Can you imagine a situation where your data has been kidnaped by someone else? This is a very inconvenient position that a ransomware can bring to your computer or a whole company. Let’s analyze a new ransomware trend that seems to be very effective in multiple industries.
What is ransomware?
Let’s start by explaining what ransomware is. The CISA (Cybersecurity and Infrastructure Security Agency), a US agency dedicated to cybersecurity, explains that ransomware is a type of malware designed to encrypt files on a device with the main purpose of making them unusable. Then the perpetrators will demand a ransom in exchange for decryption[1].
This threat can have devastating effects on an organization if they do not take steps to protect it or pay the requested amount to recover the infected devices.
What is this Cicada3301 malware?
The name comes from an online puzzle posted between 2012 and 2014 that apparently wanted to recruit people that are really skilled in problem solving.
This ransomware written in Rust has a very wide attack range. It can attack Linux and Windows distributions. It will shut down virtual machines, terminate processes and services, and delete shadow copies inhibiting system recovery. Beside this, it is capable of encrypting network shares for maximum impact. It uses the ChaCha20 + RSA encryption to fully or partially encrypt files [2].
It will show the next image after the system is infected and the steps to recover the control on the system files:
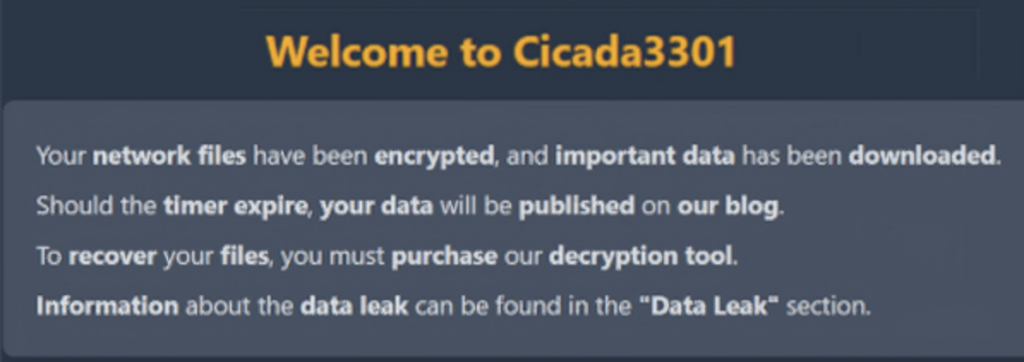
System infected with Cicada3301[3]
One thing that puts more pressure over affected users is the menace of publishing confidential files in public forums, social media or customers, partners, and competitors. If you don’t pay before the deadline the data will be released, making backups less effective to protect against this threat.
This new threat has already affected over 30 victims since June 2024. Normally ransomware works along other malware programs to gain system access and deliver the payload. So the team behind this malware recruits pen testers and access brokers to work along this program to perform an attack, giving up to 20% commission for the job done [4].
What can we do?
The awareness of new threats like this is an important step for any cybersecurity expert that wants to protect a system. The CISA has a guide with specific steps that helps prevent and how to respond to this kind of attacks [5]. It is important to keep these guidelines to avoid or reduce the impact of this attack. Some basic tips are also shared:
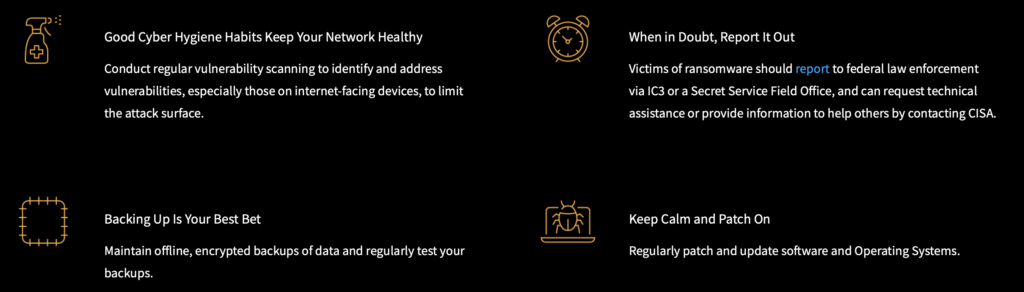
Basic good practices to protect against ransomware [1].
Although backups seemed to be the best bet for this attack, new ransomware can also pressure victims by releasing information, that is why encryption of sensitive files and reducing the attack surface. We have to keep in mind the catastrophic effects of this attack and take the necessary steps to protect and keep healthy systems.
References:
[1] https://www.cisa.gov/stopransomware
[2] https://thehackernews.com/2024/10/cross-platform-cicada3301-ransomware.html
[3] https://www.tripwire.com/state-of-security/cicada-ransomware-what-you-need-know
[4] https://www.securityweek.com/blackcat-ransomware-successor-cicada3301-emerges/


I’m curious how ransomware can still be effective even with advanced features like Core Isolation in place.
Thanks for bringing up this topic Smruti. I searched about Core Isolation-like features and most of them creates virtualization on the hardware to run processes in an isolated mode, in this way these processes can run without the interaction of malware. In this case it will protect some parts of the data, but it can not guarantee a full protection. It would be good to consider that this new ransomware can disable VMs and terminate processes and services, so depending on the computer configuration it could encrypt the whole system or part of it. The CISA group suggests to prevent the attack with multiple protection layers and not rely on a silver bullet solution. So it would be better to follow the best practices to avoid the full impact of the malware in the organization assets.
