
Preamble
To start off, I believe that some definitions are in order, as understanding some of the concepts FritzFrog utilizes helps paint the picture of what exactly it does. Firstly, P2P is the short form of peer-to-peer; which refers to a type of network, where two or more systems are connected (Computerworld). Peers on a peer-to-peer network, can communicate with each other; more explicitly, they can transfer and relay data to and from one another (Oxford). Botnet bears a similar meaning, in the sense that it is a type of network of systems (Trend Micro). However, each system in a botnet is infected to some degree, and any of these infected systems can be become the point of control for the attacker (Trend Micro). A P2P botnet is the amalgamation of these two concepts. It is a network of intertwined systems that can communicate between each other, and any one of them can become the point of control without the need for an overlying control point. From this, we can see why it’s called the FritzFrog, as much like a frog, control can jump from place to place. Additionally, we can begin to understand how it is still in circulation, as the removal of it from one system, doesn’t effect it as a whole, and finding the location of the current commander is not impossible, but rather complicated. Not to mention the developers of it are able to adapt it as time progresses, to help it remain undetected.
What does FritzFrog do?
FritzFrog attempts to connect to SSH servers, and if it can connect, it drops payloads onto said system; it also adds its own SSH key to the list of keys (Guardicore). One of the main things installed on these systems is something known as a netcat client. This (unfortunately) is not a virtual cat for the infected user to enjoy, but rather it takes whatever it has seen in the terminal, and sends it to the FritzFrog server. In addition to this, it attempts to run a Monero cryptominer (The Hacker News). This is what can be assumed to be FritzFrog’s main goal, as Monero is a decentralized, and untraceable currency. Switching topics, in FritzFrog’s inception it used brute force to infect a total of 500 systems, and is currently infecting 500 per day as of January 2022 as per The Hacker News’ article. According to Guardicore, it used to mask itself as ifconfig, and nginx (which are common Linux software/tools), but now it has changed slightly, and tries to appear as apache2, and php-fpm. It is quite clear that it aims itself to infect servers running Linux, as they often have a reasonable amount of computing power due to numerous machines attached. The earlier mention of it creating a SSH key, now becomes relevant once again as we begin to talk about why it is so tricky to detect. In order to evade detection it utilizes SSH to connect to hosts (as previously mentioned), it is fileless (which is why it needs/wants its SSH key on the system), and it uses a proprietary P2P protocol (Guardicore). The evolution does not stop at changing what mask it wears on systems, as it has also implemented a secure copy protocol feature, and it can even detect high-end machines (The Hacker News). This, quite blatantly, adds more backing to the fact that its sole-purpose is to mine cryptocurrency, rather than to steal information or destroy systems. It seems to be hard to detect, but Guardicore has provided a script to aid in the detection of this malware.
Who is it attacking?
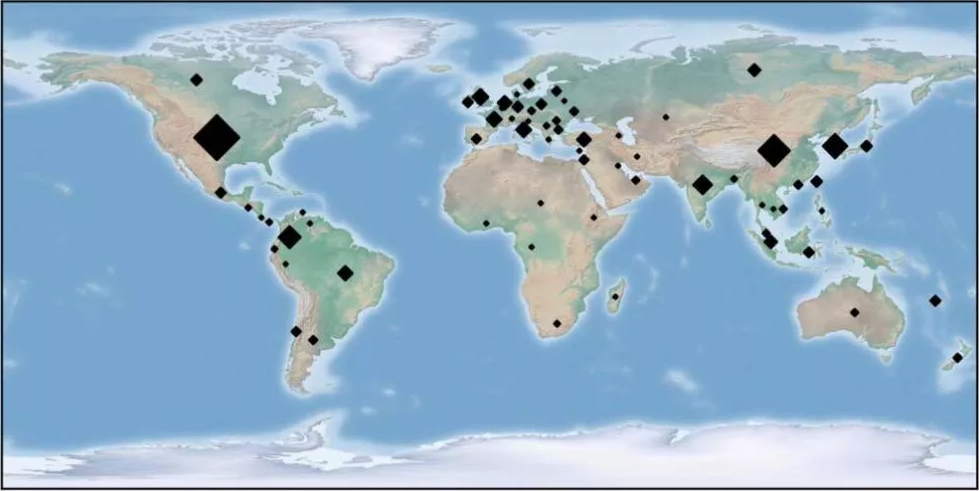
Currently, the aim seems to be large scale entities, rather than small ones. There have been many universities, colleges, healthcare institutions, and others attacked so far (The Hacker News, Guardicore). A disproportionate amount of the infected systems are in China, but other countries such as the United States, and Russia have been also been successfully attacked (The Hacker News). Most likely it inadvertently attacks large institutions (especially universities and colleges), as they normally use SSH, and Linux systems for their servers. Considering it masks itself as common Linux software, adds some sort of proof to this claim. It may also potentially attempt to target individual systems, but this remains to be seen on a large scale. In general though, it seems that it attacks whoever and wherever it can, showing no remorse for any system (unless of course, it can’t be used to mine crypto).
