Ransomware-as-a-service, or RaaS, is a business model in which developers sell ransomware to a network of affiliates who may lack the resources or experience to create their own malware. Profits are then split between the two groups. Although such services are typically accessed via the dark web, they operate similarly to legitimate software services, with marketing campaigns, help forums, and kits that allow even those with little technical knowledge to pose a serious threat. Bitcoin is the preferred method of payment, making criminal behavior even more difficult to track.[1]
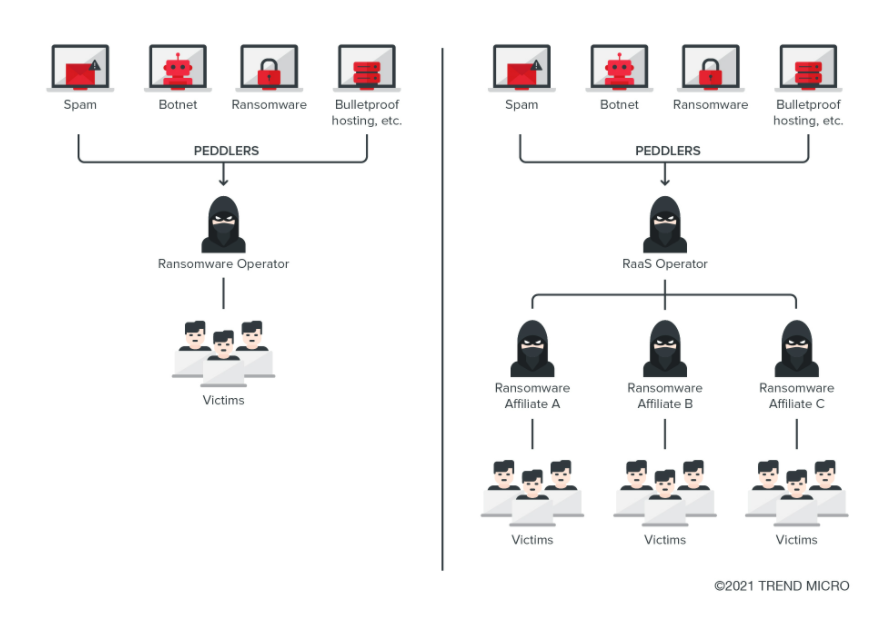
RaaS coupled with more sophisticated extortion strategies are credited with the proliferation of ransomware attacks in recent years. Not only are the number of reported attacks on the rise, but the average ransom payment has increased (up approximately 82% from 2018 to 2020).[2] According to Cybersecurity Ventures, it is estimated that ransomware attacks occurred once every 11 seconds in 2021.
Businesses of any size are at risk. While smaller businesses tend to have weaker security measures in place, larger businesses may be more willing to pay higher ransoms to minimize downtime.
NetWalker’s Notoriety
NetWalker, formerly called Mailto, was established by the cybercrime group Circus Spider in 2019 and transitioned to a closed-access RaaS model in 2020, meaning affiliates were screened before being granted access to customize the ransomware as they saw fit. In particular, NetWalker selected hacker gangs who specialized in high-precision network attacks against larger companies rather than mass-distribution methods targeting smaller entities.[3] The group’s activity was at its peak in early 2020, attacking immigration agencies, schools, law enforcement centers, and hospitals.
NetWalker’s success can be attributed to the utilization of double-extortion techniques, leaking samples of the victim’s data and threatening to release more if their demands were not met.[4] Healthcare facilities were particularly vulnerable, due to understaffed IT departments overwhelmed in the early days of the pandemic. Universities specializing in medical research also became prime targets.
