Recently, Zimbra email servers have come under threat due to a critical Remote Command Execution (RCE) vulnerability, identified as CVE-2024-45519. This vulnerability has been actively exploited, prompting urgent warnings from cybersecurity experts and organizations like Proofpoint and HarfangLab.
What is CVE-2024-45519?
The vulnerability was first reported by HarfangLab’s threat researcher, Ivan Kwiatkowski, on September 27, 2024. Within 24 hours of the report, Proofpoint began detecting malicious activities linked to this vulnerability. Attackers have been sending spoofed emails that mimic Gmail addresses, embedding malicious code in the CC field. This tactic exploits weaknesses in Zimbra’s postjournal service, enabling unauthorized access and execution of commands on affected servers.
How the Vulnerability Works
Initial Discovery
To fully understand the nature of this vulnerability, researchers at Project Discovery adopted a comprehensive approach by examining the patch to identify the original flaws. Utilizing reverse engineering tools like Ghidra, they analyzed the patched postjournal service, focusing on critical functions such as system and exec*. During their investigation, they discovered a function named run_command, which could be traced back to the address_lookup function referenced by main. This led to the identification of how user input could be manipulated to execute arbitrary commands.
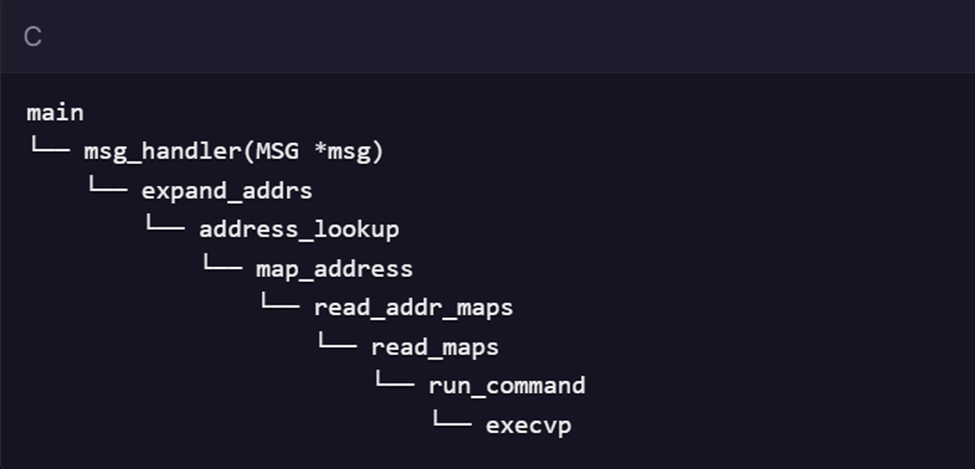
Source: ProjectDiscovery.io
In the unpatched version, the lack of input sanitization created a significant security gap, allowing attackers to inject and execute malicious commands. The patched version, however, implemented changes such as the use of execvp, which treats user input as an array, thus mitigating the risk of direct command injection.
Source: AI generated
Key Changes in the Patch
- Input Sanitization: The introduction of a new function,
is_safe_input, serves as a critical line of defense. This function sanitizes user inputs before passing them toexecvp, significantly reducing the risk of exploitation and ensuring that only safe commands are executed. - Replacement of Vulnerable Functions: The patch replaced the insecure
popenfunction—historically known for its vulnerability to command injection—withexecvp. This change enhances security by preventing unauthorized command execution directly from user input.
The Importance of Timely Patching
The CVE-2024-45519 incident underscores the necessity for administrators to promptly install security patches released by Zimbra. Cybersecurity is a constantly evolving field, and threats can emerge rapidly. By remaining vigilant and proactive in applying updates, administrators can safeguard sensitive data and maintain the integrity of their email servers. Regular audits and monitoring of system activity can further help in identifying potential exploitation attempts.
My Opinion
Developers should always implement input sanitation when dealing with user input. Before executing any code, it is crucial to validate the input to prevent potential vulnerabilities. Proper input validation not only protects the application from attacks but also fosters a culture of security awareness in software development.
Conclusion
The CVE-2024-45519 vulnerability in Zimbra’s postjournal service highlights significant weaknesses that could lead to severe consequences if left unaddressed. With the introduction of input sanitization and safer function calls in the patch, administrators can better secure their systems against potential attacks. Staying informed and proactive in applying security updates is essential for any organization utilizing Zimbra email servers.
For a detailed walkthrough of the vulnerability and its implications, check out the full analysis by Project Discovery here.

I completely agree, Ranjan. The input sanitization is a must—it can make such a difference in preventing these issues. The CVE-2024-45519 vulnerability really highlights how important it is for us to keep up with patches and security updates. Appreciate you sharing this important information!
To prevent SQL injection and remote command execution, both need proper input validation from the developer. It is great to see that the patch was given in a short time. I wonder how attackers are attempting, sending spoofed email, mimic a gmail address along with malformed code in cc !!!
Well done Smruti! Your thorough and insightful study of the Zimbra Mail Server vulnerability is quite impressive. I really enjoyed your explanation of the vulnerability’s mechanism of operation and the main adjustments made by the patch. It is important to emphasize the significance of input sanitization because it draws attention to a fundamental principle of coding that is often overlooked.
Well explained, Ranjan! This situation really underscores the need for a proactive approach to cybersecurity. It is indeed very important to release patches quickly because vulnerabilities like this can lead to serious risks such as financial losses, damage to reputation, and even regulatory penalties, depending on the type of data at stake. Staying ahead of these threats is key to protecting both the organization and the trust of their customers.
Excellent job! With this blog, The Zimbra Mail Server vulnerability (CVE-2024-45519) exposes servers to remote command execution through maliciously crafted emails. Timely patching and implementing input sanitization are crucial to securing systems and preventing exploitation.
Great post, Smruti! It’s frightening to think that just using email could allow for remote code to be executed. Most people are aware of phishing and will take care to not click random links in emails from senders that they don’t know. However, most of us wouldn’t consider that the emails in a CC field could be dangerous, and just by those being processed, code could be executed on our devices for any reason the attack wishes. I am curious when this would occur as well. Does just viewing your inbox cause the code to execute, or is it when you open the email?
Great post Smruti, something that really caught my eye was when you mention that with 24 hours of the report about the vulnerability, Proofpoint began detecting malicious activities linked to this vulnerability. Obviously we have to assume that the vulnerability was already being exploited prior to the report, but what about the case where the people who wrote the report where the first to encounter it. This reminded me of “https://crt.sh/” which is a website that lists all newly registered domains, and as we saw in the worksheet, the domains where immediately attacked. Are there people monitoring blogs and journals for new vulnerabilities to try to exploit? should the people who discover these vulnerabilities be required to come up with a solution before publishing or is that not their job. Even if they do post a fix, how quickly will that be adopted and how many hackers will use this as a new vector of attack in the mean time? The more I see the more it feels like the attackers are always favored while cyber security professionals are just playing catch up.
Great educational blog Ranjan! It is crucial for organizations that rely on Zimbra for their email services to understand the specifics of CVE-2024-45519. Preventing attacks is always better than dealing with the aftermath. The possibilities of remote command execution is alarming, as it can lead to severe breaches and data loss. This highlights the importance of input sanitization. Additionally, regular security audits and keeping software up to date can further enhance defenses against such vulnerabilities.