Conti, a well-known ransomware organization, declared support for Russia when it attacked Ukraine on February 25. It turned out to be a terrible idea: a vast collection of the gang’s secrets was disclosed just days later. The data includes information on hacking activities, the gang’s Bitcoin wallets, and speculation on the future of cryptocurrency as a money-laundering tool. Experts in ransomware are already combing over the data to learn more about the group’s internal activities. The files were translated into English by security researchers. In their statement, the leaker said, “Glory to Ukraine.”
The Conti ransomware dumps revealed exactly how profitable ransomware can be, with upwards of $2 billion placed in the group’s principal Bitcoin wallet in the previous two years. The disclosed data package contains about 400 files comprising tens of thousands of internal Conti group conversation logs in Russian. The files contain around a year’s worth of messages dating back to January 2021, almost six months after the group’s formation in mid-2020.
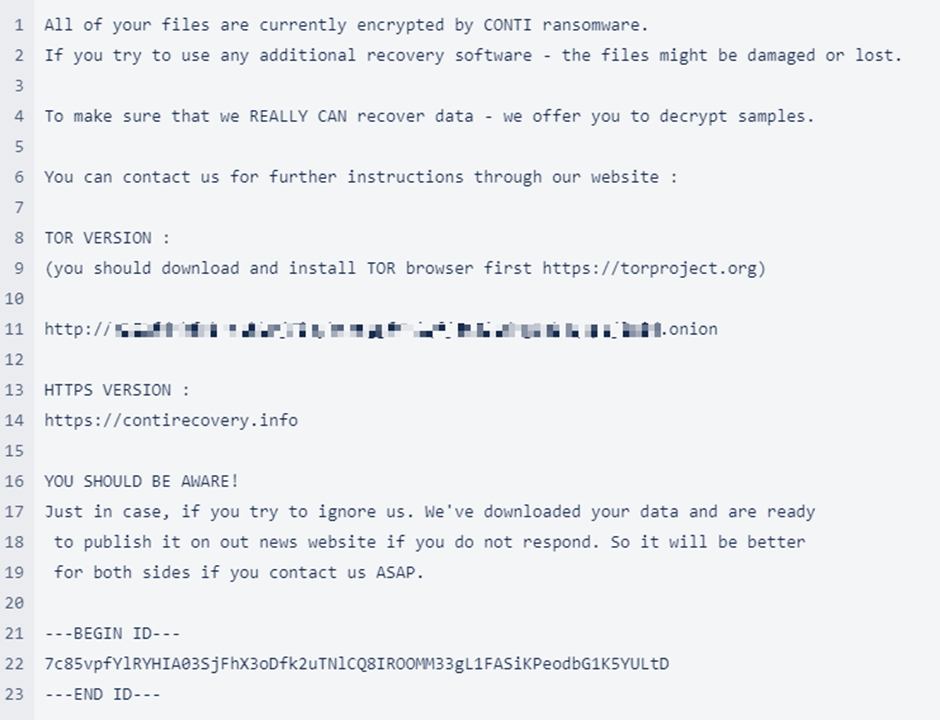
What is the Conti Ransomware?
In May of 2020, the Conti ransomware surfaced on the threat scene. It has several similarities to other ransomware families. Conti has evolved quickly since its discovery, and it’s notable for how quickly it encrypts and installs throughout a target system. Conti is a “double extortion” ransomware that takes and threatens to reveal data in addition to encrypting it. Ryuk ransomware that first appeared in 2018 was created by the same group. The group is known as Wizard Spider and is based in Saint Petersburg, Russia. According to experts, Conti is said to have links to Russian intelligence which allows affiliates to rent access to the company’s infrastructure in order to conduct attacks.