Conclusion
FritzFrog is a dangerous malware, and its aim is to mine cryptocurrency on infected machines. The developers are highly skilled, and the P2P botnet’s progress, from inception to now, are proof of this. It inadvertently attacks large scale institutions, and can easily detect systems that are capable of mining crypto. In times like these, we must have trust in the SSH servers we connect to.
Citations
- Sharma, Ax. “FritzFrog malware attacks Linux servers over SSH to mine Monero” Bleeping Computer, www.bleepingcomputer.com/news/security/fritzfrog-malware-attacks-linux-servers-over-ssh-to-mine-monero/. Accessed 18 February 2022.
- Harpaz, Ophir. “FritzFrog: A New Generation Of Peer-To-Peer Botnets” Guardicore, www.guardicore.com/labs/fritzfrog-a-new-generation-of-peer-to-peer-botnets/. Accessed 18 February 2022.
- Lakshmanan, Ravie. “FritzFrog P2P Botnet Attacking Healthcare, Education and Government Sectors” The Hacker News, thehackernews.com/2022/02/fritzfrog-p2p-botnet-attacking.html. Accessed 18 February 2022.
- “Botnet” Trend Micro Incorporated, www.trendmicro.com/vinfo/us/security/definition/botnet. Accessed 18 February 2022.
- “peer-to-peer” Oxford Learner’s Dictionaries, www.oxfordlearnersdictionaries.com/definition/english/peer-to-peer. Accessed 18 February 2022.
- Cope, James. “What’s a Peer-to-Peer (P2P) Network?” Computerworld, www.computerworld.com/article/2588287/networking-peer-to-peer-network.html. Accessed 18 February 2022.
- “Netcat (nc) Command with Examples” Linuxize, linuxize.com/post/netcat-nc-command-with-examples/. Accessed 18 February 2022.
- “Monero Means Money” Monero, https://www.getmonero.org/. Accessed 18 February 2022.

The worst part about crypto-miner malware is that they are extremely lucrative for the attacker, or owner of the botnet. Normally, A hurdle to profiting from mining cryptocurrency, aside from finding a buyer, is the cost of power (electricity) for the machine, and the strain mining cryptocurrency puts on a GPU, pushing it to 100% utilization for long periods at a time. A regular miner will have to pay an electric bill and swap worn out GPU’s but with a crypto mining botnet, the attacker can bypass all of this, and still get cryptocurrency mined into their wallet, from which the crypto market is the only obstacle to making money. The lucrative nature of such attacks means that these kinds of botnets will probably become more common, especially if crypto becomes more accepted as legal tender. Thank you for the insightful post.
Exactly! As a few others have pointed out, using a botnet to mine crypto is quite lucrative. Not to mention, all of the normal fees that would be associated with mining crypto disappear when considering a botnet; Monero is also pretty untraceable, as Peter mentioned. Thus, when you consider the nature of the botnet, and what cryptocurrency it mines, you begin to realize how well thought out this P2P botnet truly is. I failed to mention it in the blog post, but if you look at the article on Bleeping Computer (in the first paragraph) it states that it has been active since (at least) January of 2020. It’s at the top of my citations if anyone wants to take a gander. Its long active time, further proves that it has some skillful developers behind it.