The Case
In January 2021, Sebastien Vachon-Desjardins, a former Canadian government employee, was arrested for his alleged involvement in the NetWalker ransomware attacks from April-December 2020. Canadian authorities seized approximately $28.1 million worth of bitcoin and $790,000 CAD, as well as 20 terabytes of data leading to the identification of 17 compromised Canadian companies.[5] Around the same time, the Bulgarian national police force disabled part of NetWalker’s payment infrastructure that doubled as the group’s leak site.[4]
Earlier this year, Vachon-Desjardins pled guilty to charges of participation in a criminal organization and unauthorized use of computer data. He has recently been extradited to the US and is now awaiting further charges.[6, 7]
Despite the increase in ransomware attacks, effective enforcement for cybercrime remains low for the simple reason that the law often does not cover situations in which the perpetrator originates in a different jurisdiction as the victim. The apprehension of Vachon-Desjardins proves that strong international collaboration is a vital tool in combating and deterring future attacks.
References:
- https://www.trendmicro.com/vinfo/us/security/news/cybercrime-and-digital-threats/ransomware-as-a-service-enabler-of-widespread-attacks
- https://www.pandasecurity.com/en/mediacenter/security/ransomware-statistics/#ransom
- https://www.varonis.com/blog/netwalker-ransomware
- https://threatpost.com/netwalker-ransomware-suspect-charged/163405/
- https://www.newswire.ca/news-releases/successful-collaboration-between-the-rcmp-and-the-fbi-leads-to-guilty-plea-and-forfeiture-of-over-34-million-in-assets-865266069.html
- https://www.infosecurity-magazine.com/news/netwalker-suspect-extradited-to-us/
- https://techcrunch.com/2022/03/11/netwalker-extradited-bitcoin-seized/

Interesting and very well-written blog post! You mentioned that NetWalker screens their potential customers before agreeing to work with them. Why do they do that? By doing so, they are limiting the number of customers they work with. Do they screen their customers to protect the secrecy of the ransom attacks?
Very informative and unique post! This is the first time I have heard of organizations that sell ransomware to people who are unable to make their own. While I’m not surprised that groups like this exist, it is unfortunate that they do. These groups allow more people to commit cyber attacks, and most of the time, it is hard to trace the attack all the way back to the group who originally made it. They get to keep making malware, and get paid for it without being at risk of getting caught. Thanks for informing us about groups like this.
I think the purpose of this system is to make it as opaque as possible. By including various proxies or middlemen. It can be very difficult to trace back to its source. I would even argue that this was formed as a result of ensuring that more ransomware attacks can be conducted with minimal intrusiveness from a regulatory body. This way the group can make more money in a shorter period of time. Additionally, I think NetWalkers have revolutionized the game and I would not be surprised as these attacks gain weight as time goes on with various groups all over the world applying the same methodology to other victims all around the world. Now more than ever we need cybersecurity experts on the spearhead to ensure these groups do not metastasize to the point of malignancy.
It’s interesting that there is a gap in the law when the perpetrator is in a different jurisdiction than the victim. Given how spread out the internet is, one would assume that there is the proper enforcement on those kinds of cases. It sounds like NetWalker is a very careful group and it is also my first time hearing about a group that has made a business out of ransomware. This seems to be an issue more companies should be made aware of.
Vachon-Desjardins was captured in Florida fair over a year prior. Agreeing to the US Division of Equity, he picked up generally $27.6 million by means of ransomware assaults on Canadian companies such as the Northwest Regions Control Organization, the College of Medical attendants of Ontario, and a Canadian Tire store in B.C.
Thank you for sharing this topic.The use of Ransomware is becoming more and more frequent these days. There are also more and more businesses and individuals being attacked by them. Most had to choose to pay a ransom to settle the incident. This will only make them more frequent. How to prevent and combat ransomware is also the part we need to improve
Great post! The RaaS model is definitely on the rise. In my blog post I also looked into the recent SF 49ers ransomware attack which was also done in a similar fashion, but through a different group. It’s very good news that they have found some culprits with how difficult RaaS groups are to target. Especially since the attackers can be anywhere in the world, I agree that a more collaborative approach is needed to prevent these attacks.
The post points out that the business model of RaaS makes profits by selling ransomware, which poses a great threat to various institutions. They are looking for a way to track the difficult way to carry out this transaction and take the loophole path of the law. Undoubtedly, the high accuracy of their ransomware attacks on the organization has increased. The perpetrators and victims come from different jurisdictions, making it impossible for the law to cover this situation. I think the effective law enforcement of cybercrime still needs to be improved to combat such extortion and ensure the data security and network security of users. The loopholes in the law should also be repaired as soon as possible.