Previous thefts of Conti
Conti has been accused of launching ransomware attacks on scores of companies, like Shutterfly, as well as key infrastructures, such as emergency dispatch centers and first-responder networks. Conti took out the Irish healthcare system’s networks in May, prompting a state-wide suspension of IT systems that caused serious delays around the country and cost the government more than $100 million in recovery expenses.[5]
Ransomware can be lucrative
Ransomware is still prevalent for one simple reason: it’s profitable. It’s beneficial not just for ransomware producers (who are only one part of the equation), but for the whole network of participants that make up the ransomware economy.
Conti received $180 million in extortion payments last year, more than any other criminal organization. Conti was able to do things that average investors couldn’t, such as manipulate the price of cryptocurrencies in one direction or the other, thanks to his money. Building a cryptocurrency platform and seeding it with ill-gotten bitcoin from phantom investors is another option.[6]
What’s next?
Information security, state-sponsored hacking, ransomware, and malware have all been at the forefront of the Russia-Ukraine conflict, with hackers on both sides purportedly executing large-scale operations against their opponents’ infrastructure.
Experts are keeping a tight eye on both nations, fearful that a volatile situation involving one of the world’s most powerful hacking superpowers might spark a massive cyber fight that outlasts the physical clashes.
What to do immediately (if you have been hit with Conti):
To lessen the chance of being hacked by Conti ransomware, network defenders should implement the following mitigations, according to CISA, FBI, and NSA.
• Set up network segmentation and traffic filtering.
• Run a vulnerability scan and maintain your software up to date.
• Disable any programmes that aren’t essential and implement controls.
• Keep user accounts safe.
References
- What Is Conti Ransomware and Who Is Behind It? (heimdalsecurity.com)
- https://info.varonis.com/hsfs/hubfs/fig1.png?width=1202&name=fig1.png
- Ryuk (ransomware) – Wikipedia
- Shutterfly Hit With Conti Ransomware | PCMag
- Irish Healthcare System Requires More Than $100 Million To Recover From the Conti Ransomware Attack – CPO Magazine
- Conti Ransomware Group Diaries, Part IV: Cryptocrime – Krebs on Security
- Conti Ransomware | CISA


I wonder how this would affect other Russian based cybercriminal organizations since these organizations have members with citizens of both countries for example there was a Ukrainian member in REvil. in addition with the ongoing war in Ukraine this may cause a divide with other groups other than Conti. I liked how you mentioned that this could spark a cyber war the could outlast the actual conflict, as nationalism may cause a divide against Russian and Ukraine cybercriminals which if gotten into a prolonged conflict would most likely last longer as its easier to conduct a cyber war rather than a physical war. I wonder if this will cause a rise in ransomware groups targeting Russians as previously Ukrainian Cybercriminals would work with Russians and some of them would not target systems that were Russian, but potentially those Ukrainian cyber criminals could target Russians. This article shows how socio and political environments can affect the cybersecurity space and I was pleased to know that the Conti group received some form of karma.
Well, on my view , I would say this is good, because Ukraine need all the help they can get right now, and as always, the black hat hackers being hacked is something shocking because they expect themselves to be the best but they forget that there are people who are better than them. Great post, it is nice to keep on learning new things and knowing what goes on all over the world of ours.
Wow. Betrayed by one of their own, too. It’s interesting to see how deeply a conflict can influence a society, even going as far to build tensions and data dump a multi billion dollar hacking organization. With a lot of the larger hacking groups originating in Russia, I wonder what else will happen over the course of the war, or in the aftermath? Maybe we’ll get to see some major shifts occur in and around the hacking community. Hopefully the infighting amongst these groups leads to overall less outward attacks on innocent civilians.
Thanks for the interesting post. Those giant hacking organizations are multi-national, therefore it is impossible to truly understand the perspective of each member and keep them under control. With the Russian-Ukraine war going on, it is not surprising when nationalism kicks in among the members of those cybercriminal groups. The betrayal could cripple their organization and affect the hacking society, potentially leading to a much devastating attack in revenge. I just hope they can keep the civil war in the hacker community and not attempt to attack innocent people.
