In Brief
Benjamin Harris, CEO of watchTowrs, successfully manufacture fake HTTP certificates, tracked email activity, and execute code of his choice on thousands of servers for $20. He registered the domain dotmobregistry.net, which was previously the authoritative WHOIS server for .mobi. He observed the domain’s expiration and set up his own .mobi WHOIS server there, allowing him to execute code on thousands of servers. (1)
What is WHOIS and why WHOIS database was created?
WHOISis a public database that stores all information related to domain name registration and DNS configuration updates. The WHOIS database is regulated by. ICANN, or the International Corporation for Assigned Names and Numbers. It ensures that websites are properly registered in order to keep them safe. (2)
The WHOIS database stores information in multiple locations, which are administered by various domain registrars. Each domain registrar and registry are in charge of handling certain top-level domains like .com and .net, ensuring that all details are correct and up to date. (2)
First, the database was designed as a directory, collecting all of the contact information for anyone transmitting data across the ARPANET, a precursor to today’s Internet, and the WHOIS lockup was created to promote transparency in domain registration by ensuring that every domain name has identifying, information, making it easy to check the registrant and identify the website owner. The WHOIS lookup can be used by anyone online and it can help business owners monitor domain availability, investigate potential infringements, and make data-driven decisions. (2)
The WHOIS database contains important information about a domain, including but not limited to:
- Registrant Name – the person or entity that owns the domain
- Registrant Contact Information – when domain was registered
- Domain Expiration Date – when registration expires
- Nameservers – the DNS information that direct traffic to the right web hosting service
Some registrants utilize services that disguise their information in the WHOIS lookup to protect their privacy. (2)
The Uncertainty
His server received from over 76,000 unique IP addresses in hours and 2.5 million inquiries in five days from 135, 000 different systems, including domain registrars, online security providers, governments, academic institutions, and certificate authorities. According to the research, governments and authorities around the world have misplaced trust in the process. The business argues that well-resourced nation-states will find defects in this critical process since they are continuously hunting for gaps. (1)
Harris removed real.mobi address from his WHOIS database, concentrating on administrative emails address and watchtower.com domains, and added ASCII art for levity, which appears as this:

WHOIS information for google.mobi as shown by a rogue server at whois.dotmobiregistry.net Credit: watchTowr
However, the rogue WHOIS server provided Harris enormous access, including the ability to dictate the email address certificate authority that GlobalSign uses to identify domain ownership. Harris received an email from GlobalSign with a verification link for a certificate signing request for Microsoft.mobi. He then called off the project due to ethical concerns.
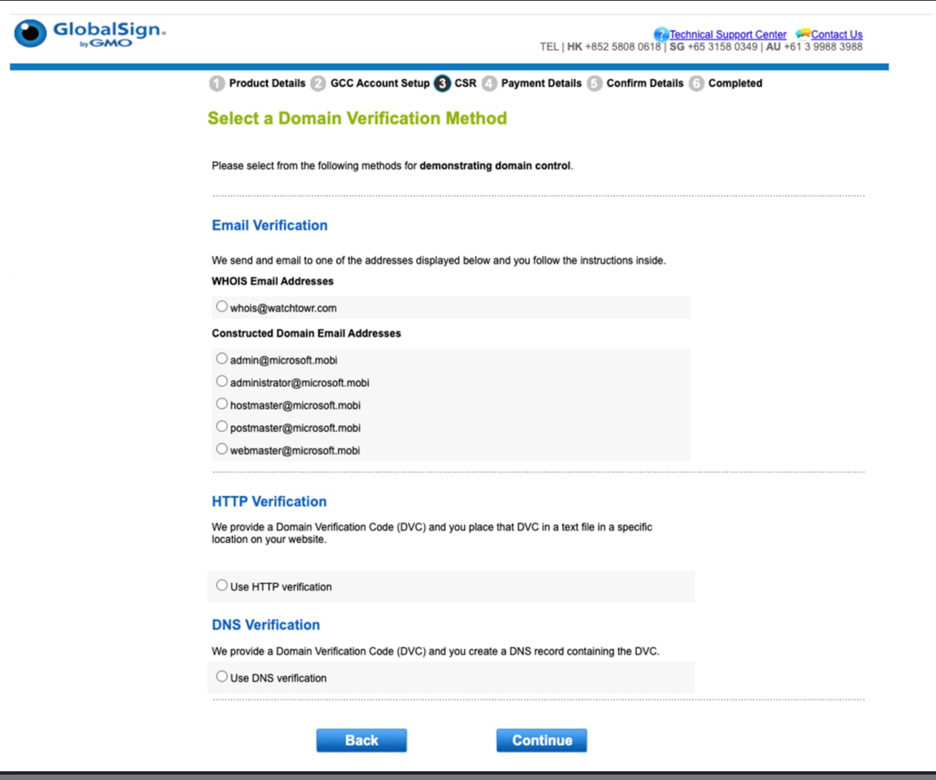
An email Harris received from GlobalSign after generating a certificate signing request for microsoft.mobi. Credit: watchTowr
Therefore, the ability to issue a TLS/SSL certificate for a.mobi domain enables a variety of criminal operations, such as traffic interception and spoofing the target server, rendering threat models outdated. (1)
Other WHOIS server Exploit
