The spyware has been around for more than a decade but recently has been making rounds in the news cycle as several governments have confirmed of being a victim of attacks by it.
Recently, both Finland’s Ministry for Foreign Affairs and Poland’s Supreme Audit Office (NIK)[1] have disclosed that they had been the target of the Israeli-developed Pegasus spyware. “The highly sophisticated malware has infected users’ Apple or Android telephones without their noticing and without any action from the user’s part,” Finland’s Ministry for Foreign Affairs announced.[2] It does not come off as a surprise as multiple activists, journalists and even global agencies such as the Human Rights Watch have been attacked by this malware. This deleterious piece of technology has been utilized by various intelligence agencies and governments as a measure of offence, and this raises several questions regarding the threat the spyware poses. And unlike the mythical creature from the Greek fable with which this spyware shares its name, this Pegasus is no myth and should be a subject of much concern when it comes to security and privacy.
What exactly is “Pegasus”?

NSO Group Technologies is an Israeli-based software firm that credits itself as a company that “creates technology that helps government agencies prevent and investigate terrorism and crime to save
thousands of lives around the globe.”[3] Calling it just a software company would do it an injustice as its advanced technology is not applied to produce any everyday user-friendly application, it’s used for much more sinister causes. Back in 2011, the initial version of this notorious Pegasus software was created but it was not until the August of 2016 that it came into the limelight after researchers investigated a failed jailbreak attempt by deciphering a malicious link.[4]
How does it function?

Earlier iterations of the spyware were installed on smartphones via utilizing flaws found in commonly used apps or through spear-phishing, which involves tricking a user into clicking a link that secretly installs the software. It can also be installed manually if an agent can steal the target’s phone or via a wireless transceiver near the target.
“When an iPhone is compromised, it’s done in such a way that allows the attacker to obtain so-called root privileges, or administrative privileges, on the device,” said Guarnieri, who runs Amnesty International’s Berlin-based Security Lab. [5]
By exploiting such vulnerabilities, Pegasus can sneak its way into your phone and get access to all kinds of data such as private photos, messages, calls and so on. The horrifying fact is that all of this can happen just via WhatsApp missed calls or text messages.
How has it posed harm to society?
The reason this piece of software raises grave concerns is because of its scandalous track record. A glimpse at NSO Group’s official website would make you think that such sophisticated software is only being engineered for governments and intelligence agencies to “fight crime and terrorism” but recent events say otherwise. Instances of misuse of this technology include:
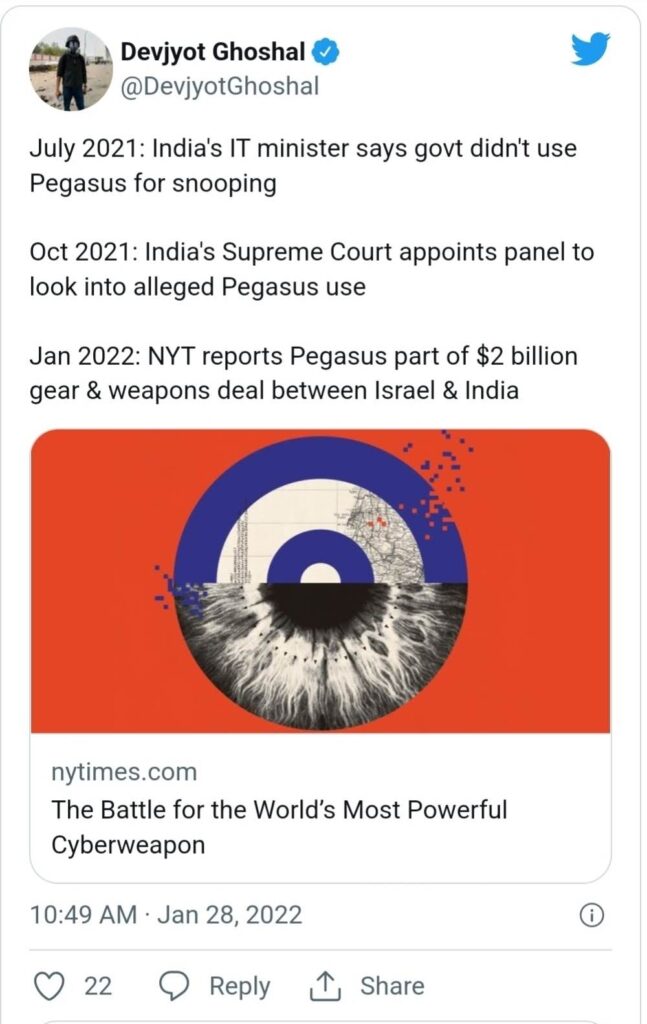
- Governments spying on opposition parties. For example, it has recently been revealed the Indian government purchased this cyber weapon to spy on opposition parties.[6]
- The NSO Group has stated US phone security companies have offered them large sums of cash to acquire access to its signalling network.[7]
- It has been used to spy on various people who are considered to be persons of interest such as journalists, human rights activists and even presidents.[8]
Should we be worried?
Given such severe attacks have posed a threat to mostly major figures such as journalists, world leaders or people who are in positions that could jeopardize governmental power, the average citizen is unlikely to have been targeted by Pegasus at the cost of so much money.
However, the fact that such attacks are possible, and that they could come into the hands of cybercriminals aiming to target the general public is certainly troubling. The thought that governments can have such power where they may paralyze anyone’s phone and keep tabs on the masses should not be pushed under the rug and companies such as the NSO Group should be under immense scrutiny for developing such intrusive tools.
References:
[4]https://www.theguardian.com/news/2021/jul/18/what-is-pegasus-spyware-and-how-does-it-hack-phones