Very interesting post! I guess these are the new “mercenaries for hire”. I wonder how many other businesses use this model, and how the contract is even going to look like, and how much of the cut they even get.
Great Post! I did not know that RaaS (Ransomware as a Service) is a business model between ransomware operators and affiliates in which affiliates pay to launch ransomware attacks developed by operators.
Great read! This definitely makes me feel somewhat uneasy just now learning about the concept of RaaS, and thinking of how terrible it could be if this strategy is employed by those who simply have large wallets. Or how some vindictive person could potentially use this to terrorize us everyday people, rather than larger corporations or institutions that seem to at least be the norm for some of these groups, but if this idea of RaaS’ grows, there may be some that don’t ‘screen’ the customers first, selling only to the highest bidder. Just goes to show how important cyber security is and will be in the future.
Best Post! From your post, I come to know that Netwalker ransomware is a Window’s specific ransomware that encrypts and exfiltrates all of the data it beaches. After a successful attack, victims are presented with a ransom note demanding a bitcoin payment in exchange for full decryption of the compromised data.
This is super interesting. I find the statistics that you mentioned to be astounding (i.e., that average ransom payments have gone up ~80% since 2018 and that ransomware attacks currently happen every 11 seconds). Its honestly quite sad, especially how healthcare facilities have been targeted as a result of the COVID-19 pandemic – they’ve certainly had enough to handle as it is. Also, I agree with your argument that strong international cooperation will be important in handling future cyberattacks. Unfortunately, catching/stopping attackers is definitely more difficult when they reside outside of your jurisdiction.
Great post! Hearing about hackers targeting hospitals always makes me angry. These institutions exist to save lives, and hackers merely view them as a source of income by exploiting their desperation and necessity to get their systems back up and running. I’m very happy to hear that Vachon-Desjardins was found and extradited, and part of NetWalker’s payment infrastructure was shut down. I hope the punishments are very harsh and set a precedent for all potential hacker groups to be scared of.
Good Post! There are a number of interesting, and rather scary stats presented here. The fact that a cyberattack was performed every 11 seconds in the US is a startlingly high number. If the number really is this high, then I’d imagine that a large amount of these cyber attacks either fail or are not reported on at all. I’m leaning toward the side of failure, otherwise, this might be an issue that would be receiving more attention. You also mentioned that a common target of these attacks is hospitals. This is rather aggravating and disappointing, these hospitals need their software to help keep people alive, and a ransom or cyber-attack crippling their systems could lead to real people dying, all in exchange for a simple ransom payment? The need for stronger cyber-security practices is essential considering these statistics.
Hey, great post. This looks more like a multilevel marketing model to generate as much revenue as possible. Clearly, the game of Ransomware is taking a new shape with aggression and efficiency being the primary drivers. I think there should be more being done to prevent this occurrence. It will only get worse with time and as such more time and effort would need to be invested to ensure this does not happen. Another thing that stood out to me was how hospitals are being targeted. Clearly, this is a grave violation that is predating on the most vulnerable population. Ransomware attacks on the hospital are a great cause of concern and more should be done by the hospital administrators to circumvent these attacks. I could imagine that life-saving treatments that operate using wifi would be halted in response to a ransomware attack on their infrastructure. I think this was a well-written post overall as I learned a great deal of information from this post. Good job overall!
Great post! I didn’t know much about RaaS and found this post informative. The increase in the number of attacks and the average ransom payment is concerning. It seems that stopping the rise of RaaS can be challenging given that organizations involved often have no choice but to pay the ransom to protect their data, making it very profitable. Plus, the business model where ransomware can be made and customized for affiliates makes it a lot more accessible.
A really good post! I never heard of anyone selling ransomware to people who can’t make their own. Then, also using bitcoin payments to make it hard to track those transactions also is another malicious intent I have not noticed before. The attack developers definitely can make a lot of money this way but I wish these people put all that skill and knowledge to good use instead of these malicious tasks.