In early July 2024, Albertans lined up at gas stations and grocery Co-Op stores. The impact was publicly realized after a formal announcement from by the Federated Co-Operatives Ltd (FCL) on the 27th of June 2024 confirming a security incident on western FLC stores. The cyber-attack widespread knocked out hundreds of Canada’s Co-Op western stores (Hadfield, 2024) [1]. According to a recent report in 2023, published by the Canadian Federal Corporation department, the FLC has about 5,605 stores, employs more than 100,755 people, holding $47.3 billion of assets, and paid more than $2.7 billion in salaries and wages [2] last year. These numbers triggered a lucrative target for cyber-criminals.
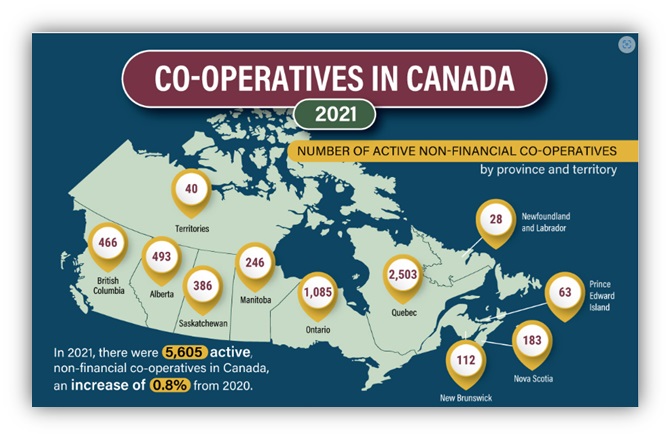
Canada Statistics: Co-operatives in Canada 2021 [3]
The impact
Widespread attack: The reported cybersecurity incident was initially assessed as impact on some internal and customer-facing systems limiting querying the inventory of some grocery items [1]. Unfortunately, the impact was just the first wave of serious damage. On July 1st, the inventory issue was exacerbated causing a disruption in the supply chain and customers started experiencing shortages in products.

CBC News, Cop-cop acknowledged the cyber attack impact (Jul 01, 2024) [4].
FCL acknowledged the impact hit confirming a cyber incident widespread covering from British Colombia (B.C.) to Manitoba nationwide, and disrupting 274 grocery stores, 454 gas bars, and 396 commercial cardlock fuel facilities [4].
Long-planned Attack: According to Terry Cutler, the CEO at Cyology Labs, an ethical hacking cybersecurity company was hired by FCL to assess their retail systems,
“The average time, right now, that a hacker is in your system is 286 days before being detected,”, Terry Cutler [4].
The fact, the attack happened 286 days ahead of realizing the impact publicly, indicates a concerning alert about traditional cyber defense strategies like using firewalls, and anti-viruses which do not always guarantee proper security measures. Security attacks especially those targeting distributed systems need time to saturate and foster the impact. Security experts must use that this time as an advantage to exercise proper cyber defense strategies capitalizing on defense-in-depth and penetration tests.
Data Leak: According to the CTV news on July 10th, FCL released a statement confirming that the hackers threatened to disclose sensitive data stolen from the company. Brad DeLorey, the spokesperson for the Co-op confirmed the cyber attacks involved locking private data, systems, and contents publicly. The incident is classified as a ransomware attack [5].
Financial Damage: Yet, there is no official release from FCL on the financial impact. Nevertheless, the disruption in the retail supply chain operation and the interruption of payment processing systems had a considerable financial impact not only to FCL only, but also to business partners whom were impacted by these delays.
How The Cyber Incident Started?
The Rabbit hole: Yet the root cause of the cyber attack is still not announced officially. Nonetheless, Cutler, CEO at Cyology Labs, commented to CBC News: “Companies should have a playbook to ensure they’re managing cyberattacks without erasing evidence of how they were compromised.”. This raises a question about how FCL were able to keep records and evidence of the attack. It a mandate having these security audit logs available to understand what happened and identify the gaps to ensure future preventive measures.

