
Human error causes problem.
Cybersecurity refers to all the technologies, processes and attitudes that aim to protect data, devices, programs, systems and networks from cyber threats and attacks. [1] Experts take all possible measures and precautions to minimize the risk of cybercrime affecting system security.
However, we found that the fact is, most threats to organizational information systems (IS) are due to vulnerabilities and breaches caused by employees. About 72-95 per cent of cyber threats to organizations are due to users’ mistakes. Human error can occur both at home, involving your personal devices and data, and at the workplace, where its consequences can be much farther-reaching. If business data and systems are affected, the company may lose time, money, clients, partners and can even face lawsuits. [9] For years, “human error” has consistently been identified as a major contributing factor to cybersecurity breaches. Several recent reports revealed that 43% of C-Suite leaders who reported a data breach cited human error as the second major cause. The average cost of human errors in cybersecurity breaches was $3.33 million.[7]
From ransomware attacks to serious data breaches, human error invariably plays a role in information security incidents. Almost all successful cyber breaches have one variable in common: human error. Human error can manifest in a multitude of ways: from failing to install software security updates in time to having weak passwords and giving up sensitive information to phishing emails. Yet it remains true that many organizations still fail to take into consideration this important factor when thinking about their information security strategy. [2] Human errors are used by cybercriminals to effect unauthorized access, steal credentials, and infect IT systems and endpoints with malware such as ransomware. Without the human-in-the-machine effect, cybercrime would be much more difficult. Therefore, if we can fully analyze the network security problems caused by human factors, extract potential problems according to the case, reflect and correct the loopholes, and minimize the cybersecurity problems caused by human errors. Then this will have a positive effect on the entire network security environment and greatly reduce the attack methods of cyber criminals. [5]
How many cyber security incidents are caused by human error?
There are three types of human error in cybersecurity. The first type is unintentional human error. Errors of this type result from a lack of knowledge or skill, or perhaps distraction. Some human error, however, is intentional: an IT worker might deliberately take a risk with their organization’s systems that could cause a cybersecurity incident. These errors often violate ethics and laws on data stewardship. The third kind of human error is even more intentional. Malicious error occurs when an employee deliberately makes a system vulnerable in order to steal (exfiltrate) confidential data.
There are the 800 largest data breaches to occur between 2007 and 2019 in the US, how many were the result of human error? The answer is 291, roughly 36%. However, another 47% may have been due to human error as well. Of the 291, 102 are selected for further analysis since enough data exists about them to make that possible. In this dataset, the author identifies three different types of human error in cybersecurity: skills-based mistakes (mistakes in repetitive, familiar activities that do not require conscious thought), rule-based mistakes (mistakes in using a known rule or procedure to respond to a familiar situation) and knowledge-based mistakes (mistakes in using slow, conscious, analytical processes to solve new and unfamiliar problems) and matches them to three different types of vulnerabilities that often cause breaches: system misconfiguration errors, skills-based errors and rule-based errors.
Relevant Researches
Researchers from the Old Dominion University have conducted a cross-sectional survey study of employees in different organizations. Their results suggest that gender has moderate effects on safety self-efficacy, prior experience, and computer skills, but has little effect on action cues and self-reported cybersecurity behaviors. [2]
In addition, According to the research from Vilnius University, there is a relationship between genetically informed traits such as impulsiveness and the likelihood of IT workers to accidentally cause cybersecurity breaches. These personality traits are particularly important due to the long working hours, stress and wide-ranging responsibilities entailed by IT.