The rogue WHOIS server can be used for a variety of malicious objectives, including getting forged certificates, tracing emails chains, and exploiting weaknesses in WHOIS clients and security services. This enables him to passively infer communication partners and exploit vulnerabilities that are usually only available to trusted WHOIS servers. As a result, the rogue server has been investigated by a number of third-party sites and services, including Google’s VirusTotal, URLScan, domain registrars, and WHOIS websites. WatchTowr collaborated with the National Counterintelligence and Secuirty Centre and ShadowServer to protect the dotmobiregistry.net domain. (1)
Conclusion
It is quite concerning that $20 domain purchase has exposed vulnerabilities in communication and subversion of the Certificate Authority verification system, highlighting the need for improved trust and security process for internet users.
Unfortunately, this will become increasingly common as the internet’s foundation is being neglected, leading to increased vulnerability in critical systems like financial institutions, universities, hospitals, and government websites.
References:
[1] Rogue WHOIS server gives researcher superpowers no one should ever have. (11.Sep.2024). Retrieved from https://arstechnica.com/security/2024/09/rogue-whois-server-gives-researcher-superpowers-no-one-should-ever-have/
]2] What is WHOIS and How to Look Up a Domain? (n.d). Retrieved from https://www.domain.com/ca/en/blog/what-is-whois-and-how-is-it-used/


This post is very insightful. It is a pity that innocent ones are exploited unaware for a cheap price of $20. This is just proof that the internet is a vast community and a new approach exploiting organizations and individuals to keep surfacing based on how deep the hackers explore the internet space. Cybersecurity awareness has to spread like wildfire to migrate an increase in cybercrimes.
I can’t believe a $20 domain could expose such huge vulnerabilities in the WHOIS system. It’s alarming that Harris could access sensitive data and mess with certificate authorities like that. It really makes you think about how much we can trust these systems to protect our information. Thanks for sharing this important insight, John!
I am feeling overwhelmed. Ankita, trust in our Certificate Authority and branded resellers is critical. By prioritizing the security and trustworthiness of our digital certificates and identity validation procedures, we can assure the security and integrity of the certificate issuance process, secure user data, and maintain our end-users’ trust.
I feel that these types of vulnerabilities will become more common as time goes on. Like here where a trusted and well used domain expired and they can be easily bought and put to nefarious use. Gladly in this instance a security researcher noticed and didn’t use it for ill use. But what about next time or the other base systems that as time goes on get more and more neglected. Seeing vulnerabilities like this and learning how the PKI works make me a lot less confident in the internet’s security. As it takes just one vulnerability or one CA to issue a bad certificate and boom the whole internet trusts that certificate and website. Hopefully as time goes on we can put in better regulations and monitoring so simply expires don’t create vulnerabilities in the future.
I feel that these types of vulnerabilities will become more common as time goes on. Like here where a trusted and well used domain expired and they can be easily bought and put to nefarious use. Gladly in this instance a security researcher noticed and didn’t use it for ill use. But what about next time or the other base systems that as time goes on get more and more neglected. Seeing vulnerabilities like this and learning how the PKI works make me a lot less confident in the internet’s security. As it takes just one vulnerability or one CA to issue a bad certificate and boom the whole internet trusts that certificate and website. Hopefully as time goes on we can put in better regulations and monitoring so simply expires don’t create vulnerabilities in the future.