Nice post! I am familiar with the Pegasus software and am aware of the notorious implications it poses for humanity. Pegasus was initially created for use against criminals and undermining terror threats, however, the software has been exploited by both authoritarian and democratic governments to spy on opponents and critics. Although the software was developed with positive intentions, countries have weaponized it to further their own personal and political agendas. For example, Pegasus has been used in Armenia, Azerbaijan, Bahrain, and other countries, to spy on hack activists, bloggers, and members of human rights groups, which all pose a threat to the more dictatorial systems that govern these countries. Furthermore, in January 2022, Pegasus was used by Israeli Police to monitor citizens in addition to foreign nationals. This surveillance was conducted without warrants and judicial supervision. Although these are just a few examples among dozens, it is quite evident that Pegasus, although created for the purpose of enforcing positive change, offers benefits and powers that can be exploited to do more harm than good. This obvious misuse of the software should prompt an international effort to either ban the software or only allow countries with stable democracies to utilize it. Even so, countries with stable democracies may abuse the benefits it offers.
Thank you for your informative post on the topic of Pegasus spyware attacks. This software is especially dangerous as it can allow unauthorized third parties full control over a targeted device. In my opinion, ‘ethical’ spyware does not exist; so long as the financial or political benefits to the company outweigh the repercussions of getting caught, it will be used for malicious purposes, regardless of whatever positive intentions the original developers may claim.
While I do not agree with the use of spyware unless the intended target is beyond a reasonable doubt to pose a great threat to the greater public (sorry for the lawyer speak), my biggest fear regarding something like Pegasus is the chance that the software could be handled inappropriately and get leaked. If the public got ahold of such a piece of software, you can bet that it will be deconstructed and replicated; essentially giving any individual or organization their own version of Pegasus. At this point, public security and privacy would be undermined, and anyone and everyone could be a target for sophisticated spyware. Governments would be in trouble too; many scandals would emerge as people learn to detect the spyware and find that their device is infected. It may almost be better if the innerworkings of Pegasus were to remain a secret, though I don’t like the notion of its existence in the first place. Just food for thought, thank you for the post.
This is an interesting topic. I think that software like this is far too commonly used for malicious purposes that it raises the question of whether it should have been developed in the first place. Even though the original intentions may not be malicious, it will inevitably be misused when it falls into the wrong hands. Preventing such an incident is nearly impossible, so I think the best way to protect against it as any individual in the general public would be to be as careful as possible when clicking links, especially in text messages for this specific spyware.
It seems that cybercrime as a catch-all term no longer seems to describe the varying nature of attacks.
Tools like this are not intended to be used in low-level scamming tactics, but seem rather to be weapons to fuel ideologies. I never really considered the risk that comes with using my phone, as I was always preoccupied with securing my desktop computer. I wonder what common apps have been used to launch this type of attack other than WhatsApp. If you can’t trust a reputable developer, who can you trust at this point?
Very interesting article. I think it bears repeating what several other commenters have mentioned so far: if a large institution or state is using this type of technology to watch individuals, should it be characterized as cyber crime, or is it just another tool already used by states to pursue their own mandates? Also interesting is the question of at what point, if any, that the use of this software is justifiable by institutional players.
Interesting article. It discourages me that governments actively seek the production of things like this to use on their own populace as a form of surveillance, as it feels almost like the software equivalent of creating a bioweapon. Most of its use will be of some immoral intent and work against the population, or worse yet it could be accidentally leaked and end up being used by malicious hackers for their own ends. I hope in the future the production of such tools is frowned upon enough that their usage becomes outlawed.
Hey, nice post Reeshad. The reason I am worried about Pegasus is because if the public gets hold of such a piece of software in their possession it would be a disaster for everyone. Companies and people might try to replicate this software for their own agendas. Therefore, public security and privacy would be undermined. So, in my opinion, an international effort should be made to either ban the software or only allow countries that has stable democracy.