I’m curious how ransomware can still be effective even with advanced features like Core Isolation in place.
This article talks about the serious threat from Cicada3301 ransomware, which uses advanced methods to attack both Linux and Windows systems. Its dual strategy of encrypting files and threatening to reveal private information puts more pressure on victims. The hiring of penetration tester and people who help them get into systems shows a worrying pattern in organized cybercrime. As ransomware attacks get more complicated, it’s important to use multiple ways to defend against them. This means combining technology with human vigilance to protect important data and keep operations running smoothly.
Good job, Oscar! Cicada3301 is a shift in ransomware evolution, which means it is time for businesses to adopt several levels of security. It’s a wake-up call to improve backup strategies, as traditional methods may not be sufficient. In addition, businesses need to balance immediate responses to threats with long-term security planning.
Great info on the new malware Cicada3301. I did some additional research in to this malware program. It looks like IBM X-Force, which is the cybersecurity services sector of IBM Consultancy have identified some patterns that potentially ties this back to an existing ransomware group ‘Blackcat’ and ‘Backcat’ supposedly went dark in early 2024 after receiving a huge ransom payment of 22 million dollars in bitcoin for their attack on Change Healthcare. Many Ransomware groups have started to take this route when they hit a huge target, they tend to go offline for a while and resurface with a new name, but they retain the same employees and infiltration tactics.
Nice post Oscar. This post does an excellent job of breaking down ransomware and its serious implications for cybersecurity. The fact that this new ransomware variant is written in Rust, can target both Linux and Windows systems, and disable virtual machines shows how adaptable and dangerous ransomware has become. Defending against ransomware attacks now requires a proactive, multi-layered approach that includes not only regular backups but also data encryption, network segregation and ongoing system monitoring.
Oscar weldone, The post is informative, and I feel the best practice for any cybersecurity expert is to always conduct frequent tests on the backups and patch regularly to avoid attacks or detect threats on the network.
This is one of the emerging Ransomware-as-a-service (RaaS). Cicada3301 offers Ransomware services via a sophisticated attacking panel with many impressive attacking actions which are quite similar to Kali, except the Cicada3301 panel allows attackers for 20% commission making this more of a darknet business (Lakshmanan, 2024)[1]. The challenge as stated above, the attacks are done by completely darknet strangers who just used the the Cicada3301 tools. This makes the data leak is not traceable and hard to litigate. An interesting question would be, should these RaaS services be criminalized? Some intelligence agencies use these tools for crime fighting. Hence, criminalizing these RaaS platforms would not help. It is a never-ending race and a controversial debate.
[1] Lakshmanan.(October 17, 2024). Researchers Uncover Cicada3301 Ransomware Operations and Its Affiliate Program, Retrieve from https://thehackernews.com/2024/10/cross-platform-cicada3301-ransomware.html
Thanks for the comment Tamer! I would like to share some info and my personal opinion in the question you shared. Currently any kind of ransomware is illegal in many countries. In Canada, paying ransom to a listed entity or sanction is a criminal offense. Now, offering or purchasing this malware is also illegal. But, this has obviously not stopped black hat hackers from implementing it. Developing RaaS is just going to the next level!
I agree that it is a never ending fight. Unfortunately there is an increase in the interest in this kind of software by criminal organizations, that is why these platforms are developed. Some governments use this kind of resources to make counter attacks or to specific targets. When should be used or not is indeed a good question. Just like a knife can be used to make delicious food, it can also do harm, this also applies to technology. Thanks for bringing this up!
Great insight Oscar. Thanks for the elaboration.
Very interesting post, Oscar! It is very alarming to see how ransomware like Cicada3301 continues to evolve, especially with its ability to target both Linux and Windows systems and the added threat of public data exposure. Using Rust for cross-platform capabilities shows how ransomware developers are adapting to widen their attack areas, making it more challenging to defend against. Recruitment of access brokers and penetration testers for infiltration is also a concerning new development. As you mentioned, strong preventive measures and awareness are necessary. CISA’s guidelines on handling ransomware, combined with encryption are crucial steps in reducing the impact of such advanced ransomware.
Good post ! The threat of publishing confidential information as a pressure tactic adds a whole new layer of urgency to ransomware attacks, making backups alone insufficient for full protection. For organizations, this means it’s more critical than ever to focus on additional measures like data encryption, strict user access controls, and network segmentation. The basic good practices outlined by CISA—such as regular backups, network segmentation, and security awareness training—are essential steps, but given the sophistication of ransomware like Cicada3301, they might not be enough on their own. Adopting advanced strategies like zero-trust architectures and continuous monitoring for suspicious activity can strengthen defenses, helping organizations stay resilient against increasingly complex threats.
Hi Oscar, your discussion post was incredibly insightful and kept me interested from beginning to end. Great work! One detail I was never fully aware of was that there was a ransomware named Cicada3301, which shared no relation to the online puzzle with the same name. Another factor that shocked me was the ability of the attack to perform on many different operating systems, which enables the ransomware to be pertinent across many devices. Following this, the ability to pressure users who have been attacked into following their instructions because of the ability to release sensitive information is very shocking. The article showcased a multitude of cases where Cicada3301 was able to facilitate its attacks, which means there must be an increase in awareness and preparation that cybersecurity experts must develop. By ensuring proactive measures can be taken to reduce the ransomware threat level, we will be able to maintain data integrity and system health.