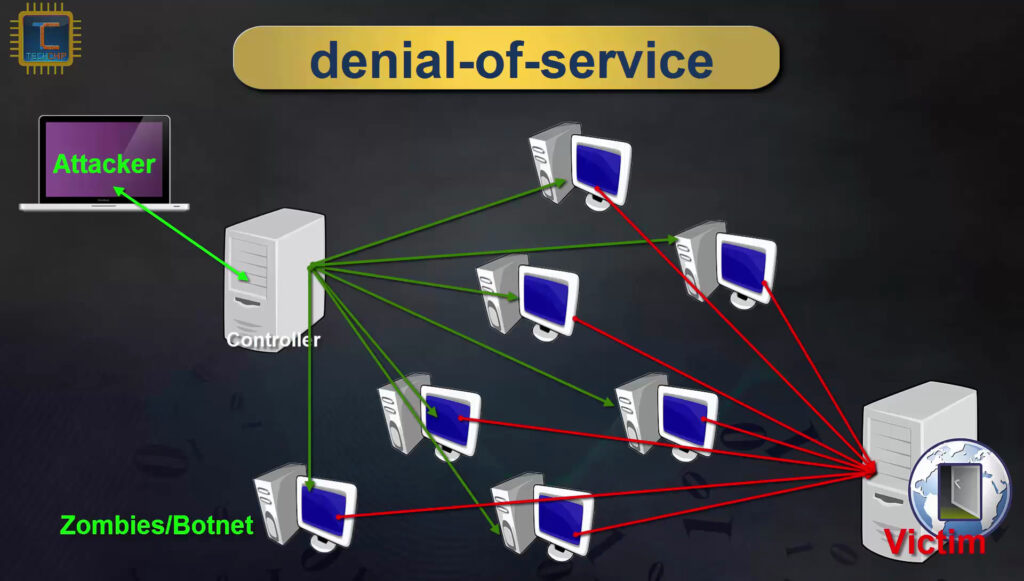
DDoS attacks have always been a problem in the past, and to no one’s surprise, are still a big problem today. Recently, hackers have begun to amplify their DDoS attacks by weaponizing TCP Middlebox Reflections. This made it easier for hackers to do a lot more damage using DDoS attacks, causing lots of problems for tech companies.
What is a DDoS attack?
A distributed denial-of-service (DDoS) attack is a method used by cybercriminals to slow down or stop networks from operating. This is done by flooding a network with malicious traffic to the point that it cannot operate normally. DDoS attacks are usually used to stop people from being able to use a website, causing problems for both the owner and users of the website.
What is a Middlebox and TCP?
Before talking about why weaponizing TCP middle box reflections is such a big deal, lets take a look at what it is exactly. A middlebox is a device that is in between two communicating end hosts. It is used to inspect, filter, and transform packet streams being transported. Middleboxes are widely used all over the world, and often used by countries who wish to censor the internet. Transmission Control Protocol (TCP) is used to organize data such that there is a secure transmission between a server and a client.
How are TCP Middlebox Reflections being used to attack?
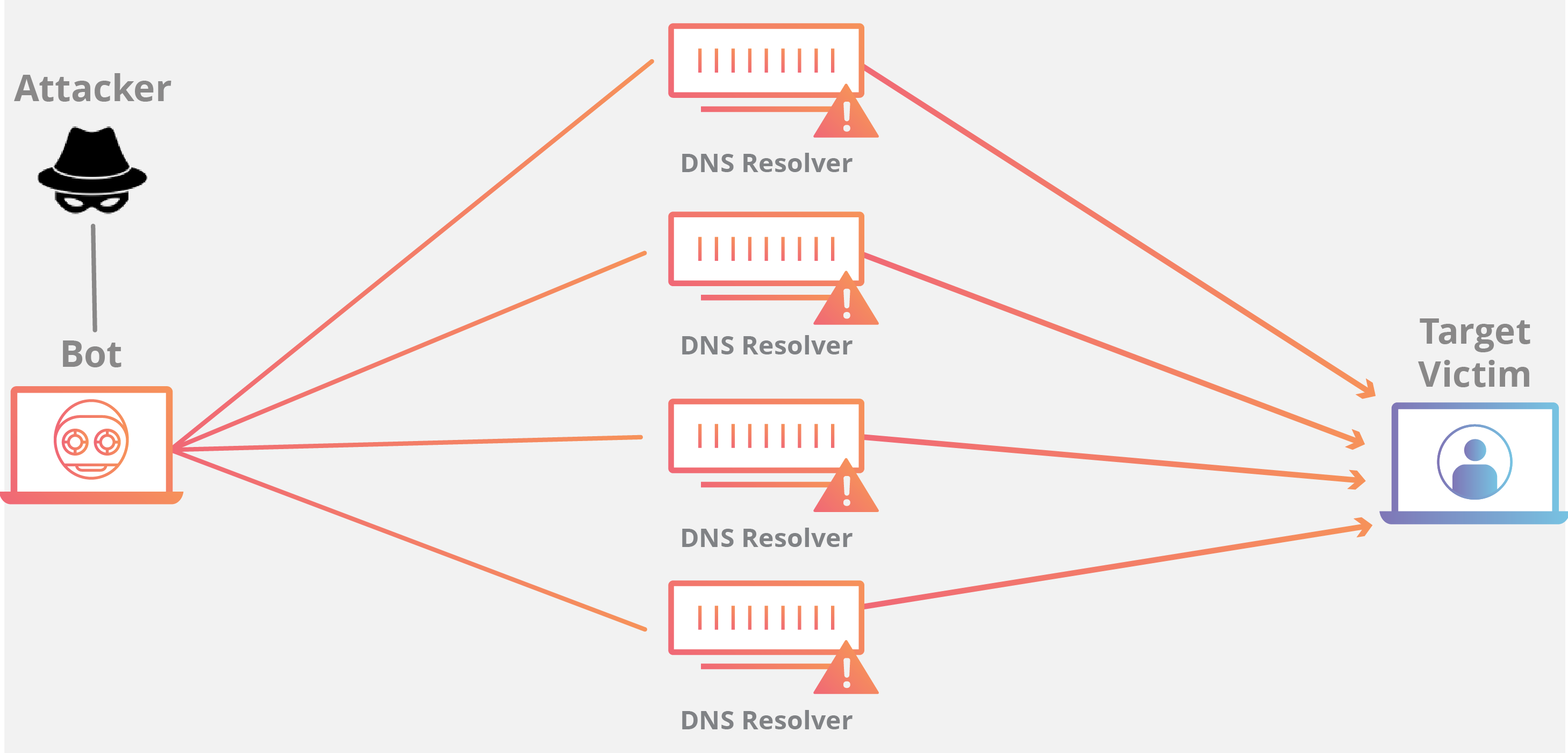
