Passwords have become ubiquitous in our lives as the main tool of account authentication, but relying solely on passwords is not very secure. With so many websites we use daily requiring accounts and passwords, many individuals reuse passwords or use very weak ones, like password123 [1].
If a password is reused on multiple sites, and one of those sites has a data breach, then those leaked credentials may be used on other sites, allowing the attacker to gain access easily [2]. Weak passwords, however, are highly susceptible to brute force attacks [3].
One way to improve the security of your accounts is through two-factor authentication (2FA). As the name suggests, two different factors will be required to prove that you are the owner of that account. The factors used will be two of the following: something you know, something you have, and/or something you are [4]. Most commonly, for login purposes, a password is used as one of the factors (something you know), and a one-time password sent to the user’s phone by SMS is used as the second factor (something you have) [4].
However, though this is more secure, having an OTP sent by SMS to your phone is vulnerable to the SIM swap attack.
But First, What is a SIM Card?
A SIM card, which stands for Subscriber Identity Module, allows your phone to connect to the cellular network offered by your provider. It’s a tiny chip which contains two key pieces of information. The first is the Integrated Circuit Card Identifier (ICCID) which uniquely identifies you in the network. The second is the International Mobile Subscriber Identity (IMSI) which holds information such as what country and mobile provider you use. This sensitive data is encrypted, allowing you to prove your identity in the mobile network [8].
What is SIM Swapping?
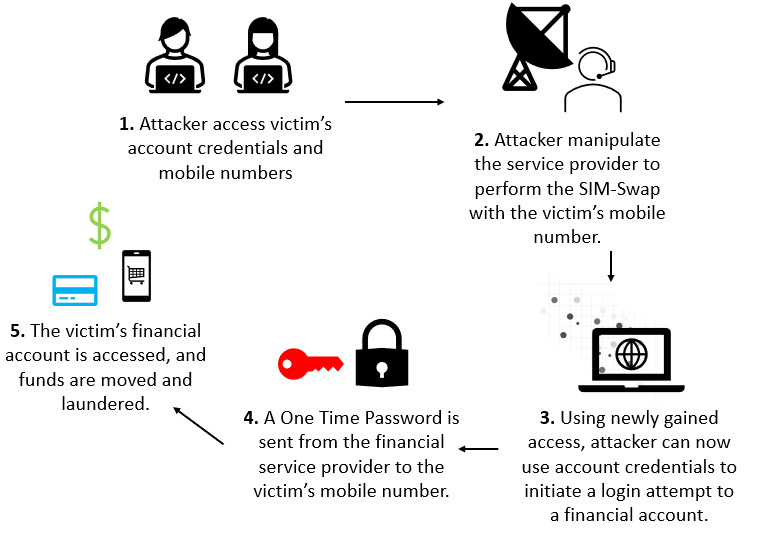
Source: Financial Cybercrime: A Comprehensive Survey of Deep Learning Approaches to Tackle the Evolving Financial Crime Landscape (Nicholls, Kuppa and Le-Khac, 2021) https://www.researchgate.net/figure/Diagram-of-the-SIM-Swap-process-Phase-1-attacker-accesses-victims-account-credentials_fig5_356887995
SIM swapping is a targeted attack where the scammer is able to convince the victim’s cell provider to send them a new SIM card for the victim’s account [5]. The attacker is able to convince the cellphone provider that they are the victim through social engineering or other means, such as knowing the answers to your password recovery questions. Then, the attacker is able to receive an OTP for any accounts linked to that phone. This is especially an issue for bank and cryptocurrency accounts, where attackers are able to authenticate fraudulent withdrawals [5].
SIM swapping is lucrative enough that SIM-swap-as-a-service is being offered by some hacker groups [5]. Many of these groups have gone after celebrities and other high profile individuals, amassing $1.8 million and $5 million in cryptocurrency in some recent individual attacks [6]. Even actress Sydney Sweeney has fell victim to this scam. Her X account was taken over and used to advertise a fraudulent cryptocurrency service [7].
However, regular people have been targeted as well. In August of this year, 10 people in Toronto were arrested for using SIM swapping to defraud multiple individuals of over $1 million [9]. Over 1500 accounts were compromised by this group of attackers [9].
How can you prevent a SIM Swap Attack?
There a few strategies you can use to reduce your risk of being a victim of a SIM swap. As recommended by Europol, if possible, use an authenticator app for 2FA, such as those offered by Google or Microsoft, rather than having codes sent by SMS [6]. As well, to avoid being a victim of social engineering attacks, limit the personal information you share online and avoid giving any such information to unknown callers [6]. Additionally, you can contact your mobile carrier and ensure your account is configured using the highest security settings. If possible, try to get your account configured so that acquiring new SIM cards can only be done in person [6].
