Recently, the Malwarebytes Threat Intelligence Team discovered a new spear phishing and malware attack from a notorious hacker group, Lazarus Group, a North Korean state-sponsored APT, or Advanced Persistent Threat.[1] In a nutshell, an APT is an adversary with many resources and a high level of experience, which it leverages to infiltrate the IT system of an organization to extract information or undermine their mission. They typically hang around in a system for an extended period, adapting to any defenses.[2] Lazarus is believed to be behind the 2017 WannaCry Ransomware attack; a 2014 cyberattack on Sony Pictures thought to be related to the airing of ‘The Interview’ [3], a Sony Pictures film which North Korea was not too pleased about, and various other cybercrimes.[4]
What is Spear Phishing?
Spear phishing is a form of phishing attack, where users are tricked into believing a website or electronic communication is legitimate and click on a link to give over their personal details to an adversary, or inadvertently install malware on their machine. Spear phishing follows these same basic principles, with the key difference being that it is targeted towards a specific individual or organization. By posing as a trustworthy source and using personal information, even vigilant users can fall for this attack, leading to serious data loss, malware, or espionage, if a component of an organization’s IT infrastructure is compromised.[5]
What exactly did Lazarus do?
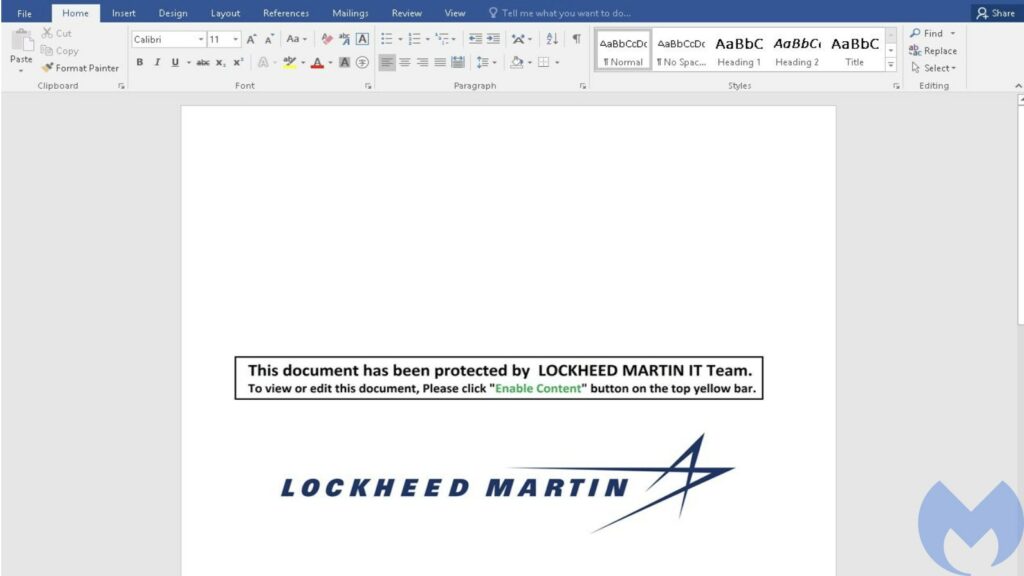
Lazarus targeted the US defense industry (a natural target for a government-run cybercrime group) by advertising job opportunities at Lockheed Martin, an American aerospace, arms, and defense corporation. The job opportunities come in the form of a Word document with a malicious macro embedded.
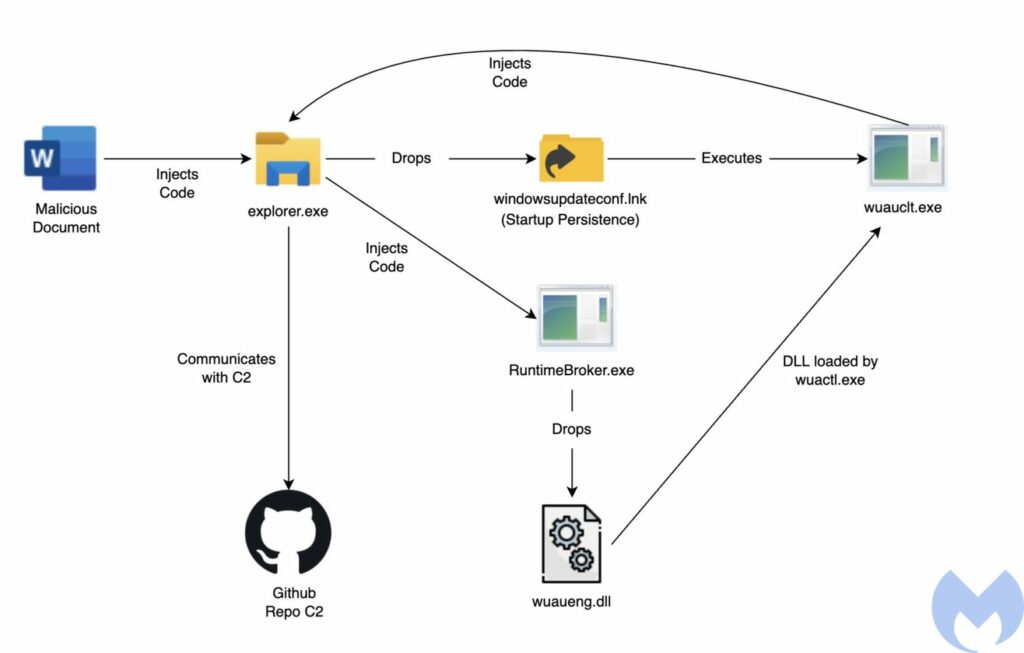
When the macro runs, it hijacks control flow (the flow of code execution) in a novel way and executes its own malicious code to create a DLL (Dynamic-link Library), effectively an extension to an executable file but is not executable by itself. This DLL is initialized by a function in the macro and serves to inject explorer.exe (Windows Explorer) with another DLL, which in turn exploits Explorer to check for and execute yet another DLL that is run using the Windows Update Client. This clever trick is how it bypasses security detection, since Windows Update is assumed to be a trusted process.
