Group: Mehedi Hasan, Jagadeesh Somepalli, Prajwal Thippeswamy, Moein Ghavi
Introduction
Every day, we need to encounter a lot of sensitive and valuable digital data that needs to be encrypted when it is being transmitted from source to destination so that, eavesdroppers can’t extract the information during the transmission. At the same time, we need to encrypt data saving on the cloud for any organization.
However, we must decrypt those data prior to use for any project. As soon as, we decrypt data it becomes vulnerable to hackers. This is an ongoing issue for data encryption.
Homomorphic encryption is an advancement in the era of cryptography.
What is Homomorphic Encryption?
The main purpose of homomorphic encryption is to allow computation on encrypted data. In that way, data can remain encrypted while it is processed. In any vulnerable environment, homomorphic encryption is a revolutionary algorithm to accomplish the task of processing encrypted sensitive data without decrypting it.
A homomorphic cryptosystem is another form of public encryption in that it uses a public key to encrypt data and allows only the individual with the matching private key to access its encrypted data. However, even though it is another form of public encryption, but it uses a different algebraic system to allow a variety of computations on the encrypted data.
In mathematics, homomorphism explains the transformation of one data set into another while preserving relationships between elements in both sets. This encryption method works well with integer data while using addition and multiplication as the operational functions and during that process, encrypted data can be manipulated and analyzed as though it’s in plaintext format without being decrypted.
Types of Homomorphic Encryption
There are three types of homomorphic encryption. The primary difference between them is related to the types and frequency of mathematical operations that can be performed on the ciphertext. The three types are:
- Partially Homomorphic Encryption
- Somewhat Homomorphic Encryption
- Fully Homomorphic Encryption
We will be talking about fully homomorphic encryption for the topic voting system. This encryption method can use both addition and multiplication any number of times and makes secure multi-party computation more efficient.
Enhancing Election voting system’s privacy
There are multiple types of research are going on to use homomorphic encryption to make the democratic elections voting system more secure and transparent. For example, the Paillier encryption scheme uses addition operations and would be best suited for voting-related applications because it allows users to add up various values in an unbiased way while keeping their values private. It also allows the third party to verify the system.
Normal Encryption vs Homomorphic encryption
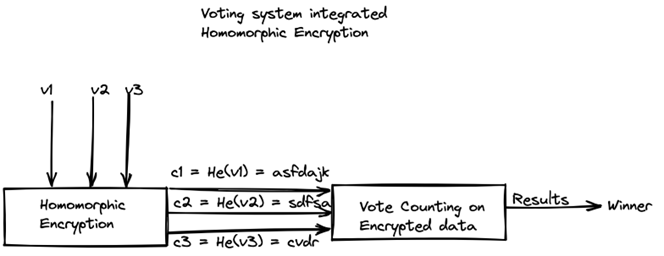
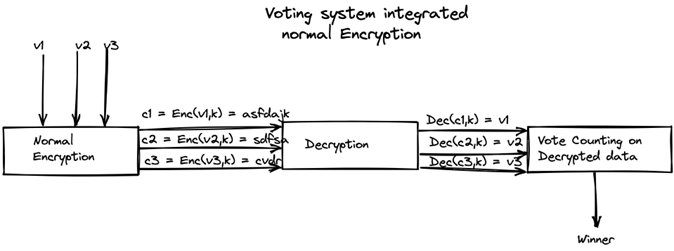
Simple script to simulate voting between Cat Lovers and Dog Lovers with homomorphic encryption.
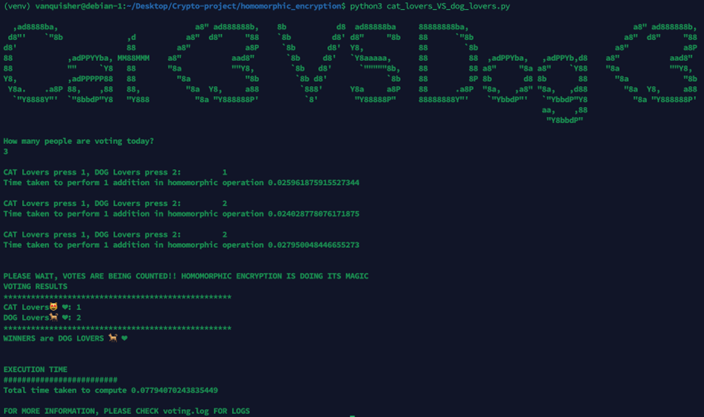
Above is the screenshot of the output that the script produced.
