by Stephen Penner, Ben Etukudoh, Oluchi Henry-Ucheonwu, Julie Stiehl (edited)
Introduction
This is our first attempt to explore the world of WirelessHART, to have a clearer perspective of what it is and how it works with a focus on data integrity and security. We also examine this protocol with reference to Wi-Fi alliances latest standards for security; WPA3 even with Emerson’s bold statement that WirelessHART is not Wi-Fi. We take a dive into some of the concerns stakeholders have and how the HART foundation has addressed them.

Highway Addressable Remote Transducer – Wirelessly
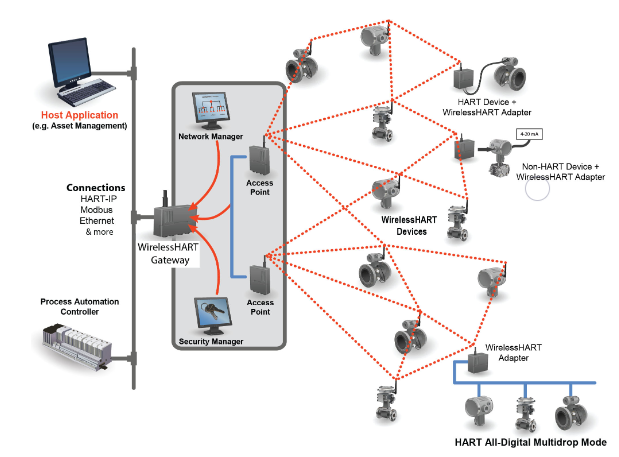
WirelessHART is a wireless field device communication protocol that is part of the Highway Addressable Remote Transducer. It is a wireless mesh network communications protocol for process automation applications. WirelessHART was released in September 2007 as part of the HART 7 Specification. WirelessHART technology was designed to enable secure industrial wireless sensor network communications while ensuring ease-of-use was not compromised. The built-in security cannot be disabled. It uses Advanced Encryption Standard (AES) 128-bit encryption, which is implemented end-to-end. These sessions ensured that messages were enciphered in a way that only the destination could decipher and utilize the payload created by the source device. It adds wireless capabilities to the HART protocol while maintaining compatibility with existing HART devices, commands, and tools.
WirelessHART’s security architecture helps owners and operators address all three of these areas: [3]
- It minimizes, controls, and audits user’s access.
- Requires high levels of technical expertise to sabotage, which removes complexities.
- Reduces infiltration span and duration of any individual breach because it uses a mesh network.
Each WirelessHART network includes three main elements:
- Wireless field devices connected to process or plant equipment.
- Gateways that enable communication between these devices and host applications connected to a high-speed backbone or other existing plant communications network.
- A network manager responsible for:
- Configuring the network.
- Managing message routes.
- Monitoring network health.
- Scheduling communications between devices.
The network uses the IEEE 802.15.4 radio operating at 2.4 GHz. The radios employ direct-sequence spread spectrum (DSSS) technology and channel hoping for communication security and reliability, and time division multiple access (TDMA) to ensure latency-controlled communications between devices on the network.
Major security features of the WirelessHART protocol are: [4]
- Radio security features.
- Multiple encryption keys.
- Multi-path mesh networking.
- Protection against non-repudiation.
- Protection against denial of service.
- Secure join process with all devices authenticated.
- 128-bit message encryption to protect against eavesdropping.
- Data confidentiality is maintained as it is routed around the network using keys.
- Protections against replaying man-in-the-middle, sink hole, and other attacks.
- Verifications that messages have not been tampered with by using integrity codes.
The WirelessHART protocol has been specifically designed to provide the highest level of data security to industrial process automation applications. Combining the designed-in security features of WirelessHART with both operational technology (OT) and information technology (IT), network best practices will produce a high-performance wireless field device network that maximizes data availability, confidentiality, and integrity while dependably delivering industrial process data.
