Imagine a sunny day setting in a coffee shop, peacefully sipping your Frappuccino drink, then someone next to you hijacks your car key fob without even touching it or talking to you.
A recent statistic by the Insurance Bureau of Canada (IBC) shows that auto theft insurance claims spiked to $1.5 billion in 2023 [3]. The numbers show a concerning car theft increase especially in the last four years, so what is the story?
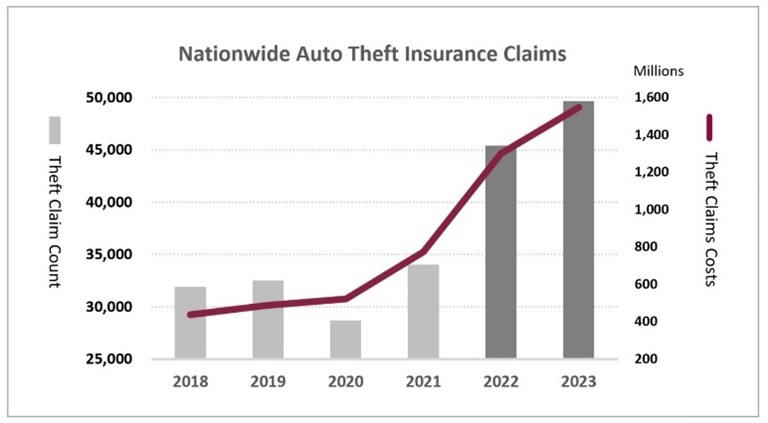
Canada nation wide auto claims 2023 [3]
The Story of a Crypto Grabber “Flipper Zero”
According to Flipper Zero’s website, the device was launched in 2020 as a community project [1]. $4.8 million was raised through a campaign on an online funding-raising platform called “Kickstarter” [2]. The device was promoted as a portable multi-purpose gadget that helps security nerds and researchers in security penetration tests without a need to design sophisticated printed circuit boards (PCBs) [6]. The portability of this savvy tool made it widely adopted by the security community and led to an influx of a variety of creative open-source applications published by the community developers. Starting from cloning NFC cards to sniffing any radio frequency signals. Nevertheless, the tool was not available for legitimate use only, but also for malicious hackers as a new way of exploitation techniques.
The federal Innovation, Science and Economic Development (ISED) linked the automobile theft surge to the flipper devices and revealed an investigation document (DGSO-003-24) spotting the strong relationship between the car theft surge and this emerging flipper as a crypto grabber [4].
“Code grabbers or crypto grabbers: devices designed to receive or copy the code emitted by a vehicle remote key to replicate and/or transmit the copied code to access the vehicle.,” posted by ISED.
On February 8th, 2024, Canada’s federal government’s public safety minister Dominic LeBlanc announced the banning of the Flipper Zero devices (Flippers) due to surging automotive thefts. These flippers can copy the wireless signals of the Remote Keyless Entry (RKE) fobs allowing offenders to steal any car without any traceability [5].
How the Flipper Zero work?
Sending wireless codes from key fobs to a car securely has been an arena for vehicle theft crime since the mid-nineties. Initially, the key fob was a primitive design sending a fixed (static) message from the fob to the car using a short Radio Frequency (RF). In a nutshell, the signal contains a static (fixed) frequency that maps to a specific function like opening the car doors. It was not a troubling effort for an intruder to break this system by capturing or sniffing the signal and reusing it repeatedly without needing the key fob anymore.
With technology getting advanced and compacted, the Flipper devices just came perfectly to be a portable gadget as smaller as the keychain in size. Flippers are equipped with built-in local storage and various transceiver modules that can store signals and reemit them on target vehicles. It is not only easy to use but also can intercept fob signals without anyone noticing.

The Dilemma
The evolution of using computer boards in automobile manufacturing imparked on various anti-theft attempts, some of these were good yet are breakable. Rolling Numbers (aka, Rolling Code) is one common anti-theft design that depends on the use of symmetric cryptography calculating a challenge code that must match both the car and the fob. The car would have a computer board that maintains a list of rolling numbers (generated incrementally and used in a sequential order). These rolling numbers are used in calculating a symmetric challenge code. Once the challenge is confirmed and matched, the car allows certain actions like door opening, etc. It is a symmetric system as each time the fob is pressed by the car owner, both the car and the fob must use the same rolling number to calculate and have a matching challenge code. Once a rolled number is used, the car removes it from the list, then the next expected rolling number is incremented for the next fob use. The car maintains a lengthy list of rolling numbers list that is enough for tremendous, and long fob usage. Here is an interactive demo to play the rolling numbers game (How Rolling Code Works (harryli0088.github.io) [9].