Another way to safeguard yourself is to be aware if you are currently experiencing a SIM swap attack. During an attack, your phone will lose service. You may see “SOS” in the top right of your phone where your cellular signal information typically is [9]. This disruption may only be temporary as the attacker will often switch back to the original SIM card after gaining access to your accounts [9]. If you experience an unexpected service disruption, contact your cellphone carrier to determine if any new SIM card requests were made recently. Also, notify your bank if you see any fraudulent activity taking place around that time.
Conclusion
Though 2FA by SMS message is by no means perfectly secure, is still preferable to just using one factor of authentication, like a password. However, if an authenticator app is available for 2FA, that can provide an extra layer of protection against attacks such as SIM swap attacks. As always, staying on top of current advancements in security and authentication will allow you to keep your accounts secure, even as new attacks are identified.
References
[1] https://www.nomios.com/news-blog/password-problem/
[2] https://www.cloudflare.com/learning/bots/what-is-credential-stuffing/
[4] https://www.pearsonitcertification.com/articles/article.aspx?p=1718488
[7] https://www.pcmag.com/news/sydney-sweeneys-x-account-reportedly-hijacked-via-yet-another-sim-swap
[8] https://mobileklinik.ca/blog/how-do-sim-cards-work-and-where-can-you-buy-them/
[9] https://toronto.ctvnews.ca/10-suspects-arrested-in-sim-swap-scam-toronto-police-say-1.6985584


Fantastic Blog, Nicole. That was insightful. I think I was naive all along since, after reading this blog, I realized that depending on network service providers for 2FA is not as dependable as I had previously believed. Hackers continue to succeed in their attacks despite the increasing sophistication of our security measures. Because of this, you must keep up with any relevant security updates so that you don’t become a victim like Sydney Sweeney and others. An article from the Canadian government site Get Cyber Safe, which is linked below, also emphasizes the usage of smart key cards, pins, and biometric signatures as additional security measures. Right after this post, I am going to hook all my accounts to my Microsoft Authenticator Application, ” it is better late than sorry”..
https://www.getcybersafe.gc.ca/en/blogs/examples-multi-factor-authentication-action
Great article Nicole! Thanks for sharing this possible thread. One thing that came to my attention is the fact that phone service providers are still offering the option to change a SIM using security questions. The NIST password best practices mentions that the secret questions or hints should be avoided in the authentication process. With such advanced social engineering available for hackers to find a personal profile, the security questions method is not a secure option. The client should go to a service branch and make the necessary identification process there.
But it is important to be aware if this option is available with our service provider and set the best security options as you mentioned. Thanks for the heads up!
– https://pages.nist.gov/800-63-3/sp800-63b.html#singlefactorOTP
Great informative post, Nicole. The challenge with phone calls and SMS as second-factor authentication both rely on trusting the number (SIM) which is a kind of blanket to whoever gets the SMS or the call, either by the owner of that SIM or a malicious attacker. This topic drove many security and identity experts to look into other methods to perform “just-in-time” identity proofing such as FIDO2 or First Identity Online [2]. The concept is using Public Key and Private to a encrypt challenge word proving the identity of a user when an authentication is desired. The key point in this method is that the private key is kept on a device to which only one identity user has access. This private key is also protected in some cases with biometric validation for more security (e.g., face, iris, thumbprint recognition).
[1] Karim, N., et al., (2024). Choosing the right MFA method for online systems: A comparative analysis. International Journal of Data and Network Science, 8(1), 201-212.
This is an insightful post, Nicole! I had not heard of the term SIM Swap attack until today. While 2FA can get annoying sometimes, it seems to be the most secure way to access accounts.
The strategies you provide are also important to take note of. Towards the end of paragraph 1, you advise that we get our accounts configured so new SIM cards can only be acquired in person. However, I recently just got a new iPhone and was only provided with an eSIM. Apple products now are switching to an eSIM as they suggest it makes transferring and handling multiple eSIMs efficient and easy for users. How would an eSIM change the SIM Swap attack? Wouldn’t this create more security issues given its digital format as opposed to the previous physical form? I would love to hear your thoughts on this!
Great post Nicole! Passwords alone are definitely not enough in today’s world, and the rise of SIM swap attacks is truly alarming, especially since many websites still rely on SMS for two-factor authentication without fully considering the risks. Some carriers have taken steps to mitigate this by encouraging or requiring customers to set up a PIN for their account [1]. If an attacker doesn’t know the PIN, they can’t transfer the phone number. However, PIN numbers are not a foolproof way to prevent an account from being SIM swapped, especially if users select easy-to-guess codes. [1].
Your suggestion to use authenticator apps instead of SMS is spot on. It is such a simple yet effective way to add another layer of security, and more people need to realize how easy it is to make the switch. With cyber threats constantly evolving, staying informed and taking proactive measures, whether by using authenticator apps or being cautious about what personal information we share online, can make a big difference in protecting our accounts.