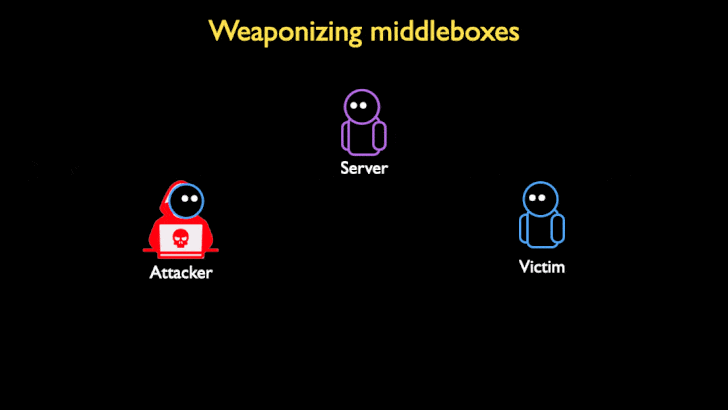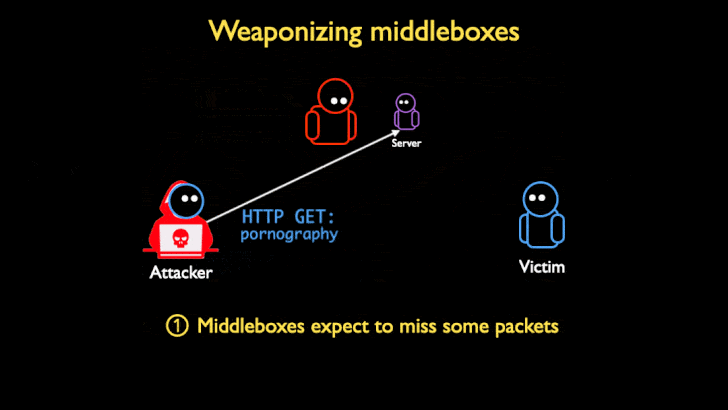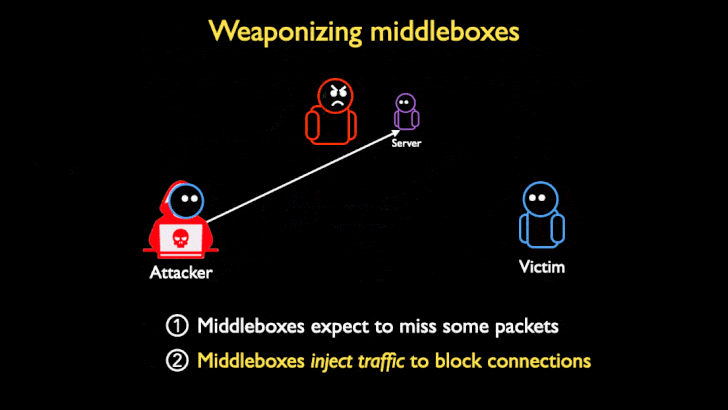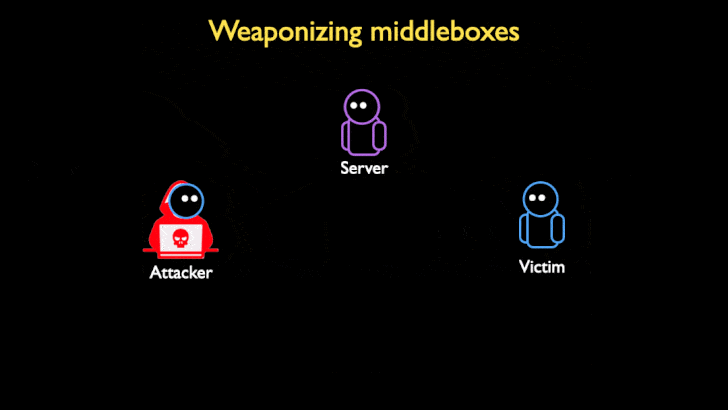
TCP Middlebox Reflections are being used to abuse the Middlebox filtering system, and reflect traffic created by the Middlebox to a victim. The way that these attacks work is that an attacker sends requests containing an IP spoofed as the target victim to a server. The request is usually an HTTP address for blocked content. When the request reaches the middlebox, usually the connection would be blocked, however, many middlebox systems don’t take into account TCP streams when filtering content. Because they don’t take TCP streams into account, when a request is received through a TCP stream that would normally be blocked, the middlebox assumes that some packets got through. In order to prevent the user from accessing the restricted content that was not blocked, the middlebox will flood the client’s browser to prevent the user from getting to the restricted content. Since the attacker spoofed the IP on the request as the IP of a victim, all of the traffic is reflected to the victim’s browser, hence the use of reflection in the name. The middlebox floods the victims address in an amplified way that causes all the bandwidth to be exhausted. This is the reason that the attack can be so detrimental.
