What is QNAP Systems?
QNAP systems is a Taiwanese company that specializes in network-attached storage (NAS) devices. A NAS device is a data storage device that connects to a network instead of directly connecting to a computer. These devices have a processor, their own operating system, and can easily be accessed by multiple people. They are used for storing files, sharing files, and surveillance applications. Here is how a NAS device looks:

So what happened?
Unfortunately, a new ransomware group has emerged called DeadBolt. This group was able to encrypt QNAP NAS devices worldwide, using a vulnerability they found in the device’s software. They started these attacks on January 25th, 2022, and were able to encrypt the files on the devices. They also changed all the file names by adding a .deadbolt extension to the end. When QNAP customer’s, tried to log into their NAS devices, they were greeted with this:
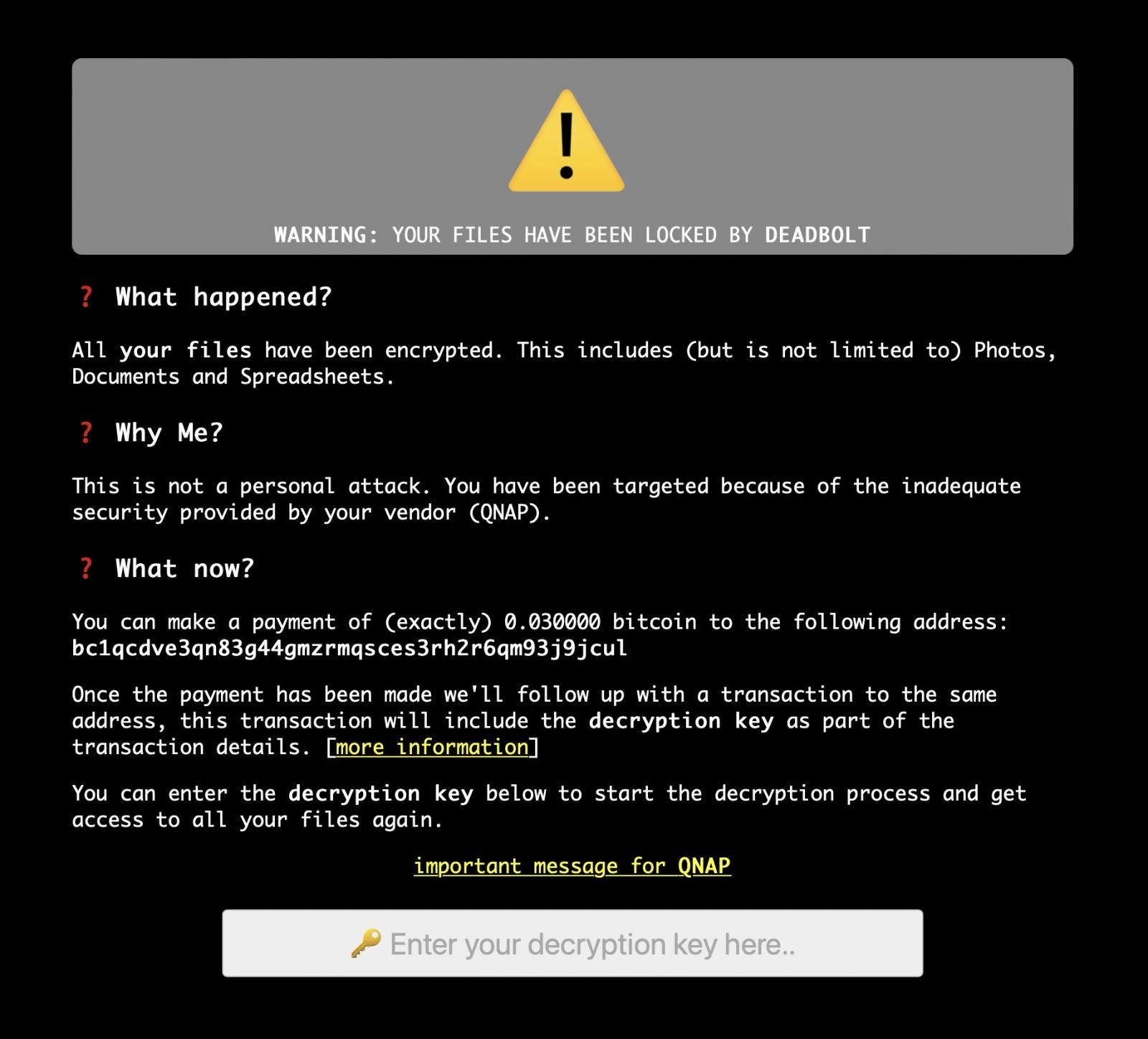
Source: https://www.bleepingcomputer.com/news/security/new-deadbolt-ransomware-targets-qnap-devices-asks-50-btc-for-master-key/
I want to highlight a part of the ransom note which seems somewhat funny but also pretty interesting. It is the section under why me?, where the hackers seem to claim that it is not a personal attack and that the customers should blame the inadequate security of QNAP instead. At the end of the ransom note, the hackers demand 0.03 bitcoin ($1400 Canadian dollars) payment to a bitcoin address that is unique to each victim, so that the customer can be given a decryption key, which they can use to decrypt all of their files. The hackers also give instructions on how to obtain the decryption key once the victim makes the payment.