This is a very good post. As the war between Ukraine and Russia continues to develop, the battle has gradually shifted from reality to the internet. It’s not hard to imagine that the future war will not only destroy buildings on a physical level, but also use hacking techniques to destroy each other’s networks. As the war continues to develop, more and more companies are announcing the cessation of their activities in Russia, including many gaming companies. The Russian hackers responded by offering a pirated software website that provides 95% of the world’s games and software for free. Back to the cyber war, no one wants to live in a world full of cyber wars, everyone wants the world to remain peaceful, but how do we stop the war when it has already started? Private hacking of networks is obviously not a solution. Who can guarantee that these nationalistic hackers will not make the war more and more complicated by their actions? My thought is that we should do our part to stop the war and let both sides negotiate at the table, rather than using force or hacking to try to make the war more and more intense.
Very interesting post! I knew ransomeware was profitable, but I did not know that it was this profitable. But then again there were over 2000 thousand ransomeware attacks and they averaged $102 million per month.
Good Post! It is very interesting to see that even well-known groups such as Conti can have their data breached. I find it amusingly ironic that a group based around illegally obtaining and ransoming the data of others for profit has had their data broken into and released to the public. It is also rather shocking that such a group can be so successful (with 180 million dollars paid to them in the last year) and yet can be vulnerable to having their data leaked. As other commenters have mentioned, it is likely that the leaker was someone within the group and had the data released due to nationalistic reasons regarding the current war in Ukraine. This would make more sense than an outside group breaching and leaking the data, as an insider would have full access to the group’s documents, and the power to collect and release them.
Fascinating post. It’s incredible that one criminal organization could cause 100 million dollars in damage. If enough such attacks were launched on a government it would become bankrupt (or necessitate desperate, destabilizing measures in the target country). It could bankrupt a small-enough corporate much faster. There is one encouraging facet to this story: it is sometimes possible to appeal to the conscience/values of cybercriminals.
Good post! It is interesting to see what appears to be another war going on in the shadows of the cyber domain. This conflict appears to offer many new lessons to be learned regarding how these malicious groups initiate their attacks and what other activities they participate in. From this attack on Conti, it appears that they too can be vulnerable as well. Even though these guys initiated their own cyberattacks, they appear to have failed the basics of securing their own data. One would expect that a good attacker would have at least learned from their own experiences to adequately defend their own software and information.
The article raises a good point as well: Will this cyber conflict outlive the physical war? Perhaps, but it is hard to say. The Kremlin will have to deal with cyber groups that are vengeful to retaliate (those who it hires, and many in Ukraine seeking to retaliate against Putin and his minions). I am on the side that this cyber conflict may (unfortunately) outlive the physical war.
It’s rather entertaining to see cyber-crime group have their own information leaked, a sort of cruel irony in a way. Not entirely sure what the group was thinking making such a controversial statement, it’s only natural that at least one member didn’t agree with them and decided to sabotage them. We can only wait and see how this plays out. Ideally the situation will get defused soon, but chances are this conflict might play out longer than the actual physical conflict like you’ve mentioned. A very good post!
Ransomware does indeed seem to be profitable based on this. It’s nice to see that at least one member of the group seemed to have not agreed with their actions and led to the data leak, although it would’ve been funny if they got hit by a separate cyberattack instead that led to the leak. Just like previous blog posts on here reading stuff like a ransomware attack taking out the whole Irish healthcare networks is quite scary and really puts into perspective what cyberattacks are capable of now and the damage they can cause. Wizard spider is also a great name.
The point you about the separate cyberattack is actually hilarious. I hope there are spies who somehow work for these cybercriminal groups only to expose them in the end. That would be pretty funny as well.
I guess I see why the developers who create these ransomware do these kind of malicious work to generate more profit, rather than just putting their skills to good use. I would always choose ethical ways of generating income instead of unethical ways (even if that way possibly might make more money). However, it’s funny to see the cybercriminal group’s own information got leaked like that.
Great post!