
Attackers have been increasingly uploading malicious packages to the popular JavaScript package repository, npm, in order to gain access to sensitive information, set up botnets, steal cryptocurrency, and more.
‘npm’, what is it?

Node Package Manager, better recognized by its acronym ‘npm’, is a free, open source software registry that was recently acquired by Microsoft-owned GitHub. Upwards of 32,000 packages are uploaded monthly and an average of 17,000 package updates daily, npm hosts over 1.8 million JavaScript packages. Created in 2009, it has grown to become the center of JavaScript code sharing. With more than 11 million developers relying on its service, there is no doubt that attackers will aim to take advantage of this.
Why attackers choose npm
The nature of being open-source and free gives rise to one of technology’s greatest fears; a lack of security. Most of the packages uploaded to npm are maintained and verified by users and open-source communities, making the JavaScript ecosystem ‘ripe for exploitation by attackers’, according to open source security and management firm WhiteSource. A huge problem with npm packages is that they don’t need to be run or used – as long as they’re on the system, they are automatically given permission to do whatever they want.
It is estimated that there will be more than 2 billion websites by the end of 2022 and almost 98% of them will depend on JavaScript. The popularity and dependence of npm across numerous systems and applications provides exactly what attackers are looking for: quick distribution with a large audience.
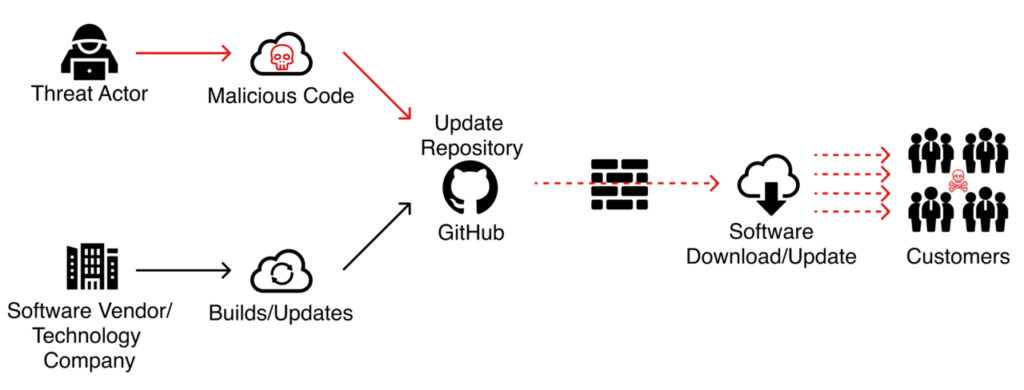
And indeed, attackers are taking advantage of the malicious opportunity that npm presents, having already targeted its popular registries to attack Discord in January and December last year.
Attackers are utilizing the distributive nature of npm and focusing their attacks upstream to ‘infect existing components that are distributed downstream and installed potentially millions of times’, according to this npm Threat Report by WhiteSource. In the last six months, WhiteSource identified more than 1,300 malicious packages that were uploaded to npm in 2021. Of the 1,300 packages, about 14 percent were found to steal sensitive information such as credentials while nearly 82 percent were acting as spies and trackers – passively or actively gathering information on unsuspecting clients.
The malware, and more
As stated in this threatpost article, here are some of the malware that WhiteSource detected and identified in their report:
- mos-sass-loader and css-resources-loader, which engage in brandjacking for remote code execution (RCE);
- circle-admin-web-app and browser-warning-ui, which select external packages including malware for download;
- @grubhubprod_cookbook, which engages in dependency confusion aimed at entering Grubhub company data
- H98dx, a remote shell executable that runs upon install to infect machine; and
- Azure-web-pubsub-express, which enables data aggregation that collects host information.
Earlier this year, researchers also observed a software supply chain attack in October which leveraged a popular npm library, ua-parser-js, used to parse user agent strings to identify various user attributes, in order to gain access to sensitive data and vulnerable resources stored in the cloud. After they supposedly took control of the developers’s account, attackers managed to upload three versions of ua-parser-js, which at the time saw upwards of 8 million downloads a week, each containing malicious code that could allow attackers to steal sensitive information or even take control of the system. GitHub issued an advisory for the package, warning users to migrate their secrets and keys and consider their computer compromised. A quick response from the developer mitigated damage but the affected software had already remained in the popular repository for over three hours.
What does this mean for users?
Fortunately for us, WhiteSource reports all its findings to npm, who removes the malicious packages from its registry. However, this process is not instantaneous. If a malicious package is detected and reported on a Friday, it is unlikely that the package is removed until the following Monday. Unfortunately, this means that it could have been downloaded thousands or even millions of times over the weekend. Unsurprisingly, WhiteSource also reports that Friday is a popular day for attackers to make their move.
Businesses and individuals alike should be especially mindful when downloading packages on weekends, as that is when attackers are most likely to release malicious packages. Naturally, users should always take precautions when downloading software from open-source repositories such as npm and only update when you are confident in the content.
References
https://threatpost.com/malicious-npm-packages-web-apps/178137/
https://www.securityweek.com/1300-malicious-packages-found-popular-npm-javascript-package-manager

That was quite an interesting read. I’m surprised that open-source has issues like this, because I’ve mostly heard the opposite, which is that open-source is more secure because vulnerabilities can be caught right away by the community, and that the code is heavily scrutinized, thus improving its simplicity and security. It’s good to know that there’s another side to that coin!
This is a very interesting article.
Wow! Something as downloading packages that are normally suspected to be safe, becoming a serious security threat, is super concerning. It is good that such malicious packages are removed and detected fairly early. Once the packages are downloaded, it seems to be that the hacker gains quite a bit of access fairly easily, which makes this really dangerous. Thanks for enlightening us with this.
