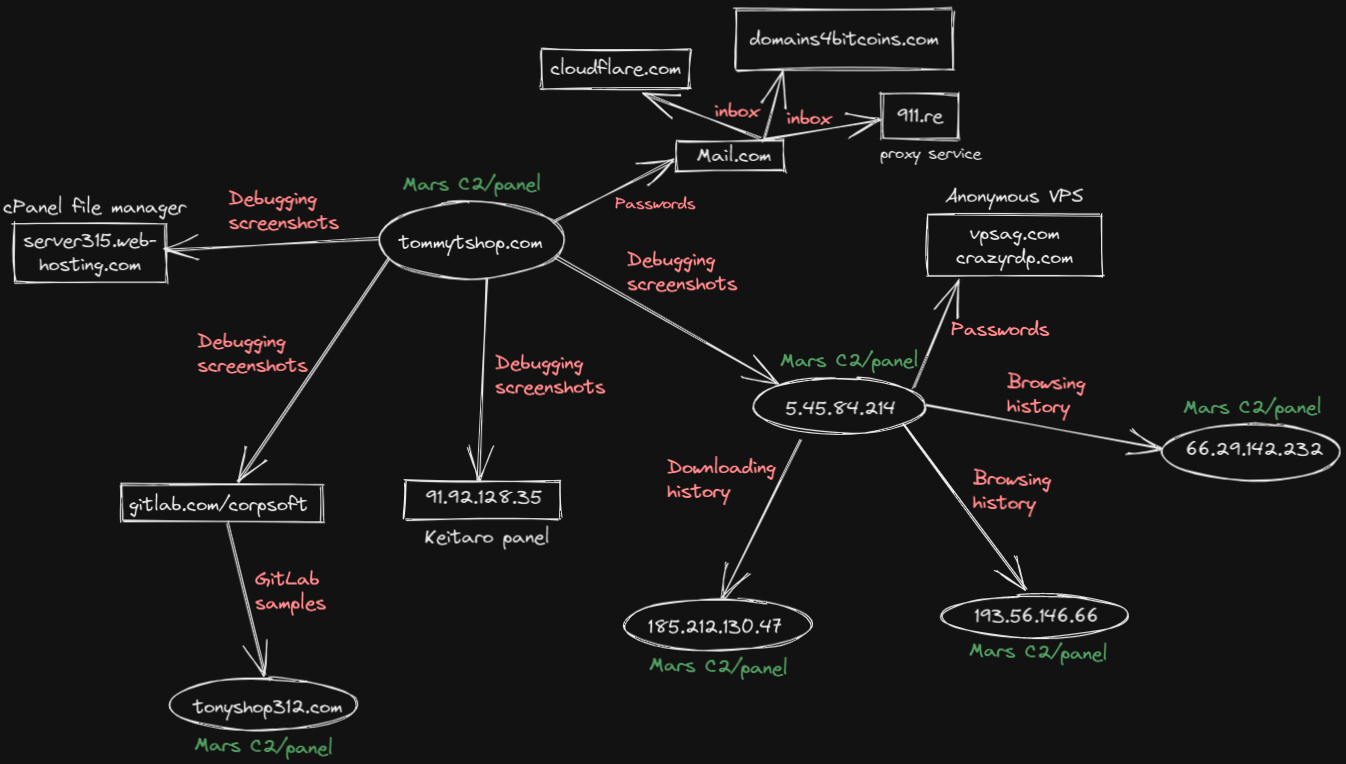
Source: Morphisec
Mars Stealer is a piece of off-the-shelf malware going for around 160$ for a lifetime subscription on various underground forums and dark web sites. It can steal information from your browser like cookies, autofill data, and credit card info. It can steal information about your computer or even attack your cryptocurrency wallets. Furthermore, depending on the customer’s intentions, it can be configured to download something else onto the infected machine, such as more malware.
