Apple has rewarded a record-breaking bounty of $100,500 to a security researcher, who reported a bug that can gain unauthorized webcam access[1]. The bug is known to exploit the security flaws within iCloud Sharing and Safari 15, which allowed attackers to also have access to every website ever visited by the victim.

Who Found this Bug?
The security researcher that found this bug is Ryan Pickren, who is a founder of proof-of-concept sharing platform “BugPoC” and a former Amazon Web Services security engineer. This is not the first time that he has identified a flaw within the Safari Browser. Back in 2020, he discovered that flaws in the Safari Browser can be used to snoop one’s iPhones, iPads, and Mac computers through cameras and microphones[2].
What exactly was the bug?
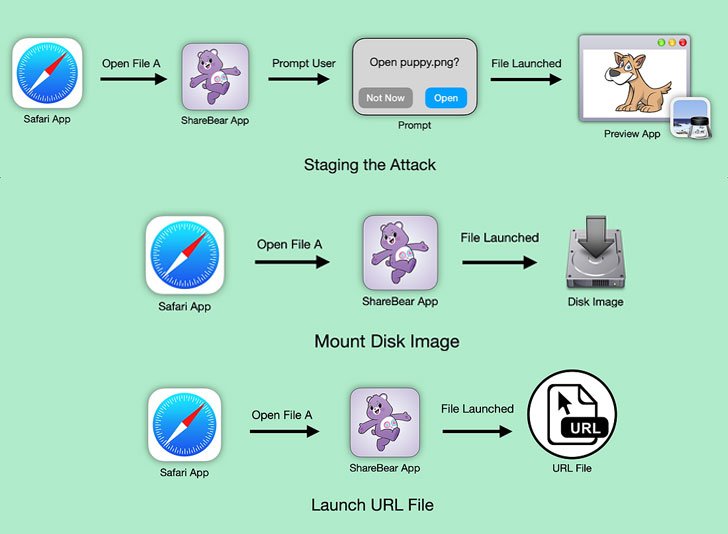
According to Pickren, the vulnerability is centered around an app called “ShareBear”. ShareBear is an iCloud Sharing app that prompts users when they attempt to open a shared document file for the first time and only the first time. The most important thing about ShareBear in this context is that it only prompts the user the first time. If the victim accepts the prompt, the attacker has permission to the file as long as the file is shared with the attacker, because the victim’s Mac would remember that it has accepted the file. Once the attacker has full permission to the file, the attacker can plant a polymorphic file onto the machine and remotely launch it at any moment[2]. Since the victim’s Mac recognizes the file and has already given permission to the attacker, the attacker can plant the polymorphic file without having the victim to allow this action.
You might ask yourself what a polymorphic file is.
A polymorphic file is a virus that can constantly mutate its code, making it extremely difficult for computers to detect the virus yet retain the same basic routines after every infection [3].
There are three steps involved in using Sharebear to download and open a web archive file[2].
- Trick the victim into giving permission, so that the attcker can plant a polymorphic file
- Turn an image file with .PNG format into an executable binary after the victim has agreed to open the file.
- The executable binary generates an exploit chain that takes an advantage of other flaws discovered in Safari in order to take over the machine’s microphone, webcam , or even to access every local file in the system[2].
Imagine yourself wanting to open a cute picture of your dog, well that picture is now an executable binary that your computer cannot detect.
Conclusion
Apple has now fixed this behavior in macOS Monterey 12.0.1. But, one thing we have to take note of is that an exploiter can use approved applications to do a malicious con and that one little flaw in the application can enable a pathway to the victim’s system.
References
- https://thehackernews.com/2022/01/apple-pays-100500-bounty-to-hacker-who.html
- https://threatpost.com/apple-bug-bounty-mac-webcam-hack/178114/
- https://www.trendmicro.com/vinfo/us/security/definition/Polymorphic-virus

Really nice post, Sean! I am beginning to see that the notion of offering a “bug bounty” has become a mainstream practice amongst Big Tech companies. I think offering such bounties is an absolutely critical practice for all tech companies (big and small) to embrace. Obviously, external developers offer objectivity in resolving such bugs, meaning that they have the ability to view, understand, and effectively create counter-measures, without harbouring a vested interest, possibly leading to fewer mistakes being made (Analogous to doctors performing surgeries on family members, this is risky and not advisable. Thus, it is better to bring in another surgeon). However, bug bounties can also increase a company’s vulnerability. By allowing an external individual to fix bugs, companies are also providing that person with the ability to gain access to secure systems, which might not always be an advisable, secure practice. For example, in 2013, a Palestinian computer science student found a vulnerability that would allow anyone to post a video on any Facebook account. The student attempted to disclose this vulnerability through the bug bounty program, but later, the student exploited this vulnerability by targeting Mark Zuckerberg’s Facebook account. It seems as though bug bounties are a double-edged sword.
