Every day that we are alive on this planet, humanity and the software continues to grow and evolve collectively, if not together. And everyday we are introduced to more and more vulnerabilities in both areas, from the unfortunate effects of Covid-19 to losing your computer data because all you wanted to see were some dancing pigs. Today, I will be sharing with you a new type of malware that has recently arisen in the news known as the Daxin Malware, a complex and undetectable virus that is able to take your information via a shared network.
What is it? Why is it?
The Daxin Malware, or more formally Backdoor.Daxin, is a piece of malware that is able to enter your computer(s) as a backdoor (A backdoor is a type of malware that negates normal authentication procedures to access a system, aka a form of a trojan virus) to allow the controller to insert whatever they would like into it. Not only that, it also has network tunneling abilities (a protocol that allows for the movement of data from one network to another) and can even hijack Transmission Control Protocol/Internet Protocol connections! It was created by china-linked actors, and is considered the most formidable and advanced piece of malware released by China thus far. Although its original purpose was to be used against the Chinese government or related members in its espionage campaign, its an incredibly complex sort of code and can do disastrous amounts of damage to any computer system in its path. It is optimized to hack into the targets network as quietly as possible to steal data and cause overall chaos
TCP/IP stands for Transmission Control Protocol/Internet Protocol and is a suite of communication protocols used to interconnect network devices on the internet.
https://www.techtarget.com/searchnetworking/definition/TCP-IP
Okay, but when was this discovered?
The Symantec Threat Hunter Team, the first to discover that this virus had been lurking around, deduced that this silent virus may have been used since 2013, its age showing how it infects its victims as a Windows kernel driver, which is more uncommon nowadays, only having minor tweaks before then up until November 2021, which is when its more recent attacks occurred. It was thought that one attack that used this virus was back in 2019, in which Daxin and another malware, known as OwlProxy, was found in the computer of a small tech company. They used OwlProxy as a last resort after attempting to deploy Daxin, but failing to miserably. In July of 2020, they used this virus as an attack on the Chinese military, making two unsuccessful attempts to eject a driver with suspicious content that was thought to be Daxin due to the nature of its prior attacks, though it remains unconfirmed.
It was thought that before Daxin, the creators of this virus had been experimenting on something prior, called Backdoor.Zala, which had almost all the features of the Daxin, but was somewhat less advanced in quite a few aspects such as in its networking techniques. The two malwares, however, shared many common libraries, leading many to believe the two shared a codebase.
That’s fine and all, now what does it REALLY do?
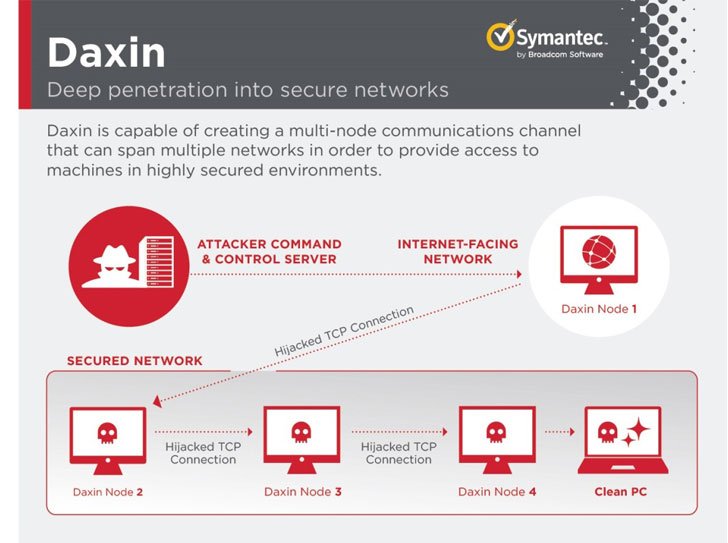
As previously mentioned, Daxin operates as a Windows kernel driver, and is designed to hop from infected system to infected system with a single external command, over one network of course, an astonishing advance in malware since normally most attackers get from node to node one command at a time.
As previously stated, it hijacks TCIP/IP sessions too, and does this by monitoring traffic and finding patterns only to disconnect the client straight after in order to take over the connection, and establish a secure peer-to-peer network over the hijacked network link so that the backdoor can receive communications from the command-and-control network. This method allows it to bypass any sort of firewall and minimizes all risk of being noticed by a security team, since its not opening any sort of new network services, and is instead abusing any real services already running on the infected computers.