When someone succeeds to infect a group of computers with a virus or other type of “malware,” they may just steal information or try to extort money from the owners of those computers.
Sometimes, however, they’ll employ this vast group of infected computers to perform large-scale calculations or other operations.
If your computer is infected with malware and joins one or more of these botnets, it will run poorly for the majority of the time, your internet bandwidth may become constrained, life will be difficult, and (worst yet), you will be participating in making the Internet a terrible place for everyone else.
As a result, it is critical to use effective anti-virus software and to run it frequently (particularly for Windows users). Not just for your own benefit, but for the benefit of the entire world. A very helpful topic for our generation. Thanks.
Good read! While I myself am a newbie to using SSH key to connect to servers, it seems that even through SSH servers are not safe anymore. But I still think that this malware is not for individuals like us but mostly for large scale organizations for long term and greater shot of gains. Universities, colleges should take necessary early steps from now on as the malware is new.
I found this very interesting, especially the portion where you said it’s infecting about 500 systems a day! It’s really crazy to think of these computer viruses as things that are able to spread as fast as real viruses. I always heard jokes online about how if someone’s computer is running slow that might be cause somebody is mining crypto on their machines but it’s really crazy to see viruses that really do just that.
I find this malware interesting, because its a great example of how computer programs can be used to steal tangible things rather than abstract data. While it is common knowledge that malware can target people for financial gain directly, this one essentially involves theft of the electricity required to power the machines. That’s not to say that electricity bills are the only consequence of this malware; as others have mentioned, the server would be much slower with a much worse user experience. Its also worth noting that the constant mining would probably incur real world costs as hardware degrades from constant overuse.
If there’s any upside, the map reflects that not many targets of this malware are worth it. It would cost more in hours to develop this software than you would gain monetarily from infecting a chromebook with it, so it seems like servers (or the odd powerful home PC) are the only ones that need to worry.
This is actually pretty cool how it drops a payload via SSH and even adds itself to to the list of SSH Keys! In regards to Monero as a cryptocurrency, its unfortunate that it seems that its primary use case is targeted towards illicit activities due to its decentralized nature as at it’s core, Monero is able to hide the sender, amount sent, the logging of the transaction itself and even to the receiver.
I recommend looking into how Monero is used as a exchange medium in the dark-web and into random-ware cases as well.
It seems like in the future we will have to regularly monitor every inch of our devices for malware. I hadn’t even thought of malware that cracks into an SSH server to mine crypto, but your post has enlightened me. Your post also brings up an interesting point where the decentralized and untraceable aspects of cryptocurrency can be used for crime and not just as a different form of currency.
Interesting post! I can imagine this becoming an increasingly more powerful and destructive malware if cryptocurrency continues to become more common and accepted by the general population. This also reminds me of a similar situation where I was told a student here actually tried to use the universities’ servers to mine crypto. Though this is just a rumor and I never actually confirmed it.
Good Post! I find the idea that discovering that your system has been infected with malware only to see that the malware is simply mining cryptocurrency, rather humourous. However (as another commenter mentioned) mining cryptocurrency can have quite a negative effect on the mining system. You mentioned the fact that multiple large-scale institutions have been hit. You also outlined the reasons behind why these institutions are being attacked, yet it is still fascinating that so many of these types of systems have been breached. These institutions bring in millions (if not more) of dollars annually and most likely have employed some pretty serious (and expensive) security measures to prevent these types of attacks from breaching their servers, yet this software not only breaches these types of systems exclusively but has done so to a large number of them. I agree that the developers of this botnet are very skilled indeed.
Hey interesting post!
I wonder how many malware cryptominers there are that haven’t been discovered. I read a few months ago that hackers had placed miners on websites such as the San Diego Zoo, and the governments of Mexico and others. This goes to show how insecure these websites were and how lucrative these miners are. At the rate you mentioned it wouldn’t surprise me if I had visited had a miner.