At this point in the attack, the malware utilizes GitHub to download a .PNG file which disguises yet another DLL, which retrieves the username, computer name, and list of all running processes on the computer, and commits them to the same GitHub repository.[1]
Impacts
Unfortunately, the Malwarebytes Team were only able to get their hands on this DLL and were not able to determine any more information about the potential impacts of this malware.[1] However, considering the history if this APT, it is safe to say that there was something more going on, possibly stealing data or sabotaging operations. Their use of three new techniques, namely the way they hijacked control flow, the use of Windows Update to bypass detection, and using GitHub as a remote server, demonstrates their ability and threat they pose.
In concluding…
I hope this has shed light on this new attack, and that you learned something today. If you are interested in the way Lazarus hijacked control flow, or if you are looking for any further details, I’d recommend you read the Malwarebytes blogpost ([1]).
Finally, be careful about any emails sent to you! You never know what might be hiding beneath the surface.
References
[2] https://csrc.nist.gov/glossary/term/advanced_persistent_threat
[3] https://resources.infosecinstitute.com/topic/cyber-attack-sony-pictures-much-data-breach/
[5] https://www.kaspersky.com/resource-center/definitions/spear-phishing
[6] https://asset.unitybank.com.au/images/phishing-vs-spear-phishing.png

Hi,
Hearing news about this really did surprise me. What scared me most was since with this kind of hacking technique, terrorists and hackers can pretty much easily hack into almost any kind of securities once they get acess of computer’s control flow. Like as you said for example, if hackers hacked into US’s defense corporations, hackers might’ve teamed up with terrorist and could plan a big terror attack in publics. It spooked me out that techolonigies really can be scary sometimes!
Yeah! It’s really crazy how even the most (seemingly) secure organizations can be compromised, and the consequences thereof can be unknown for years. A lot of APTs can sit in a system for months, completely undetected, gathering information and sending it home. Definitely calls for good security practices and training on top of that to prevent these kinds of spear phishing attacks.
Nice post Ben. What I find fascinating is the ability for the APT to do so much damage simply by someone opening a word document. I was unaware that MS Word macros were powerful enough to have that effect. I wonder if MS should consider reducing the level of authorization that macros can have on the user’s PC.
Thanks! As far as I understand, macros shouldn’t have this much power, but Lazarus came up with a new way of exploiting Windows to hijack execution and do more than macros are supposed to be able to. I didn’t fully understand how they did it, it seems pretty complicated. I think that for security, maybe Office should only be run in a sandbox environment (VM) with no access to the rest of the system, network, and internet, especially for these high security organizations.
I just find it frightening how easy it appears for these hackers to infiltrate government organizations. It appears that many of these groups are now more actively attacking and sabotaging government organizations. Given how more anxious government departments are about their privacy, process of authorization for access, and security, one would safely assume they were more able to secure their information and data more robustly than the general population. Global Affairs Canada was also targeted in a cyberattack last week as well.
I have recently written an article on cyber warfare and I did not realize North Korea played a critical role in cyberattacks against the United States. My focus was mostly on China and Russia since they are known to mess with other countries. I think in the future, cyber warfare would be at the forefront of many issues regarding national security because it is critical that the government can protect its institution and the people. However, I would not be surprised if many countries such as Iran resort to using the cyberattack as their primary means of waging war against hostile countries. After all, cyber warfare if executed perfectly, the toll and devastation could be exponential and every in the global network can be affected as a result. Therefore, I think most countries should make cyber security their primary concern to prepare them for the future.
It is quite surprising to know about new types of attacks every other day. While I was making up my mind to study computer science, I never thought knowing how a system works could be used to make such attacks. I had heard of phishing attacks but never knew something like spear-phishing exists where you want to target a specific organization. It is sometimes difficult to understand if a website is fake or not. In this world of social media, we see numerous links everywhere. I though if we analyzed the url and read it correctly, we could distinguish real website from a fake one. But now reading this article, I have come to know that even this can be misleading. If somehow, these hackers gain confidential information about a country’s defense system, an entire nation can fall down within days. Trusting technology is becoming tougher every day.
Great Post, I learned lot of new things, how North Korean hackers were targeting the US defence and aerospace sectors with fake job offers in the hopes of infecting employees looking for better opportunities and gaining a foothold on their organizations’ networks.
Great post! But to think they could do such a sophisticated attack from a single word document, that really puts into perspective how dangerous downloading anything from the internet is. I wonder what exactly it was that they gained from the attack though.