What happened?
On Oct 11th 2024 all 22 locations of public libraries across Calgary was shut down amid a cyber-attack. The early news suspected it to be the ransomware attack endangering public’s crucial data at the hands of attackers.
Why was library targeted?
“Libraries are a rich target, and the reason that they’re rich target is because they hold a lot of data,” said Ritesh Kotak, a Toronto-based cybersecurity and technology analyst.
The Public library contains crucial data of its users. At the time of getting the library card, a user is needed to provide sensitive data as in date of birth, address, full name and photo ID. From a hacker’s point of view, it is an ideal platform to attack and demand ransom money.

Since the beginning of Covid-19 the cyber attacks have gained more popularity as the paradigm of working has shifted to remote access/cloud-based. However, the cyber extortion methods dates back to 1980s and the first ransomware attack took place in 1989 with the PC Cyborg Trojan.
In today’s evolving IT world, cyber security practices need to be more robust than ever before to save end users, clients and companies data from cyber-attacks and to mandate confidentiality, integrity and availability of data always.
Since the Calgary Library’s Ransomware attack is quite recent; the final report is yet to come, let’s investigate the Ransomware and its categories to get a closer look at the situation.
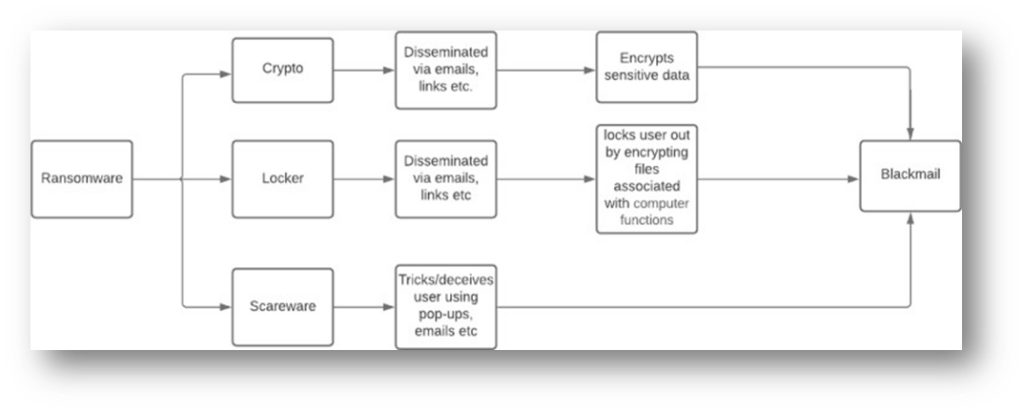
There are three types of Ransomware attack, locker, crypto, and scareware.
Scareware: It manipulates end user to click a pop-up ad that traps user into downloading a software in order to run a certain application. In the end, if the user clicks it ends up downloading a malware infecting the system.
Locker: The purpose of this type of ransomware is to block the user’s computer. It is done by encrypting certain files which tends to lock the computer screen/keyboard so that it cannot be accessed/used.
Crypto ransomware: Unlike locker technique, it does not alter the basic computer functions but encrypts the user’s sensitive files. It is an irreversible ransomware as current encryption methods such as AES and RSA are almost impossible to revert if the implementation is properly done.
There are three encryption schemes for Crypto Ransomware;
- Symmetric: A purely symmetric approach is problematic as the encryption key must be embedded in the ransomware, this makes this approach vulnerable to reverse engineering.
- Asymmetric: The issue with this approach is that asymmetric encryption is slow compared to symmetric encryption and hence struggles to encrypt larger files
- Hybrid: The hardest to decrypt and the most effective method is hybrid encryption. It uses both symmetric and asymmetric encryption.
How to mitigate Security threats and Ransomware attacks
- The unawareness about the use of internet, the scarcity of knowledge of ransomware techniques amongst the masses and an inadequate detection mechanism result in more frequent attack these days.
- Implementing strong network segmentation layers that contain lateral movement at the time of attack.
- Installing antivirus and firewalls to secure sensitive data.
- Patching needs to be done for all the systems, keeping high priority for internet facing apps/systems. By doing so, the loose access points can be minimized for the attackers.
- Install an advanced Endpoint Detection and Response solution.
- A very well formulated disaster and recovery plan for all the critical systems.
- Encrypting sensitive data using best in place mechanisms to secure sensitive data.
- Systems and end users must be enforced with the least privilege Also logging must be done about all the key accesses.
- Multi-factor authentication (MFA) for all critical systems including VPN access must be implemented.
References;
https://www.cbc.ca/news/canada/calgary/calgary-public-library-cyberattack-ransomware-1.7356464
https://pmc.ncbi.nlm.nih.gov/articles/PMC8463105/#bib001
Lallie H., Shepherd L., Nurse J., Erola A., Epiphaniou G., Maple C., Bellekens X. Cyber security in the age of covid-19: a timeline and analysis of cyber-crime and cyber-attacks during the pandemic. arXiv preprint arXiv:2006.11929. 2020 doi: 10.1016/j.cose.2021.102248.
