Hospitals and other healthcare organizations has been a lucrative target for threat actors since the dawn of ransomware attacks. This is primarily due to the volume of sensitive information stored in hospitals like Patients personal information, their medical records and access to diagnostic devices. Some of the industry experts believe that a patients medical and personal data is worth 10 times [1] over their credit card information to the hackers. And the latest victim on the market is ‘Ascension Healthcare.’
Ascension is one of the largest health systems in the United States with over 142 hospitals operating in 19 states and District of Columbia.[2]

On May 9, 2024, Ascension released a public statement that the company detected unusual activity on select technology network system on May 8, 2024, which they believed was a potential cybersecurity event. They also mentioned: “Our care teams are trained for these kinds of disruptions and have initiated procedures to ensure patient care delivery continues to be safe and as minimally impacted as possible. There has been a disruption to clinical operations, and we continue to assess the impact and duration of the disruption.“[3] But we are about to learn how much the care team struggled to keep patients alive.
How did it Start?
All it took was one email to bring an entire hospital system down. Apparently, an employee at one of Ascension hospitals in Michigan accidentally downloaded a malicious file, mistaking it for a legitimate document. In a media statement from Ascension on June 12, 2024, they clarified that employee accidentally downloaded that malicious file and that was anything but an ‘honest mistake’.[3] A mistake that allowed the attackers to hack into seven of the hospital systems 25,000 servers resulting in a week-long cyber-attack.[4] CNN reported that the type of ransomware used in this hack contains the signature of a broad criminal group called ‘Black Basta’. They are known for their accelerated attacks against healthcare sector with at least two other health care organizations in Europe and US affected in the last month causing ‘Severe Operational Disruptions.’ [5]
The exact origin of the ‘Black Basta’ group is still unclear, but there are several indications that the group operates out of Eastern Europe with some ties to Russian cybercriminal networks. It operates as a closed ransomware-as-a-service (RaaS) group and some of the most popular threat actors in their groups includes Storm-1811 and FIN7.[11] You can read more about their strategy and infiltration techniques here: Storm-1811 | FIN7.
Day of the Attack:
Ascension had to pull something out of their playbook to ensure critical patient needs are addressed as soon as they became aware of the incident. Standard operating procedures in such situations includes:
- Shutting down the entire network immediately.
- Initiate Paper-trail/manual documentation procedures.
- Run possible diagnostic devices that are offline.
- Diverting Emergency care and Ambulances to hospitals that are not impacted by the attack.
- Post pone all scheduled appointment and surgeries.
- Halt all insurance processes, claims, and payment processing.
Majority of the health care workers were used to the digital way of working things out and have never done any sort of manual documentation. Kris Fuentes, who works in the neonatal intensive care unit at Ascension Seton Medical Center in Austin, said she remembers when paper charting was the norm. But after so many years of relying on digital systems, she said her hospital wasn’t ready to make such an abrupt shift.[2]
Marvin Ruckle, a nurse at an Ascension hospital in Wichita, Kansas, said he had a frightening experience: He nearly gave a baby “the wrong dose of narcotic” because of confusing paperwork.[4]
“For a lot of our nurses, they’ve never paper charted at all,” said Connie Smith, a charge capture coordinator in Wisconsin, “We were using forms that we pulled out of drawers that hadn’t seen the light of day in a long, long time.” [4]
For health care providers, this was not just about loss of data, cash and customer confidence. People’s Lives were at Stake – Literally!
