
Okta Inc (OKTA.O), whose authentication services are used to grant access to networks by firms such as FedEx Corp (FDX.N) and Moody’s Corp (MCO.N), and more than 15,000 clients, announced on Tuesday that it had been hacked and that some clients may have been affected. Okta reported that in the “worst-case” 366 of its clients were affected and that their “data may have been viewed or acted upon” – the company’s stock dropped 9% as a result of the announcement.
Although the breadth of the breach is unknown, it might have significant ramifications because Okta, located in San Francisco, manages access to hundreds of firms’ networks and apps.
Now let us get to the topic, they were hacked and this breach was carried out by the cyber-gang Lapsus$. Lapsus$ hackers utilize the same old method to get around MFA.

According to Ekram Ahmed of cyber-security firm Checkpoint, the ransomware gang is a South American threat actor that has lately been linked to cyber-attacks on certain high-profile targets. The cyber-gang is infamous for extortion, threatening the publication of sensitive information if its victims do not comply with their demands.
The gang has claimed to have broken into several high-profile firms, including Microsoft, in the past.
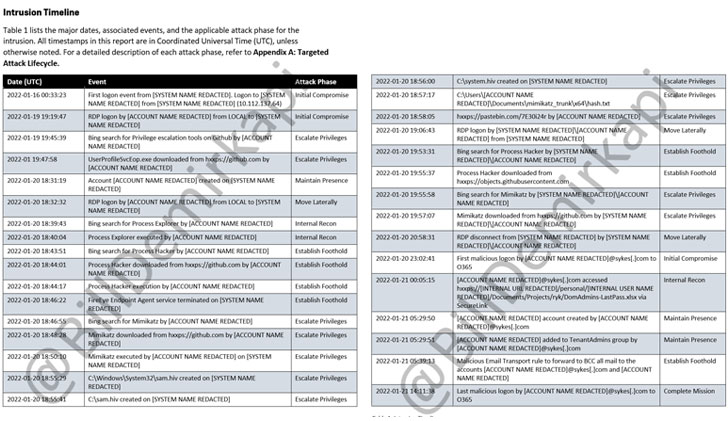
The malicious activities, which granted the threat actor access to nearly 366 Okta customers, took place over a five-day period between January 16 and 21, during which the hackers carried out various phases of the attack, including privilege escalation after gaining an initial foothold, persistence, lateral movement, and internal network reconnaissance.
The vulnerability was eventually discovered two months later, when LAPSUS$ uploaded images of the compromise on their Telegram channel on March 22.
Okta said that it just received a short report regarding the issue from Sitel on March 17 after sharing symptoms of the breach with them on January 21. The criminal gang then said on March 22, the same day it posted the screenshots, that it had gotten a copy of the full investigative report.
The criminal gang then received a copy of the full investigative report on March 22, the same day it posted the screenshots.
“Even when Okta received the Mandiant report in March explicitly detailing the attack, they continued to ignore the obvious signs that their environment was breached until LAPSUS$ shined a spotlight on their inaction,” Demirkapi wrote in a tweet thread.
In a comprehensive FAQ written on March 25, the San Francisco-based firm admitted that it made a “mistake” in failing to warn its consumers about the January hack.
“In light of the evidence that we have gathered in the last week, it is clear that we would have made a different decision if we had been in possession of all of the facts that we have today,” Okta said, adding it “should have more actively and forcefully compelled information from Sitel.”

Company’s reaction after the attack:
Cloudflare, one of Okta’s clients, stated in a blog post that it did not believe it had been hacked.
“There is no evidence that our system has been hacked or compromised,” FedEx told Reuters.
Thanet, which uses Okta to make it easier for employees to manage and sign in to different apps, told BBC News that the attack “has not affected the council’s data’s security,” but that it “will continue to monitor the issue.”
The National Cyber Security Centre in the United Kingdom claimed it has “not observed any indication of effect in the United Kingdom.”
At last, here is a video from youtube which summarises it all:
Sources:
[1] https://www.bbc.com/news/technology-60849687
[2] https://techcrunch.com/2022/03/28/lapsus-passwords-okta-breach/
[3] https://thehackernews.com/2022/03/new-report-on-okta-hack-reveals-entire.html
[4] https://www.wired.com/story/lapsus-okta-hack-sitel-leak/
Thank you all for your time and consideration.

Interesting read! I think out of almost 150 posts I have read a 100 about cyber attacks. Which shows how common cyber attacks have become these days. Even though there is a lot of awareness about cyber crimes out there companies do not tend to make an effort to increase their security system. For example the cyber gang which attacked OKTA used the same old hacking method which involves MFA. In my opinion companies should be responsible for at least making sure their security system is able to prevent the common attack methods out there.