Researchers from Middel Georgia State University designed a set of scenarios-based hands-on tasks to measure the cybersecurity skills of non-information technology (IT) professionals. Their study shows the importance of skills and hands-on assessment appears applicable to cybersecurity skills of non-IT professionals. Therefore, by using an expert-validated set of cybersecurity skills and scenario-driven tasks, this study established and validated a set of hands-on tasks that measure observable cybersecurity skills of non-IT professionals without bias or the high-stakes risk to IT. [3]
Survey from cyber security companies
We also surveyed several employees from the industry. Some results are showed as follow:
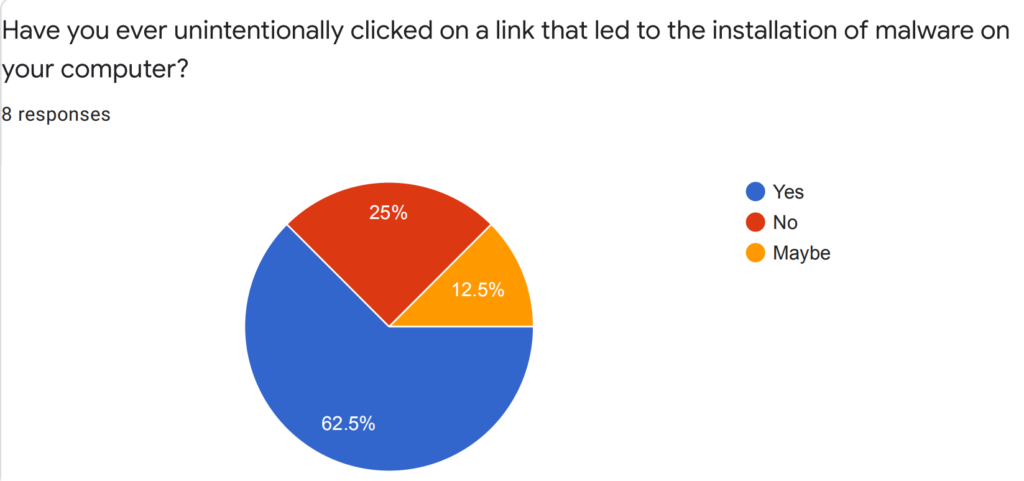
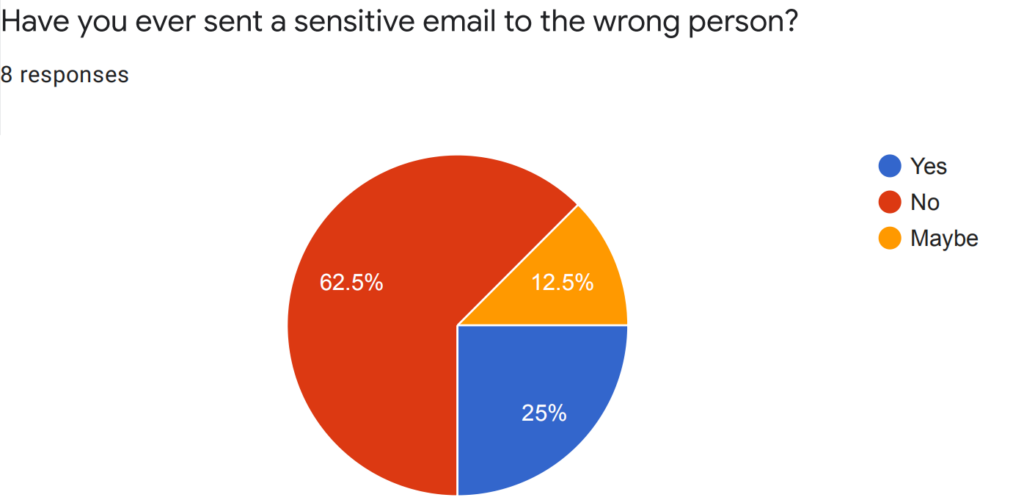

Our Story Map
The format of our project is the Story Map. This blog only contains part of its content. For more details about this topic and our project. Please browser our story map to explore. Link of Story Map:
References
[1]. aAmbrozaitytė, Laima, et al. “Human Characteristics and Genomic Factors as Behavioural Aspects for Cybersecurity. Augmented Cognition, Springer International Publishing, Cham, 2021, pp. 333–350. Lecture Notes in Computer Science.
[2]. Anwar, Mohd, et al. “Gender Difference and Employees’ Cybersecurity Behaviors.” Computers in Human Behavior, vol. 69, 2017, pp. 437–443.
[3]. Melissa Carlton, et al. “Mitigating Cyber Attacks through the Measurement of Non-IT Professionals’ Cybersecurity Skills.” Information Management & Computer Security, vol. 27, no. 1, 2019, pp. 101–121.
[4]. Cornejo, Gabriel A. Human Errors in Data Breaches: An Exploratory Configurational Analysis, 2021.
