Image credit: https://www.gettyimages.ca/photos/ezra-shaw-49ers
After falling short in the NFL Conference Championship, the San Francisco 49ers football franchise was recently hit with another blow; but this time off the field. On February 13, 2022, the organization was reportedly a victim of a ransomware attack by BlackByte [1].
What is ransomware?
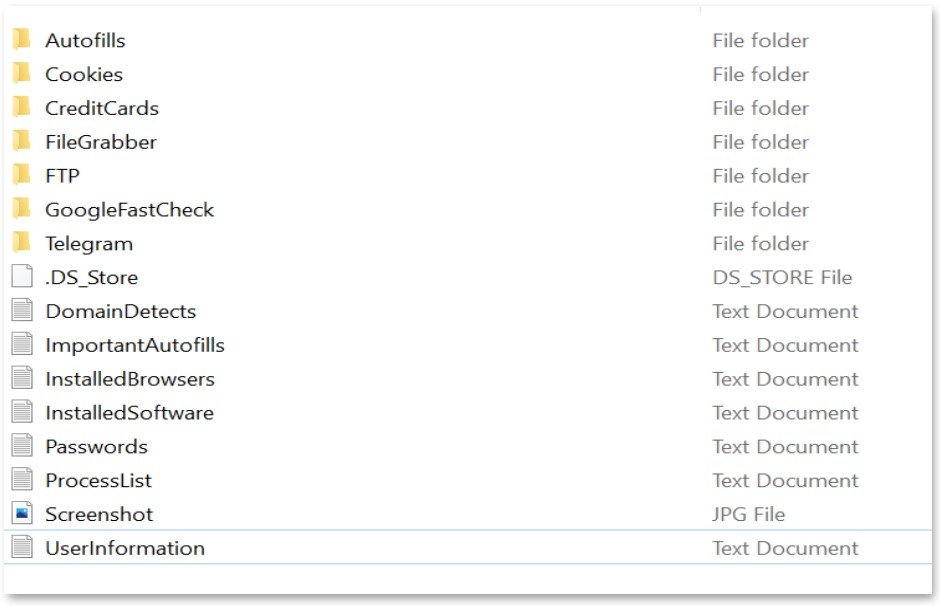
Ransomware is a type of malware which attacks files on the computer system by encrypting them. To decrypt the files, the attacker typically asks for a ransom [2].
Who is BlackByte?
BlackByte is Russian ransomware gang that has been targeting corporate organizations since July 2021. They operate as ransomware-as-a-service (RaaS) which means they rent out ransomware software to others for a percent of the ransom [3]. The RaaS operation makes tracking the attackers difficult, because the operators can use the malware from anywhere. Although, their first ransomware version was not too complicated, it appears their second version is much stronger and has been used to target “at least three US critical infrastructure sectors (government facilities, financial, and food & agriculture)” according to the FBI on February 11 [1].

Image credit: https://www.hackread.com/blackbyte-ransomware-san-francisco-49ers/
The ransomware gang appeared to have used Microsoft Exchange Server, a mail server, to gain access to the team’s networks. They then moved “laterally across the network and escalate[d] privileges before exfiltrating and encrypting files” according to the FBI alert [1]. Escalating privileges refers to an attack that increases privileges to give the attacker higher levels of control [4]. The security breach remained in their IT networks and doesn’t seem to impact the stadium operations or season ticket holders. However, the ransomware gang gained access to some of the team’s financial data, including a file named “2020 Invoices” that was leaked on their website on the dark web. It is unclear how much of the data has been encrypted and if an incident response company has been hired to help with the ransomware investigation [5].
What are authorities doing about this?
Although the FBI issued an alert about BlackByte, there isn’t too much that can be done at the moment due to the anonymous nature of the RaaS operation. The trend towards more RaaS operating groups brings more challenges for corporate organizations around the world, but certain measures can drastically reduce the likelihood of a ransomware attack.
According to the FBI and US Secret Service [6], some of these measures include:
- Implementation of network segmentation so the malware cannot spread throughout all computer on the network.
- Installation of updated antivirus software.
- Disabling of hyperlinks on incoming emails.
- Regular backup of data which is stored offline with password protection.
- Making sure offline copies cannot be modified from the original machine.
The monetary gain currently outweighs the risks of severe consequences for their actions. This should not be the case. With ransomware on the rise in 2021, the US Department of Justice has made progress by forming the Ransomware and Digital Extortion Task Force [7], but clearly the efforts have not been enough to deter ransomware gangs.
References
[1]: https://www. hackread.com/blackbyte-ransomware-san-francisco-49ers/
[2]: https://www.mcafee.com/enterprise/en-ca/security-awareness/ransomware.html
[3]: https://techcrunch.com/2022/02/14/blackbyte-critical-infrastructure-ransomware/#:~:text=BlackByte%20is%20a%20ransomware%2Das,to%20target%20corporate%20victims%20worldwide.
[4]: https://www.beyondtrust.com/blog/entry/privilege-escalation-attack-defense-explained
[5]: https://www.msspalert.com/cybersecurity-breaches-and-attacks/ransomware/49ers-ransomware-attack-details-and-recovery-update/
[6]: https://www.bleepingcomputer.com/news/security/fbi-blackbyte-ransomware-breached-us-critical-infrastructure/
[7]: https://techcrunch.com/2021/12/30/the-year-the-tide-turned-on-ransomware/