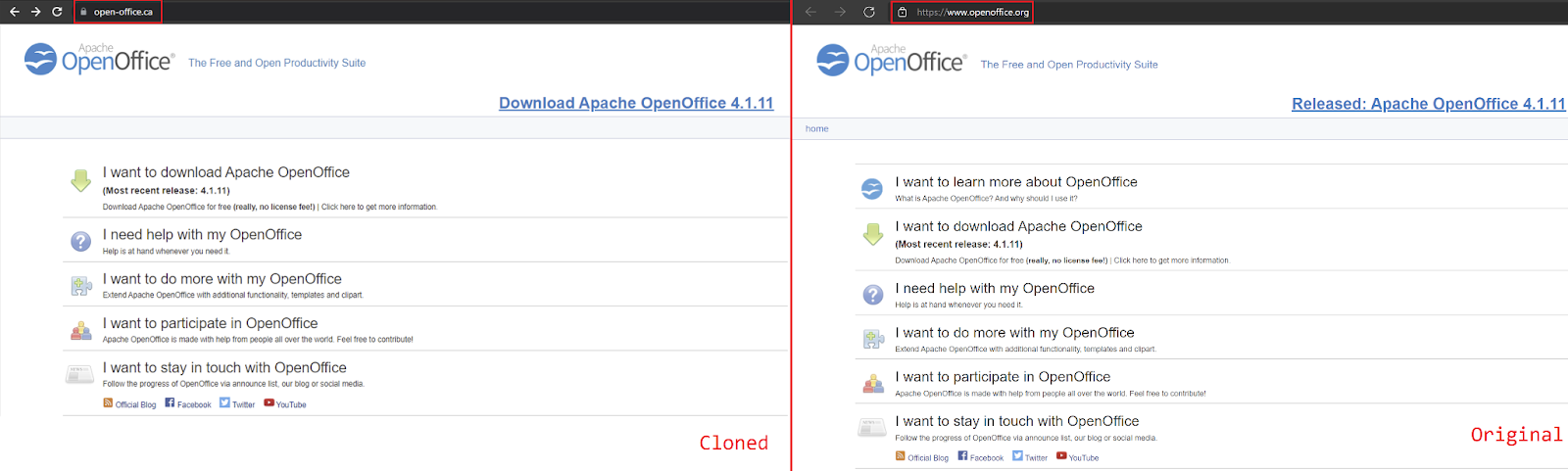
One particular attacker has set up clones of sites where you can download well-known software, and then used Google Ad Services to advertise these clones. When an unsuspecting user clicks on the ad, they are directed to this cloned site where their computer is infected with malware. The attacker is paying for these ads using stolen information, and using geographically targeted ads to target Canadians[2].
Source: Morphisec
Shortly after the latest version was released, someone released a cracked version with an instruction document. Fortunately, this guide contained flaws. These flaws lead to customers improperly setting up their environments, which made investigating Mars much easier for security researchers. Researchers were able to gleam a great deal of information about the abovementioned attacker because on top of being one of those individuals with an improperly set up environment, they managed to infect their own computer while debugging, so their information was found with all the victims’ info[2].
About Mars Stealer
Mars Stealer is an evolution of an older, no longer supported information stealer known as Oski Stealer, which had a thriving community of happy customers who left positive feedback on their experiences with this ‘product’ and the support provided by the team behind it before it abruptly stopped[3]. Mars is apparently still receiving updates.
This malware has two features I thought were particularly interesting. First, it will not attack a computer within the CIS (Confederacy of Independent States). It achieves this by checking the user language ID of the region format setting against a list of IDs corresponding to countries within the CIS, including Russia, Belarus, Kazakhstan, etc.[4] Second, it has a one month expiration date; it checks its own compile time and then compares this to the current time from the system, and if it was compiled more than one month ago, it exits.[4]
Obfuscation and Detection Evasion
Mars Stealer uses some interesting techniques to avoid detection by Windows Defender as well as some more savvy tech enthusiasts who might be checking for malware.
To confuse humans, Mars obfuscates its code by encrypting the strings used in the program and also by using run-time dynamic linking. This means it is necessary to decrypt the strings using the key stored in the program, and then resolve the libraries and functions it uses in order to be able to read the code easily[3]. Furthermore, it is able to detect when it is being run in debug mode by initiating a sleep for 15 seconds. After the sleep call, it checks how much time actually passed, and if it is less than 10 seconds, that (likely) means that the sleep was skipped by a debugger, and the program exits without executing any malicious code[4].