Reference
1. https://www.cnbc.com/2019/09/06/hack-of-jack-dorseys-twitter-account-highlights-sim-swapping-threat.html
Nicole, great post! This reminds me of my telecoms classes from a few years back. OTP and 2FA via SMS are ineffective against advanced security threats like SIM swapping. One thing to keep in mind is that vulnerabilities will continue to exist, and human error is possible as long as your 2FA relies on your carrier to recognize whether a hacker is targeting you. Another layer of defense is to use eSIM technology, which can be an effective technique for enhancing defenses against SIM swapping attacks while also giving certain security advantages over physical SIM cards. We must also avoid tying accounts to phone numbers and utilize multiple techniques to sign up and authenticate accounts in order to limit hackers to fewer accounts
Great post Nicole! I experienced a similar attack when my phone was stolen. The difference was that the attacker had direct access to my phone number and the MFA codes as well. Fortunately, I was able to get the number blocked in time. The risks of relying solely on SMS and passwords for two-factor authentication (2FA) are effectively highlighted in your post. It’s a bit shocking how sophisticated hacks like SIM swapping have become, impacting not just wealthy people but even common consumers. Because authenticator apps offer a higher level of security than SMS for multi-factor authentication, you are correct to recommend using them instead of SMS. Additionally, as you mentioned, it is critical to understand the signs of sim swapping attacks, which include a sudden interruption of network service. Being aware of this may come in handy in preventing such attacks by allowing swift action.
Awesome post. It’s interesting learning how SIM swap attacks work. It’s nice to learn how 2FA can be attacked a circumvented. Though it does seem most of the attack relies on users also using bad practices with their password or password recovery answer which would allow the hackers to get the SIM swap to happen. I love that you explain the best ways to stop the attack and what to watch out for to see if an attack is happening to you.
Great Post, reading this made me want to look more into the prevalence of authentication apps, and how social engineering plays a role. As you mentioned in you post using 2FA with SMS can be susceptible to a myriad of attacks but using and Authenticator app doesn’t come with such issues. “Authenticator apps are secure because they keep the code local to your device and the codes are not sent unencrypted over the internet. This means they can’t be intercepted through common cyber attack methods. Since the codes reset every thirty to sixty seconds, it’s difficult for cybercriminals to steal them. Because using an authenticator app is simple, free and secure, it’s now the most recommended type of MFA”[1]. I think the biggest threat to all of this is the social aspect. Duo Labs reports that the Banking and Investing industry is the most protected by 2FA with 93%, email and social media with 58% and 40%, respectively[2]. While things like retail and entertainment sit at 27% and 10%. The biggest issue is the disparity, with social engineering, hackers can get into your social apps and once they know the most likely answers to your security questions they can target the more secure industries. As long as we treat out banking app as more important and therefore it needs 2FA as opposed to out Netflix account, social engineering will always allow hackers to have a leg up.
1. https://www.keepersecurity.com/blog/2023/07/20/what-are-authenticator-apps-and-how-do-they-work/#:~:text=Are%20Authenticator%20Apps%20Secure%3F,through%20common%20cyber%20attack%20methods.
2. https://www.comparitech.com/studies/data-breaches-studies/two-factor-authentication-statistics/#7_Two-factor_authentication_uptake_on_Twitter_is_shocking
Awesome post! It is great that the concern for protecting weak passwords is addressed with mitigating measures. There are various ways to mitigate the concerns associated with reliance on passwords, with this shedding more light on another way it can be achieved. Most times, users opt for the easier method which is 2FA via SMS as this is easier and more straightforward rather than having to download an authenticator app. However, this post is important because it highlights the potential dangers that come with choosing the SMS route and why the app is better. This is a great knowledge add! Personally, I know it can be difficult to manage the bad password practices of users, so this is a great way to include an additional layer of protection, should the passwords be compromised.
Good article! Awareness and knowing all about the best security control and security measures is a should nowadays. As passwords themselves are vulnerable. Just be aggressive; hackers will never stop innovating, and there will always be a contest. Always, multi-security layers should win. The need to implement different approaches became more in demand as fast as technology was developing. One of the best models for the implementation of multi-security layer authentication is the Bank app. A better response to threats would be to use MFA for user authentication rather than sending an authorization code to mobile numbers, as most banks today provide.
In India, SIM swapping attacks became so common that service providers implemented a 24- to 48-hour cooldown period. During this time, the new SIM can only receive SMS from the service provider. I think this was a smart move! What are your thoughts on this approach?
Great job Nicole, this is really insightful before now i was thinking two factor authentication is extremely important and safe but now with this article I have now come to realise that hackers can still penetrate through it so I think using a MFA will go a long way instead of using just a 2FA and also improving our skills set by always learning new security measures on how to secure our data and asset and also more security design should be made available to always be ahead of the hackers.
I think often we forget how much information we are sharing online without even realizing it can cause negative incidents for us. There is a need for more awareness on social engineering where we can educate folks on how what they share online can impact them negatively if there were a victim of cyber-attack. We can have the most secure systems in the world but without humans actively thinking about the consequences of their actions online, bad actors can exploit.