[5]. Hoske, Mark T. “Advice from Cybersecurity Incident: Cybersecurity Incident: Human Errors Enabled It, but the Triconex Safety Controller Shut down the Plant as Designed, Say Experts with Schneider Electric and ARC Advisory Group. But It’s Still a Call to Action for Industry. Have You Implemented Changes since Then?” Control Engineering, vol. 65, no. 4, 2018, p. 10.
[6]. Maalem Lahcen, Rachid Ait, et al. “Review and Insight on the Behavioral Aspects of Cybersecurity.” Cybersecurity, vol. 3, no. 1, 2020, pp. 1–18.
[7]. Malatji, Masike, et al. “Validation of a Socio-Technical Management Process for Optimising Cybersecurity Practices.” Computers & Security, vol. 95, 2020, pp. 101846–17.
[8]. Khalid Khan, Shah, et al. “A Conceptual System Dynamics Model for Cybersecurity Assessment of Connected and Autonomous Vehicles.” Accident Analysis and Prevention, vol. 165, 2022, p. 106515.
[9]. Kim, Hee Eun, et al. “Systematic Development of Scenarios Caused by Cyber-Attack Induced Human Errors in Nuclear Power Plants.” Reliability Engineering & System Safety, vol. 167, 2017, pp. 290–301.
[10]. Nobles, Calvin. “Botching Human Factors in Cybersecurity in Business Organizations.” Holistica : Journal of Business and Public Administration, vol. 9, no. 3, 2018, pp. 71–88.
[11]. Pollini, Alessandro, et al. “Leveraging Human Factors in Cybersecurity: an Integrated Methodological Approach.” Cognition, Technology & Work, 2021, pp. 1–20.
[12]. Sawyer, Ben D, and Peter A Hancock. “Hacking the Human: The Prevalence Paradox in Cybersecurity.” Human Factors, vol. 60, no. 5, 2018, pp. 597–609.
[13]. Jeremy Straub, “Physical security and cyber security issues and human error prevention for 3D printed objects: detecting the use of an incorrect printing material,” Proc. SPIE 10220, Dimensional Optical Metrology and Inspection for Practical Applications VI, 102200K (15June 2017); https://doi-org.ezproxy.lib.ucalgary.ca/10.1117/12.2264578


Yeah it really amazes me how many security vulnerabilities are caused by human error, For example a I remember an attack by Lazarus that almost cost the bank of Bangladesh 1 billion dollars, where the hackers gained access to the network through an email to employees asking them to download a CV from a website. Also I thought it was really interesting that gender and genetic traits may cause someone to be predisposed to cause security breaches. I’m not too sure how to minimize human error since we don’t have the tech to determine if any email is legitimate as AI is far from being able to that so maybe to prevent this companies need to start training people to adequately deal with cyber security risks and what not. Overall I enjoyed this post!
It makes sense to me that a large about of cybersecurity are due to human error i’d imagine a bunch of normal security errors or mistakes in general are due to human error. I also find the part on how gender affects safety as well as genetically informed traits very interesting, the results for both make sense to me.
Hey, Interesting post!. This reminds me of the lectures when we were discussing vulnerabilities and weakest links. These security systems and the malware they are designed to protect against need to be “dummy” proof while also not inhibiting on users’ functionality otherwise they wouldn’t be used. I definitely have clicked some suspicious looking links that may have been loaded with malware and I think I am a more informed individual regarding security but when 99% of the links I click are safe and show what I think they should show then I become sort of blind to the dangers.
I think the most telling survey results are from the last question. If a service is attached to a large or reputable tech firm, then members of the public are liable to assume that they are secure when they can still be used for malicious purposes (i.e., links embedded in google forms, etc.). Ultimately, services that are used by millions of users will always be vulnerable to malicious users seeking to exploit others, including IT professionals. The best defense long term will be public education and awareness because large tech firms will always have cases where malicious actors slip through their security measures, simply as a function of the number of users that use their systems. As stated in your project, tech companies that want to avoid security breaches in the future are best served by cultivating good security habits in their employees to avoid human-error driven data breaches.
