Remote working is not something new. Since the Covid19 pandemic started the diversity of remote learning is incomparable. There was always cyber security threat in remote working. However, it increased recently as people were forced to work from home to reduce the spread of virus it caused a rise in the new remote learning landscape, and Ransomware played an important role in this cyber threat push.
What Ransomware is?

Ransomware is a type of malware from crypto virology that breach victims’ data and block access for the victim and threaten the victim if a ransom is not paid.
How does Ransomware work?

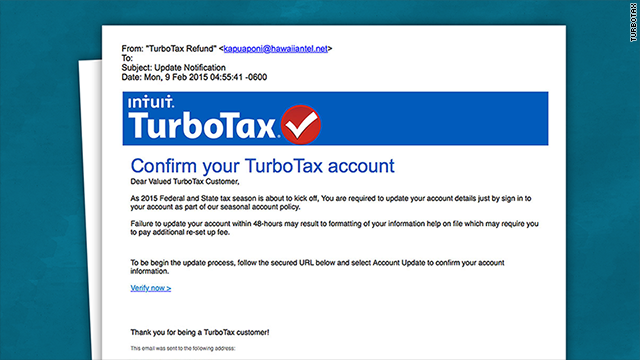
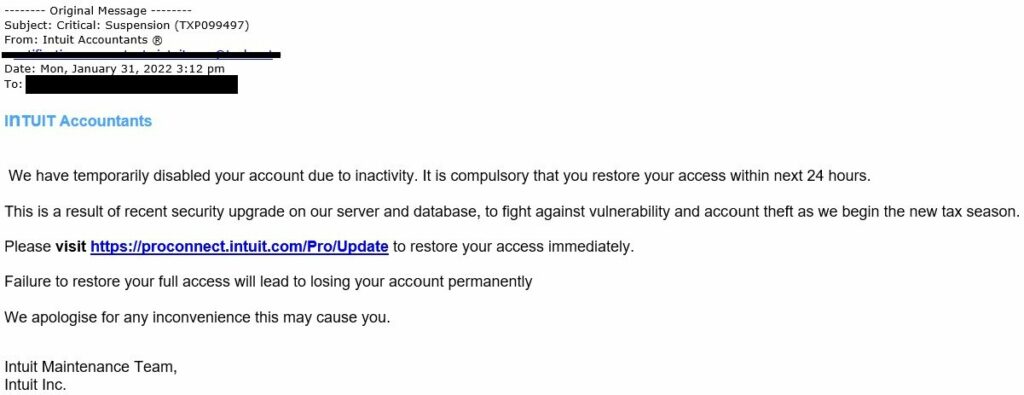
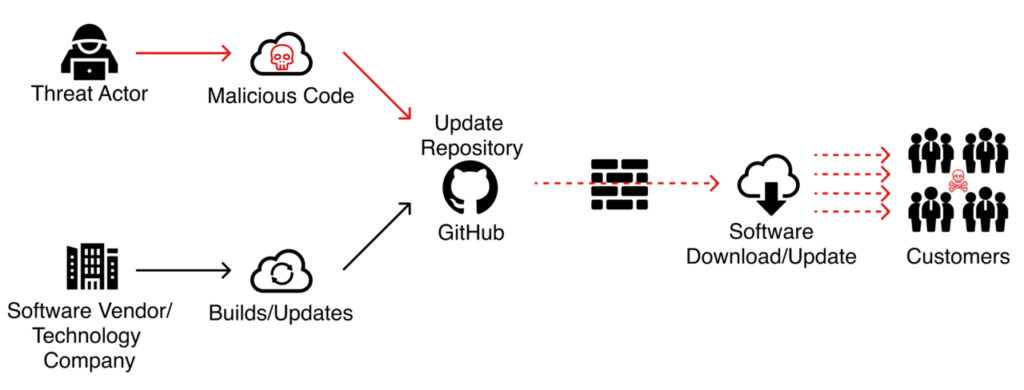
Ransomware could happen in many ways. However, the most common one is phishing spam emails with an attachment. If the user opens the spam email the attachment will be downloaded into the user’s system without the user’s knowledge, then the malware will encrypt the victim’s files and victims will be instructed to get the decryption upon payment.
Ransomware and its explosion in recent years!
Ransomware has long posed a cybersecurity threat to remote working and recently it exploded because of Covid 19 pandemic. According to the global security group, the Institute for Security and Technology only in the US $350 was being given to hackers and it’s a 311% increase over 2019.

