Who is “Earth Lusca” and what is their motivation?
Earth Lusca is a Chinese-based cyber-espionage group that has been very active in recent years. Their main motivation is spying and gaining intelligence information from government and private institutions worldwide. It has been rumored that they spy on other governments and institutions for the benefit of the Chinese government but these rumors remain uncertain as they have also been associated with purely financially-motivated attacks against Chinese companies.
When looking at some of the attacks that were withheld, the rumors of working with the Chinese government make sense. A list of the institutions and organizations they organized these attacks against include¹:
- Government institutions in Taiwan, Thailand, Philippines, Vietnam, United Arab Emirates, Mongolia, and Nigeria
- Educational institutions in Taiwan, Hong Kong, Japan, and France
- News media in Taiwan, Hong Kong, Australia, Germany, and France
- Pro-democracy and human rights political organizations and movements in Hong Kong
- Covid-19 research organizations in the United States
- Telecom companies in Nepal
- Religious movements that are banned in Mainland China
I think it’s rather worrying that this group continues to undertake these attacks world-wide with no apparent consequences. This has been going on for the past few years!
I also think it’s quite interesting to note that in the recent past it has almost become a trend for government espionage groups to take part in financially-motivated attacks. Some examples include² Rocket Kitten (Iran), Lazarus Group (North Korea), and UGNazi.
How are the attacks being operated?
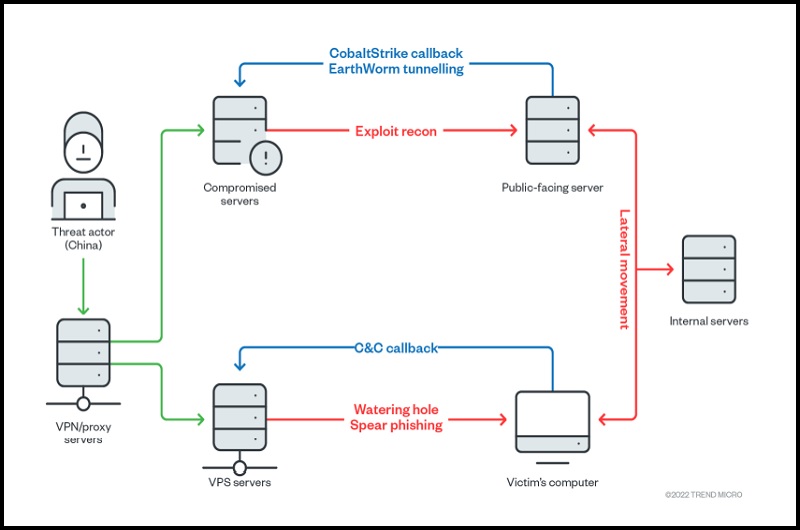
As it can be seen in the above diagram, there are two pathways that the group operates on. The bottom pathway relies on virtual private servers (VPS) that push out watering hole and spear phishing operations to victims’ computers. Once victims’ computers are compromised by malware, this pathway is also used as a command-and-control server (C&C callback) to gain complete control of victims’ computers.
The top pathway in the diagram also acts as a C&C server. It also serves another function of searching a victims’ computer for loopholes, vulnerabilities and building tunnels within the victims’ network (EarthWorm tunneling).
To emphasize on the technicalities, some of the malwares Earth Lusca use include⁴:
- Doraemon backdoor
- FunnySwitch backdoor
- ShadowPad backdoor
- Winnti malware
- AntSword web shell
- Behinder web shell
How can the attacks be minimized or even stopped?