Hacking methods are so common now, and the failure of admitting to their users that they have been attacked is very bad becuase then the users will not be able to trust the company any more because they were not able to protect their information. Companies these days should be discreet upon storing and keeping data, coding has errors and that is where the cyber attacks come from, mail functions in the system.
Very interesting how much news Lapsus$ is making as of late. Their “leader” was actually recently ousted as a 16 year old boy from England as large amounts of their group was arrested and they announced they would be going on a break. The fact that a group this young is capable of performing attacks on such large scale organization’s shows just how prevalent hacking has become! Perhaps they should be signing the ethics waiver we had to sign. Companies will have to respond in some way to this, though how they do will be interesting to watch. It always seems like the “bad guys” are a step or two ahead.
Its interesting to me how consistently vulnerable major companies are to these kinds of attacks, and how poorly they always seem to respond. One would expect that an entity with millions (at least) of dollars at their disposal would be able to invest in enough security measures to avoid this type of situation, or would at least be faster to acknowledge and resolve the issue before real harm occurred. On one hand, these stories make it evident to me that security is not such a simple thing; If companies that rely on the security of their product can be attacked, it speaks more to the fact that no security system will ever be perfect in the face of attackers. One the other hand, however, I would think that at the very least a company would be eager to recognize these issues rather than putting them off, as if breaches are inevitable then you may as well make it known that you take them seriously.
All in all, I struggle to believe that companies are this consistently clueless, so there must be some greater method to their reactions. Maybe they don’t want to give the groups attention, or maybe they’ve crunched the numbers and decided it works out better not to mention anything. Either way, I struggle to think this helps them build trust with users. My takeaway overall is that while computers are obviously amazing, the frequency of breaches makes it almost seem inadvisable to keep much important on them.
While people are a company’s greatest asset, they are also a company’s greatest weakness. Unfortunately, most employees in a company are either not trained or are unaware of some of the potential weaknesses they can create for their companies in terms of cybersecurity. To top it off, many companies who don’t use private contracting for cybersecurity become complacent and their security departments are limited in what they can do or cannot keep up with the ever-evolving practice standards. Like you said, it’s almost becoming a liability to keep information on company networks, which is what the networks were originally supposed to be built for. Most people in a company do not understand issues regarding cybersecurity, thus security issues are not just put off, but not acknowledged in the first place. Big companies with many people, and thus many targets for attacking, are prime targets for attackers.
Another commenter questioned why major corporations don’t invest more in stronger cybersecurity measures when breaches occur so often. It seems to me that too many companies focus on short-term financial gain over long term prospects: the amount of money they lose to ransomware gangs might only constitute a small fraction of total annual revenue. However, failing to adequately protect their customers may ultimately lead to lawsuits and a decline in reputation.
Companies must not be granted immunity from such lawsuits. If preventing breaches costs more than a breach itself, their incentive to properly encrypt consumer data vanishes.
Very informative post. At this point I’m not even surprised to see that Lapsus$ is behind yet another big hack. They have been doing a lot of damage to companies all over. One thing I like about this post is that it shows an example of how hacks can directly affect individual clients who happen to be regular people. Usually these big hacks talk about how the company is suffering, but that there is no issue to the customers, but the hack on Okta shows that even a regular person can be affected.
News of hacker attacks is common, and no enterprise or organization should be overconfident in its security measures. Attention should be paid to potential vulnerabilities when they are found, and their authenticity should be ensured in a timely manner and solutions should be formulated. This will minimize the damage.
This is a very good post. With the prevalence of hacking attacks. I’ve found that many large companies don’t take their network security seriously enough. Most of these companies are not incapable of providing better security for customer information. It’s just that from their point of view, their protection will always be adequate in the absence of a hacker attack. In order to prevent large companies from being irresponsible with their customers’ privacy, I think the government should fine these companies and require them to form partnerships with reliable Internet security companies in the industry.
Great post! You hear all the time about large 1st factor firms being hacked (i.e. TD, Equifax, Microsoft, etc), but you almost never hear about the secondary firms that drive a lot of the technology that they rely on, and which arguably handles even more data. Perhaps it’s because “Facebook Hacked” drives more news than “some company that’s huge but nobody knows their name has been hacked”. Either way, it’s food for thought, and really quite scary that so much data can be attacked and gained from so many different angles.
