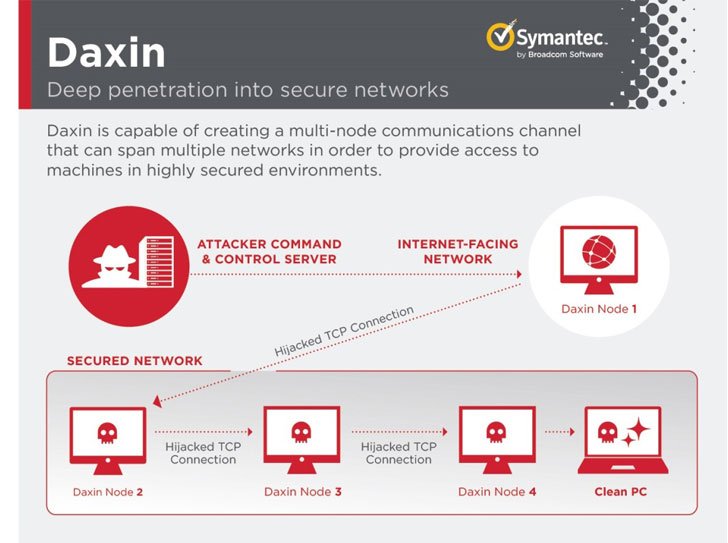
Over the past week, while the concerns have been mounting over cyber attacks initiated from Russia against Ukraine, government, business and investors across the world are shifting to the larger focus of cyber security and information privacy.
If evidences of the cyber security as a solid concern were to be requested from real world, the FBI, and Cybersecurity and Infrastructure Security Agency as well, alerted the U.S. companies over the weekend of the danger of potential ransomware hits, which hold hostage of data internal to an organization until payment – the ransom – is paid to the hacker. As such, the security breach of data cast the cyber security and privacy of users in question.
As covered on the media, ransomware gangs and extortionists have breached 52 US critical infrastructure organizations, including those belong to energy, financial services, government, critical manufacturing, and information technology sectors. Cyber attacks, especially taking the form of ransomware attack, target companies and cause damages including:
- Financial costs
A few cases and facts in focus to spot the damage caused by ransomware attack are provided. Cyber attacks come with a price to pay, and frequently a huge one. As of 2021, companies were cost of up to $4.24 million by cyber attacks on average, which registered an increase of around 10 percent compared to that in 2020 since IBM publishing the data.
- Leakage of company data/privacy
Last week, NVDIA Corp. experienced an ransomware attack and found its company data stolen in the cyber attack. Following the ransomware operation initiated by LAPSUS$, employee passwords, credentials and other information proprietary to NVDIA online were leaked, and the extortionists threatened the company to remove its Lite Hash Rate technology from its graphics cards. Unless the ‘ransom’ was paid through the company’s compliance, NVDIA would be further threatened to more data leakage.
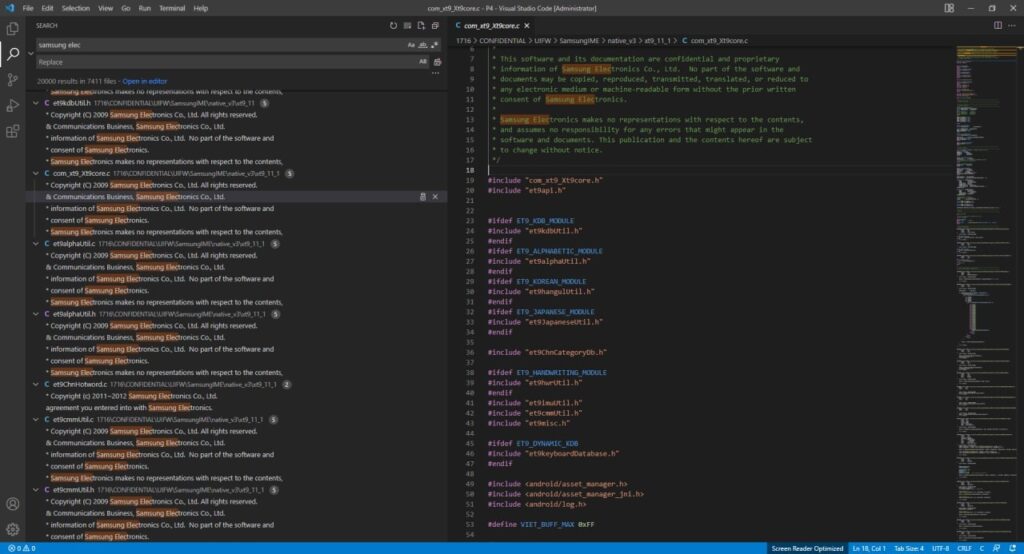
Just a few days after the data leakage at the global leading chipmaker NVDIA, the ransomware gang LAPSUS$ was claiming in high profile to have Samsung Electronics as its another victim, and the time has come to release the data stolen from the global consumer electronics giant.
- Supply chain disruption and reputation damage

The damage that ransomware attacks cause on companies extends beyond technical to reputational and business level. As with the case of Samsung Electronics, loss of consumer confidence and supply chain disruptions are anticipated as LAPSUS$ announced with pride on its Telegram channel to have a taste of biometric authentication information and source code of Samsung and its supplier, Qualcomm.
Cyber Security Risks and Ransomware Here to Stay

Even for large, state-of-the-art tech firms such as Samsung is no easy escape of a target of such ransomware hit. The interest in writing this blog is to inform the persisting challenge of this cyber security concern, in terms of the costs caused and large scale of impact involving multiple stakeholders. In the most recent cases of NVIDIA and Samsung, they alert us the vulnerabilities of data-focused security.
References
Vumetric Cyber Portal. (2022, March 7). FBI: Ransomware gang breached 52 US critical infrastructure orgs. Retrieved from https://cyber.vumetric.com/security-news/2022/03/07/fbi-ransomware-gang-breached-52-us-critical-infrastructure-orgs/
Bracken, B. (2022, March 7). The move comes just a week after GPU-maker NVIDIA was hit by Lapsus$ and every employee credential was leaked. Threatpost. Retrieved from https://threatpost.com/samsung-lapsus-ransomware-source-code/178791/
Hill, M. (2022, March 7). Extortion group teases 190GB of stolen data as Samsung confirms security breach. CSO. Retrieved from https://www.csoonline.com/article/3652335/extortion-group-teases-190gb-of-stolen-data-as-samsung-confirms-security-breach.html
Navillier, L. (2022, March 8). Why Cybersecurity Stocks Are Soaring. Investorplace. Retrieved from https://investorplace.com/2022/03/why-cybersecurity-stocks-are-soaring/





/cdn.vox-cdn.com/uploads/chorus_image/image/67463013/msedge_X9RFhS71eu.0.jpg)