WPA3 – an Alternative to WirelessHART
WPA, or Wi-Fi Protected Access, was a work in progress over many years and is now on its 3rd iteration. Since the dawn of commercial Wi-Fi, the Wi-Fi Alliance has struggled to keep up with the evolving attacks on WEP and WPA. When the first Wired Equivalent Privacy (WEP) standard was released in 1997, with only a 64-bit key, its longevity as a secure protocol was already off to a rocky start and its encryption was quickly broken.[1] The stop gap measure of WPA helped to solve the issue but was replaced with the now dominate standard of WPA2 and was secure until 2018 when the new standard WPA3 was made mandatory for all new Wi-Fi devices. [1]
WPA3: The following is a brief list of improvements on WPA2. [2]
- Increased key size to 192-bits.
- Stronger encryption standards.
- Secure easy onboarding of IOT or screenless devices.
- Bug fix for offline password attacks that broke WPA2.
- Support for encrypted open networks with Opportunistic Wireless Encryption (OWE).
Major security features of the wireless WPA3 protocol. [2]
- 256-bit to 384-bit message encryption using AES.
- 128-bit to 265-bit frame protection for broadcast/multicast traffic.
- Uses Simultaneous Authentication of Equals (SAE) to store password hash.
- Forward Security allows the protection of data even if the password is compromised.
- Using unique encryption keys for each device.
WPA3 specifications may seem like it is stepping in the right direction to get ahead of the curve for data security. However, they have already suffered setbacks due to side-channel attacks, downgrade attacks, denial of service attacks, and the aptly named Dragon’s Blood Attacks that include a suite of all the previously mentioned attacks. While some devices were fixed with vendor patches, the biggest flaw with WPA3 is the mass of non-upgradable WPA2 devices in the wild. [1] Since WPA2 had a 14-year reign as the leading protocol, billions of devices lack support for the WPA3 standard and are now left vulnerable.
Comparing WPA3 vs WirelessHART
Since early 2015 the FieldComm Group has been working with leading process end users, manufacturers, universities and research organizations to direct the development, incorporation, implementation and set the standard for communication technologies such as HART and Foundation Fieldbus for the process industries.
The security standard for Wi-Fi products and implementation building on the IEEE 802.11 architecture is set by Wi-Fi Alliance®, a worldwide network of companies that lead and develop industry-agreed standards for Wi-Fi®.
For starters, WirelessHART operates with an 802.15.4 radio while Wi-Fi uses an 802.11 radio. The 802.15.4 architecture supports low power short range wireless implementation, while the 802.11 supports wider range wireless solutions.
The WirelessHART uses enterprise WPA2 with Extensible Authentication Protocols to authenticate users. Whereas WPA3 uses Simultaneous Authentication of Equals (SAE) to provide stronger defenses against password guessing. SAE is a well-known secure key establishment protocol.
The encryption algorithm used in WirelssHART is AES with a 128-bit key length (16-bytes). The AES algorithm encrypts information and validates the data sent. This concept is called Data Integrity and is achieved using a Message Integrity Code (MIC), also named Message Authentication Code (MAC), that is appended to the message. This code ensures integrity of the MAC header and payload data attached. It is created encrypting parts of the IEEE MAC frame using the key to the network, so if we receive a message from a non-trusted node, we will see that the MAC generated for the sent message does not correspond to the one that would be generated using the message with the current secret key, so we can discard this message. The MAC has a length of 128-bits; however, it is always created using the 128-bit AES algorithm. Its size is just the bits length which is attached to each frame. The larger the more secure it is, although the message can take less payload. Data Security is performed encrypting the data payload field with the 128-bit key. Whereas the WPA3 Standard allows for up to 192-bit cryptographic strength (AES-256 in GCM mode with SHA-384 as HMAC) preventing unauthorized eavesdropping or data manipulation of any of the communications.