One of the most recent ransomware hacks happened because a company employee used a public network. By Which hacker breached into the private network and used remote employees IDs to connect with the company system which forced to shut down a colonial pipeline that used to supply 45% of the eastern United States’ fuel.
The hack of Twitter in 2020 was not for ransomware but the main breach point of this incident was remote working. Several employees were being called by the hacker and claimed to be IT department support and offered help to connect through the company’s virtual private network being used by employees working from home. From this hack, the hacker was able to seize 117,000 bitcoins.
We could say remote working is one of the reasons right now which increased the threat of cyber security and Ransomware is one the easiest way for this accomplishment of hackers’.
How to avoid Ransomware and Remote working threat?
- Wi-Fi:
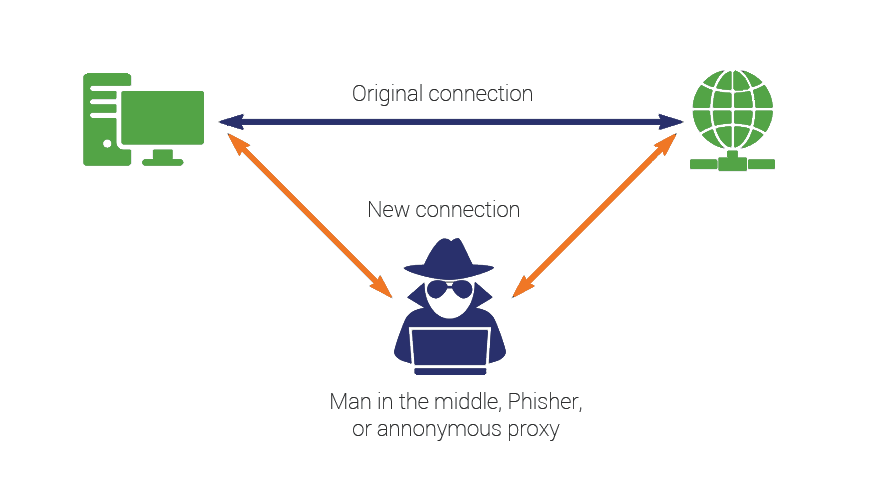
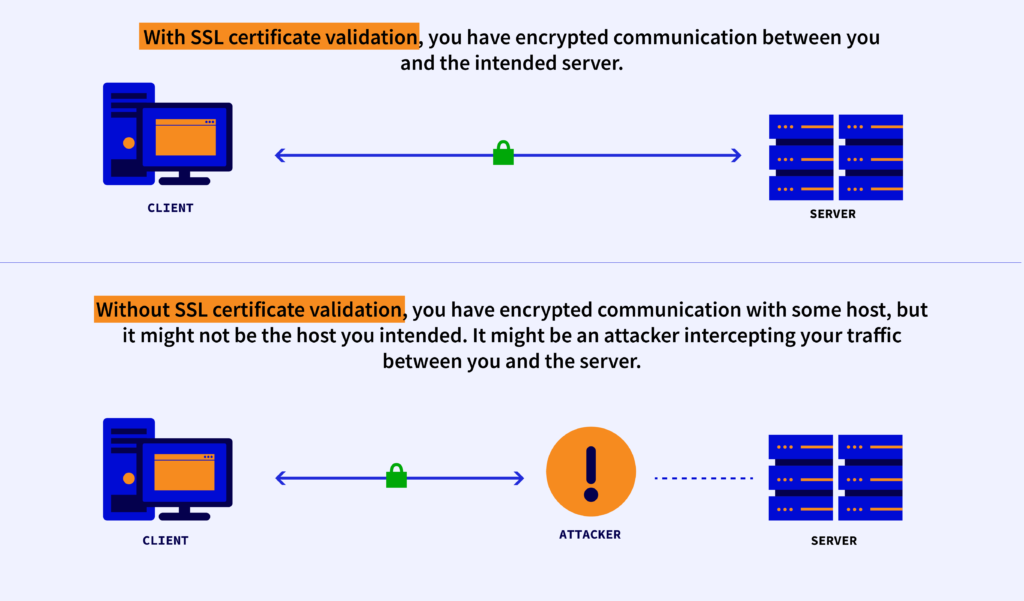
If an employee uses a home wireless network or public network that will give chance to the malicious actors nearby can easily spy on their connection and harvest confidential information. For this reason, employees should not use unknown Wi-Fi unless they are using VPN.
- Password:
Using a weak password is one of the reasons for being hacked in remote working. So, employees should practice using a stronger password with the randomly generated number. Moreover, they should practice using a password manager.
- File-Sharing:
Employees should practice sharing unencrypted data. Companies may be thinking they are because their encrypted data are stored in their server. While The company information can be theft when encrypting data in transit from one place to another.
- Email Scam:
If any email scam occurred companies should be responsible for that because when remote working started most of the employees did not have enough training and Idea about remote learning. So companies should do a workshop to prevent this situation and educate their employees about cyber security and its threat.
- Work from home security policy:
· Clearly state that which positions are eligible for remote work.
· List the tools and platforms they should be using.
· Give guidelines to the employees to follow steps if they have been compromised.
References:
- https://link-springer-com.ezproxy.lib.ucalgary.ca/chapter/10.1007%2F978-3-030-78645-8_74
- https://www.theguardian.com/technology/2021/jun/17/ransomware-working-from-home-russia
- https://heimdalsecurity.com/blog/cybersecurity-issues-with-remote-work/
- https://en.wikipedia.org/wiki/Ransomware
- https://www.csoonline.com/article/3236183/what-is-ransomware-how-it-works-and-how-to-remove-it.html







![Figure [1] : Filing tax forms online](https://wpsites.ucalgary.ca/isec-601-f21/wp-content/uploads/sites/115/2022/02/hi-taxform-ipad-hands-852-8col.jpg)