As with most cybersecurity incidents, customers impacted through this attack were provided with complimentary credit monitoring and identity theft protection services. But the damage doesn’t stop there.[7]
With excruciating amount of financial loss and direct impact to patients’ lives in the last couple of years, The American Hospital Association has now written to Congress to bring in federal agencies to protect hospitals and health systems — and the patients they care for — by deploying a strong and sustained offensive cyber strategy to combat this ongoing and unresolved national security threat.”[8]
The Data Does Not Lie
Paying a ransom demand is like making a deal with the devil. There is zero guarantee that the paid ransom will return 100% of the stolen data and hackers exactly know the weak link when it comes to healthcare data. By putting lives at risk, hackers know these organizations are a ripe target for ransom demands being paid, and quickly. Let’s look at the below data to better understand the severity of the situation:
- 850 health care networks and hospitals were affected by ransomware in 2021.[9]
- 60% of health care organizations were hit with ransomware globally in 2023 and just in US it accounted to 389 impacted healthcare institutions.[10]
- Mortality rate increases by 1-2% when a cyber incident hits a hospital.[4]
- 239% increase in hacking-related data breaches in healthcare between 2018 and 2023.[6]
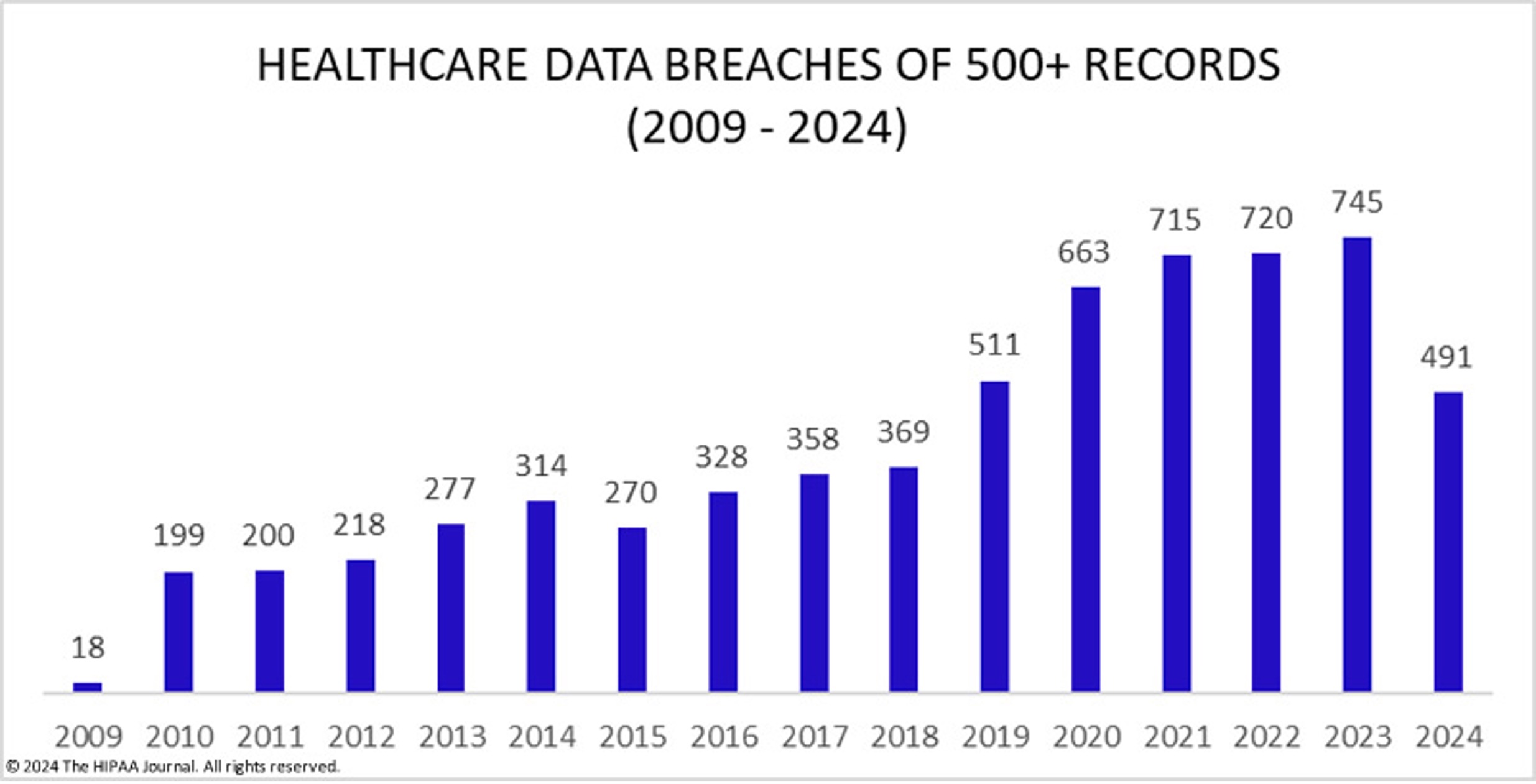
Source: HIPAA Journal Published on September 24, 2024: Healthcare Data breach Statistics
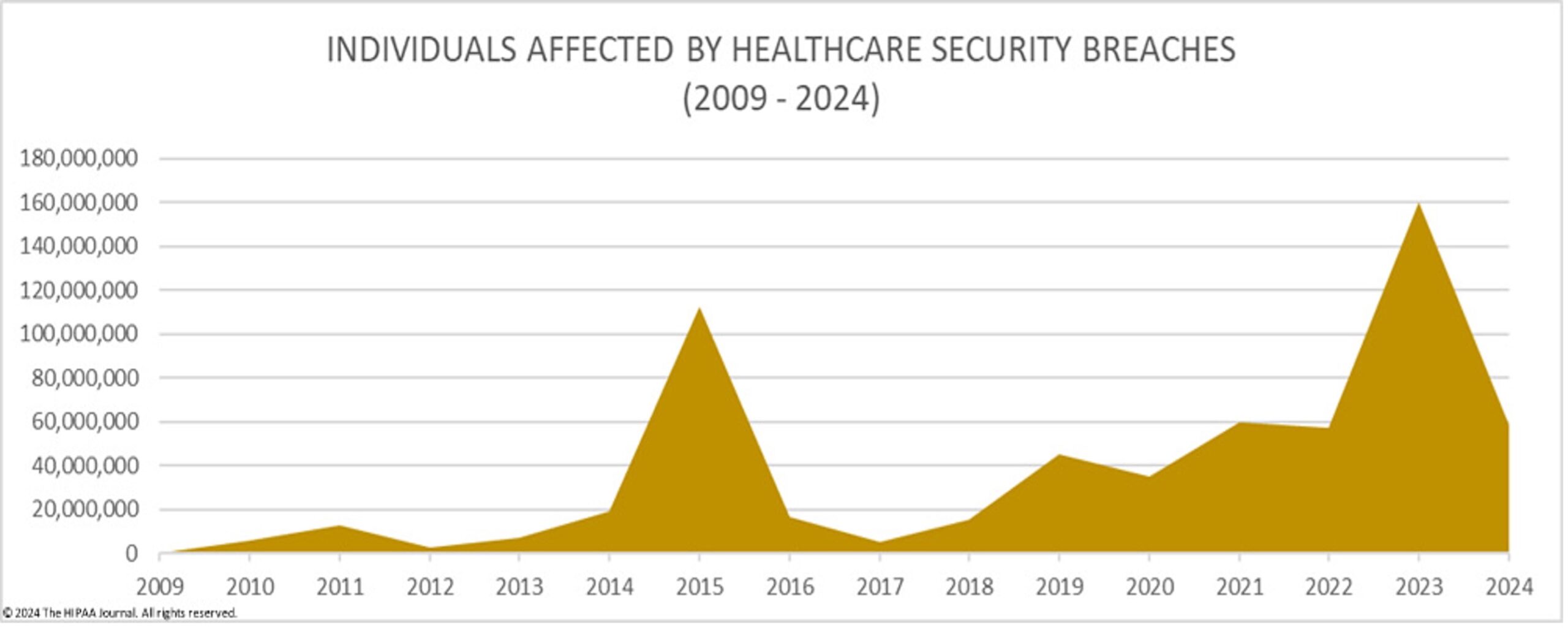
Source: HIPAA Journal Published on September 24, 2024: Healthcare Data breach Statistics
How to Avoid Cyberattacks:
The harsh reality is that when hospitals are preparing their budgets for the year, a new MRI machine or a piece of medical equipment or additional staff often takes precedence over a new data security system. For most medical care providers, security is still an afterthought. Threat actors understand this really well and exploit it to the full extent. Which is why healthcare institutions needs to desperately start implementing security solutions. Some of the key basic include:
