Cyberattacks is becoming a threatening concern in today’s society. Many of us should be aware of the constant cyberattack news spreading around the world with the rising tensions between Russia and Ukraine. Big technology companies such as Google, one of the most popular search engines around the world is making a big investment into the cybersecurity sector. The trillion dollar company has now agreed to purchase the cybersecurity firm Mandiant in an all-cash deal valued at approximately $5.4 billion. Google’s second biggest purchase ever reveals their commitment to investing in the development of cyber security to protect the company and users/consumers from dangerous online threats while using Google Cloud.
Why is Cybersecurity so Important for Companies?
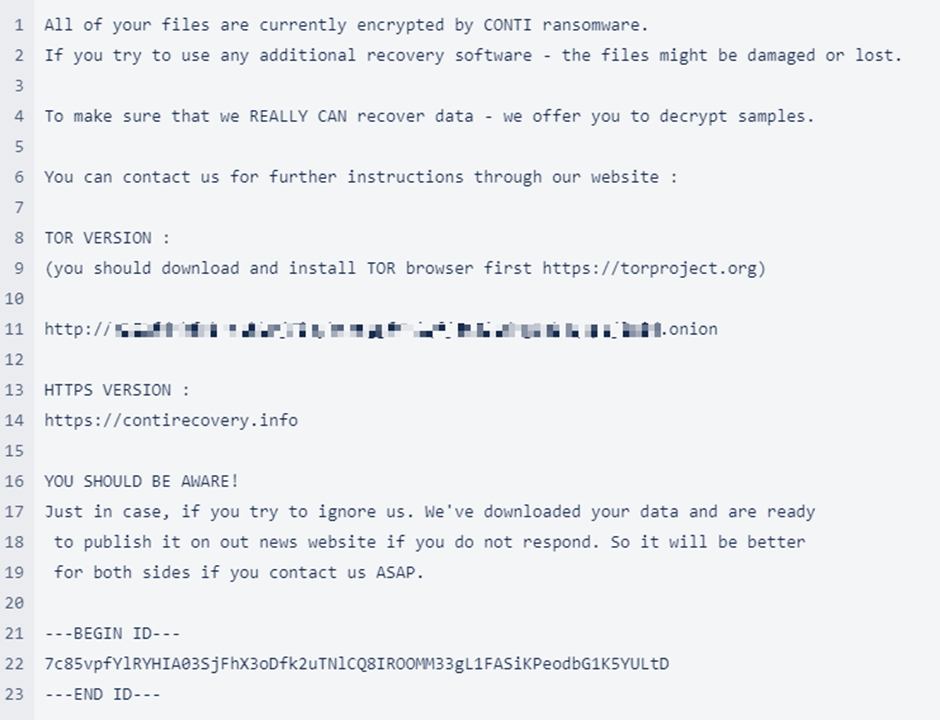
- Cybersecurity is of utmost importance to companies because it allows for private information/data to remain private. Stolen data can lead to lawsuits and a hefty ransom.
- As a company the main goal is to generate income when cyberattacks occur there can be large financial costs that can truly damage a company’s finances. If a company producing products gets cyberattacked that can lead to supply chain interferences digging a deeper hole for the company.
- Lastly, the business model around companies is to provide excellent services to the consumer/user. A companies reputation plays a big role in the ability to draw in consumers. A loss of confidence in the company from consumers would be detrimental to any company. Cybersecurity protects individuals/businesses from private information being accessed, financial bleeding, and loss of consumer trust.
Who is Mandiant and What do they do?

- Mandiant is a cybersecurity firm most known for their efforts in revealing the devastating SolarWinds attack that decimated computers across the United States federal government.
- In Google’s case Mandiant’s operations will require the work of 600+ security consultants and 300+ intelligence analysts on the Google Cloud to create a forcefield security operations suite.
- Services ranging from consulting on cybersecurity to identifying upcoming/potential threats and testing company’s ability to digitally defend.