Absolutely beautifully written post, felt like a professional analysis of the facts. Programming languages that rely heavily on packages like Javascript always reminds me of modding games, where you can never be 100% certain that the files that you’re downloading are safe and will do what you want, or end up slipping some nasty code in the backend while everything seems fine and dandy on your computer as data’s being taken away at resounding rates. You really just have to rely on trusting those who make the packages, trust in the people auditing said packages, and mitigating the damage as best you can when **** hits the fan. Attackers releasing malware on Fridays just makes logical sense as well, as lots of IT like to take their weekend breaks after long days at work, giving crucial time where malicious code can propagate far and wide through as many systems as possible before getting shut down, and I completely agree that it’s usually unwise to update software as it’s released, and I shudder to think about automated update systems that might be in place at some companies, giving the attackers even more time to infect computers.
Again, great post and great insight. Thanks for sharing!
I personally didn’t know what npm was until now, this was interesting to read. It goes to show how dangerous it is to download packages that were considered safe at first, now with cybercriminals possibly exploiting these it can cause issues. Luckily they are removed right away once detected which can prevent people from downloading harmful software to their computer. This was an insightful post, well done!
While I haven’t used npm for school CPSC projects so far, I have used it in the past for personal projects. There’s always that concern whenever we’re using user shared code, libraries, and software that this type of issue can arise. Here’s proof as to why that concern should exist. Thank you for getting this information out here. I never would have thought about the added risk to downloading packages over the weekend versus during the week when the site is being constantly monitored. Maybe they could get some sort of automated removal system setup for the weekends, but that poses its own list of problems. It’s hard to come up with any sort of solution because attackers will just find a different avenue of attack the moment their previous method is combatted. In that sense I suppose awareness really is the only viable method of protection so, again, props for this post!
Nice topic!
I never knew about npm until now, imagine downloading a file from GitHub thinking it’s secured and then getting hacked. Web application attacks are increasingly being used as a stepping stone to more sophisticated attacks in which attackers use the application to steal credentials. Attackers use the credentials to gain access to the broader network, where they can install malware or steal sensitive information.
This is a very informative blog post. I’ve used npm a decent amount in the past, and I’ve always wondered about the security mechanisms behind it. I wasn’t aware that npm packages had full permissions on your system once they’ve been download, which is honestly very concerning. If I accidentally mistype the thing I want to install when doing a “npm install”, it seems like my whole computer could be at risk. It also seems that anyone can publish an npm package as they wish, with no audit process of the code. The fact that an open-source package got 8 million downloads a week had such a major security flaw is extremely concerning as well, thanks for sharing this post.
Great post! I think I read something about a malicious package that had made its way into event-stream, a popular npm package. The malicious code in the package could check the Bitcoin and Bitcoin Cash balances on the victim’s copay account. It’s scary to think that a task as small as downloading a package could put your machine at risk
This is a great post! I did not know much about npm before reading this article but, it goes to show that your machine could be at risk for the smallest of tasks. Imagine downloading a package and losing all sense of privacy and security as your machine gets hacked, it’s scary to think about!
Open source does not imply danger or lack of security. The original intention of open source is to share, to give anyone the opportunity to use and improve. When I used a component or feature from Github in the past, IT never occurred to me that software from github might be unsafe. I think more official attention should be paid to open source code or components, such as checking for potential information leakage risks and whether they contain malicious programs.
Great post! It’s always unfortunate to see open source resources be used in such a non-intended way. In your opinion, does this issue (and others in similar open source situations) suggest any conclusions on the security of open-source software? I was always under the impression that open-source software was considered to be more safe from malicious use since anyone can view what is in it. Is that not the case, and if so does this mean that security should move away from open source entirely?
Very insightful post! I always wondered how packages got onto npm, and as someone who doesn’t really think about it before installing a package because a tutorial online told me to, I could have easily fallen victim to the attacks. But this also reminds me of an article about a school being banned from the Linux kernel because some of the researchers were submitting fake patches, while also introducing some other exploits. You can find more information here: https://www.theverge.com/2021/4/30/22410164/linux-kernel-university-of-minnesota-banned-open-source
When downloading packages of software/code, common sense should always be used. If someone is offering a super-awesome piece of code that will solve all your website problems for free, they are 1) Really generous 2) Unaware they could make a lot of money off of it 3) Lying to you and could be acting maliciously. If a repository offers something that is too good, it probably is. On the other hand, open source software usually ends up being more secure than their private counterparts, but one should be careful when downloading from a repository between official/stable patch. Usually, downloading stable patches keeps you out of harms way, as typically patches for large scale open-source software have tested their commits. Thank you for the post, I had no idea the problem was this pervasive; I didn’t know Discord was hit with such an attack.
Good Post! While I denounce the actions of those who upload malicious code or malware as npm packages, I have to commend their ingenuity, it is a rather clever idea to upload a malicious package on a Friday in order to take advantage of developer off hours. Even though the package will only be up for a couple of days, weekends are when people have their time off, meaning that internet usage (and package download rates) are likely to skyrocket. This is a smart idea, one’s package only need to be up for a single weekend to reach thousands, even millions of users (as you’ve mentioned). While the creators of this malicious code are smart, it is good to see that there are smart people on npms side reporting any weird and potentially malicious packages that are found.
Very interesting topic. I didn’t know anything about NPM. It is hard to imagine that software packages can become tools in the hands of hackers and become serious security risks. A small software package can make your computer give away all your privacy. Can there really be a safe place on the Internet these days?