Tailor J., Patel A. A comprehensive survey: ransomware attacks prevention, monitoring and damage control. International Journal of Research and Scientific Innovation (IJRSI) 2017;4:2321–2705.
Kok S., Abdullah A., Jhanjhi N., Supramaniam M. Prevention of crypto-ransomware using a pre-encryption detection algorithm. Computers. 2019;8(4):79
Dargahi T., Dehghantanha A., Bahrami P.N., Conti M., Bianchi G., Benedetto L. A cyber-kill-chain based taxonomy of crypto-ransomware features. Journal of Computer Virology and Hacking Techniques. 2019;15:277–305.

Thank you for sharing this! My family frequently visits Calgary Public Libraries, and we were shocked to hear the news. As patrons, we were only informed about the temporary closure, with no information regarding any potential compromise of our accounts. The library is currently open but offering limited services. Patrons can check out only a limited number of materials, and we’ve been asked not to return books yet. I’m curious about the extent of the breach. So far, we haven’t received any suspicious mail or calls, and I hope it remains that way, especially since we’ve shared our information.
you’re welcome maria! it is unfortunate that the residents of this city have to go through this. I hope with the cyber security best practices, in future, we will be able to avoid such incidents. for now, fingers crossed as to how the public library would respond to this ransomware attack as it contains public’s crucial data.
It feels unsettling knowing that a place meant for community and learning can be hit by something as serious as ransomware. Your breakdown of the situation really highlights how vulnerable even everyday institutions are. Since the shift to cloud-based and remote access systems during COVID-19, the need for stronger cybersecurity measures has become more critical than ever.
Thanks for sharing this; it really got me thinking.
That is so true, we trust our data with the public platforms. and if the standards are not maintained with the cyber security best practices it can be very dreadful for all.
My daughter enjoys her time in public library and it feels that the institution close to my family had been attacked and shutdown for a while due to ransomware attack. We must concentrate on enhancing security measures for all technology-connected services since public service facilities are targeted by the cybercriminals. I have not received any correspondence or phone calls (if my info was compromised), but I am uncertain of the consequences. The library is operating with limited facilities now as per their mail communication.
A very recent incident! I can relate, as I received my Calgary Library Card a couple of weeks ago. I remember I had to submit my personal information to get one. These public domains are becoming targeted by hackers more and more. Besides, I liked your presentation, especially the structure of the various ransomware attacks and encryption schemes in it. It really helps to understand the types of the attack and how to prevent it.
Great post Maheen. I like the latter end of the blog where you highlighted some useful tips on how to keep adversaries out of our systems. the greater question is whether these institutions will enforce security practices like this. Time and time again personal information of users gets leaked in breaches like this due to errors that could have been avoided to begin with. How do we as Cybersecurity students and the general public ensure that robust security implementations are rolled out and enforced? Today it’s Calgary Public Library, tomorrow it could be another public institution.
The attack on this institution has shown the significant need for better protection of governmental and other public facilities. Enhancing security and sensitizing users to some of the complexities of ransomware threats are necessary. The attack may also remind organizations of current dangers.
Great work Maheen, your insight on recent ransomware cyber attack is really well structured. It is a crucial mirtigation step as a “Proactive Attack” defense strategy, however it is also imperative emphasizing on the “Post-Attack” defense strategy as well. Ransomware attacks evolve rapidly and can happen inevitably due to one of the misconfigurations or lack of wrong implementations. The proactive precautions can definitely reduce the probability but can’t help when post attacks happen. Hence, “Cyber Recovery” is one of the modern ransomware post-attack defense methods [1] (Dangi, et al, 2024). The idea behind this methodology is to create a cyber vault backing up all the critical data the can make the system recovered with the three security CIA triad (Confidentiality, Integrity, and Availability). This recovery vault is an air-gapped process where the backups are taken in a staged approach ensuring no direct network connection is available between the data sources and the cyber vault. Also, it involves using non-standard network protocols and ensuring a uni-direction network connection in the backup and restore processes.
[1] Dangi, S., Bhanjois, B., & Madan, N. (2024). PROTECTING DATA AGAINST MALWARE ATTACKS USING CYBER VAULT AND AUTOMATED AIRGAP CONTROL.
thank you tamer for providing more insights to the subject matter. It can be a way forward in getting things right and in place in order to avoid/or recover from future attacks.
Nice post, Maheen! A place like a public library can be a great place to have personal information, even some passive information related to financial or any other sophisticated things. Such information, like email addresses and mobile numbers, can pose a significant risk. Any public organization handling public personal information must maintain high standards and practices for information security and privacy. While there are various protocols and technologies in cybersecurity, proper implementation and regular updates and patch management are crucial. Additionally, all users and personnel involved in the service must be aware of cybersecurity best practices and standards. Hopefully, Calgary Libraries’ response to this matter will provide further insight into ransomware, allowing us to develop our understanding of it.