As an input, 1 is required for CAT Lovers and 2 is required for DOG Lovers. In the above example, 3 users provide 3 votes to the program. Once the votes are provided, the votes are being counted. Votes counting is done on the encrypted value of the votes (ie., computation of homomorphic encrypted ciphers). Then the winner is calculated. Execution time is also displayed.
GitHub Repository for the source code: https://github.com/Prajwalmithun/homomorphic_encryption
Conclusion
This blog attempts to give an overview of the homomorphic encryption, different types of homomorphic encryption, and how integrating this with the current voting systems enhances the privacy. Furthermore, a simulation of the voting system with homomorphic encryption is discussed to determine the winners between the Cat Lovers and the Dog Lovers.


This is so interesting. Will your project include how homomorphic encryption takes place on the voting system and what it actually looks like?
Thanks for your comment. Yes, this project will explain HE on the voting system but we will not go too deep into mathematical terms due to time constrain. We will try to provide information as much as possible. In our blog post, we tried to put a simple example about voting with HE.
Fabulous choice of topic and much luck with the program challenges still pending! Looking at the example of voting systems my first thought is to use HE with blockchain so as to achieve the obvious need for privacy but decentralization of the data for multiple users. Here’s a great article if you have time..
https://ieeexplore.ieee.org/abstract/document/9091234
Thank you for the share!
Thank you Angelica for the document. This seems to be interesting to integrate HE and Blockchain.
Thanks for the informative content. The idea of using homomorphic encryption in voting systems is very intriguing and has great potential to enhance the security and privacy of electronic voting systems and other systems in the future. I wonder if there have been any real-world examples of homomorphic encryption in voting systems? If so, what were the results, and what challenges were faced during the implementation process? Thank you.
Thanks for the informative content. The idea of using homomorphic encryption in voting systems is very intriguing and has great potential to enhance the security and privacy of electronic voting systems and other systems in the future. I wonder if there have been any real-world examples of homomorphic encryption in voting systems? If so, what were the results, and what challenges were faced during the implementation process? Thank you.
Thanks for the informative content. The idea of using homomorphic encryption in voting systems is very intriguing and has great potential to enhance the security and privacy of electronic voting systems and other systems in the future. I wonder if there have been any real-world examples of homomorphic encryption in voting systems? If so, what were the results, and what challenges were faced during the implementation process? Thank you.
Thanks for the informative content. The idea of using homomorphic encryption in voting systems is very intriguing and has great potential to enhance the security and privacy of electronic voting systems and other systems in the future. I wonder if there have been any real-world examples of homomorphic encryption in voting systems? If so, what were the results, and what challenges were faced during the implementation process? Thank you.
Thanks for your comment. This kind of encryption currently is close to production and companies like IBM, Google or Microsoft are working on it but there isn’t any implementation available.
https://www.microsoft.com/en-us/research/project/microsoft-seal/
https://www.ibm.com/security/services/homomorphic-encryption
Thanks, Moein for the information you provided. It’s interesting to see how homomorphic encryption can be used in real life, and how some big techs like Microsoft and IBM are developing and integrating this technology into their products and services.
This is really interesting! Did you run into any challenges when building the program? Also, did you find any vulnerabilities in using homomorphic encryption in a voting system?
Thank you for your comment, Jamie!
One of the challenges that was faced while building the program is the lack of libraries and their dependencies with operating systems and other packages. The library that is used in the program is “Pyfhel”. This works perfectly fine on some of the Linux Distros, I have worked on “Debian” and this worked. But the same library had issues with just installing on the MacOS. Even in Microsoft Windows, we had issues.
The other challenge that I faced was during the containerization of the program. Even the base image of “Debian” had issues while building the containers. As of now, I was not able to find out a permanent fix for this issue. Therefore, as a workaround, this program has to be installed using the steps provided in the GitHub README.
Another challenge is the lack of documentation for these libraries. And most of the libraries are not being maintained. It was a kind of a trial and error to see which library works on which operating system.
I am aware that homomorphic encryption is complex and I am also thankful to the researchers and programmers who are working in this domain.
Also, did you find any vulnerabilities in using homomorphic encryption in a voting system?
I am not sure if my answer is 100% to the question, but, there are scalability issues with homomorphic encryption. It means homomorphic encryption uses “noise” to the ciphertext to create randomness. And, a value called noise ceiling defines the threshold for this “noise”, say if the noise is greater than this noise ceiling, the decryption will give errors.