“It is designed to be used in long-term strategic attack campaigns. To achieve that, it does the second thing, which is to be as stealthy as possible: It does not open up any new ports; it does not speak with a command-and-control servers explicitly at any point at time.”
Symantec’s Thakur
Dangerous! Is there any cure?
At this moment, much is unknown about the virus, and the discovery team has not said much about it either. In another blog post, it is mentioned how the attacks may originate from tools like PsExec, which was actually what they used to attack that small tech company mentioned earlier, instead of sending files in hopes that their victims will open them eventually.
Knowing this, they simply recommended to use good cyber security practices and to stay safe, although if you’re a member of the Chinese government, you’ll have to be more careful than most.
Everyday is a new danger, so make sure you stay safe and make certain your network is secure!

Interesting post! That’s a terrifying prospect of being able to hack an entire network just by entering one computer in that network. The backdoor aspect only makes it worse, and the fact that it is undetectable makes it a nightmare. This virus could already be deployed and gathering information, since it is undetectable there is no way to tell. With the Russia-Ukraine situation I wouldn’t be surprised to see such a powerful virus being thrown at one of the higher ups in either country, especially since this was originally made to target the Chinese government.
Interesting! That is definitely a covert way to get an information network set up covertly inside of a secure system. Hopefully it doesn’t leak out into public use, because there are definitely some people who would use such a kind of software in a detrimental way. At least we know it exists, so we can start researching into how to detect it on machines through some kind of secrecy slipup or by simply scanning the entire machine for similar code.
What scares me the most is that this malware may have been around since 2013. If it was only discovered to be prominent recently, who knows what else may be out there that is worse and harder to identify?
Interesting post here.
Backdoor malware sounds very intimidating as it goes past regular authentication procedures, especially since it can hop from system to system with just a single command. It seems that there still seems to be many discoveries that have to be made about this and a lot of unknown! Your recommendation is really all one can do when it comes to something like this, and practice good cyber security.
Interesting post here.
Backdoor malware sounds very intimidating as it goes past regular authentication procedures, especially since it can hop from system to system with just a single command. It seems that there still seems to be many discoveries that have to be made about this and a lot of unknown! Your recommendation is really all one can do when it comes to something like this, and practice good cyber security.
Interesting pose! I have never heard anything about backdoor malware and it’s scary that I had no idea about it because this virus goes from system to system and I wouldn’t have known if I had the virus on my system or not, I will make sure to follow the precautions to be as safe as possible because we don’t have much information about the virus.
Good Post! I find it very interesting (and rather scary) that this malware package has been around since 2013! (as another commenter also mentioned). 2013 was 9 years ago! That may not seem like a lot but with how fast new technologies are developing and advancing, 9 years is a long time for something like this to go unnoticed. This may be a credit to the design of this malware package and its emphasis on stealth, but it does make me wonder about what other malware programs are out there? If a piece of malware from 2013 can be implemented only to be found years later, surely there are other lurking programs that have been developed since then that we haven’t found yet.
I wonder how many other viruses go undetected for years, siphoning away our data all the while. Perhaps some of the focus on cybersecurity should be on checking for very “quiet” viruses as well as proactively working to prevent any from getting in. Another idea raised by this post is how much risk cyberattackers face. Going up against the Chinese government is a pretty bold thing to do – or is it? It may depend on where the attackers are located.
This is an excellent post! It’s always interesting learning about malware like this. The fact that this may have existed since as early as 2013 is scary. Who knows how many machines have been infected with this? It reminds me of SQL slammer for some reason, but much stealthier.
This is a fascinating article! The notion of being able to break a whole network simply by entering one machine in that network is alarming. It’s made worse by the backdoor, and the idea that this is untraceable makes it a misery. There’s no way of knowing if this virus has already been deployed and is gathering data because it’s undetected.
Interesting post! If such a virus existed since 2013, then this must mean that there are even more advanced and more undetectable viruses out there. But I also hope as the viruses improve, our ways of combating them also keeps up as well.
That’s a cool virus, its scary to think about but its interesting to think how one infected computer will infect any other computers that are within the same network. Jack Hoskins’ comment really made me view the Daxin virus in a new light because I didn’t even think about how long it had gone without being discovered and since it makes such a good job to hide itself, It definitely is a concerning thought to think of those that are still not discovered that are secretly extracting data.