Good post. I’m kind of shocked that Apple didn’t think this feature through, and I question whether it can be classified as a “bug.” This seems more like an oversight to me for the sake of convenience; Apple knows that people don’t like having to enter passcodes and phrases every time they want to use a feature, and have decided to default to a “trust” option. However, while this may work with regards to trusting a device that I want to log onto gmail with, trusting another device to send you files without restriction seems like a bad idea from the start. I think it’s charitable to call this a bug, I feel like Apple should have seen this coming to be honest.
That being said, I really like the end result. By rewarding somebody for reporting this bug, who wasn’t employed or indebted to Apple, it encourages others to do the same. This “bug” could have been disastrous, with the potential to harm anybody that uses the feature, and having outside resources to identify similar bugs before people get hurt is a good idea. I’m hoping this practice of bounties continues in the future, incentivizing people to do more “ethical hacking” in the name of cybersecurity.
Interesting post!
Only white-hat hackers who reported security flaws received public recognition from Apple. Apple announced at the Black Hat Conference back in August 2016 that hackers will be paid up to $200k to find bugs in its systems. The program began back in September 2016 and will be by invitation only. Hackers who have previously been identified by Apple as having sold exploited information to third parties will most likely be the first to be invited.
Great post! It’s pretty scary how files that are shared with you are actually more harmful than they look in this case. It seems that anyone can be vulnerable to this issue and that a file that you initially thought was safe isn’t safe at all. Thank you for your insightful post!
Hi Sean, really interesting post. It seems this bug is not really a bug but a gross oversight by Apple and it is interesting that none of their developers thought of this issue before release. I would think that such a large company like Apple would have internal review systems that would try to find and eliminate any possible vulnerabilities. Outsourcing those processes and incentivizing users to find bug fixes is becoming an integral part in running a successful tech based company. I believe that there are companies that specialize in testing for vulnerabilties not only in computer systems but also physical security systems as well.
Thank god for bug bounties. This reminded me to update my Mac os. Safari can do so many things, it’s really no surprise that there are going to be more bugs as more features come out. Microsoft also dealt with a privilege escalation bug recently, it was initially discovered two years ago but was failed to be reported due to the bug bounty rewards being reduced. Not acknowledging the significance of bugs, in general, would make our devices more vulnerable to exploits with time and with new updates that may have undiscovered bugs.
Yo Sean, I like your choice of topic because I have always found bug bounty hunting to be really interesting. Personally, I do not use mac because I think the OS sucks but it is very interesting to see how big of an impact one small flaw in the OS could have. I wonder if there could be an attack from hackers similar to this one on windows OS. Bugs are sometimes very hard to find and even then, they could have trivial impact on the security of the system. I would like to hear more and research on bug bounty hunting as there are always so many interesting stories that come with them.
An amazing and interesting post! It’s so insane to think about the clever ways people have come up with to hack into devices and to do so unsuspectingly. It’s also amazing to see how there are now individuals who’s jobs entail finding these individuals, an amazing way to put these skills to use. Kinda reminds me of super heroes and villain but imagine them sitting behind screens and battling it out. Connecting back to how this happened to such a big company is concerning. Apple prides themselves on their technological advances but in the past little bit I have heard about so many things they have glossed over especially in terms of security. It unfortunate that there is a large population that use their products but don’t understand how important the things they are glossing over truly are enabling them to keep going. I hope as our generation gains more awareness they we also continue to hold these big companies accountable as we are trusting them with so much of our information.
It’s always super interesting to hear about what bugs Apple has. I think it comes from the idea that Apple products tend to be safer from malicious attacks (although that may have changed in recent years, I admittedly have not kept up with too much Apple software and security). But it’s encouraging to see people like Ryan helping to exploit these flaws so people won’t fall victim to this very worrisome flaw. It’s interesting too that you mention “in order to take over the machine’s microphone, webcam , or even to access every local file in the system” in your very last point. I feel like there’s a misconception with computers in that people believe that they’re safe if they cover their webcam. I mean, it may help, bur the reality is, is that if an attacker has access to your webcam, they probably have access to the entire computer (microphone, file system, etc.).
It’s very surprising that macOS, which is one of the most secure operating systems was also vulnerable to this extent. It shows that no matter how secure an system is, even one weak point can give dangerous access to attackers.