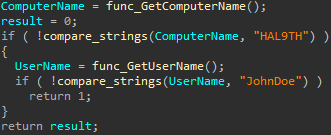
Mars also evades Windows Defender Emulation by checking the environment. Specifically, it checks whether the device name is ‘HAL9TH’ and the user is ‘JohnDoe’[4] and, as above, it immediately exits if it finds these indicators. While I appreciate the reference to the HAL 9000, there’s no way it’s this easy to beat Windows Defender, right? Right?!?(It is)
Source: 3xp0rt
On the plus side, I suppose we’ve learned that a good way to avoid being hit by malware would be to name your computer ‘HAL9TH’ and always use the username ‘JohnDoe’, thereby tricking any malware that checks for this emulator into not attacking you.
References
- https://thehackernews.com/2022/03/researchers-expose-mars-stealer-malware.html
- https://blog.morphisec.com/threat-research-mars-stealer
- https://www.cyberark.com/resources/threat-research-blog/meet-oski-stealer-an-in-depth-analysis-of-the-popular-credential-stealer
- https://3xp0rt.com/posts/mars-stealer
- https://i.blackhat.com/us-18/Thu-August-9/us-18-Bulazel-Windows-Offender-Reverse-Engineering-Windows-Defenders-Antivirus-Emulator.pdf

It has become really difficult nowadays to figure out which website is real and which actually is a clone, if we look closely of the photos of both the websites posted on the discussion above, both of them have https:, enabling them to have a safer connection, at the same time there are very less noticeable changes to monitor. Having control access of the website and using google ads for promotion, users will easily be convinced to click and this will be beneficial for the attackers. The last paragraph mentions about a possible way to not get detected by malware viruses, however there needs to be more sophisticated ways of preventing users data to be stolen.
Thanks for this informative post!
Hey, great post! It is interesting how people would rather find the cracked version of the software that hacks computers than personally go out of their way to buy it. I think the use of ads is a pretty innovative way of attacking a computer because it is a very straightforward way of infecting someone’s computer. I was wondering when the information first came out? because by now, I wouldn’t be surprised if the owners of the application are coming up with new ways of infecting computers. Additionally, I think the ‘good guys’ need to come up with an innovative way to subvert these attacks and to better protect users.
Great post! This really highlighted the lengths that malware goes to avoid being detected by common security measures. Who knew that all it took to avoid Windows Defender is just a few lines of code? That definitely sounds like something that needs to be addressed.
I found your article rather entertaining to read! It’s interesting how the attackers are using much more direct methods to get people infected i.e. through ads although I guess there is a bit of phishing at play here too. I enjoyed the information you gave regarding how the malware avoids being noticed, especially the bit about how easy it is to catch if the program is being run in a windows defender emulation state.
It’s kind of cool but also scary how malware gets bought and sold in the dark web. The world of malware as a service is truly an intriguing one.
Wonderful post! Most regular users usually try their best to avoid paying for software. Honestly, I would say this makes it so much easier for creators of malware such as Mars Stealer to achieve their goals. Of course, the laymen cannot differentiate between software clones or the real thing, especially if they just want to save money. Even though it’s a lifelong subscription, most people don’t want to pay this much. Now, someone looking on the dark web is sure to come across this sort of malware. I also want to add, that it’s notable that Mars Stealer can’t attack computers within the CIS; makes one wonder why this region isn’t targeted. The protection mechanism seems pretty simple but it wouldn’t be too hard for hackers to bypass this in the near future.
I wonder if any Malware is released on the dark web that targets malicious users as you said that people are buying these things for 160$. If maybe someone released a false malware for buyers interested in buying malware for malicious purposes, it may dissuade people to buy such items. Interestingly it seems that the ads on google are still pretty infested with malware as in the past I’ve seen ads on google with malware and ads that are phasing sites. It seems like the ad verifications are not up to par and seem too lax as they are actively promoting things that will harm their consumer base. I wonder if more attention will prompt google to respond as this issue had been going on for far too long.