This was a really interesting post, and it was a pleasure to read through the story map you identified. It’s unfortunately not all that surprising that so many of the cybersecurity issues that groups run into are caused by human error. In your report, you identified several suggestions from the University of Leeds for improving the culture surrounding security practices. In your opinion, are any of these suggestions more important, or of a higher priority than others? Or is it more of a contextual analysis depending on other factors?
While it’s not very surprising that human error is a major cybersecurity threat, I mean we all know that a chain is only as strong as it’s weakest link. The real question here is, what can we do to minimize this problem? My answer: Not much, as its extremely difficult to eliminate the human from the equation when cybersecurity is based on protecting humans.
We are living in an age where AI use is becoming more common. I believe someday, they will be used to deal with major cyber-security threats since they can not have any human errors.
But AI are created by humans, so there could be human errors in creating the AI, or perhaps human errors in properly setting up the AI. And what about maintaining the AI and keeping them updated? You can’t make an AI that updates other AIs. Not to mention a great deal of services require human input because, well, the service is for the humans, and where there is human input there could be human error.
It’s true that human errors account for many of the breaches we see nowadays, especially in regards of cryptography where many systems are broken not because of a flaw in the cryptography but rather due to an improper implementation. If we were able to remove the human factor from our systems, concepts such as phishing attacks would probably disappear. I could never tell that this many incidents could be faulted to purely human error. Overall, a very interesting read!
Human error really accounts for a lot of the incidents I’d say we see everyday. From improper implementation to falling for phasing attacks it all can really be chalked up to human error. It is crazy to think about how this will actually always exist as humans will forever be apart of the system unless we choose to make them completely human free which I’m not sure how exactly would be done. In all reality this will probably increase as technology gets more and more integrated into our lives. Its kind of like a never ending game of cat and mouse where someone will find a hole in the system then someone else will fix it learning and the cycle repeats. Overall great read!
Interesting post. Experts focus on taking preventive measures to minimize the risk of cybercrime but ignore that human errors can also cause loopholes. The network security vulnerability caused by such man-made destruction will bring huge losses to users. Research shows that gender and heredity will have an impact on network security vulnerabilities. Does this mean that when selecting information technology professionals in the future, they may make a certain degree of judgment based on these factors? Whether it is intentional or intentional human error, its staff should be fully trained and periodically audited. Ensure that their work efficiency is guaranteed. Users should also be careful to click suspicious links to protect their network security.
Interesting post. Experts focus on taking preventive measures to minimize the risk of cybercrime but ignore that human errors can also cause loopholes. The network security vulnerability caused by such man-made destruction will bring huge losses to users. Research shows that gender and heredity will have an impact on network security vulnerabilities. Does this mean that when selecting information technology professionals in the future, they may make a certain degree of judgment based on these factors? Whether it is intentional or intentional human error, its staff should be fully trained and periodically audited. Ensure that their work efficiency is guaranteed. Users should also be careful to click suspicious links to protect their network security.
Interesting post. Experts focus on taking preventive measures to minimize the risk of cybercrime but ignore that human errors can also cause loopholes. The network security vulnerability caused by such man-made destruction will bring huge losses to users. Research shows that gender and heredity will have an impact on network security vulnerabilities. Does this mean that when selecting information technology professionals in the future, they may make a certain degree of judgment based on these factors? Whether it is intentional or intentional human error, its staff should be fully trained and periodically audited. Ensure that their work efficiency is guaranteed. Users should also be careful to click suspicious links to protect their network security.
Interesting post. Experts focus on taking preventive measures to minimize the risk of cybercrime but ignore that human errors can also cause loopholes. The network security vulnerability caused by such man-made destruction will bring huge losses to users. Research shows that gender and heredity will have an impact on network security vulnerabilities. Does this mean that when selecting information technology professionals in the future, they may make a certain degree of judgment based on these factors? Whether it is intentional or intentional human error, its staff should be fully trained and periodically audited. Ensure that their work efficiency is guaranteed. Users should also be careful to click suspicious links to protect their network security.
Interesting post. Experts focus on taking preventive measures to minimize the risk of cybercrime but ignore that human errors can also cause loopholes. The network security vulnerability caused by such man-made destruction will bring huge losses to users. Research shows that gender and heredity will have an impact on network security vulnerabilities. Does this mean that when selecting information technology professionals in the future, they may make a certain degree of judgment based on these factors? Whether it is intentional or intentional human error, its staff should be fully trained and periodically audited. Ensure that their work efficiency is guaranteed. Users should also be careful to click suspicious links to protect their network security.
