Recently, Apple has patched two zero-day vulnerabilities in iOS by releasing security updates for users to protect themselves. The first zero-day bug was founded by an anonymous researcher, Meysam Firouzi, and the second one founded by Siddharth Aeri.[1] Both of these zero-day attacks have posed a risk to all iOS users, the first one was a memory corruption bug in the IOMobileFrameBuffer which has affected the iOS system, iPadOS, and macOS Monterey. The second one was a Safari WebKit bug in iOS systems and iPadOS where websites were able to track your browsing activity and possibly reveal users’ identities. Additionally, the zero-day vulnerabilities left the opportunity for Pegasus spyware on iPhones to be installed. Which allowed hackers to gain access to users’ information that is stored on their phones.[1]

What is Zero-day?
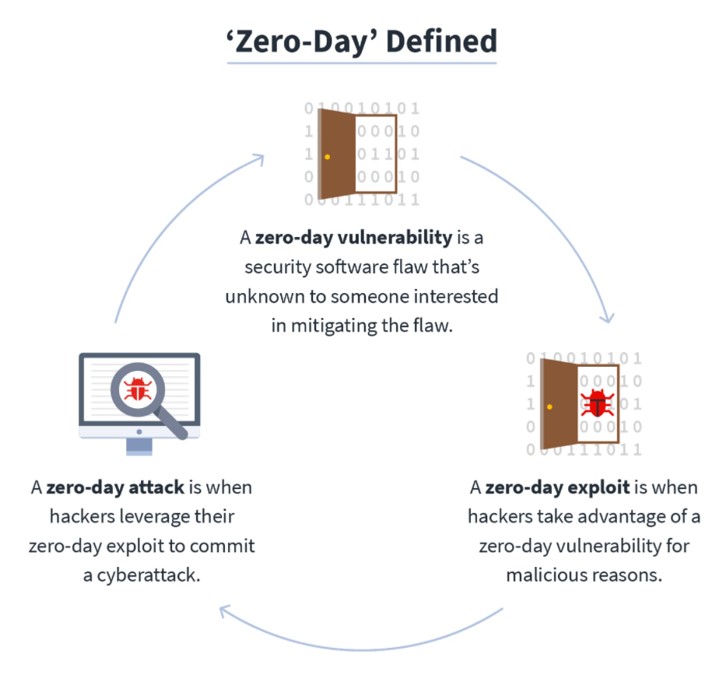
A zero-day exploit is a complex cyberattack[2] in which hackers could take advantage of a software security system due to a flaw in it. This flaw is not noticeable to any software developers and only noticeable to hackers. A zero-day is executed in three steps, first hackers will notice a flaw in the software system, this is known as a zero-day vulnerability. Secondly, hackers will take advantage of the software system, this could be done by the use of malware. Lastly, hackers will follow through with a zero-day attack, this is where hackers will leverage their zero-day exploit to carry out a cyberattack[3]. This could lead to an invasion of privacy, such as identity theft where hackers will be able to steal the identities of individuals.
What Hackers look for in a Target
Oftentimes, hackers will look for many targets with the most vulnerable system, these systems with potential vulnerabilities include; operating systems, web browsers, office applications, open-source components, hardware and firmware, and the internet of things (IoT)[6]. Along with vulnerable systems as a target, hackers will also look for vulnerable individuals. These victims can include those who use a browser or operating system that was already vulnerable, to begin with, those with valuable confidential data, government agencies, political targets and/or national security threats, and large businesses[6].
In-depth Process of Zero-Days (how it works)
Hackers will first discover that there is a flaw in the software system that developers never noticed before. Next, the hacker will write a code that will implement an exploit while the vulnerability is present, this is when developers are in trouble because they are too late to fix it meaning they have ‘zero-days’ to fix it. Researchers will become aware of this vulnerability in the system and announce it to the public, telling them that their personal information may be at risk. Researchers will also release antivirus signatures, but this will only help if the hackers used malware to target the vulnerability in the system. The antivirus signature helps researchers and developers to identify the virus and quickly implement a security patch to eliminate the virus. Lastly, once the security patch is released users’ will need to download this patch onto their device[5].
How do you avoid these attacks?
Zero-day vulnerabilities are threatening and are often detected when it is too late (which is where the name “zero-day” came from because you have zero days to fix the problem) but there are ways to protect yourself from these attacks despite the software system itself having a flaw in it. Down below are a few ways to protect your data and identity.[3][4][5]
- Limit the number of applications you download (fewer applications means fewer vulnerabilities)
- Keeping software system up to date
- Using antivirus software
- Using a firewall
- Vulnerability scanning
References
[3] https://us.norton.com/internetsecurity-emerging-threats-how-do-zero-day-vulnerabilities-work.html
[4] https://www.sophos.com/en-us/security-news-trends/security-trends/zeroday-threats
[5] https://www.fortinet.com/resources/cyberglossary/zero-day-attack
[6] https://www.kaspersky.com/resource-center/definitions/zero-day-exploit

This was really cool to learn about! I was confused on what you meant by zero-day in the intro, but your explanation was great. I’ve always viewed Apple as a company that’s always focused on protecting their users’ sensitive data (keychain, small green/orange LEDs turning on beside your selfie camera when your mic/camera is on, emphasizing on encrypting all your data, etc). But this even showed that even the slightest bug can have catastrophic consequences. Thanks for sharing!