It’s scary that only a veteran of the field, Ryan Pickren was able to identify this bug and considering how dangerous it was, it could have and might have already caused major damage. This article is a great justification as to why cyber security is so important.
This is a great post. It’s very calming to know that Apple is actually trying its best to make sure its customers are safe. This whole bug bounty idea is a prime example of that. Giving people that are educated in this sort of high tech stuff such as the fellow who found this bug, Ryan Pickren, is a smart idea by Apple to make sure that they can fix any problems with their technology. Even after reading so many blog posts on ransomware and hackers, it still surprises me that there are people out there who will put so much effort into creating new ways to hack others. I mean, who would even expect a simple app like share bear to have such a crazy bug. Thank god for these bug bounty hunters for being able to find such meticulous bugs. Who knows how long this bug could have gone on undetected by Apple.
Great job on the article. I think you have highlighted an aspect that few pay attention to, which is the groundbreaking work done by bug bounty hunters. I think this individual has saved a massive headache to the company, employees, and millions of users worldwide. I recently read an article about an individual who identified integration errors in Google Drive which creates server-side request forgery (SSRF) vulnerabilities. I use Google Drive a lot for work and personal use. I think this find was critical in helping Google maintain their data infrastructure and prevent private data leaks. You can find the story here: https://portswigger.net/daily-swig/google-drive-integration-errors-created-ssrf-flaws-in-multiple-applications. Overall, I think you did a good job explaining the concept of bug bounty hunting.
Reading articles such as this helps to appreciate those who take their time to discover vulnerabilities and exploits not for malicious intent but for the greater good. It makes systems that are used by everyone become more secure but I can’t help but think about how many other vulnerabilities being exploited right now that have yet to be exposed by someone who is willing to improve the system.
Nonetheless, this is a great post that describes the details of the Sharebear exploit and how innocuous it seemed.
Wow, I never knew bug bounties exist. I always thought it was done for free, or it was solely the duty of system security officers of that particular company to find bugs and fix them. Every other day, there is an update in MacBook but I always wait to get the stable version. But now it seems like I have to keep updating my device as soon as there is an update. Thanks to this blogposts, that I am learning new things every day. But the question is how will an average user make his/her device secure, when people with years of expertise are unable to find such exploitations.
Great explanations! I am glad that this bug was caught before too much damage could occur, and that Ryan was rewarded for it. I never knew bug bounties were a thing before this post, but I understand that it is quite useful to task a greater number of people to look for bugs, especially with the incentive. I am also amazed that someone found a way to exploit this iCloud flaw and a bit concerned that it can be used to gain access to so many things.
This was a very well written blog post. It is quite a common practice for bigger tech companies to offer bug bounties so that things like what Ryan identified could not be exploited. If it was able to be exploited it could damage the companies reputation and lead to potential lawsuits. It is amazing how with the iCloud exploit so many things could be accessed and lots of information can be taken. Good for Ryan that he was rewarded for identifying this bug.
Great post! A very interesting topic that might affect some of us and I like the amount of detail you used in your explanation of the topic. I appreciate getting a deeper explanation of how the exploit works, that is still easily understandable on a high level.
Furthermore it is very motivating to read such an example of an individual finding such a bug and getting rewarded for it. I think a bug bounty program is a great way for companies to keep their systems safe and giving incentives to the public to find mistakes to further improve the system’s security. And for us it might be an interesting career path, seeing how one could make a career in Computer Security which seems to be a very interesting and fun career path!
Interesting Post! Through his research, Ryan Pickren found out about the presence of four zero-day vulnerabilities, two of which could be used to hack the users’ camera. For reference, zero-day vulnerabilities are those bugs that are exploited by hackers before the company knows about them.
I found it really cool that bug bounties like these exist in the tech world. I really does motivate for all the security researchers out there to work on ways to make the applications (that they are dealing with) more
secure. The bug shown in this post itself seems to be really intimidating. Planting a polymorphic file onto the device (without allowing the victim to accept this action) and then taking advantage of the victim is really malicious indeed.
All in all, this was a really good post.
Good Post! I find the idea of “Bug Bounties” interesting, as the concept really is a “win-win” for everyone involved, other than those would-be attackers, looking to exploit the vulnerabilities that these bigs expose. The company offering the bounty gets help identifying bugs that could lead to exploits within their system and the “bug-hunters” get a nice sum of money in return. Something interesting about this is that the software companies offering these bounties have full teams of QA analysts looking for bugs around the clock, and even then they miss things that these “bug-hunters” are able to find. This further shows that offering bug bounties is a good idea, as it patches up even the sneakiest of bugs that could lead to potential exploits.