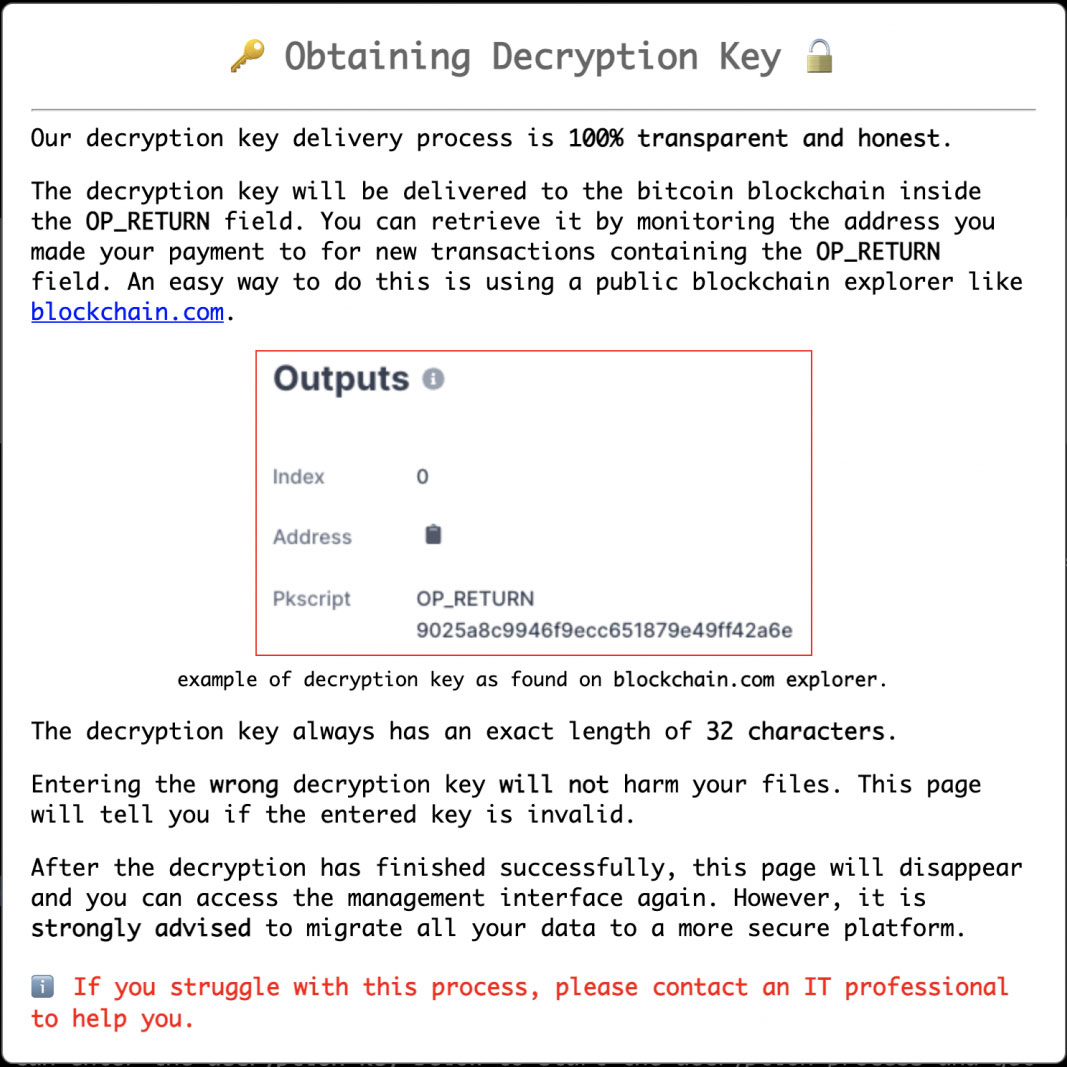
Source: https://www.bleepingcomputer.com/news/security/new-deadbolt-ransomware-targets-qnap-devices-asks-50-btc-for-master-key/
Furthermore, the ransomware group also sent a direct message to QNAP. On the bottom of the ransom note which I showed above, there is a link called “Important message for QNAP”. When the victims clicked on that link, it gave them this message:
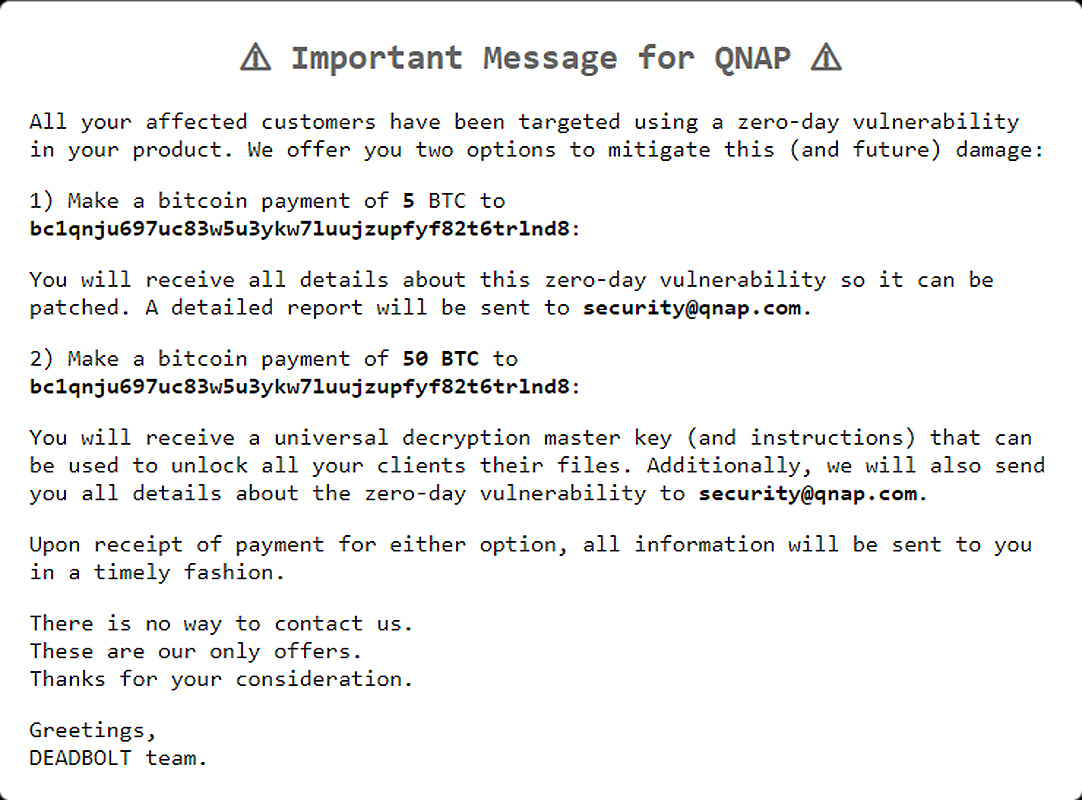
Source: https://www.bleepingcomputer.com/news/security/new-deadbolt-ransomware-targets-qnap-devices-asks-50-btc-for-master-key/
In this message to QNAP, the attackers give the company 2 options to deal with the issue. The first option is that QNAP would pay the attackers 5 bitcoin ($234,240 Canadian dollars) and in return, the attackers would reveal the vulnerability in the QNAP system which allowed them to hack the devices. This would then allow QNAP to fix that vulnerability and prevent further damage. The second option is that QNAP would pay the hackers 50 bitcoin ($2,342,460 Canadian dollars) and in return, the hackers would tell QNAP about the vulnerability and give QNAP a master decryption key which could be used to decrypt all of the victim’s files.
How were the victims feeling about this attack?
Well, after this attack had occurred, many of the victims were confused and hurt by it. These customers had been using those NAS devices for years and had many important files and information stored on them. Not being able to access those files anymore, left them in a state of worry. Multiple people ended up paying the ransom and all were able to use the decryption key to decrypt their files. One of the thousands of victims of this attack was Lex Fridman, an MIT research scientist and this was his reaction.
What was QNAPs response?