Great post! Due to these sort of ‘products’ I am wary of using my devices for things such as online banking and other information sensitive actions, because the site I am using could be a clone, or I could accidentally click on something resulting in my information getting stolen. I’d rather go to a bank in person even though it takes more time.
One could probably determine that Mars is avoiding countries within the CIS because its creators are from one or more of these states. Considering that most of the people in these states share a common language (Russian) they could easily communicate, and thus collaborate on this piece of malware. Also, I do realize that Russian is not an official language in most of these countries, but the percentage of Russian speakers is quite high in most (https://www.babbel.com/en/magazine/how-many-people-speak-russian-and-where-spoken). Either way, it seems to be quite smart and the fact that it is getting constant updates is quite a bad sign for us. As it will surely get better at doing what it does. Overall great post!
Mars Stealer may easily threaten crypto extensions, including major wallets such as MetaMask, Nifty wallet, Coinbase wallet, Binance Chain Wallet, and Tron Link, as they are primarily targeting crypto projects. Except for Opera, the Malware targets extensions built on Chromium.
The good news is, if any, that the attackers have been using Google Ads to propagate the malware, which means much attention has likely been brought to the issue. I don’t think Google will take kindly to this misuse, and if anyone is capable of potentially locating the attacker(s), it’s Google. To add to this, the security team at Microsoft has also likely been notified of these developments, and are probably working hard on Windows Defender so that the malware cannot avoid detection. At some point I’m sure the signatures to avoid detection will be added to a known list.
Great post Riley, another reason to always be wary of what your downloading and where from. Especially when it is so easy to spoof a website now, and a simple typo in a domain name probably wouldn’t register for most people if the website looked the same and legit as the intended one. Crazy how easy it seemed to be able to get by windows defender, and also how it used something so prolific as googles ads to spread, isn’t that googles main business? Ads? How could they possible let this happen for the duration it had (or still going). Another reason to double check the little green lock on your web browser and always be careful of what is downloaded!
Good read! This is just another example of malware that can be avoided by not clicking on ads. It’s also interesting how the malware doesn’t target people from CIS countries, indicating that its founders are from these countries. One positive to take away is that this is done using google ads so the google team is definitely working on mitigating this issue. Overall, it’s best to stay safe and informed so that your privacy and security is maximized.
Cool post! It’s always great to read on more malware as it helps create more awareness so people can help avoid being attacked. It is very interesting that Google is allowing malicious people like this to make use of its AdSense and create more potential victims, as we would expect Google to be a step in the process which would help prevent this. I really liked how you mentioned how to avoid this by renaming your PC as well as the user name, but it is interesting to see that it does not affect many CIS regions. Maybe it is just a coincidence….
Very interesting post! Nowadays, most people choose free software or some software substitutes to save money. It’s this kind of behavior that makes people more vulnerable to phishing software, and people’s information can be leaked. We should be cautious when using personal information on websites. People who are not educated in computer network security can hardly tell malware or phishing sites apart.
Very Interesting post! It is really cool to see all these techniques used by the malware to avoid detection. But I guess even if you want to download malware, you have to download form trusted services as well.
Neat post! I wonder, if you wanted to make yourself immune to this particular bit of malware, could you just set your location to somewhere in the CIS, thus rendering the malware unable/unwilling to target you?
Thank you for sharing! Advertisements on the website can be seen everywhere. We usually click on that advertisement without paying attention, which makes us vulnerable to malware attacks. It is very necessary for us to control ourselves not click on the advertisement of the website to avoid the attack of malware. These Mars Steeler malware does not attack computers within the scope of CIS, which is likely to indicate that the computer system in this area has special protection, or that those attackers are hidden in this area. Mars will avoid computers with the device name “HAL9TH” and the user name “John Doe”. In this way, if we modify the name of our computer, we are likely to avoid malware and execute malicious code. Mars Steeler malware is implemented through Google Advertising. I hope the Google team can find a way to detect such malware as soon as possible to strengthen the protection of the system and improve the security of users.