It’s so crazy to think about how fast the world has evolved in this sense in the past 10 years even. We all grew up watching it evolve before our eyes from the very first iPhone to the advanced computers we now have in our back pockets. With the frequency of technology increased its also crazy to think about the attacks have also. I think mistakes are normal and these companies should disclose this information. I see why they try to conceal it can effect their trust with costumers but in my opinion the being sneaky effects it more. It’s also extremely fascinating how many people are picking up on these skills and how easily they can conceal their identities. Perhaps we need cameras and deterrence techniques for the digital world as we do for the physical.
Good Post! The fact that Okta’s company stock dropped 9% as a result of this attack, shows yet another damaging consequence of these attacks, damage to one’s public image. One would think, considering the consequences of these types of attacks (and their increasing frequency) that Okta’s initial response would have been stronger. Their initial response consisted of ignoring signs that their environment was compromised, which led to even further damage (to the company’s image especially). This highlights the importance of taking an active role in increasing cyber-security measures and shows that in scenarios regarding cyber security (in this case the information security of 15,00 clients), one cannot simply be negligent.
Cyber attacks are becoming scarier everyday. When a system like OKTA’s which authenticates so many systems, is compromised, it can be very problematic for businesses and can have negative implications on the overall economy as well.
Great post! This post, like many others, highlights the widespread nature of cybersecurity threats and cyberattacks. We are living in an opportunistic world, to say the least. Furthermore, the advent of technological advances in the early 2000’s has both cultivated and fostered the rise of sophisticated cyber criminals, who have found creative and malicious ways to further their own agendas. This post highlights that cyber criminals are not constrained by limitations pertaining to the size and power of their targets. They attack who they can, when they can. We need to stay alert, especially given that the world will only advance further in the years to come.
Great post! It is interesting that Okta tried to underplay the size of the hack and I believe there should be room to hold them accountable financially. Companies like these have a duty towards their customers to protect their information and it is unfortunate to see that even though they failed, Okta still tried to downplay and brush away the topic when in reality they should have taken accountability and apologized to those they had been hired to protect. I hope that other firms learn from Okta’s mistake and hold themselves accountable, as this is not a very good look for Okta.
It’s always scary when large umbrella-like corporations get breached since a hack in such a company makes every company under them vulnerable as well. Considering Okta specializes in authentication, who knows how bad this breach has been. It’s a little strange that they weren’t more responsible in letting their clients know about the breach especially considering how liable they are for their security. An interesting read!
Interesting topic! Lapsus$ is behind yet another major hack. Okta’s breach illustrates that even the average individual may be harmed. This story appeals to me because it illustrates how hacks may have a direct impact on individual clients who are ordinary people.
Ah yes, Lapsus$, the name that is mentioned just as often as REvil. I was surprised to learn that the group is based in South America. Clearly, these groups are on the rise and would make an interesting plot for the WatchDogs franchise. Nonetheless, I was surprised that Okta would not admit to the fault in their online infrastructure. I would assume that there is no shame in admitting that they got hacked since it is starting to become a common occurrence all around the world. Additionally, aside from a massive breach, it also had consequences for individuals who are innocent. All it took was one person to overlook something and the result was an armageddon for everyone. I hope the company can learn from this and perform better in the future.
Yet another cyberattack by the infamous group Lapsus$, they have swept the cyber security world off its feet with the sheer number of attacks they have done. One thing which piqued my interest was that Okta kind of ignored when they got to know of the attack for a while until Lapsus sent it in their telegram channel. Usually we would expect the tightest security from an authentication company as many clients rely on them for security and it’s devastating for their image that they got hacked, which shows in their 9% decrease in stocks.
Great post! Throughout the semester there have been countless numbers of blog posts about how a large company has been breached. It’s crazy to think about how frequently these large companies are being breached. I honestly did expect a little more from Okta, especially when they work in cybersecurity. It’s frustrating to see Okta try to sweep this incident underneath the rug, especially when they deserve every bit of criticism for it. Many of their clients rely on this trust, which was misplaced.
Great post! I’ve lost count of how many blog posts and articles I’ve read about big companies getting breached. It’s honestly pretty surprising because you would expect these big companies such as Okta to make sure their cybersecurity is strong in order to protect the so many people that put trust in them. Something definitely needs to change because these big companies are being attacked way too much.
Man it seems like company after company gets caught up in these security breaches. I wonder how hackers feel about doing things like this and possibly costing many people their jobs? Should we feel sorry for them? Should we feel like people in security deserve because they were clearly incompetent to properly protect? I’m not quite sure but I do know that breaking something is usually easier than building.