WirelessHART is a low-power wireless protocol used to transmit relatively small amounts of data while Wi-Fi can be used to transfer large amounts of data, including video streams and large file transfers. Another major area where WirelessHART differs from Wi-Fi is the fact that the security mechanisms cannot be disabled in WirelessHART. In Wi-Fi, although not advised, a user could disable security features and operate without any encryption or authentication whatsoever.
Concerns
According to the technical note 00840-0300-6129, Rev AA published by Emerson in October 2017, to clear the air on the WPA2 vulnerability. Emerson tried to differentiate the WirelessHART from the Wi-Fi in its defense mechanism for WPA2 vulnerability to Key Reinstallation Attack (KRAK) which are Wi-Fi vulnerabilities discovered by two Belgian researchers. This vulnerability abuses design or implementation flaws in WPA2 cryptographic scheme which is also used by HART to reinstall an already-in-use or predictable key. Depending on the specific vulnerabilities that are exploited, an attacker can decrypt network information allowing the attacker to read contents of messages, inject malicious content, pose as a legitimate access point, or perform other nefarious activities. [5].
In defense, Emerson also encourages a good patch and update management program for end-users. The provided patches prevent key reuse and will be backwards-compatible. This means patched clients can communicate with unpatched access points and vice-versa, however both the client and access points have to be patched to prevent against the attacks.
Emerson has also advised the use of other encrypted protocols, such as Hyper Text Transfer Protocol Secure (HTTPS), as an added layer of protection. HTTPS was designed to work over an untrusted channel with no encryption and should be used when possible. Also, using a Virtual Private Network (VPN) can offer additional protection against these attacks. Finally, using a wired connection for sensitive traffic eliminates these concerns.
Conclusion and Recommendation
Our research is currently ongoing. We will present our conclusion and recommendations in a final presentation.
References
1. Sagers, G. (2021). Wpa3: The greatest security protocol that may never be. 2021 International Conference on Computational Science and Computational Intelligence (CSCI), 1360–1364. https://doi.org/10.1109/CSCI54926.2021.00273
2. Fi Alliance File Download. Wi. (n.d.). Retrieved January 25, 2023, from https://www.wi-fi.org/downloads-public/WPA3%2BSpecification%2Bv3.1.pdf/35332
3. Wirelesshart Security Overview – Emerson Electric. (n.d.). Retrieved January 26, 2023, from https://www.emerson.com/documents/automation/white-paper-wirelesshart-security-overview-by-hcf-en-42578.pdf
4. Wirelesshart unaffected by recent WPA2 vulnerabilities – emerson. (n.d.). Retrieved January 27, 2023, from https://www.emerson.com/documents/automation/security-notification-wirelesshart-unaffected-by-recent-wpa2-vulnerabilities-techical-note-en-1730306.pdf
5. Wirelesshart unaffected by recent WPA2 vulnerabilities – emerson. (n.d.). Retrieved January 28, 2023, from https://www.emerson.com/documents/automation/security-notification-wirelesshart-unaffected-by-recent-wpa2-vulnerabilities-techical-note-en-1730306.pdf


I didn’t know WirelessHART existed, but it seems to me that this is a better option than WPA3. I wonder why techs are not starting to migrate to WirelessHART. Would you know if this is backward compatible?
Also, according to a study conducted by Cheng, X. et al., an attacker can crack a network’s parameter configurations with exploratory jamming attacks and then perform selective jamming attacks to degrade network performance without being detected. This is quite alarming since this protocol is implemented in industrial facilities.
Reference:
Cheng, X., Shi, J., Sha, M., & Guo, L. (2021). Launching smart selective jamming attacks in wirelesshart networks. IEEE INFOCOM 2021 – IEEE Conference on Computer Communications, 1–10. https://doi.org/10.1109/INFOCOM42981.2021.9488805
The main reason is HART runs at low power 2.4ghz and is good for sensor data but not high demand applications as its similar to bluetooth.