Just a simple example,
Users can vote for the candidates in an election,
1 for candidate1 = vote_1
2 for candidate2 = vote_2
CASE 1:
Say there are 3 users,
user_1 = cast(vote) = 1 ie., vote_1
user_2 = cast(vote) = 1 ie., vote_1
user_3 = cast(vote) = 2 ie., vote_2
After encryption, noise=10, noise_ceiling = 100
For Candidate 1:
Noise(Encrypt(Total_votes_1)) = 0
Step 1 (user_1) noise 11:
Noise(Encrypt(Total_votes_1) = Noise(Encrypt(Total_votes_1)) + Noise(Encrypt(vote_1))
Step 2 (user_2) noise 21:
Noise(Encrypt(Total_votes_1) = Noise(Encrypt(Total_votes_1)) + Noise(Encrypt(vote_1))
Noise(Encrypt(Total_votes_1)) = Noise(11) + Noise(21)
= 32
Now this is fine, as the noise level is 32 and it’s below 100. Now if we perform decryption,
Total_votes_1 = 2
For Candidate 2:
Noise(Encrypt(Total_votes_2)) = Noise(Encrypt(vote_1))
= Noise(12)
= 12
Noise level is below 100. So after decryption, we get the value as,
Total_votes_2 = 1
CASE 2:
Now assume 5 users are voting
user_1 = cast(vote) = 1 ie., vote_1
user_2 = cast(vote) = 1 ie., vote_1
user_3 = cast(vote) = 1 ie., vote_1
user_4 = cast(vote) = 1 ie., vote_1
user_5 = cast(vote) = 2 ie., vote_2
After encryption, noise=10, noise_ceiling = 100
For Candidate 1:
Noise(Encrypt(Total_votes_1)) = 0
Step 1(user_1) noise = 11: Noise(Encrypt(Total_votes_1) = Noise(Encrypt(Total_votes_1)) + Noise(Encrypt(vote_1))
Step 2 (user_2) noise = 21: Noise(Encrypt(Total_votes_1) = Noise(Encrypt(Total_votes_1)) + Noise(Encrypt(vote_1))
Step 3 (user_3) noise = 31: Noise(Encrypt(Total_votes_1) = Noise(Encrypt(Total_votes_1)) + Noise(Encrypt(vote_1))
Step 4 (user_4) noise = 41 : Noise(Encrypt(Total_votes_1) = Noise(Encrypt(Total_votes_1)) + Noise(Encrypt(vote_1))
Noise(Encrypt(Total_votes_1)) = Noise(11) + Noise(21) + Noise(31) + Noise(41)
= 104
This is not good, as the noise is greater than the noise_ceiling value of 100
After decryption: it provides the wrong value.
Total_votes_1 = 1234 (wrong value)
For Candidate 2:
Noise(Encrypt(Total_votes_2)) = 0
Step 1 (user_2):
Noise(Encrypt(Total_votes_2) = Noise(Encrypt(Total_votes_2)) + Noise(Encrypt(vote_2))
Noise(Encrypt(Total_votes_1)) = Noise(12)
= 12
The noise level is below 100. So after decryption, we get the value as,
After decryption:
========================
Total_votes_2 = 1
In looking at CASE 1 and CASE 2, as the number of users started to increase, the number of operations started to increase. With each operation, the noise is expected to increase. If the noise is greater than the threshold, the decryption will be wrong and causes inconsistencies. This scaling issue can be a vulnerability if we are looking it from other angle.
Nice blog. Learnt quiet a lot about Homomorphic encryption and got to visualize one of its applications. Could you point out the major industries Homomorphic Encryption is being used in today other than PCI. I would love to try out the simulation IRL 😉
Homomorphic encryption is not completely mainstream due to some of the challenges in scalability, performance, and resource consumption. But there has been a lot of research and investment from large organizations like IBM, Microsoft, Google, etc.
This website shows the companies that are using/making homomorphic encryption usable.
https://www.ventureradar.com/keyword/Homomorphic%20encryption
IBM has a homomorphic service to try and implement:
https://www.ibm.com/cloud/blog/fully-homomorphic-encryption-on-ibm-cloud-hyper-protect-virtual-servers
Cloud Service providers can make a huge benefit with homomorphic encryption, by performing computation of encrypted data by not risking consumers’ privacy.