- Cybersecurity Infrastructure: When a disruption can affect a human life, it is a chilling reminder to build the necessary defense against that disruption. A clear budget must be set aside to get advanced infrastructure that is built with Threat intelligence.
- Incident Response: During an attack, every second counts. Having an expert response team who knows exactly what to do and when to do could reduce the impact significantly.
- Backup and Contingency Plan: Ensure backup of all critical data is available on a different network and a contingency plan to access those records in an attack situation.
- Employee Training: Regular training of employees and repeated simulations to identify vulnerabilities in the form of Human error. This will help narrowing down to a target group and they can be re-trained to better engage with malware programs.
- Communication Protocols: Transparent and effective communication among team members ensures that information is disseminated accurately.
The Way Forward
Healthcare organization have always been slow to adapt to the constantly changing digital landscape because of the nature of sensitive data they store, and the amount of time required to validate a computer software by adhering to the quality standards set by organizations such as FDA. There are a substantial number of hospital systems that still runs on legacy softwares simply because of the absence of budget to update the software and get it through the validation cycle. This situation can only improve with direct government intervention to increase the budget necessary for equipping these institutions with better cybersecurity infrastructure and a skilled workforce. This will enable the healthcare industry to adopt a proactive approach and better safeguard themselves against such incidents.
References:
- The Value of Personal Medical Information: Protecting Against Data Breaches: https://www.naham.org/page/ConnectionsThe-Value-of-Personal-Medical-Information#:~:text=Personal%20medical%20data%20is%20said,telephone%20numbers%20and%20medical%20conditions. | Publishing Date Unavailable |Accessed on October 22, 2024.