Also, to add to Stephen’s response, the HART protocol is also not suitable for big data transfers or streaming. As far as popularity, this protocol is the most popular in industrial fieldbus communication, most especially in the process and petrochemical.
Talking about the Selective Jamming attack. from the work of Cheng,X et al, the attacker also needs to overcome some difficulties, such as
Deployment-specific parameters: Moreover, a vendor use different values for the same parameter in different deployments. The attacker must derive those values by observing the network behavior at runtime. This can take quite some time and increases the chances of being detected.
Fluctuation of low-power wireless links: Like I said, this protocol is most popular in industrial setting. So the Attacker needs to be relatively physically close to the network infrastructure which may be had due to physical access control policies in place in most industrial setting.
Attacker also need to mitigate other challenges: Uncertainty of jamming effectiveness, Limited power supply: The malicious device has limited power supply and cannot perform computation-intensive tasks, such as cracking information from data protected by the Advanced Encryption Standard (AES) 128-bit encryption.
In conclusion, this protocol is breakable, but is it still considered relatively secure for its intended purpose.
Thank you for the informative explanations and comparisons of WirelessHART and WPA3 on the blog. I am aware that there are several other industrial wireless communication protocols besides WirelessHART, such as ISA100.11a, Zigbee, and LoRaWAN. I am curious to know what the biggest advantage of WirelessHART is, and in which industries and commercial applications it would be most suitable.
Hello Choi,
The WirelessHART standard is only an extension of the Capabilities of the Native HART Protocol that gas been the defacto fieldbus standard for decades. As can be seen from the OSI stack of the Protocol, Application Layer still implements the Original HART commands.
The WirelessHART devices are widely used in the process and petrochemical industries.
Thanks Ben for your explanation of their relationship. It’s good to know that WirelessHART extends the capabilities of Native HART while still keeping the original commands at the application layer.
Thank you for the informative explanations and comparisons of WirelessHART and WPA3 on the blog. I am aware that there are several other industrial wireless communication protocols besides WirelessHART, such as ISA100.11a, Zigbee, and LoRaWAN. I am curious to know what the biggest advantage of WirelessHART is, and in which industries and commercial applications it would be most suitable.
Thanks for the comments Leo,
The best application for HART is industry like power plants, oil fields, anything where you need to monitor a lot of sensors in Realtime with uncorrupted data in variable weather and RF environments. It could be useful in residential markets for IOT as more home have sensors for water and power usage, presence detection…etc. However Emmerson the main promoter of HART is mainly focused on Industrial application
Thank you, Stephen, for the information. It’s good to know that HART is better suited for industrial and residential markets due to its focus on real-time monitoring and its ability to handle challenging environments.
Thank you, Stephen! In your research did you find any industrial supporters/Clients of the WPA3 system, specifically energy facilities & pipelines? Emerson has been trying to convert many end users for years from HART due to its limitation on data and other but in my experience I have not seen any customers change.
Additionally, downtime is a huge concern as costs can be millions per day is there a clear comparison of the downtimes for each based on attacks?
Can’t wait to see the article please share it on teams!
Interesting topic. Never really heard about WirelessHART before only Zigbee, WPAs, WEP and Z-Wave. In our opinion what do you think are the biggest drawbacks of WirelessHART ? Do you think this technology will become obsolete in the very near future with alternatives taking over or do you reckon it stays around ( just like how IPv4 is gonna stick around) for some time still ?
I found it interesting, also I was not familiar with any such concept. I appreciate the explanations on WirelessHART and comparison with WPA3. I was wondering that is it suitable for all applications, would it be efficient to use WirelessHART for longer-range communication?
Yes, it can be used for long range application by simply expanding the Mesh network. The WirelessHART standard specifies that every device must have a minimum of three routs to the network. This actually means that every device is a router and a network extender. Yes the network can be extended as far as required by just adding more and more devices.