Homomorphic encryption is not completely mainstream due to some of the challenges in scalability, performance, and resource consumption. But there has been a lot of research and investment from large organizations like IBM, Microsoft, Google, etc.
IBM has a homomorphic service to try and implement:
IBM Homomorphic service and other companies are making them into homomorphic encryption like Microsoft SEAL, and Google FHE transpiler.
Cloud Service providers can make a huge benefit with homomorphic encryption, by performing computation of encrypted data by not risking consumers’ privacy.
Interesting post! I like the part “vote counting on encrypted data” then the result which makes the voting system secure and transparent. My question: Is there anywhere it has been implemented?
Thank you for your comment!
Homomorphic encryption is close to mainstream. There has been much research going on, and huge investment in this field. Homomorphic encryption struggle with complex data sets and it takes immense computing power for more practical operations. If homomorphic encryption comes to the mainstream this could be a huge positive impact on many Cloud Service Providers and their consumers etc.
But large companies like IBM, Microsoft, and Google are already providing libraries, SDKs, and services to implement homomorphic encryption.
IBM Homomorphic service: https://www.ibm.com/security/services/homomorphic-encryption
Microsoft SEAL: https://github.com/microsoft/SEAL
https://www.microsoft.com/en-us/research/project/microsoft-seal/
Google FHE transpiler: https://github.com/google/fully-homomorphic-encryption
hank you for your comment! Homomorphic encryption is close to mainstream. There has been much research going on, and huge investment in this field. Homomorphic encryption struggle with complex data sets and it takes immense computing power for more practical operations. If homomorphic encryption comes to the mainstream this could be a huge positive impact on many Cloud Service Providers and their consumers etc. But large companies like IBM, Microsoft, and Google are already providing libraries, SDKs, and services to implement homomorphic encryption.
IBM Homomorphic service: http://www.ibm.com/security/services/homomorphic-encryption
Microsoft SEAL: github.com/microsoft/SEAL
http://www.microsoft.com/en-us/research/project/microsoft-seal/
Google FHE transpiler: github.com/google/fully-homomorphic-encryption
Interesting post! I like the part “vote counting on encrypted data” then the result which makes the voting system secure and transparent. My question: Is there anywhere it has been implemented?
Great blog. I learned a lot about homomorphic encryption and how it can be used to protect sensitive data. I would like to learn more about what specific challenges does homomorphic encryption address. Also, are there any limitations of homomorphic encryption?
It was enjoyable to read your blog. H omomorphic encryption has the potential of enhancing the security and privacy of sensitive data. I am wondering, what factors need to be taken into account before homomorphic encryption is put into use?
Thanks for the comment, Ayushi. The fact is that there is a long way to have this encryption works and due to some of the challenges in performance and resource consumption it is hard to implement this algorithm unless the resource problem is resolved.
Thank you for your feedback, Ayushi!
Currently, homomorphic encryption is kind of in the research stage with some great libraries and services from IBM, Microsoft, Google, etc. Some of the challenges that we are facing to bring homomorphic encryption to mainstream is its slowness compared to plain text computation. As Moein mentioned, its very memory intensive.
Oh, Nice to also know this is largely still being researched and developed. I have never heard of this and it really interesting. I had look more into Agelica’s link for more information.
But can some correct me if I am wrong here. Am I correct to say the HE is based on the Time taken to perform the operations on the encrypted message? If that is correct then that would mean that the concept will be limited to only performing operations on known encrypted messages; like the case with the votes counting system where the voting options are known.
Thank you for introducing us to the Homomorphic Encryption and also presenting an intriguing use case. I wonder if we can achieve same results with a hashing algorithm like SHA 256, as for same input, it generates the same ciphertext everytime. Could you please describe what possible challenges made you choose Homomorphic Encryption over hashing algorithms or any other encryption algorithm discussed in class, for voting systems?.
It can be used in an environment where different apps or 3rd parties have to work with the data and we want to protect the privacy of our data. For example, this can be utilized in cloud platforms like aws or gcp that store sensitive information and needed to protect the privacy as well. But the math behind the scene is very heavy and costly and right now I don’t have any idea if they are using it or not.
It can be used in an environment where different apps or 3rd parties have to work with the data and we want to protect the privacy of our data. For example, this can be utilized in cloud platforms like aws or gcp that store sensitive information and needed to protect the privacy as well. But the math behind the scene is very heavy and costly and right now I don’t have any idea if they are using it or not.