The day after the attacks had started, so on January 26th, 2022, there were over 3600 devices that had been affected by this attack. QNAP did not give in to the demands of the attackers and instead tried to find and fix the vulnerability themselves. After doing some research, QNAP thought that they had found the vulnerability and forced an update onto all of the affected devices, improving their devices to an updated firmware. However, with this forced update, there came controversy. Many of QNAPs customers were furious with this forced update and believed that they should have been given a choice whether they wanted this update or not. The reason for this is the forced update ended up causing several different issues. First of all, even though it seemed the update was able to prevent more devices from getting hacked, a customer claimed that his device still got hacked even after the update. Another issue was that some of the functionalities that the customers depended on, ended up either being removed or changed after the update which made things harder for them. For those whose devices had already been encrypted, which was thousands of them, the update did not decrypt their files. In fact, it even made matters worse for some people as they claimed that due to the update, they couldn’t even use the decryption key anymore which they had bought by paying the ransom.
Emsisoft Decryptor
The only solution at the moment is for the victims to pay the ransom so that they can get the decryption key. Since many people were claiming that even after paying the ransom, their decryption key wasn’t working, a New Zealand anti-virus company called Emsisoft made a decryptor that would work. However, in order for them to use this decryptor, they still need the decryption key first which means they still have to pay the ransom.
My thoughts on this situation
After doing lots of research on this topic, it seems pretty obvious to me that the one at fault here is QNAP. Yes, you could say that it is actually the attackers who are more at fault, but the thing is, QNAP is the one that should have prevented these attackers. We all know that hackers and ransomware groups are inevitable, there will always be people out there that try to make a living this type of way, and it is the duty of these tech companies such as QNAP to recognize these types of threats and to make sure that their system is protected from such attacks. The fact that there was this type of vulnerability in their system, and QNAP had no clue just goes to show how badly they failed at that duty. Even now, it isn’t confirmed whether or not QNAP has managed to find and fix the vulnerability. So obviously, this situation could have definitely been avoided if QNAP had stronger security. On top of that, I don’t approve of the way that QNAP responded to this attack. Instead of forcing this update which created so many problems for the customers, they should have exercised transparency by telling the customers about the security vulnerabilities and the possible side-effects of the update.
Sources
- https://threatpost.com/conti-deadbolt-delta-qnap-ransomware/178083/
- https://www.bleepingcomputer.com/news/security/qnap-force-installs-update-after-deadbolt-ransomware-hits-3-600-devices/
- https://www.bleepingcomputer.com/news/security/new-deadbolt-ransomware-targets-qnap-devices-asks-50-btc-for-master-key/
- https://www.zdnet.com/article/decryptor-released-for-deadbolt-ransomware-affecting-qnap-nas-devices/
- https://walletinvestor.com/converter/bitcoin/usd/50

Great Post, Around 2,454 companies use Qnap. The companies using Qnap are most often found in United States and in the Information Technology and Services industry. Qnap is most often used by companies with 10-50 employees and 1M-10M dollars in revenue. Thank for providing such an informative post.
This was a really interesting post. It is interesting that instead of paying the ransom and trying to help their customers they would immediately dismiss the attackers and try to find a solution themselves. If I were the QNAP CEO I would take the second option and try to regain some customer faith and refund anyone that already paid for the decryption key. It seems that the only thing QNAP has done is alienate and anger their user base with their forced update. Given the fact that this is a very targeted attack towards QNAP, I wonder if the attackers had some sort of personal vendeta against them.
This is a very good post and it shows me how QNAP has done many things wrong with the hack. First of all, for a company that provides storage devices to actually fail to ensure the security aspects of their products is itself full of mistakes. What is even more incomprehensible is that this company’s mandatory update of the product neither worked nor asked for the customer’s opinion. While we shouldn’t try to pay hackers, that doesn’t mean waiting for your customers to pay themselves either. All in all, the thing to consider is not just how the hackers went about blackmailing customers, but what should go deeper is the disregard for cyber security by these tech companies.
I suppose QNAP tried creating a solution themselves because a) Giving in to the attackers demands sets a precedent that attacks like Deadbolt’s are an effective way to make money, and hat QNAP perhaps is a good target for such attacks, and b) It would probably cause further distrust for a security company if they were not able to engineer a solution; they could risk looking like amateurs, and who wants to buy a storage device from security amateurs. In the end, it appears the solution did not solve the exploit and actually made the situation worse for many customers, but I cannot look down on QNAP, as creating a device that can withstand global public scrutiny in bug testing is incredibly difficult, though they are still responsible for their failure. Thank you for the post, I did not know of team Deadbolt’s escapades until now.