Instruction
Nowadays we can search or browse any information we want through the internet. Creating an account and logging in may help the computer to recommend the related message in a more efficient way. However, the log of data may leak your privacy and that’s the reason why I would like to share this blog.
Is that necessary to set a password
Cryptology is a famous subject in computer science. There will be two parts for the whole majority. Encryption and decryption. During World War two, the allies had tried thousands of times to decrypt the Nazi’s telegraph and the password (or we refer to the key to decrypt the message in the right way) has turned out to be the well-known sufficient way to protect your individual information.
How to crack a password
I will show you the most common way to crack a password as a hacker as below:
Dictionary attack–This method involves the use of a word list to compare against user passwords. For example, if the college has delivered the account to you to log in for the education. The password may be related to your ID number, the year of the entrance, or your majority. The hacker will create a worklist that is involved in all possible related information and try it. If the students do not change the password, it may leak your score and other individual privacy.
Brute force attack– This method is similar to the dictionary attack. Brute force attacks use algorithms that combine alphanumeric characters and symbols to come up with passwords for the attack. It will take time, but this is the most regular way. For example, if the limitation of the password is eight characters, for the full number option, it starts from 00000000 to 99999999, it will be done in one second for the whole test and that is the reason why we recommend setting a password with a number, alphabet, symbol and even the uppercase letter.
Rainbow table attack– This method uses pre-computed hashes. You are not familiar with hashes? It doesn’t matter. Let us consider it as the ID for the web page. If you have clicked the link from the mailbox and the computer will open the related website. What if the link is faked? The computer will be wide open for the hacker to get all the info he wants. The website may be so similar, and you may not notice. For yourself, you cannot improve the algorithms, however, never clicking the strange link is enough.
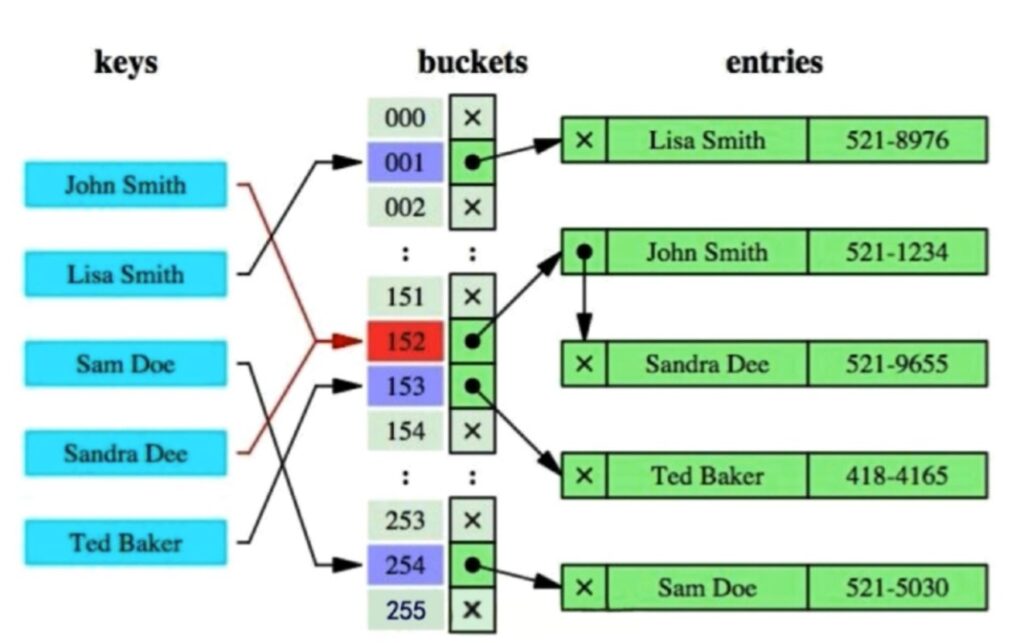
How to hash work
Guess– As the name suggests, this method involves guessing.
Spidering – Most organizations use passwords that contain company information. If you have browsed the web page, the computer will create a log named as history or cookies. This information will not be encrypted normally and please delete or ban it.
The Ways to protect you from the attack
I will introduce some helpful ways to protect your password.
1, Don’t pick a weak password– Just use a combined password with all options I have mentioned.
2, Use multifactor authentication– Link your mobile to the account and it may deliver your random Pin code as an extra way to verify.
3, If biometrics is an option, take it- Like a fingerprint or iris recognition.
4, Different accounts need different passwords- you may combine some related word (like the name of the website or the year when you created it) with the regular password.
5, Consider a password manager- It may cost much, or it will be riskier. However, this will save time.
6, Don’t share your password- Very important.
7, Don’t fall for phishing- Do you still remember the mailbox’s link? Make sure the resource and pay attention.
