Introduction
While Russia began its invasion of Ukraine, several Ukraine defense and foreign ministry websites, banks and many others were taken down in a large, distributed denial of service (DDoS) attack all over Ukraine. This is consistent with tactics used in the past by Russia when it comes to cyber attacks as seen before in 2014 with Crimea, 2008 in Georgia and 2007 in Estonia. DDoS attacks are not the only cyberattacks being seen so far either. A new data wiping malware was found on hundreds of devices in Ukraine as well as in Ukraine contractors in Latvia and Lithuania. This malware was soon named the Hermetic Wiper.
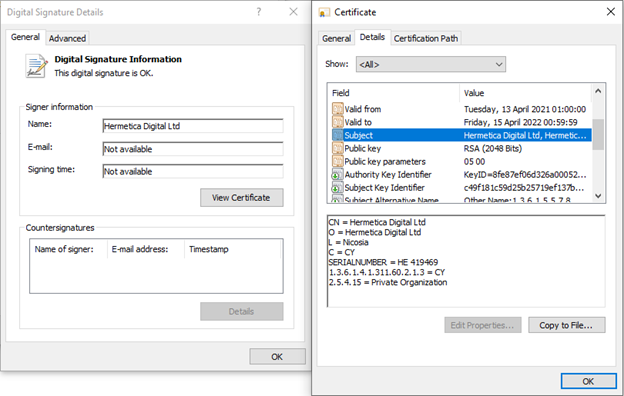
Digital Signature Information of the Hermetic Wiper malware (photo: twitter @ESETresearch)
Hermetic Wiper
It was found that one sample of the Hermetic Wiper malware had been compiled in December, suggesting that the attack had been in preparation for at least 2 months. The malware has a digital signature issued to Hermetica Digital Ltd, hence where the name Hermetic Wiper comes from. It turns out that Hermetica Digital Ltd is a small business of a video game designer in Cyprus who says he had no part of the attack and never applied for a digital certificate or knew that one was granted for his company. Although the malware was compiled in December the digital certificate was issued back in April 2021, which could lead to further analysis of the timeline for the invasion of Ukraine. However, it is also just as possible that the certificate was bought recently on the black market for this campaign from cyberspies who routinely steal identities.
The wiper itself uses a common malware wiper technique of abusing legitimate drivers to corrupt data and reboot the device. A ransomware now named Party Ticket was also deployed along with Hermetic Wiper. Party Ticket is believed to be a decoy to distract targets while devices are wiped by Hermetic Wiper. The ransomware program also consists of various mentions of the USA government and Biden.
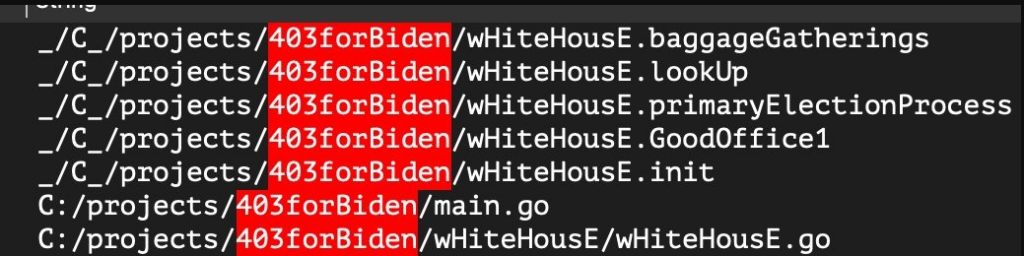
Folder and Function names of the Ransomware (Photo: https://www.sentinelone.com/labs/hermetic-wiper-ukraine-under-attack/)
What’s Next
Cyberattacks continue to occur and worsen as not just Ukraine websites but some Russians one too are going down from DDoS attacks with cyberactivist groups taking credit and Ukraine creating their own cyberattack IT groups. The United States and their allies are now warning organizations, businesses and governments the importance of strengthening their cyber defenses as much as possible in case the cyberattacks continue beyond Ukraine as already seen with traces of Hermetic Wiper in Latvia and Lithuania. Concerns have also been raised about just how devastating a cyberwar could be between USA and Russia if the USA were to get fully involved with capabilities listed to include shutting off power, tampering and stopping or speeding up trains, disrupting internet connections and many more devastating cyberattack effects.
References
https://www.sentinelone.com/labs/hermetic-wiper-ukraine-under-attack/
https://www.sentinelone.com/blog/a-cisos-guide-to-the-security-impact-of-the-attacks-on-ukraine/
https://www.digitalshadows.com/blog-and-research/russia-invades-ukraine-what-happens-next/
White House Denies Mulling Massive Cyberattacks Against Russia