Each challenge code is calculated as a combination of a serial number (which could be the Vehicle Identification Number or VIN) in addition to a rolling number from the maintained list. Now consider this situation, what if an attacker sends a rolling number faking it as your original fob? now the next expected rolling number is incremented, which means your intercepted fob now is out of sequence as it has an old number that has been removed already from the list. That is why I urge you, please do not try flippers in your car.
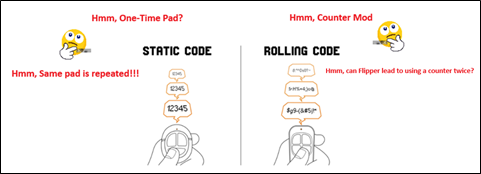
Flipper Zero Launches Campaign to Fight ‘Absurd’ Canadian Device Ban [12].
While rolling numbers model is a good cryptography as it is hard to break the content of the signal and know the rolling number sequence, yet it is a breakable cryptosystem. The attacker did not need to know the content of the challenge code to break into the car. The implementation of this cryptosystem did not prevent the attacker from cloning the fob signal and retransmitting it again then accessing the car. The good side of this model though, is that the attacker can not reuse the same signal multiple times. Also, copying the fob signal is possible only the if fob is pressed physically by someone and the attacker happens to be near to that signal to capture it.
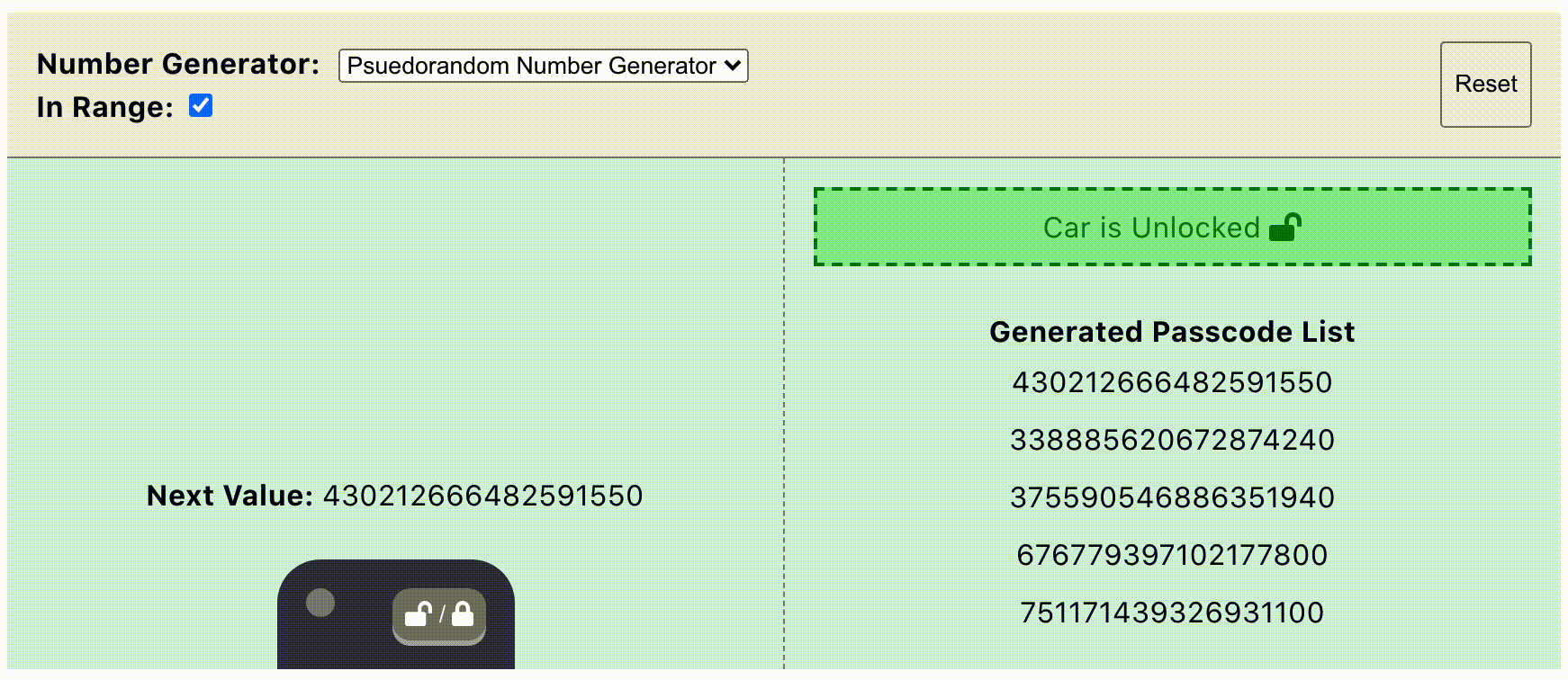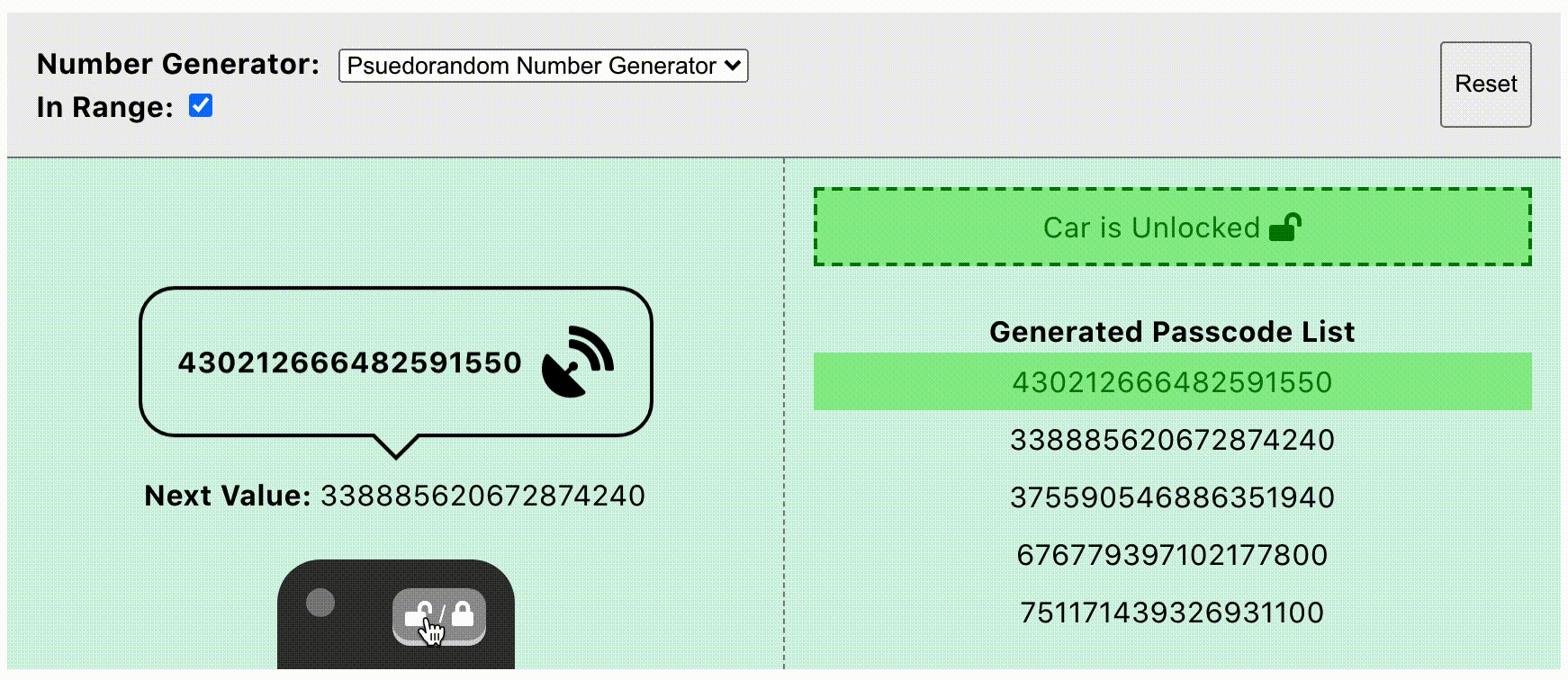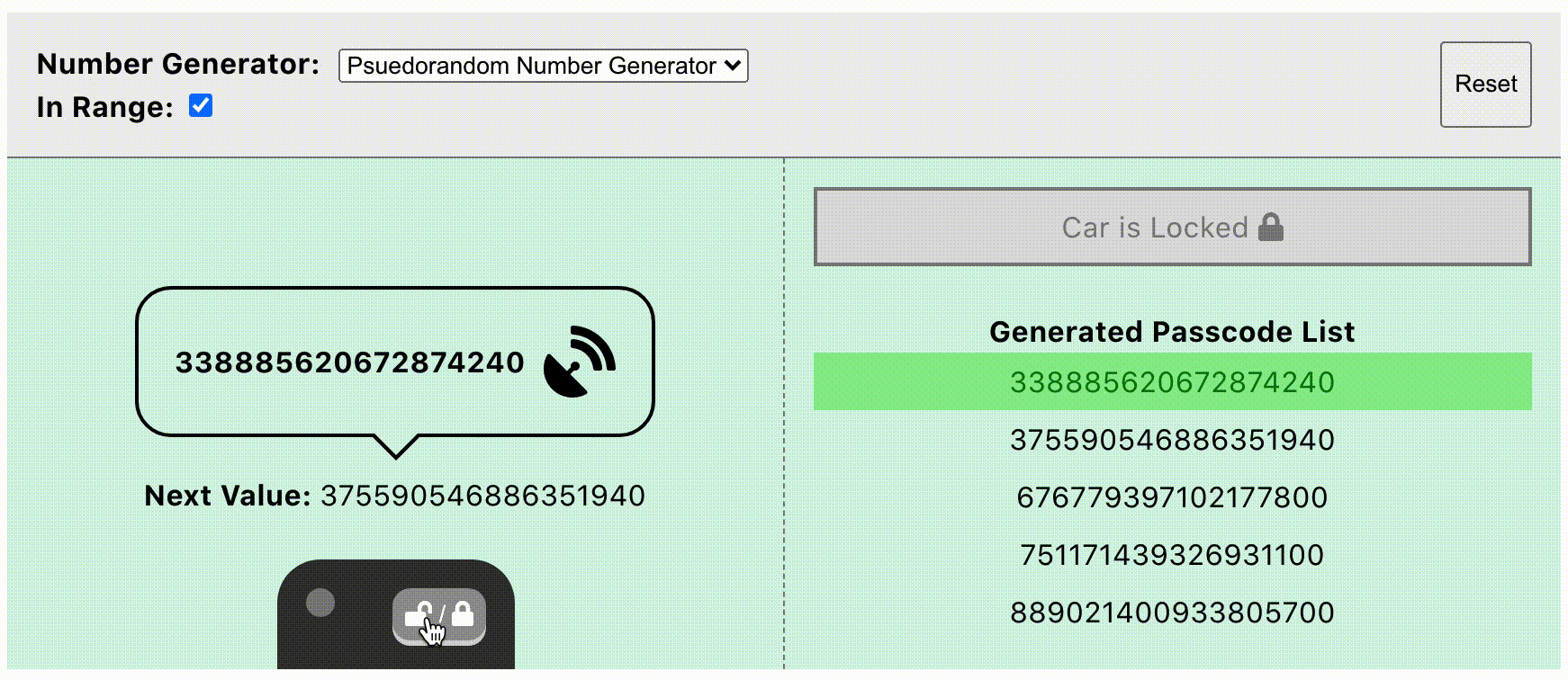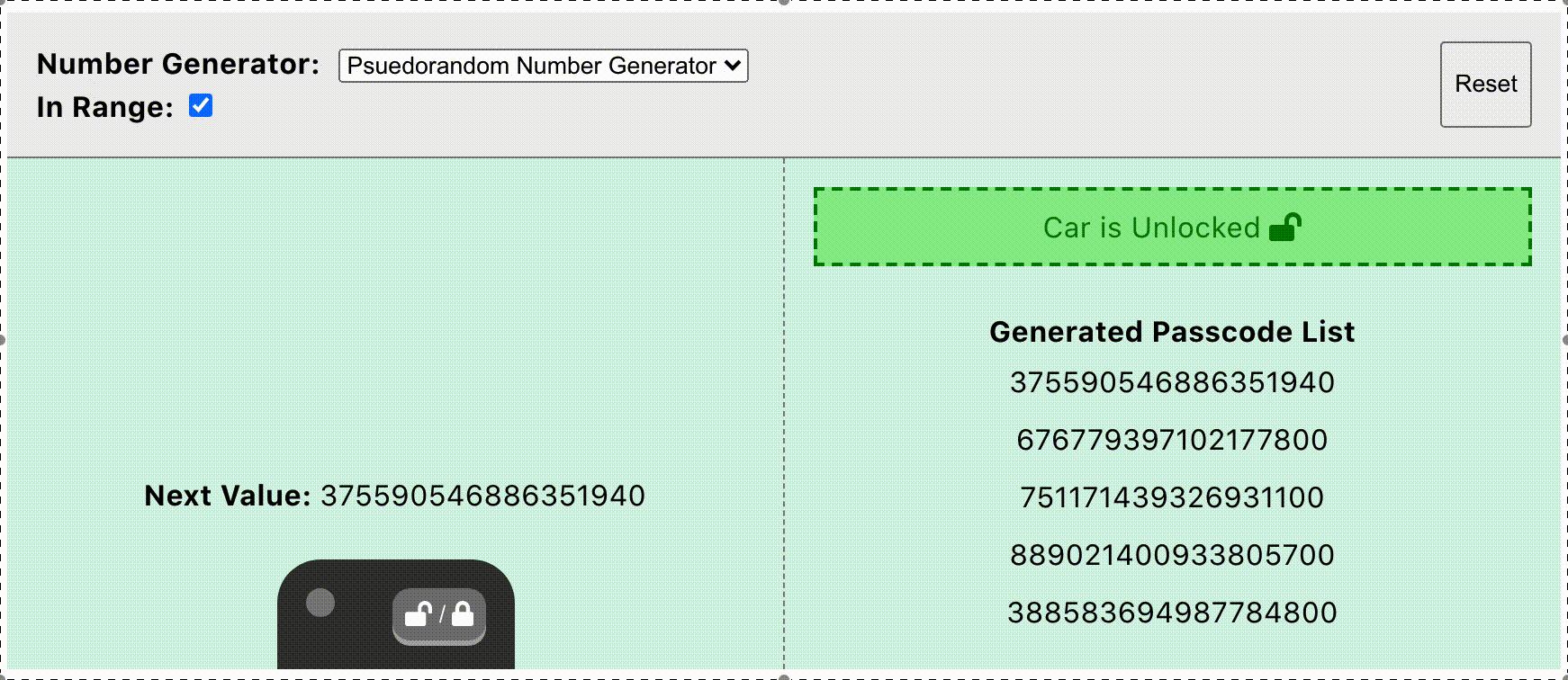
Rolling Code, Securing keyless entry systems [9].
The manufacturers realized a need to make it hard for the attackers to sniff the fob signals. Hence, a two-way communication is essential where the car’s computer board and the key fob can communicate automatically confirming the symmetric challenge without even pressing anything on the fob. In modern cars nowadays, this typically happens when the car detects a fob in a close distance range, the car then sends