Thank you for introducing us to WirelessHART. As you rightly pointed out that the biggest flaw with WPA3 is the mass of non-upgradable WPA2 devices in the wild, I would like to know to upgrade to which of the two WirelessHART or WPA3 devices provides a better financial proposition in terms of security-to-cost ratios, especially considering that WirelessHART is appropriate for short-range wireless communication only.
security-to-cost would be WPA3 as its geared toward a larger audience and they are moving just as fast as LTE for next gen. They are already working on Wi-Fi 7 and I suspect WPA4 will hit the road map soon with all the debacles WPA3 has had.
It is a very interesting topic. I like how this blog provides a clear understanding of how these technologies are used and the measures they take to ensure data security.
Do you think future advancements in technology would have an impact on the effectiveness of WirelessHART and WPA3?
Interesting topic! I have never heard of WirelessHART until today so it was intriguing to read about another secure way of device communication especially with IoT devices. After reading up on new features of WPA3 it seems like WirelessHART may be the more secure way to go, but is not quite main stream yet, is that a correct statement?
Also, based on your research, what advantages does WirelessHART’s mesh network topology provide over device-to-device communication?
Centralized control would be the big one. Based on the research it seems more like wireless spanning tree to me if one node goes down the rest auto negotiated a new path to keep the Realtime data and commands streaming. Uptime is a big factor in HART architecture as it could mean the difference between a site running properly or exploding.
There are benefits to node redundancy. Is fail-over between nodes built in the technology specifications? Or is it up to individual implementation? Or does it detect nodes are down? By regular signals from individual nodes to show that they are alive or by centralised poling by the central node?
This is a very interesting topic! I am not very familiar with these types of topics, and have only really learned about WPA2 and WPA3 briefly through previous networking classes. I have never heard of WirelessHART before today and find it quite intriguing. From what I was able to understand from reading up on it a bit more, it seems that it is not very mainstream currently. Although WirelessHART seems to be much more secure, from your research were you able to find instances where WPA3 may be overall better to use vs WirelessHART?
Wow, this is such a well-written blog post! This was all completely new to me with my very limited networking background. I did not know that WirelessHART existed before reading your post so I appreciate the education! I look forward to seeing your recommendations for its use in your final project. You mention that WirelessHART is currently only practical for relatively small amounts of data at this time. Does it have the potential to scale up to allowing transfers of larger amounts of data in the near future?
Janelle, I am not sure if there is plans to scale up data handling capacity. The WirelessHART is actually based on the IEEE802.15. standard which is designed for Low power, low range and small bandwidth applications, specifically for IoT.
I was always interested in knowing about the technologies that drive industrial systems. Like the others, I had never heard about WirelessHART before today. I definitely can see why it must be implemented securely, especially in high-risk and critical environments. Thank you for this enlightening post!
WirelessHart uses multiple encryption keys to ensure security, confidentiality, data integrity and authentication. So you can see how
secured it is!
1. Do u agree or believe that enterprise WPA2 is as secure as WPA3 in certain situations?
2. What do u think are the reasons for low adoption rate of wirelessHART? Are there other (emerging) technologies that can serve the same purposes of wirelessHART? While having the low power consumption benefits? I suppose it is not for the reason that it is a patented technology and therefore needs licensing fees?
Talking about wireless communication, did u know that Hedy Lamarr ( in Jeff Beck (r.i.p.) and Johnny Depp ‘s song “This is a Song for Miss Hedy Lamarr”) invented frequency hopping that played a significant role in WWII and was eventually used to develop Wi-Fi, Bluetooth, and GPS? It prevented enemy forces from “jamming” or blocking the signal that guided the Allies’ torpedoes.
Not just a Hollywood star, she has tremendous but little known scientific talent also.
Source: Miller, H. L. (2022) How Hedy Lamarr and Her Inventions Changed the World. In Leaders. https://leaders.com/articles/leaders-stories/hedy-lamarr-inventions/