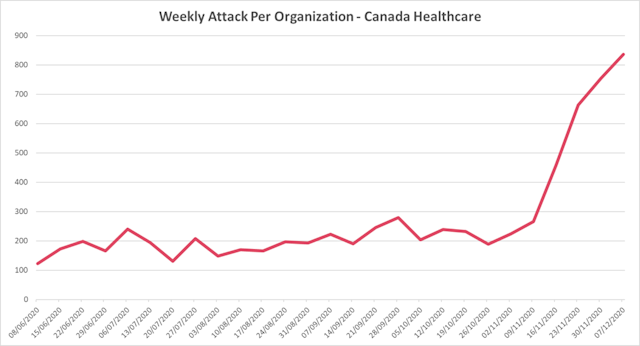
Introduction
It’s been recently reported that over half of medical devices have critical security vulnerabilities. (Cynerio, Jan 19, 2022) Healthcare organizations are an easy target for cyberattacks due to their weak defenses, and something must be done about it for the safety of the public.
Why is this a big issue?
Hackers are becoming increasingly successful in breaching healthcare organizations’ data and this problem has been running rampant for the past few years. These data breaches have huge consequences for everyone.
For example, Maryland’s department of health was hit with a devastating ransomware attack, which gave hospitals a difficult time, especially due to the higher hospitalization rates due to COVID-19. One major consequence of this data breach was that the department couldn’t release their case numbers over the course of a few weeks, hindering their ability to take well-informed action in response to COVID-19 and to notify other states of their case numbers (ZDNet, Jan 12, 2022).
Recent research reveals that ransomware attacks are posing serious threats to healthcare consumers, including increased mortality rates and complications in treatment that often increase recovery time or yield incomplete recoveries.
Some examples of hospital equipment that are especially vulnerable to attacks are:
- IV pumps, 73% of which possess a serious vulnerability that can threaten patient safety, leak confidential data, or limit the accessibility of the pump itself in the case that is targeted in an attack (Cynerio, Jan 19, 2022).
- Any devices using versions older than Windows 10, which make up the majority of the devices in a multitude of healthcare departments. This presents potential danger to patients connected to any of these devices (Cynerio, Jan 19, 2022).
How is this issue being addressed, and what are the challenges in doing so?
According to an article by Cynerio on January 19, 2022, the use of network segmentation is sufficient to prevent over 90% of the security dangers associated with medical devices in hospitals, and is the most effective method in doing so. However, this article does not mention the logistics of such an implementation in terms of time or money.
Another strategy for improving the security of data in hospitals is to have up-to-date software. The old software that is still in use in many healthcare organizations presents a significant variety of shortcomings in regards to protecting against cyberattacks. This could be improved upon by these organizations by updating to more recent and higher quality software. This proves to be a strikingly difficult challenge, however, as investing in an area such as this does not produce revenue for the organization.
Further, any attempt made by healthcare organizations to predict the cost-effectiveness of upgrading software appears to be a fruitless effort, as technology has been evolving far too rapidly for there to be any significant historical evidence to inform such a decision.
Yet another struggle for hospitals is the lack of individuals with expertise in the field of cybersecurity working in healthcare. For example, only 21% of hospitals had a dedicated security executive in 2019, yet only 6% were identified to be a Chief Information Security Officer. There is a significant rush for hospitals to hire cybersecurity professionals, which is leading to such high demand that cybersecurity companies are providing hospitals with a growing array of services (Black Book Research, Nov 4, 2019).
Due to this lack of knowledge, healthcare organizations remain unaware of which solutions exist, let alone have the knowledge necessary to know which ones are best suited for them. An additional result of this is that hospitals are unable to put in their due diligence for testing their cybersecurity systems, thus causing them to deal with attacks retroactively rather than proactively.
What does the future of cybersecurity in healthcare look like?
Over the past few years, healthcare organizations have become increasingly aware of the dangers associated with cyberattacks, so it is becoming increasingly common for them to set concrete goals in terms of cybersecurity (Black Book Research, Nov 4, 2019). This will allow them to attain measurable results and assess their ability to protect themselves against cyberattacks. The vast majority of healthcare organizations predict a foreseeable increase in cyberattacks against them in the future, thus giving them a good reason to improve upon their existing systems. Alas, we can only hope that in the future, healthcare organizations will choose to pay more attention to the security of their data so they are better enabled to save more lives.
Key Takeaways
Healthcare organizations have been a very common target for cyberattacks in recent years, and this danger’s presence is only projected to increase in the coming years. This happens for a multitude of reasons, most of which lie in the inability of healthcare organizations to address such issues and a lack of experience with attacks of this nature in the ever-evolving digital landscape. Hopefully, they will be able to find effective security solutions in the coming years as the attacks inevitably continue.
References
- https://www.zdnet.com/article/more-than-half-of-medical-devices-have-critical-vulnerabilities/
- https://www.cynerio.com/blog/cynerio-research-finds-critical-medical-device-risks-continue-to-threaten-hospital-security-and-patient-safety
- https://www.zdnet.com/article/maryland-officials-confirm-ransomware-attack-shut-down-department-of-health/
- https://blackbookmarketresearch.newswire.com/news/healthcare-data-breaches-costs-industry-4-billion-by-years-end-2020-21027640
- https://www.businesswire.com/news/home/20210922005436/en/New-Ponemon-Institute-Research-Shows-Ransomware-Attacks-on-Healthcare-Delivery-Organizations-Can-Lead-to-Increased-Mortality-Rate