Researchers from Akamai claim that “This type of attack dangerously lowers the bar for DDoS attacks, as the attacker needs as little as 1/75th (in some cases) the amount of bandwidth from a volumetric standpoint.” This shows how much easier it is to DDoS using a TCP middlebox reflection than other methods such as a UDP attack.
Who is being targeted, and how can it be stopped?
While there have not been many observed attacks, researchers believe that the number of attacks using a TCP middlebox reflection are going to greatly increase since these attacks are easy and effective. In the past few days, the main targets for this attack so far have been against banks, medias, and web-hosting companies, however, this list is likely to increase in the future.
There are many methods that could be used to stop this type of attack, such as removing all censorship of the internet everywhere. However, that might not be the most practical method (although I’m sure many people would like that). Some more realistic ways to mitigate attacks would be to use methods like anti-spoofing. That way, the middlebox would not flood the browser of the victim associated to the spoofed IP, since the spoof will get removed. Other DDoS mitigation methods can also be used since, although new, this is still a DDoS attack, so using specially designed networks to counteract DDoS attacks can be helpful.
References:
https://thehackernews.com/2022/03/hackers-begin-weaponizing-tcp-middlebox.html
https://www.akamai.com/blog/security/tcp-middlebox-reflection
https://usa.kaspersky.com/resource-center/preemptive-safety/how-does-ddos-attack-work