a challenge code to the fob expecting a reply with a challenge code containing a correct rolling number. Once the challenge confirmation happens, the car ensures the challenge is correct and belongs to an authorized fob, then it allows the fob to perform certain actions like opening the door or even starting the engine. This is very similar to the same previous workflow except it initiates the communication automatically when there is a proximity between the car and the fob.
Unfortunately, the attackers got cleverer coordinating the hacking attack using a two-phase method called the Relay Attack. In this type of attack, the attackers establish a side shadow communication channel where each obtains the challenge code without the need to have proximity between the car and the fob, as shown in the diagram below. In this exploitation, one attacker approaches the car with a transceiver faking itself as a fob, while the other attacker has another transceiver next to the fob faking itself as a car. Both attackers have a shadow private communication channel where they can retransmit the signals received from the car and authorized original fob, establishing the proximity but at a longer distance. Now think of the coffee shop story especially when go for coffee next time, please do not panic and start looking around.
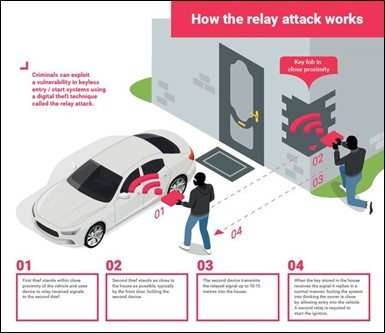
How the auto relay on attacks work [10]
One puzzling point on the rolling number method as a symmetric cryptography implementation is, it lacks the sense of identity for the communicated devices. The Relay Attack example shows that any attacker can fake being a car or a fob. The question now is how can the car and the fob be sure of the identity of the communicating devices? Yes, the answer is using asymmetric cryptography and digital signatures. However, this entails various questions and concerns. I really hope that we do not pay for annual fees to renew our car fobs.