Funny enough, researchers suggest that by simply avoiding clicking on links in emails/websites from unknown sources and updating applications regularly, this can significantly minimize these attacks or even completely stop them. I think it’s crazy (and funny) to think that governments and high-value organizations, who constantly advise the public about the importance of cyber security, are getting attacked and hacked this easily. Advanced cyber security tools such as “Trend Micro XDR” can also be used by big organizations to provide maximum protection against such groups. According to Trend Micro’s technical analysis on Earth Lusca, these tools work by “collecting and correlating activity data across multiple vectors — from emails and endpoints to servers, cloud workloads, and networks — enabling a layer of security detection and investigation that cannot be matched by traditional security solutions.”⁵
On a final note, I would like to share my opinion on organizations and how they handle/talk about cyber security. I think that most companies and governments in the recent years have raised awareness to the general public about the importance of cyber security and have started applying advanced and modern tools of cyber protection. However, I think the topic is still not taken seriously by many and some companies are also not very transparent about the whole process. Cybersecurity failure is one of the main risks that face the entire world in the short-term and medium-term and should be treated according to its magnitude. (The Global Risks Report)
References:
- https://therecord.media/earth-lusca-threat-actor-targets-governments-and-cryptocurrency-companies-alike/ (list of institutions)
- https://en.wikipedia.org/wiki/List_of_hacker_groups (hacker groups)
- https://www.trendmicro.com/content/dam/trendmicro/global/en/research/22/a/earth-lusca-employs-sophisticated-infrastructure-varied-tools-and-techniques/technical-brief-delving-deep-an-analysis-of-earth-lusca-operations.pdf (pathways image, Trend Micro’s Analysis of Earth Lusca’s Operations, Page 2 Figure 2)
- https://www.bankinfosecurity.com/new-chinese-threat-group-conducts-espionage-theft-a-18336 (list of malwares)
- https://www.trendmicro.com/content/dam/trendmicro/global/en/research/22/a/earth-lusca-employs-sophisticated-infrastructure-varied-tools-and-techniques/technical-brief-delving-deep-an-analysis-of-earth-lusca-operations.pdf (page 28: conclusion)
- https://www.trendmicro.com/en_id/research/22/a/earth-lusca-sophisticated-infrastructure-varied-tools-and-techni.html
- https://www3.weforum.org/docs/WEF_The_Global_Risks_Report_2021.pdf (the global risks report)

One thing that everyone should note is that even Canada is vulnerable to cyber attacks from countries such has China. One key example was the corporate espionage of the now defunct Canadian telecom company “Nortel”. While these allegations are controversial, intellectual property from Nortel was stolen by Huawei and may have been used in developing their own patents and products. As a result, this may have benefitted Huawei in saving R&D costs in developing their own infrastructure and pass down cost savings to their products for a bigger competitive advantage. Here are some interesting reads below!
https://www.bloomberg.com/news/features/2020-07-01/did-china-steal-canada-s-edge-in-5g-from-nortel
https://globalnews.ca/news/7275588/inside-the-chinese-military-attack-on-nortel/
One thing that everyone should note is that even Canada is vulnerable to cyber attacks from countries such has China. One key example was the corporate espionage of the now defunct Canadian telecom company “Nortel”. While these allegations are controversial, intellectual property from Nortel was stolen by Huawei and may have been used in developing their own patents and products. As a result, this may have benefitted Huawei in saving R&D costs in developing their own infrastructure and pass down cost savings to their products for a bigger competitive advantage. Here are some interesting reads below!
https://www.bloomberg.com/news/features/2020-07-01/did-china-steal-canada-s-edge-in-5g-from-nortel
https://globalnews.ca/news/7275588/inside-the-chinese-military-attack-on-nortel/
One thing that everyone should note is that even Canada is vulnerable to cyber attacks from countries such has China. One key example was the corporate espionage of the now defunct Canadian telecom company “Nortel”. While these allegations are controversial, intellectual property from Nortel was stolen by Huawei and may have been used in developing their own patents and products. As a result, this may have benefitted Huawei in saving R&D costs in developing their own infrastructure and pass down cost savings to their products for a bigger competitive advantage. Here are some interesting reads below!
https://www.bloomberg.com/news/features/2020-07-01/did-china-steal-canada-s-edge-in-5g-from-nortel
https://globalnews.ca/news/7275588/inside-the-chinese-military-attack-on-nortel/
Very interesting post! After reading this, Earth Lusca looks to be a highly talented and hazardous threat actor who is primarily driven by financial gain and cyberespionage. To entrap a victim, the organization continues to use tried-and-true methods.
And avoiding emails might be difficult since they usually include extremely attractive offers or something visually appealing, and anyone can end up clicking those links and losing control over the system. And I agree with you that some firms are still avoiding such a major issue by continuing to utilize their outdated firewall and other security systems, and others even appear to be without them.
I would tend to agree with you that it is quite humorous just how vulnerable government and international actors can actually be to cyberattacks, despite all of the well-intentioned “advice” they give to individuals. In your opinion, if more information is brought to light that conclusively links this group with the Chinese government, do you think it might lead to sanctions or other consequences?