Thank you for your comment! Yes I agree, the smallest bug can cause a lot of issues even if the bug appeared to be minor at first.
With the extent of the attackers out in the world and the widespread knowledge of computer science and software, it really discourages someone from starting an online business, or releasing software. When you sell a product, you have to be aware that SOMEONE is going to find a flaw and exploit it. You must contend with everyone in the world with access to a computer, and if there is a flaw, you can be sure that eventually someone will find it and use to hurt someone or something. Thank goodness for the researchers who find security flaws like in this case, and restrict the damage before it becomes extensive. The best defense against cybercrime are white collar hackers. Thank you for the insightful post.
Thanks for your thoughts! It definitely does discourage someone to release a new product for that exact reason, it also seems that there’s always going to be a flaw in something that is created.
Hi,
Interesting post! I didn’t know what zero-day exploits were until this post. A large company like Apple and other large tech companies that have been producing technology products for several decades have gone through cycles of new technology (Ex Popular languages like C/C++, Ruby on Rails, Java, and now its Javascript and Python), and I wonder if the transition of code bases (if it happens) to new tech could result in these vulnerabilities remaining unfound. It’s kind of like a bias in a way where a code base has been used for decades previously and we think its secure. I guess this is part of the reason code reviews are so important!
Thank you for your comment! I think that it could result in new vulnerabilities since there are going to be flaws in it that could be unnoticeable to the people who created it as opposed to hackers who are trying to exploit it.
Hello,
That was an intersting post to read! I have heard that zero-days attacks may lead to devastating and it starts to be so common these days as the only people who knows about these attacks are the attackers themselves. It became scary how phinshing became so common and new ways are increasing every day with new methods. I believe that there should be a kind of protection on these source codes and people should read the code before using it. But Overall it was a well explained and insightful post!! Thanks!
It was an interesting read.
I didn’t know anything about zero-day until I read your post. I don’t understand how these companies, who are designing softwares since over a decade can have such vulnerabilities in their software security system. But this also makes me think that no matter how secure your software is, there will always be someone smarter than you who will find a flaw.
Overall, this was very informative and well written post.
Zero days attacks are always eventful. It always makes me question, when a specific update or software is released, how much of a race is it to find a vulnerability and I wonder if companies higher security firms to find these vulnerabilities in order to fix them before malicious hackers do, or maybe there is a bounty that gets put out for anyone to find said vulnerabilities. I think those points listed to protect yourself are some perfect, catch all steps everyone can take that don’t involve a whole lot of knowledge about computers. And luckily, some of those are already setup by default (like the firewall and antimalware software with Windows Defender).
I think you should have also mentioned the economy of the zero-day attack. I heard that zero-day exploits can go up to a million dollars on the black market and most buyers tend to be individuals who are involved in corporate espionage. The reason why they are so expensive is that a zero-day attack is devastating to the company and the software. Additionally, the amount of work that is put into finding the exploit is time-consuming which is why people will pay big bucks to get their hands on this. However, I would like to get your opinion on what can the companies do to avoid zero-day attacks on their most prized software?
Informative post! I wasn’t aware of zero-day exploits until I saw this post. Your explanation of this exploit and how threatening it can be was incredibly easy to understand. It really is frightening how this exploit is basically the embodiment of the phrase “it’s already too late” as the attacker already knows what vulnerabilities and loopholes exist while the security experts don’t. It’s because of this fear that I support the use of white-hat hackers or bug bounty hunters.
It was very informative reading your post on zero-day attacks. I have never heard of knew much about these attacks until coming upon this post. I think it is extremely important to test software for weaknesses and possible exploits as much as possible before releasing it to general population. The steps you mentioned in your post are great ideas on how to protect yourself from these attacks. Great post!
Great post! I didn’t know what zero-day vulnerability was before reading this article. The thing that scares me is as a software developer it’s hard to find this kind of flaws and as you said in your post that it’s too late when they’re detected and this reminds me of a phrase that we were taught in class at the beginning of the term i.e., you need to think as an attacker before defending a system.
Great post!
Before reading your blog, I always thought “Zero-day” was just a cyberpunk name randomly given by some hackers. I didn’t know the meaning of it. Your blog is very helpful for me to understand the meaning of “Zero-day”.
My mother is a fan of the iPhone. Even though she has a CPSC degree, I don’t think she is professional in Computer Science. She always believes that iOS is secure, but I don’t think so. I believe every operating system has vulnerabilities and can be attacked by malware. I will show this blog to her to prove my thoughts.
Zero day exploits are always tons of fun to hear about. They’re the secret superweapon lurking in the hands of hero and villain alike. One important part that you missed about zero day exploits however is that attackers usually like to keep them hidden for as long as possible, and use them only when its important to attack a service immediately. The moment a zero day exploit is used, it gets patched as soon as possible, so government agencies like the CIA own stockpiles of these exploits and are always on the hunt for more, as they’re crucial to lots of their investigations on cybercrime, and incredibly strong when used in tandem with other vulnerabilities or even other zero day exploits.
Excellent post talking about these! It seems like there were more than once student in this class who were unaware of these. It’s always fun to see the fireworks when these go off, and the residue can lead to other attacks or other zero day exploits if stuff isn’t patched fast enough or well enough.