So, What Is Missing?
There are a few noticed issues in the current anti-theft models:
- Absence of Identity Authentication for the communicating devices. How the car can be sure it communicates to an authorized fob, and vice versa as well, how the fob can be sure it communicates to a car it belongs to? How to ensure none of both are being intercepted by fake transceivers?
- The proximity is not a security control.
- Symmetric key is a strong cryptography if used carefully. The cryptosystem implementation though is a key factor to secure the anti-theft model.
An Interesting Question, Can Flippers Perform “Relay Attacks”?
It is a controversial debate, and the answer is yes and no. It depends on the exploitation circumstances. The Flipper enthusiastic community is creative and is adding more attached gears to the device extending the RF range and, in some cases, it can crash a cell phone remotely.

Expansion Board for Flipper Zero [11].
In contrast, other security experts perceived Flippers as a portable handy gadget that went viral on social media. However, they still see Flipper devices as limited in hardware and radio frequency. In fact, experts know other alternatives in the market can do better. Ivan Reedman, the director of secure engineering at IOActive, explained, “To attack with the Flipper Zero is substantially more complex than simply relaying the signal to the keyfob,” said Reedman. He also said relay attack devices are readily available or can be easily assembled.” [7].
Conclusion
There are various RF hacking devices used in auto theft existed in the market for years. What made Flippers Zero so popular is its portability and its ability to exploit wide different vulnerabilities beyond auto theft. In fact, the Flipper Zero became very visible as it caught social media attention and led to a government demand for banning. There will always be a new device called whatsoever, and the banning will never prevent future auto theft. These anti-theft systems are weak already, the government should encourage cryptographers and researchers to study these cryptosystems and work with the manufacturers to enhance their security posture for these systems. Finally, wrap this reading with Dr. August Kerckhoff ‘s principle, “The system must not require secrecy and can be stolen by the enemy without causing trouble. That the method used to encipher data is known to the opponent, and that security must lie in the choice of key.” [8].
References:
[1] Flipper Zero corporation. (n.d.). Retrieved from https://flipperdevices.com.
[2] Flipper Zero – Multi-tool Device for Hackers. (n.d.). Retrieved from https://www.kickstarter.com/projects/flipper-devices/flipper-zero-tamagochi-for-hackers.
[3] New data shows severity of Canada’s worsening auto theft crisis – Theft insurance claims top $1.5 billion in 2023. (2024, May16). Retrieved from https://www.ibc.ca/news-insights/news/new-data-shows-severity-of-canada-s-worsening-auto-theft-crisis.
[4] Consultation Relating to the Use of Radiocommunication Devices in Auto Theft. (2024, May). Retrieved from https://ised-isde.canada.ca/site/spectrum-management-telecommunications/en/learn-more/key-documents/consultations/consultation-relating-use-radiocommunication-devices-auto-theft
[5] Federal action on combatting auto theft. (2024, Feb 8). Retrieved from https://www.canada.ca/en/public-safety-canada/news/2024/02/federal-action-on-combatting-auto-theft.html.
[6] Flipper Zero gets a big firmware upgrade, and some amazing new features. (2024, Sept 11). Retrieved from https://www.zdnet.com/article/flipper-zero-gets-a-big-firmware-upgrade-and-some-amazing-new-features.
[7] Canada’s Planned Flipper Zero Crackdown Provokes Backlash. (2024, Feb 13). Retrieved from https://www.bankinfosecurity.com/canadian-flipper-zero-planned-crackdown-provokes-backlash-a-24348.
[8] Auguste Kerckhoffs, ‘La cryptographie militaire,’ Journal des sciences militaires, vol. IX, pp. 5–38, Jan. 1883 [PDF], pp. 161–191, Feb. 1883 [PDF].
[9] Rolling Code, Securing keyless entry systems. (n.d.). Retrieved from https://harryli0088.github.io/rolling-code.
[10] Keyless car theft: What is a relay attack, how can you prevent it, and will your car insurance cover it? (n.d.). Retrieved from https://leasing.com/guides/relay-car-theft-what-is-it-and-how-can-you-avoid-it.