Insightful post, John! This is an important post to learn more about the Domain Name System (DNS), certificate authority key providers, and the corresponding security protocols and technologies. Generally, DNS-related communications, such as registrations and IP address-to-hostname mappings, are not monitored from a security perspective. This lack of security monitoring can pose a significant threat to overall network security and the privacy of domains and their functionalities. This study shows that a $20 domain experiment can expose vulnerabilities in the WHOIS database. This research significantly enhances our understanding of DNS and related key providers, contributing to improved security. Hopefully, relevant authorities will take this into account and strengthen overall security measures to prioritize information security and privacy.
Insightful post, John!
This incident reveals a serious vulnerability in the WHOIS system. A $20 domain purchase enabled Harris to create a rogue WHOIS server. The fact that his rogue server attracted millions of inquiries from reputable organizations highlights a dangerous level of vulnerability. This event underscores the necessity for improved verification methods and illustrates how inadequate supervision can result in significant security issues across various sectors, including finance and government. As we increasingly rely on digital infrastructures, we need to rethink how we protect our online security. It’s important to make sure basic systems, like WHOIS, are strong and safe from being misused.
Good work, John! Harris’ exploit of the WHOIS system is like an instruction manual on how easily we can abuse our digital trust frameworks. Effective work to enhance security protocol in Certificate Authorities and WHOIS databases is necessary to prevent similar incidents in the future.
Nice post John! I was impressed on how such an important resource as a WHOIS server is actually providing such information. Now that there is an exploit on this kind of server they will be targeted more widely. As you mentioned, neglect and lack of security measures makes life easier for hackers and makes others be at risk. These are important servers and stealing valid credentials is something to consider seriously. Thanks for the info!
I am grateful for your comment. Oscar, hackers typically use vulnerabilities to gain unauthorized access and wreak greater damage. It’s a never-ending race between those defending and those trying to exploit system weaknesses. To properly manage these threats, we must be attentive and proactive in protecting our digital future.
Great and informative post, John. I recall one of the domain validation methods is sending an email to the domain administrator, which is recorded in the WHOIS database. This vulnerability could have been very impactful if exploited by harmful attackers. Additionally, the vulnerability spotted light on the need for an authentication process to ensure who is the trusted source of truth responding to WHOIS queries. WHOIS is a query sent over TCP (ICANN. 2023, November 2)[1], according to ICANN (RFC 3912): “WHOIS lacks mechanisms for access control, integrity, and confidentiality, WHOIS-based services should only be used for information which is non-sensitive and intended to be accessible to everyone.”. (IETF Datatracker .n.d.)[2]. Finally, Harris was able to successfully manufacture fake HTTP certificates. This raises the importance of the Extended Validation Certificate (EV) where the certificates should not be issued to WatchTowers without Organization Validation (OV), especially for critical services like WHOIS.
I am inspired by this post John and I just realized an amazing startup business idea from this story that I may present it to UoC Hunter Hub. Thanks for sharing again.
[1] WHOIS and Registration Data Directory Services – ICANN. (2023, November 2). https://www.icann.org/resources/pages/whois-rdds-2023-11-02-en.
[2] RFC 3912: WHOIS Protocol Specification. (n.d.). IETF Datatracker. https://datatracker.ietf.org/doc/html/rfc3912.
Hi John, I found your discussion post incredibly engaging and thoroughly enjoyed reading it from start to finish. Firstly the introduction of watchTowr CEO Benjamin Harris was exciting. Following his exploitation of an expired domain that, in turn, situated him so that he would be able to manipulate certificates, track emails, and utilize code through many servers was unbelievable. Following this, the issues with WHOIS that were presented raised a very different approach, created as a directory for ARPANET, it was able to maintain and provide domain ownership details and configuration abilities. However, after Harris’s separate WHOSIS severe, which collected 2.5 million queries over five days, it became apparent that foul play at work. Due to the issues that occurred, we can see the importance of certificates and maintaining securities so that traditional threat models are not bypassed. Harris has shown us the vulnerabilities in internet trust systems, which can be exploited relatively cheaply.