Wow this is really interesting! I wonder if google is able to do anything to try and prevent these “clone” sites from being advertised because most people just click the first link that comes up on google, not even realizing it is an ad and inadvertently exposing them to malware attacks. I also found it quite interesting about how the malware doesn’t attack computers from CIS countries and how it can avoid detection.
Very Interesting post! Fake official websites are also a common method for us to steal our personal information. They look almost exactly the same as the normal official website, and even have similar URLs. If you don’t look carefully, you can’t tell the difference.
Interesting post! I often think that an endorsed google ad will be more trustworthy than a random website but after reading this post I am reconsidering this. Combined with the last lecture comparing the two identical amazon websites I am starting to think trusting a website has to go a little deeper than what I am currently used to looking for. It’s crazy the level of disguise these malware attacks have gotten to. This is the interesting thing about cybersecurity is that the skills are same for each of the “good” sides and “bad”. It kinda comes down to who’s hands it falls in which makes it sounds “superheroy” but it’s a super interesting concept to think think about.
This is really interesting. This malware can not only steal cookie, autofill and credit card information, but also has clever capabilities that can make it unknown to windows defender. Its interesting to see that there is a whole market for this type of malware and lots of money being made despite being unethical.
Thanks for your post, it is very informative and raises awareness over the fact that these ‘products’ are popular. I always find it interesting to read about malware, although it can be unsettling. Seeing how attacks like Mars Stealer can easily disguise themselves and use adds to steal user information really makes you think twice about what you’re downloading. Good thing I have add-block. It was also shocking to read that it is that easy to evade Windows Defender. All in all, this was a great read.
This is really interesting. I am always afraid of fake website when accidentally clicking on an ads on Google. There are websites that intentionally direct you to the advertisement website. It is very hard to avoid being directed to fault websites. Recently, I tried to block redirection from such pages but it did not work. I wonder if Google has any solutions for the problem.
This is my first time hearing about malware which can be bought or subscribed to. I suppose that given that most of this can only be found on black markets or the dark web is likely to be responsible for this. I would be curious to hear more about how a subscription works though, but asides from that I found it very informative and interesting as to how the malware manages to avoid being detected, especially when it is being run in a debugging mode. Thank you for this easy to understand and interesting post!
Good Post! I find it interesting that Mars Stealer will avoid your computer if it detects you are from a country within the CIS alliance, this might point a finger toward the malware’s potential origin? Considering the recently large number of emerging cyber-attacks and malware originating from Russia within the past decade, it wouldn’t be far-fetched to say that Mars Stealer came from there. While I denounce its use as a form of malicious malware, I have to say, it does sound like an excellent piece of engineering, being able to so adequately avoid detection by most standard security systems and those who wish to look into its source code.
Great Post! Mars Stealer expanded modestly until lately when the unexpected shutdown of Raccoon Stealer pushed hackers to seek alternatives. It was promoted on hacking forums at inexpensive pricing of $140 to $160.
Really cool post!
I was surprised to read that Mars Stealer can set up clones of sites, where users can download popular software browsers. Also a little scary that it can detect when a program is running in debug mode and initiate a sleep for 15 seconds. This just goes to show how advanced our technology is getting!
Great blog post! I found it really amusing how it is that easy to trick Windows Defender. I had no idea and I thought it was pretty funny that they made that reference. I always knew there where nefarious software up for sale on the black market but its weird to think about how some random people would just buy it probably without fully knowing how to use the software because they followed some faulty guide that had errors.
Great post! Mars Stealer is a very interesting piece of malware and I appreciate how in-depth you went into how it works. I especially thought that interventions used to evade detection were really interesting- encryption of strings, use of run-time dynamic linking, and sleep initiation are pretty smart ways to prevent being noticed. Given that this software was 160$ on the dark web, I wonder if there are any other software floating around the dark web with similar capabilities. This one was only detected due to the flawed instruction document, so there may be many other different software being used today that are still fully functional and exploitative.
