On January 20, 2022, researchers at Kaspersky discovered a hidden threat entrenched within the firmware of a computer: a rootkit. It’s called “MoonBounce” and is believed to be developed by government-backed Chinese hackers[6].
So what are rootkits?

Generally, when talking about malware, rootkits are a type of malware designed to conceal itself or traces of other malware. They are usually bundled with other types of malware to work together to achieve one goal — to ensure that it or the malware that it works with exists for as long as possible.
The real danger from rootkits is that it’s usually very hard to tell when you have one as a user, and thus a reason to buy software to detect and remove one. The most primitive of rootkits could modify the ‘ls’ command, common in most UNIX operating systems, to not list infected files. Nowadays, the most dangerous of rootkits have the ability to[3]:
- Hijack or disable antivirus software (without you knowing)
- Spy on a user’s behavior
- File removal
- Remotely control your computer
- Install additional malware on a computer or system.
- And really anything you can think that malware can do
How rootkits work (at a basic level)
Fundamentally, a rootkit is basically a program that modifies requests made to the operating system. By modifying these requests, a rootkit can provide false data or incomplete data, allowing the rootkit control over the output. This is why it’s very difficult to tell when you have a rootkit because you cannot trust any of the information reported back to the computer since it’s likely to have been modified by the rootkit.[5]
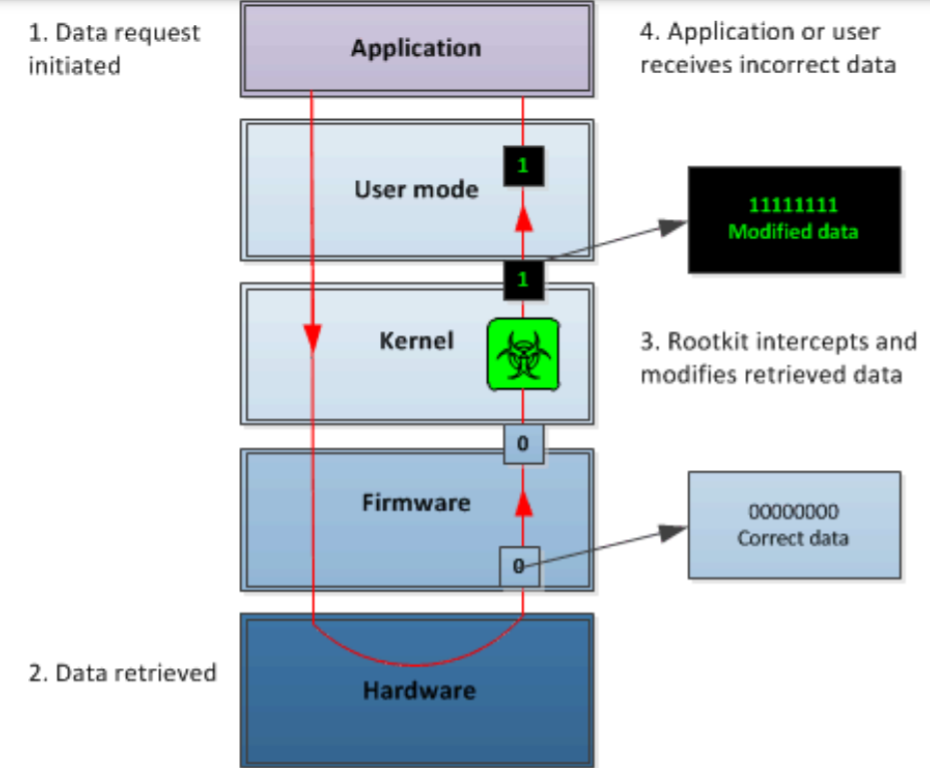
In the diagram above, the information requested by the application has been modified from being ‘00000000’ to ‘11111111’ by the rootkit, effectively changing what the outputted does.
Back to MoonBounce
MoonBounce is a firmware rootkit, firmware being a type of software used to control the hardware of a computer. These types of rootkits are known to inject themselves into the hard drive, router, or a system’s BIOS (or equivalent)[4]. Most disturbingly of all, even performing a factory reset on your machine or wiping your hard drives will not remove this type of rootkit[1].
MoonBounce is known to infect something called the Unified Extensible Firmware Interface (UEFI), a piece of firmware inside computer chips (it’s very similar to a BIOS). It’s a piece of software that boots the system and loads the operating system. Luckily, the researchers who’ve discovered this rootkit suggest that the nature of the attack is very targeted, being detected in only a single case[6]. However, security researchers say that the code used in MoonBounce is “pretty simple”[1] and has plenty of room for enhancements, suggesting that malware that targets the UEFI firmware may be much more common in the future.
How to prevent rookits
The capabilities of a rootkit can be frightening. Also, a rootkit is one of the most difficult types of malware to find and remove. So, do yourself a favour and prevent your computer from being infected by a rootkit. Here are several suggestions and recommendations by cybersecurity experts[1][3][4]:
- Be cautious of links and attachments of emails that you don’t recognize or that seem suspicious.
- Keep applications up to date and remove deprecated applications that you don’t use.
- Download files from trusted sources only
- Scan your systems regularly (Malwarebytes suggests that to use multiple scanners)
- Enable secure boot on your computer
- Encrypt your hardrive
- Monitor your network traffic
References
- https://www.darkreading.com/threat-intelligence/rare-firmware-rootkit-discovered-targeting-diplomats-ngos
- https://blog.comodo.com/comodo-news/uh-oh-uefi-rootkit-malware-spotted-in-the-wild/
- https://www.blog.malwarebytes.com/how-tos-2/2020/01/how-to-prevent-a-rootkit-attack/
- https://www.kaspersky.com/resource-center/definitions/what-is-rootkit
- Microsoft Malware Protection Center Threat Report: Rootkits, Microsoft, 2012, https://www.microsoft.com/en-us/download/details.aspx?id=34797
- https://securelist.com/moonbounce-the-dark-side-of-uefi-firmware/105468/