- How the Ascension cyberattack is disrupting care at hospitals: https://www.npr.org/sections/shots-health-news/2024/05/23/1253011397/how-the-ascension-cyberattack-is-disrupting-care-at-hospitals | Published on May 23, 2024. |Accessed on October 22, 2024.
- Cybersecurity Event Update: https://about.ascension.org/cybersecurity-event |Media Statements Published between May 09, 2024, and June 14, 2024. | Accessed on October 22, 2024.
- The Ascension Incident: How One Email Took Down An Entire Hospital System: https://www.thinkstack.co/blog/the-ascension-incident-how-one-email-took-down-an-entire-hospital-system | Publishing Date Unavailable |Accessed on October 22, 2024.
- Cyberattack forces major US health care network to divert ambulances from hospitals: https://www.cnn.com/2024/05/10/tech/cyberattack-ascension-ambulances-hospitals/index.html | Published on May 10, 2024. |Accessed on October 22, 2024.
- Healthcare Data Breach Statistics: https://www.hipaajournal.com/healthcare-data-breach-statistics/ | Published on Sep 24, 2024. |Accessed on October 22, 2024.
- UnitedHealth says wide swath of patient files may have been taken in Change cyberattack:[https://apnews.com/article/unitedhealth-change-cyberattack-50e7e86ace92e95711dfbf8914d27db1] | Published on April 23, 2024. |Accessed on October 22, 2024.
- AHA House Statement on “Fiscal Year 2025 Department of Health and Human Services Budget: https://www.aha.org/testimony/2024-04-17-aha-house-statement-fiscal-year-2025-department-health-and-human-services-budget | Published on April 17, 2024. |Accessed on October 22, 2024.
- Baby died because of ransomware attack on hospital: https://www.nbcnews.com/news/baby-died-due-ransomware-attack-hospital-suit-claims-rcna2465 | Published on September 30, 2021. |Accessed on October 22, 2024.
- Nearly 400 US healthcare institutions hit with ransomware over last year, Microsoft says: https://therecord.media/ransomware-healthcare-microsoft-last-year | Published on October 15, 2024. |Accessed on October 22, 2024.
- Black Basta’s nasty tactics: Attack, assist, attack: https://blog.barracuda.com/2024/05/18/black-basta-nasty-tactics | Published on May 18, 2024. |Accessed on October 22, 2024.


Good post….i think the post highlights the challenges faced by the healthcare sector, which is a result of lag in adapting to the rapid change in technology and cybersecurity eco-system. The government have to provide more avenues to increase cybersecurity awareness in every sector that uses the internet.
I completely agree that healthcare organizations struggle to adapt to the digital landscape due to the sensitivity of their data and lengthy software validation processes. It is disheartening to see attackers exploit vulnerable situations, especially knowing that lives are at stake. Many companies believe their security protocols and disaster recovery plans are sufficient, but it often takes a real attack for them to realize their preparations fall short. It’s also true that employee training is crucial in preventing these incidents. Increasing awareness and providing regular reminders about potential threats can make a significant difference in safeguarding against attacks.
Nice work! I recall working on a telemedicine project for a district hospital in my home country. The integration of telemedicine into hospital healthcare is a huge technological achievement, yet cybersecurity remains a critical concern. Some of the risks include data privacy, communication security, and regulatory compliance. The future looks bright if we focus on user experience and data privacy first.
The challenges that healthcare organizations face in adapting to the ever-changing digital landscape are well known; however, with the use of advanced technologies and innovative security frameworks will highlight the need for robust measures to defend against sophisticated cyber threats targeting hospitals. It is necessary to maintain awareness and be proactive.
Excellent post! It’s alarming to see the rise in cyberattacks, especially when targeting hospitals where lives are directly at risk. Unfortunately, healthcare systems are often exploited by attackers because they hold sensitive data, operate on outdated software, and sometimes lack the resources for robust cybersecurity measures. It’s disturbing that attackers are aware of the critical nature of these institutions, yet still choose to exploit them. As highlighted, it’s essential for both the government and the community to work collaboratively to enhance cybersecurity measures. By doing so, we can protect not only sensitive data but also the lives that depend on these healthcare systems. Strengthening defenses and investing in proper infrastructure should be a priority to ensure patient safety and data integrity.
The Ascension Healthcare breach underscores a critical need for enhanced cybersecurity in healthcare. With rising cyber threats, the risk to patient safety is profound. The disruption exposed staff’s unpreparedness for manual processes, highlighting the need for comprehensive training and robust cybersecurity measures. The government’s role in bolstering cybersecurity defenses cannot be overstated. As the threat landscape evolves, so must our strategies and investments in cybersecurity. It’s crucial for healthcare organizations to invest in security infrastructure and collaborate with government efforts to protect sensitive data and ensure patient care.