Great post! As an aside, for anyone that wasn’t already using an adblocker, here’s an excellent argument for why you should. If hackers can this easily sidestep Google’s own security measures for advertisers and pay a corporation to essentially provide the infrastructure to spread their malware, then end users are basically on their own to protect their own security. I was also floored that Windows Defender had such an obvious security flaw. The damage potential for this virus is off the charts given its dissemination protocol that leverages a major ad vendor network. I’m curious to know whether the hacker was an individual(s) from the CIS, given their apparent desire to avoid spreading malware within CIS jurisdiction or whether there might be other reasons for their hesitance in that region. I suppose time will tell.
This was a very interesting blog post. It never really occurred to me that these types of products could be available on the dark web for malevolent people to take advantage of. Luckily, if someone is ill-equipped with the skills to employ such a project it can backfire and infect their own system. Hopefully, when rumours of these incidents spread it will discourage other customers from purchasing the malware too. Despite not having the capability to spread like wildfire, I think that serves as one of its advantages because it almost seems “aware” of which systems to infect. Just like you mentioned, it has sophisticated mechanisms to detect system specification, geological location, and affiliation with organizations. These are the ideal characteristics for malware to go undetected by governments and cyber security official for a long time.
Now a day’s pretty much every happening in online. Moreover, attackers are taking advantages of that and they are making clones which is not doubtable at all. Once i was about to get into a trap of clone website by someone which was exactly like my bank website. However, my anti security system saved me from that trap.
Such an interesting post! Attackers seem to be coming out with new strategies in order to execute and succeed in their plans. Thus it is recommended that only authentic and certified sources be used. Furthermore, all software products must be activated/updated with valid developer-provided functions. Suspicious or unrelated emails should not be opened, especially if they contain attachments or links. It is critical to have a reliable anti-virus/anti-spyware program installed and kept up to date to ensure device and user protection. This software must be used to perform regular system scans and to eliminate any risks that are found.
I thought your post to be a lot of fun to read! It’s interesting to see how the attackers are utilising much more direct tactics to infect people, such as through advertising, but I’m sure there’s some phishing involved as well. I liked the details you provided about how malware avoids detection, particularly the part about how easy it is to detect if the software is executed in a Windows Defender emulation mode.
It is such an informative blog! To be honest, today I heard about mars stealer. Mars Stealer, in particular, has the potential to gain access to any crypto wallets that utilize browser extensions. Not only that, it can extract information from popular email clients, as well as harvest information about the host computer.
This is a very important topic that you have talked about. I understand how dangerous this malware is and how devastating its impact can be, but the issue we are not talking about is how Google Ad was used to spread the malware to general public. Advertisement industry has grown a lot and this is one of the most popular ways to share information. But the biggest concern is that anyone can pay google and advertise anything they want. However, this should change and the respected authorities should be concerned about what information is being advertised and if it is legit. If Google authorities went through the link which was advertised, maybe many people would have not been the victim. My piece of advice is that do not click any link directly even it is being advertised by renowned advertising companies.
Great post! Malware is on the rise, and has been for quite a long time. Prior to this post, I was entirely unfamiliar with the “Mars Stealer”, which is apparently a very strong information stealer. From what I have read, this malware is being distributed through various social engineering techniques, malspam campaigns, and keygens. Furthermore, the release of this malware has been followed by an increase in attack campaigns, suggesting that this malware is particularly powerful at targeting unsuspecting users. It is evident that the Mars stealer is a powerful malware, created by sophisticated actors, to empower cybercriminals and propagate vicious, self-serving attacks, at least, in my opinion.
Great post! It is quite surprising that malware organization can clone those famous websites in details even include the lock next to the URL. I really wonder if we can actually find a fake certificate and a signature by clicking on that lock. By the way, I think Google should also take responsibility about this type of malware because it make use of their ads and they do not even know. At least Google should reinforce the investigation and supervision of the ads they provide.
Amazing article! How in-depth you went into how the virus actually functioned and how it evaded Windows Defender was enlightening. The techniques used by the virus to obfuscate detection was quite innovative I must say. The notion that one can purchase virus services like this is quite new to me and makes me more concerned for my own information and security. I feel like google should do more of a review for those sites that want to take out ads using their system. By ignoring these or even simply allowing it to happen, they are complicit with the propagation of these viruses and information leaks.