Would you have any statistics or quantitative data how much computing power is needed? Is that the only component that makes it not mainstream? I use many uses of the technology, e.g., confirm property ownership. Those cases demonstrate the need for privacy as well as the need for public information or acknowledgement.
Thank you billy. As far as I have researched the math behind the scene is so complex and they made different type of this algorithm such as Partially Homomorphic Encryption(PHE) , Somewhat Homomorphic Encryption(SHE), and Fully Homomorphic Encryption (FHE) to reduce the complexity. However, there are some good libraries like https://github.com/homenc/HElib or https://github.com/Microsoft/SEAL if you want to test it yourself.
Thank you for your comment, hashing is mainly for solving the “Integrity” issue, whereas “Encryption and Decryption” provide “Confidentiality”. Homomorphic encryption is also a type under public-key encryption, so it requires a public key to encrypt the data, and a secret key to decrypt on top of that there are other keys for computation.
To answer this part of the question “I wonder if we can achieve the same results with a hashing algorithm like SHA 256, as for the same input, it generates the same ciphertext every time”.
Answer: With SHA 256 you get the message digests with the same length and for each input, there is a fixed hash. But, we cannot perform mathematical operations like addition or multiplication on these digests. The only way to do this is to perform a dictionary attack on the hash and identify the message, then perform a mathematical operation.
For this part of the question “Could you please describe what possible challenges made you choose Homomorphic Encryption over hashing algorithms or any other encryption algorithm discussed in class, for voting systems?”
Answer: As mentioned in my previous answer, we cannot perform mathematical operations on hashes directly, so hashing algorithm is ruled out.
Now, coming to the other option, traditional encryption algorithms like AES, RSA etc, Even if we use traditional encryption, cipher texts have to be decrypted to perform computation, so this is basically, performing computation on the plain text. Computation on the plain text has problems with privacy. So, what if there is a way we perform mathematical computation on ciphertext directly without decrypting it? Here comes homomorphic encryption, mathematical computation like addition, and multiplication are performed on the ciphertext directly. So, we thought, this is a good way to preserve privacy in voting systems, so we choose homomorphic encryption.
Hope, I was able to answer your question.
Great content guys! This seems like something that would be used for Database Privacy so that not even administrators would be able to see what data is being stored but can perform the required computations on them. Based on your research, what are the pros and cons to using Fully Homomorphic encryption rather than Partially Homomorphic encryption?
This a very interesting topic with great potential such as the Database Privacy case as cited by Teddy.
I would imagine that, for now, its use will be limited to relatively simple datasets and operations due to performance issues.
Did your research reveal any error detection or correction methods for decryption when issues, such as the Noise Threshold being exceeded, are encountered?
The topic is interesting and voting systems are a hot button issues since they have know to be compromised easily. I think the general tone in society right now is that computers cannot be trusted with something as important and possibly easily manipulate like voted. It will be interesting to see if homomorphic encryption can solve that issues or if we are forever going to use paper ballots and long lineups.
I really enjoyed reading this blog entry and look forward to your final project! I also find homomorphic encryption to be an extremely interesting topic – so much so that I wrote my undergrad thesis on the mathematics of homomorphic encryption. It was very interesting to take a step back from the math while reading your blog and learn about a possible application that would have a huge effect on the world! I really appreciated seeing a real implementation of homomorphic encryption with the cat/dog program.
If anyone else is super captivated by this topic, there are some very cool other applications in the works in the medical field. Homomorphic encryption is currently being used to see if it can diagnose skin cancers from encrypted images.
Thanks for the comment, Janelle. I didn’t aware of skin cancer diagnosis and it is amazing that how encryption can help the world.
This was a very interesting read! As you work on showing encryption on voting systems do you focus on a particular country and they voting procedures or how to validate voting in a general view?
Great post Gentlement and fingers crossed the issues work themselves out. First thing that came to mind was blockchain and HE…
https://ieeexplore.ieee.org/abstract/document/9091234
What an interesting topic. I wonder if it could ever apply to US elections…. ? I look forward to seeing more in your final project. 🙂
Would you think smart contracts or Blockchain can help solve voting problems in terms of non-repudiation and privacy? How to ensure only valid voters cast their votes and also ensure anonymity? Or can the technology lead to traceable votes?
One more comment. Do votes need digital signatures in traceable votes or in the validation of voters ( in non-traceable voting)?