Excellent work! I agree with your emphasis on the need for healthcare organizations to prioritize cybersecurity infrastructure. The post captures the strain on healthcare workers who had to pivot to manual processes under incredible pressure. It’s clear that incident response is critical, but this case underscores the importance of regular simulations and drills so that staff are better prepared for any digital interruptions. Hospitals are rightfully dedicated to patient care, but the risks from outdated systems are too high to ignore. This case should push not only Ascension but also other health systems to ensure they have proactive cybersecurity strategies in place.
While most hospitals have started paying attention to security risks, the one area that they are still struggling is real-time simulations. In a hospital set up, simulations like temporary manual documentation poses a significant risk as well. They end up relying on the trainings employees instead which most us know the level of importance it gets when you are dealing with emergency situations and sleep-deprived employees. But I agree its high time that every single security gap in a healthcare system is addressed with government intervention.
It’s impressive that they were prepared to operate even if their entire infrastructure went down. Though I’m little bit upset that even with 25,000 servers and such a large setup, yet no SOC or incident response team in place.
Nice work, well elaborated incident, Achu! Enjoyed reading this, I am amazed to see so many posts not just in our MISP blog but also cybersecurity news across multiple platforms these days are reporting new ransomware attack everyday. I am certain there are attacks happening every moment and the big buck ones are hitting the news whereas the small businesses, entities are getting lost in the piles of attacks happening across the globe. The geo-political situation isn’t helping and only exacerbating the situation state sponsored cyber attacks are on the rise. This is the new war! looks like the fight for data is already on. One can only imagine where this is heading, its crippling industries, massive losses, such incidents does make smaller vulnerable organizations go bankrupt, whereas the bigger ones scramble to keep their reputation intact.
Good job, Achu! The numbers presented are quite shocking, and it is manifest that hospitals are not very well protected from cyber threats. Healthcare organizations should adopt proper controls for its implementation, besides continuously integrating security controls and ensuring that employees who work with such specific patient recordings are well trained in handling sensitive information of such patients. One significant challenge is budget constraints, which make it difficult to phase out outdated, insecure systems. Considering these obstacles, it’s crucial to question the role of the government in addressing these issues.
Excellent post, Achu! I didn’t realize that healthcare information was so lucrative compared to banking information. That makes it clear that healthcare companies need to defend this PII much better. In terms of the specific issue that caused the vulnerability, it’s hard to know a good course of action for defending against a malicious file was downloaded. If it came from an email, perhaps better training around email safety and better scanning systems for incoming emails, especially from external sources, would have helped. If it came from a website, white listing trusted sites and better applications for blocking access to malicious sites might have helped.
Great post! I am shocked at how simply clicking a document in one phishing email can bring an entire hospital system down. Looking at the graphs, the number of individuals affected by healthcare security breaches have significantly increased since COVID-19 in 2020. With important data from banks are compromised, sensitive information such as credit card details are leaked but when health data is compromised, lives of individuals are directly in danger. Given the rise in AI platforms and tools, perhaps incorporating AI within hospital infrastructure will be beneficial and may lighten the load on cybersecurity teams. Having an AI algorithm sift through data continuously to report or flag malicious activity for cyber analysts to review will increase efficiency and security. Still, like you pointed out in your post, with incorporating new technologies to perform tasks, heavy validation is required as it is equally if not more important to ensure that introducing new technologies enhance security rather than create new vulnerabilities.
Well done Achu! It is a very insightful article. I was impressed by how the mortality rate in hospitals increased due to attacks on their IT infrastructure, these attacks literally cost the lives of people. Although medical services take extra care storing and managing sensible data it is still vulnerable to very specific attacks such as the one performed to Ascension.
One thing that came to my attention is how unprepared hospitals are for these scenarios. Just as there are fire drills or earthquake drills, there should be cyber attack drills so employees can be aware of further actions and reduce the impact on the service as much as possible. Thanks for the information!
Thank you Achu for this post!
The constant healthcare system target by the adversaries never ends! Its so clear they do not care about lives that are at risk but I believe the government should care and its time to set basic standards for the healthcare industry on prioritizing cybersecurity just like how sterilizing the surgical tools is part of the first steps in any surgery preparation so should cybersecurity be for every healthcare system! Lives are at risk so we should give no room for an attack! Its just a sad situation and hopefully we all can figure out how to at least bring these attacks to the barest minimum.