[11] Expansion Board for Flipper Zero. (n.d.). Retrieved from https://oman.whizzcart.com/product/20972372/for-flipper-zero-modification-module-expansion-board-for-flipper-zero-2-4g-module-expansion-support-nef-sniffer-mousejacker-cc1101-module-wifi-multiboard-development-board-for-flipper-zero.
[12] Flipper Zero Launches Campaign to Fight ‘Absurd’ Canadian Device Ban. (2024, March 20). Retrieved from https://www.pcmag.com/news/flipper-zero-launches-campaign-to-fight-absurd-canadian-device-ban.


Great post, Tamer! I really enjoyed your thorough analysis of the different attacks that car thieves can execute based on the vulnerabilities of key fobs. The ingenuity of attackers is fascinating, and it makes it clear that we should all adopt a “security mindset” as explained by Bruce Schneier here: https://www.schneier.com/blog/archives/2008/03/the_security_mi_1.html. That way, we can pre-emptively thwart these types of attacks. I agree with your statements in your conclusion that the solution to prevent these car thefts should not be banning Flipper devices, but the onus should be put the on car companies to implement more secure cryptographic solutions.
Thanks, Nicole. I agree with you on the concept of Dr. Schneier thinking, as an eavesdropper it is essential to find the weak links in the system and exploit these security holes. As we learned in the lectures, a $5 wrench is cheaper than breaking the cryptographic algorithm. In the car theft specifically, the attacker did not need to know the encrypted message, but just re-resending it.
what a good post giving insight to the how flipper device caused major security concern in Canada due car theft. i’m not surprise about popularity of the device on social because the device was portable and make life easy for users before the attacker got the knowledge of its vulnerabilities. i strongly with your conclusion below ‘These anti-theft systems are weak already, the government should encourage cryptographers and researchers to study these cryptosystems and work with the manufacturers to enhance their security posture for these systems.’
Absolutely George. It is crucial making the cryptographic algorithms available and questionable to experts identifying the weaknesses as per Dr. Kerckhoff’s principle from scientific perspective.
Amazing read Tamer!! I followed CBC news analysis on the relay attacks amounting to the surge in vehicle thefts in Toronto but you post definitely explains the topic in great detail. Thieves have capitalized on the vulnerabilities in popular vehicles which the manufacturers have overlooked for years and some for decades. One such attack is the Rolling PWN I Honda Vehicles. Honda vehicles use rolling codes to unlock the vehicles, so when the key fob is pressed the rolling codes generate a code and is used to unlock the vehicle, rolling codes are used to prevent man in the middle or replay attacks. But in Honda vehicles the codes doesn’t need to match it just needs to fall in a window, once the codes are send to a Honda vehicle the codes are resynchronized, now once the counter is resented the old codes can be reused in the order to unlock the vehicle. Now the most astonishing part of the story is the vulnerability came is limelight in 2022 but it was discovered in 2012 , so currently all vehicles in market are vulnerable.
Reference: Author : Sue Poremba, What you should know about the Honda key fob vulnerability, link: https://securityintelligence.com/articles/what-to-know-honda-key-fob-vulnerability/
Thank you, Kaushik. The fact that Flipper Zero is portable and can be carried in a pocket sniffing RF signals without being noticed is a scary thinking. It introduces a lot of potential attacks not limited to car theft only but even building access, door tags, and NFC cards in wallets. I read about Nano-Technologies in spying gadgets and I have become furious about what I am approaching since that.
I had been working on a similar type of concept in my undergrad. These systems are more vulnerable on remote sites, for example, deep sea, where we usually put some sensors to get weather updates or naval security. In those scenarios, information is usually collected from sensors and sent to the databases placed in the land. The concerned authority enters the system through proper authentication to have those updates. So the idea we generated in our project is that we have set multiple layers of security where new and old users will be authenticated differently to reach the system. Again, they will identify themselves through an auto-generated secret key using the AES algorithm. In this way, outsiders will identify easily, and the system will be alerted by them. Lastly, I want to highlight that, now-a-days, this kind of system has proven very essential for us, but at the same time, we have to be aware of them as those can be easily breached by the hackers.
Nice topic the fact that you explained this in details just shares more light in the vulnerabilities of the flipper device and how most cars right now are easy to steal. so the government should encourage a more synchronous cryptographers into the manufacturing systems so they can build a more secured systems for our cars.