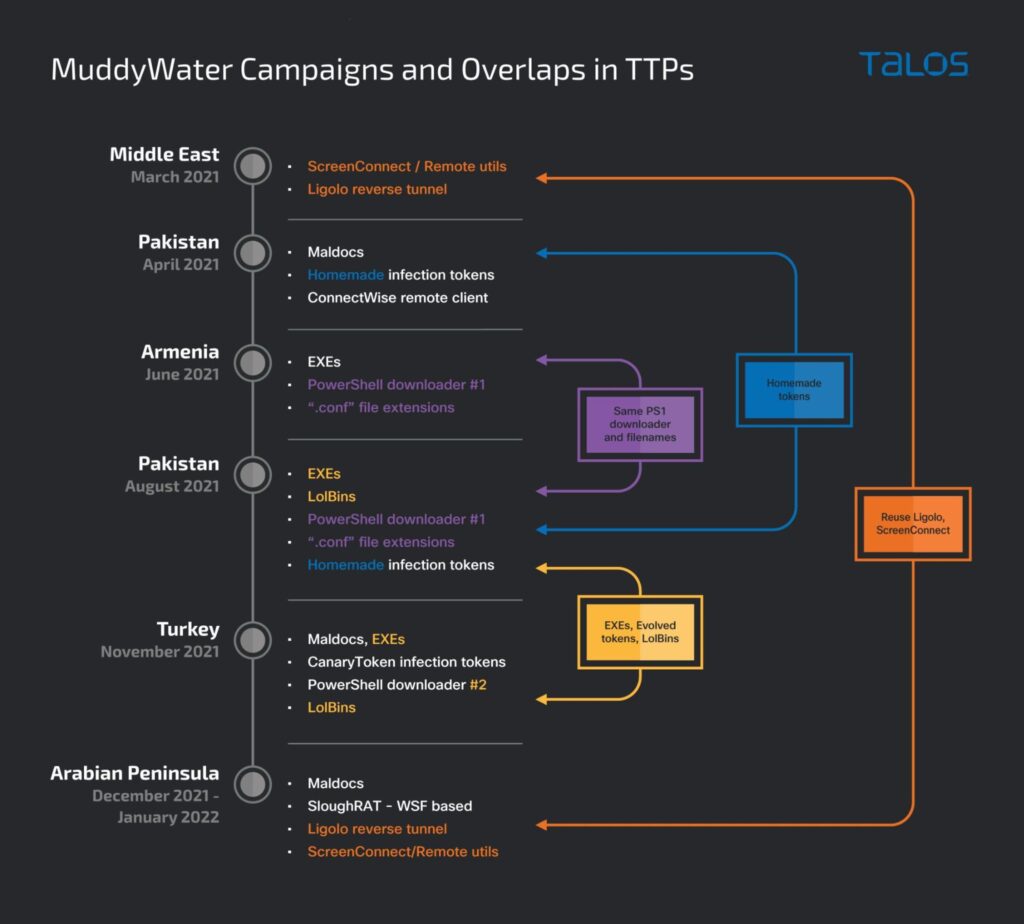
- Mandiant will help reinforce the dangers foreseen in the cyber security sector following the wave of cyberattacks from Russia and others as the geopolitical tensions rise.
Outlook of Cyber Security for the Future
As mentioned by Mandiant CEO Kevin Mandia in a press statement “There has never been a more critical time in cybersecurity. Since our founding in 2004, Mandiant’s mission has been to combat cyber attacks and protect our customers from the latest threats”. Cybersecurity could be the difference maker where a consumer must choose between two companies that offer a cloud service. Cybersecurity companies such as Mandiant will be looking to “deliver expertise and intelligence at a scale, changing the security industry.”(Kevin Mandia). However, this deal is not set in stone yet as there are antitrust enforcers that could potentially block this deal from concluding. Ultimately cyber security will continue trending upwards as our world continues to be driven by new technologies requiring protection from potential dangers in the world of technology.
References
Grant, Nico. (2022, March 8) Google to Buy Cybersecurity Firm Mandiant for $5.4 Billion. Yahoo Finance. Retrieved from https://finance.yahoo.com/news/google-buy-cybersecurity-firm-mandiant-113342878.html
Ott, Matt. (2022, March 8) Beefing up its cybersecurity, Google buys Mandiant for $5.4B. abc News. Retrieved from https://abcnews.go.com/Business/wireStory/beefing-security-google-buys-mandiant-54-billion-83315471
Vincent, James (2022, March 8) Google is buying the cybersecurity company that uncovered the SolarWinds hack. The Verge. Retrieved from https://www.theverge.com/2022/3/8/22966907/google-buying-mandiant-cybersecurity-outfit-5-4-billion