Absolutely Fahim, it is important to keep the public data safe so that such organizations won’t loose trust and credibility.
Super informative post. I can’t wait for the final report to come out about the hack and see how the hack was performed and what the weak part of the libraries system was. Though seeing Calgary’s library get attacked is also really jarring, as like most of my classmates I have a Calgary library card and have used the library. While I haven’t personally used it recently many of my family members and friends use it quite frequently and were affected by the hack simply because the library was closed because of the hack. I hope no data was stolen or any ransom is being paid though that’s likely wishful thinking. Like you said with ransomware attacks becoming more and more common after COVID everyone and every company needs to be more vigilant and careful not to fall victim to these types of attacks. Following the best practices you mentioned in the post to help thwart attacks before they become the next headline in the news.
Absolutely Hayden, i am also waiting to hear the final word from the organization to understand how the crucial public data is handled and what measures have been taken in order to keep the integrity of library safe at the hands of the attackers
Insightful post Maheen! I have been following closely the Calgary Public Library security breach. I am relieved to know as the preliminary report suggest the attack has been foiled and the detection systems in place was able to successfully wade off the attack right on time as the security team scrambled into action by taking the entire library network off the grid. This also proves that the security system in place is working and effective. We are glad that the Calgary public library attack didn’t go the way Toronto Public Library went, which took 4 months and 1 million books piled up for return. Ransomware has been on the rise and organizations supporting critical infrastructure from govt to finance needs to be on their toes to defend.
Reference: https://www.bitdefender.com/en-gb/blog/hotforsecurity/hackers-attack-toronto-public-library/
https://www.cbc.ca/news/canada/toronto/toronto-library-ransomware-recovery-1.7126412
Nice post Maheen! I think that this is a good reminder for any organization that keeps personal data. This provides relevant data that can identify people. So it is an attractive target for hackers that can sell the information on the dark web. It is unfortunate that the Calgary Library service was a victim of this attack. But this has to confirm that any organization is exposed to attacks no matter how big or small they are. It is important to keep aware of these attacks and how to be protected against them. Thanks for the information Maheen!
This is so true, the data is either exploited or it is sold to the 3rd parties who would then use it to make even more money from the end users. It is really unfortunate that our data is not at all secure these days and more and more vigilance is required to keep ourselves safe from theft.
Great post Maheen! It is interesting to see how much the world has shifted since COVID-19 and continuing ahead in the future where technology is advancing quickly, cybersecurity remains of vital importance to ensure data is not compromised by unauthorized individuals. With data stripped from the library containing information of individual names, birthdates, emails, and photo IDs, cyber attackers may attempt a multitude of attacks. For example, attackers can impersonate individuals or create synthetic identities to commit fraud. Using this, attackers could potentially open bank accounts or even craft highly targeted phishing emails. This poses a significant danger to the individuals registered in the Calgary Public Library systems. Working on implementing strong best practices is vital to prevent such attacks.
Great post Maheen! It is interesting to see how much the world has shifted since COVID-19 and continuing ahead in the future where technology is advancing quickly, cybersecurity remains of vital importance to ensure data is not compromised by unauthorized individuals. With data stripped from the library containing information of individual names, birthdates, emails, and photo IDs, cyber attackers may attempt a multitude of attacks. For example, attackers can impersonate individuals or create synthetic identities to commit fraud. Using this, attackers could potentially open bank accounts or even craft highly targeted phishing emails. This poses a significant danger to the individuals registered in the Calgary Public Library systems. Working on implementing strong best practices is vital to prevent such attacks.
Absolutely, with the AI gaining more popularity and advancement lately, impersonating someone won’t be much of an issue with the relevant data collected from such an attack. you have given very good analysis of the worst case scenario of such an incident.
Nice post Maheen. The ransomware attack on Calgary’s public libraries highlights the growing vulnerability of public institutions to cyber threats. Libraries, though seemingly low-risk, hold sensitive data, making them prime targets for attackers who exploit weak points in publicly funded infrastructure. This incident serves as a wake-up call, not only for libraries but also for other institutions that store sensitive user information.
That is so true, we trust our data with the public platforms. and if the standards are not maintained with the cyber security best practices it can be very dreadful for all.
Great post and thanks for this! I absolutely agree with and believe that having robust and strong disaster recovery plans would be a great first step to identifying ways to recover critical systems, which would also be supported by a business continuity plan to ensure that at least the basic business operations are still ongoing. The implementation of the least privilege principle and MFA are also crucial because applying the least privilege principle ensures users only have access to the minimum data necessary to fulfill their tasks. I believe is a great suggestion because implementing this goes hand in hand with the sensitivity of data each user is authorized to have access to.
I agree with this Faizah. With the given security best practices, one can ensure that the data is at an arm’s length of the attacker. hopefully, together we can build the robust system where the data is not easily exploited at the hands of the attackers every now and then.