Interesting post. Experts focus on taking preventive measures to minimize the risk of cybercrime but ignore that human errors can also cause loopholes. The network security vulnerability caused by such man-made destruction will bring huge losses to users. Research shows that gender and heredity will have an impact on network security vulnerabilities. Does this mean that when selecting information technology professionals in the future, they may make a certain degree of judgment based on these factors? Whether it is intentional or intentional human error, its staff should be fully trained and periodically audited. Ensure that their work efficiency is guaranteed. Users should also be careful to click suspicious links to protect their network security.
Interesting post. Experts focus on taking preventive measures to minimize the risk of cybercrime but ignore that human errors can also cause loopholes. The network security vulnerability caused by such man-made destruction will bring huge losses to users. Research shows that gender and heredity will have an impact on network security vulnerabilities. Does this mean that when selecting information technology professionals in the future, they may make a certain degree of judgment based on these factors? Whether it is intentional or intentional human error, its staff should be fully trained and periodically audited. Ensure that their work efficiency is guaranteed. Users should also be careful to click suspicious links to protect their network security.
Interesting post. Experts focus on taking preventive measures to minimize the risk of cybercrime but ignore that human errors can also cause loopholes. The network security vulnerability caused by such man-made destruction will bring huge losses to users. Research shows that gender and heredity will have an impact on network security vulnerabilities. Does this mean that when selecting information technology professionals in the future, they may make a certain degree of judgment based on these factors? Whether it is intentional or intentional human error, its staff should be fully trained and periodically audited. Ensure that their work efficiency is guaranteed. Users should also be careful to click suspicious links to protect their network security.
Interesting post. Experts focus on taking preventive measures to minimize the risk of cybercrime but ignore that human errors can also cause loopholes. The network security vulnerability caused by such man-made destruction will bring huge losses to users. Research shows that gender and heredity will have an impact on network security vulnerabilities. Does this mean that when selecting information technology professionals in the future, they may make a certain degree of judgment based on these factors? Whether it is intentional or intentional human error, its staff should be fully trained and periodically audited. Ensure that their work efficiency is guaranteed. Users should also be careful to click suspicious links to protect their network security.
Great research! It’s interesting to learn that human error causes such a substantial amount of the breaches, but also not surprising at the same time. While I believe tech professionals try to make it secure for companies to use their tools and platforms, there is so much they can do as there will always be people finding new and creative ways to exploit the system. I believe based on the research you conducted, it shows that education on employees can be enhanced to prevent such errors.
Interesting post. I would say that it’s not very surprising that human error causes so many breaches. I think there definitely should be some sort of solution to help decrease the number of breaches from human error. This is inevitable though, as human error is something that can’t be avoided.
It’s not surprising that so many security breaches are caused by human error, at the end of the day, phishing scams and different kinds of malware are very hard to spot in emails and links that look perfectly normal. Considering the amount of people using computers and surfing the web and the amount of people that have a good amount of knowledge about information security, these numbers will stay the same unless more and more people try to actively learn about these security dangers and take action against such scams. Great post!
It’s interesting how most often, the easiest vulnerability to exploit is actually human psychology. A good hacker knows how to manipulate people as well as machines.
It’s really weird to think about how prevalent human error is exploited for malicious reasons, especially considering how simple it would be to fix ideally (I’d assume just being educated would allow one to be much more receptive to potential risks). It is kind of funny, since I had always assumed it would be extremely high level hackers that were the reasons computers were hacked into.
I just another post where it was discussed about how AI can be used to deal with cybersecurity issues (regarding verification and authentication).
When it comes to building security, there is bound to be human errors around the world which are intentional. So, maybe AI can take over these tasks once and for all one day but I am not sure if that is likely to happen since that would run a lot of people out of their jobs. However, when it comes to the intentional malicious work, that is just criminal work and these people should be held accountable and be punished.
All in all, this was a really informative post.
It very fitting and poetic that humans are always the biggest threat/vulnerability to what we create for security purposes.