8, Always update software- The company will improve the security and just update it.
All above are just some common shares for the password, which I hope is to introduce the importance of your privacy and the way to protect it. May this passage be helpful for you.
References
https://www.cnbc.com/2016/02/24/8-ways-to-protect-your-passwords-from-identity-theft-online.html

Nice and concise summary of the topic of password privacy! Good password practices are very clearly stated and easy to understand given the information on the common password hacking techniques. While requiring number, alphabet, symbol and uppercase letter within a password may seem like a good idea to make it arithmetically harder to guess, I believe it was mentioned in class that specifying requirements can actually facilitate password guessing. All in all, every mechanism has its pros and cons, and it’s important to take them into account for the purpose of security and privacy.
In this digital world, accounts are made every day of the week. The eight steps listed above are very good tips on keeping one’s password and privacy safe. These remind me of the first few weeks of this course where we practiced guessing passwords and determining what helped prevent them from being guessed.
Great post here, very informative.
This relates heavily to some of our topics earlier in the course. Although there are many dangers and threats to online security, passwords should be one of the first few things we should take care of. Having simple passwords and using the same ones for each site only invites danger. There are many ways, some of which you discussed in this post, that people use to solve passwords. However, making them more complex, like using special characters, numbers that are not relevant to you (like birthyear) and making the password longer will make it far difficult to have your information stolen.
A great way to summarise the passwords chapter. I find your post very interesting since you mentioned everything we have been taught in class. Another great way to protect your data is to keep it backed up always. This way if you are a victim of an attack you will always have your backup data which you can use. However, this won’t work in every case so the methods mentioned in the blog should be given more attention. Hackers always come up with new ways to hack passwords, so it necessary everyone follows the tips very carefully. Anyways you wrote a great piece. Good job!
A great blog on password security. Many of these steps are important to follow while ensuring extra layers of security from hackers. I do have a question though since our emails are the most common part for most of our accounts: wouldn’t holding onto multiple email addresses (each for their specific purpose) act as another layer of protection? In improving anonymity and security from adversaries, having multiple emails would mean that each will be hard to trace back to you (if you make several sound ‘punk-ish’) and ensure your other accounts are not compromised if one account is accessed.
informative post! In today’s world people make accounts everyday related to social media, school, work etc. and they need to select unique password every time since they can’t use the same one they used before as it would be easier to hack their accounts. So when signing up for something you need to create a strong password so that your account is secure and also enable MFA just to keep your account safe and to not disclose your personal password details to anyone.
Good Post! This is a good summary of some of the guidelines regarding creating good passwords that we learned in class. You mentioned Phishing Attacks. These types of attacks are very interesting and I find them to be rather clever. You would think most attacks attempting to steal passwords are launched by external attackers trying to breach and obtain the passwords of users, but in this type of attack, the password is literally given to the attacker. The method of faking a website and using it to steal users entered information is an old one, but because the action of clicking on links on websites is so frequent, we can often be fooled into giving out something as valuable as our login data, directly to any would-be attackers.
Great post! I had just read another article about a cyberattack that managed to exploit inactive accounts with weak passwords, allowing them to disable multifactor authentication for all accounts. It’s crazy to think that had some people just followed the steps you pointed out here that the entire attack could have been prevented. Your post does a great job at describing how and why you should protect yourself with a strong password.
Interesting post! I used to use the same password for several websites with small variations and recently had one of them show up on a database leak. I then started using a password manager and although the initial setup took a bit its been smooth sailing since then. I highly recommend getting a password manager (I use BitWarden, its free).
Very interesting post!
For convenience, I always use the same password for all of my accounts on different websites. I used to try to use different passwords for my accounts on different websites, but I failed. This is because I can only remember about five passwords that I use for my accounts after half of a year. Also, I never trust any password manager, because I think the owners of those password managers would sell my accounts information to hackers. As a result, for now, I use only one password for all of my accounts on different websites. For account security, I often use multifactor authentication for my accounts, just like what you have mentioned in your blog.
In conclusion, I agree with most of your points in your blog. But, I don’t recommend password managers because I don’t think they are secure enough.
Thanks for making this post! It’s always important to inform people on how to make good decisions about protecting their privacy and security online. The recommendation to use a password manager is a good note, but I don’t think there’s really a “cost” to most password managers. For example, I use a free manager called “bitwarden” and it’s helped me feel like my accounts are much more secure!
Very Informative post! It seems like a password manager is the best form of protecting oneself, because all the user has to do is remember one password, but you also need to enable MFA as well on the password manager, because if the password manager is compromised, then it could be catastrophic.
I really enjoyed reading your post. Though it is not a brand-new topic, it concludes important information we need to know about protecting our passwords. Especially brute force attack is a counter example for why digit-only passwords are vulnerable. I wish I had included this in my final project.