking or downloading anything from web or App Store. As Google says, we understand how enticing it is to download that free video editing programme or role-playing game, but can you trust the website that provides it? Before downloading or installing anything, it’s sometimes a good idea to exit that website and look for reviews or information about that website or programme. Because downloads are one of the most common ways for people to receive malware, think hard about what you’re downloading and where you’re getting it from.
Very informative post! But at the end you said always download from trusted sources, but on Android, the Play store is meant to be a trusted source so how does a person avoid it on Android?
No not necessarily. As we found that the Play Store doesn’t seem to be checking the applications carefully before accepting for publication, we need to be aware that what applications we are downloading. if we have to download something, it’s better to check the reputation, users’ reviews, etc. of that particular application before downloading and/or installing to the device. By telling trusted source, I meant the developer and publisher of the applications, not the marketplace.
This was a really informative post. Well, I am glad I use an iPhone and I hope Sharkbot is never put into any of the apps on the appstore. I always make sure that all the apps I download from the App Store have good reviews. If there is any instance where another user has written that the app has messed with his or her personal information after downloading it, I am definitely staying away from that application. However, it is definitely intimidating that users secretly can get attacked (personal information attacks) when downloading an app from such platforms.
One important thing to check even if you download any apps from the Apple App Store is the permissions and the data collected by this applications and if there is any connection to link your identity. If you just simply scroll down of the app, you will find a section where Apple publishes some information such as data connected to your identity, and the data collected by this application, etc. This information is truly helpful to decide whether you should be aware of the application or not, even if it’s already verified by apple and thus available on the marketplace. I hope this helps to all of us.
It’s somewhat ironic to see an anti-virus contain an actual virus but I must say, hats off to the creators of the virus for thinking of such a method of deployment since most people would assume that they’re safe from viruses after downloading an anti-virus. Since anti-viruses generally ask for the accessibility permissions in order to screen your phone for malicious links and software this seems like the perfect trojan horse. Here’s to hoping that all the compromised devices belong to people who don’t use online banking on their phones.
To be honest, that’s why I can not trust anti-virus softwares most of the time. I mostly use the in-built defender available in my machine. In my perspective, I always thought that what if the anti-virus software download and use can start acting as the criminal here? And if they do, we will probably never be able to realize what’s going wrong in my machine. I think there is no reason to use any third party anti virus softwares and putting ourselves into risks, if we just simply follow some basic security techniques. We have to change the way we interact to any softwares/applications, otherwise we will always be a victim or scammed.
Good post! I am an Android user, so this blog has been very useful for me and anyone else here who uses Android. Before this post, I did always download apps that either had a lot of good reviews or other sorts that verify the app’s authenticity. At the end of the day, this does show that the company needs to prioritize beefing up its security features and review processes for apps in the Play Store to minimize these sorts of attacks. Has Samsung said anything in relation to this event that indicates they will be taking these issues more seriously?
Great to hear from you, William! I am not sure if Samsung said anything in relation to this event yet. As far as I believe is that the issues are only being identified and discussed across the scientific community, but no organizations building mobile phones that runs on android OS have not acknowledged anything yet. But I think they should acknowledge the event, and let their users know that they are taking appropriate actions. Otherwise, it will seem to be an obvious fact to their users and may thus impact the trust issues on their review processes from now on.
This is really an informative blog. There are now many cyber hackers stealing people’s private information through various means to achieve their goals. Spreading viruses, Trojans and worms is one of their main means. The thing that surprised me is that some antivirus software are potential vectors of viruses. If even software designed to fight viruses and ensure a secure network environment turns into malware, our last resort for using the Internet safely is to unplug it.
Totally agreed. In fact I think antivirus softwares should be verified by some sort of organizations before they can publish, especially because antivirus software requires literally every permission in users’ machine. So we may not never know what is going inside the antivirus softwares. Similar to digital signature generation and verification by reputed companies, anti-virus softwares should be verified as well. In this way, we may prevent any malicious publishers to publish their malicious antivirus softwares and also facilitate users to give enough information before they download and install them in their devices.
Good Post! As the owner of an older Samsung Galaxy model phone, I guess I should be on the lookout for applications like this. It is interesting to see that there is a whole class of malware programs specifically targeting financial software. The fact that we even have a whole class of programs specifies how lucrative and dangerous cyber attacks in the financial sector are. Even more frightening is the fact that these “bots” can bypass multi-factor authentication, a process that has so far been thought to have been relatively safe and has been seen as a necessary upgrade regarding security.
That’s a great post. I am ios user although i like more android to use because you can do whatever you want in this operating system. However, that’s where the security and privacy questions rises whatever we are able to do in android are those safe for us?