It was interesting to read about the details of the malware. I have never seen malware that operates in this manner. I always thought that the ads displayed by Google and these popular sites would at least be legitimate, but this article proves otherwise. This is the first time I’ve seen malware that expires and has the ability to detect when it is being debugged. A corrupt computer scientist is truly terrifying.
It is genuinely scary knowing that a malware can use a targeted ad to target it’s preys. We all know about the fake ads which are obviously viruses but what if you are researching about buying a software and you see an ad about the same software being on sale.
Additionally, I really like the ways the attacker has used to fool the debugging systems, it’s simple yet quite effective but it also alarming how easily this malware fooled the windows security system.
I really love the attack diagram provided in this blog. I keep coming across different types of malwares everyday and it certainly helps me being more aware of them. The amount of damage that can happen concerns me a lot. Overall, Great post!
You’d think with the way that Windows makes a bunch of noise about enabling its defender, that it would take more than a couple lines of code to bypass. Surely something like this needs to be addressed. However, I don’t doubt that companies would pay a good deal of money for that stolen information.
Interesting post! I found it really cool how smart this malware is. Not only does it check for things like where in the world it is being run, but it also avoids being caught by windows defender. Malware is becoming smarter, but old antiviruses have stayed the same. Perhaps its time for windows to update their antivirus and make a more secure one. Great post!
Thank you for bringing this sophisticated malware to our attention. It is quite concerning how malware is utilizing google ad services to spread. People will likely not think twice when clicking a legitimate google ad. The extent to which this malware goes to remain hidden from antiviruses is remarkable and the fact that its codebase is encrypted is a sign that this malware was designed by very sophisticated people. The fact that this malware avoids targeting Eastern European nations makes me wonder if that is where it was made and the developers do not want to infect their own socio-economic zone.
Interesting post! It’s impressive how well designed this piece of malware is. It reminds me of the malware portion of the lectures when the professor was discussing how security designers are always fighting at a disadvantage because they never know how the malware creators will attack. I wonder how much money the actual creators make from either selling the malware or using it to generate money through scams etc.
It’s impressive how close the fake and real site look to each other, as well as how indepth this malware is with all it’s features ranging from sleeping if being debugged, to checking its compile time, user language id, username, device name and much more. It’s also interesting that the malware avoids the CIS nations.
Informative post! I appreciate that you mentioned that malware “evolves” to become more effective in its attacks and that is certainly true! It’s also quite concerning how easily you can work around Mircosoft Defender. I would have hoped that anti-virus and cyber defense applications/systems would also “evolve” at the same pace as malware does.
Really interesting post! This goes to show how important checking the authenticity of a website is before anything from it. In addition, also not over-relying on antivirus software like Window’s Defender especially since, as discussed in the lecture, they’re reactionary and have poor defences against zero-day threats. Antivirus should only be one of the last lines of defense.
Great post. It was very concerning to read how easily hackers can get around Microsoft defender. I expected these types of antivirus systems to be very safe and good at protecting you. Another important takeaway from this is to always make sure websites you visit are authentic.
This is certainly something to be worried about, having malware hidden in google ads like this makes use of unsuspecting people that click ads by accident when trying to click on the little “x” button in the corner. It honestly amazed me how easy it was to evade or pass through the windows defender. Its also very interesting to learn about a malware that checks its own compile time and essentially gives itself an expiry date. Also interesting how the malware has a check to see if a debugger skipped the sleep duration and exits without showing any elicit activity if that happens. Great post!
First of all, I found it really funny that the researcher got a hold of the above-mentioned attacker because one of the individuals infected his own computer with malware. In the past, I did sometimes get redirected to different websites while I was on a website and now I wonder if those pages were malicious and if they put malware into my computer system. Other than that, I never thought websites get cloned and they prey on people through ads, so that the people can visit these fake-clone pages instead of the original page, and then get malware in their system.
All in all, this was a really interesting post.
It is quite difficult to tell which websites are scams and which ones are legit. I find it quite funny when actual companies have such scammy looking websites and when scam companies have extremely well put together websites! I wonder in the future if all things will be so similar to eachother that we will always have to get a secure link or something from the company itself