Federated Co-operatives Facebook Announcement [6]
Current Status:
Recovery Time: According to FCL’s official website, all internal systems and cardlock operations are restored and back online on July 17th [7]. It is impressive how the IT team at FCL was able to restore business operations in just two weeks. Normally, ransomware could take months to recover which indicates the business recovery plan that IT team has to enable business back to operation in a short time. According to an IBM report published in 2022, “It took an average of 277 days, about 9 months, for companies to identify and contain a breach, and that time is of the essence for companies looking to avoid spiralling costs.[8]. Yet the root cause of the cyber attack is still not announced officially. Nonetheless,
So, What Is Missing?
There are notable issues with respect to the FCL cyber attack:
- Absence of holistic security defense-in-depth (DID) strategy. Penetration test (Pen Test) is one of the DID strategies that could realize cyber attacks in the early stages.
- Absence of security audits and playbooks. Recovering from cyber-attacks could be a lengthy process as system and data cleaning up from a ransomware attack could turn into a never-ending loop. Once the recovered system or data are in place, the other infected systems will bring the attack again into a cycle. Hence, Security Information Event Management (SIEM) system and Security Playbook can significantly reduce the cyber recovery time by isolating the attack sources.
- A need for Security Operation Center (SOC) continuous monitoring. SOC plays a crucial role in detecting cyber attacks proactively. A multi-billion organization such as FLC must invest in contracting a reliable SOC or even establishing an internal operation part of the IT and business continuity services.
- Capitalize on “Transparency” to adequate “Communication” to regain customer trust. The effort to recover customers could be more than the effort to recover the systems. Below is an example of how social media can take the incident beyond IT effort.

Federated Co-operative Facebook Announcement [6]. - Large scale organizations with massive consumers are very visible targets for cyber-security attacks, Hence, these organizations must maintain a solid and comprehensive security defense strategy that ensure proactive discovery of security vulnerabilities, and FLC is not an exception. According to Coletto, one to three of Canadian adults is a member of a Co-Operatives [9].
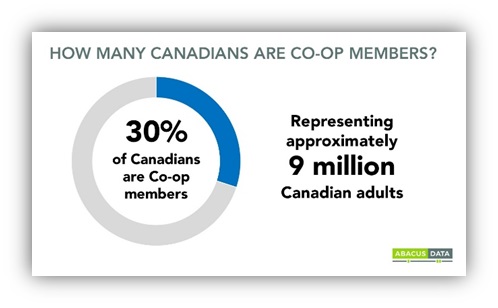
Number of Canadian Adults Member of Co-operatives on 2021, (Coletto, 2020)[9].
Conclusion
The threat of cyber attacks is always a living and looming possibility. Nevertheless, security expertise and a security operation center (SOC) have become necessary for all organizations (Anon ,2022) [10]. Despite the size of the organization size, the leadership needs to assess and recognize a holistic security defense strategy that is adaptive and responsive to ensure security measures can defend the organization against the evolving massive cyber attacks. According to Checkpoint’s Live Cyber Threat Map (https://threatmap.checkpoint.com), on Halloween day 2024, there were 11 million attacks on Oct 30th, 2024.
“SOC prevents, identifies, analyzes, and responds to cybersecurity incidents while continuously monitoring and improving an organization’s security posture” (Basta, A. 2025) [11].
References:
[1] Miles Hadfield. (July 2, 2024). CO-OP News: Cyberattack knocks out systems at Canada’s Federated Co-op stores. Retrieved from: https://www.thenews.coop/cyberattack-knocks-out-systems-at-canadas-federated-co-op-stores
[2] Co-operatives in Canada. (n.d.). retrieved form https://ised-isde.canada.ca/site/cooperatives-canada/en
[3] Canada statistics. (6 November 2023). Co-operatives in Canada 2021, Retrieved from: https://www150.statcan.gc.ca/n1/pub/11-627-m/11-627-m2023065-eng.htm
[4] Dayne Patterson, CBC News. (17 July 2024). Retrieved from: https://www.cbc.ca/news/canada/saskatchewan/federated-co-op-websites-cyberattack-1.7267090
[5] David Prisciak, (10 of July 2024), CTV News: Cyberattack knocks out systems at Canada’s Federated Co-op stores. Retrieved from: https://regina.ctvnews.ca/co-op-investigating-allegations-of-stolen-data-related-to-cyberattack-1.6958445
[6] Federated Co-Operative Facebook announcement, (27 June 2024). https://www.facebook.com/photo/?fbid=770584371912487&set=a.576802894623970
[7] Caitlin Brezinski. (19 July 2024), Co-op operations and systems ‘fully restored’ following cybersecurity incident. Retrieved from: https://regina.ctvnews.ca/co-op-operations-and-systems-fully-restored-following-cybersecurity-incident-1.6970648#:~:text=Federated%20Co-op%20Limited%20(FCL,statement%20on%20X%20on%20Friday.
[8] Amanda Stephenson, (26, June 2023). Suncor Energy cyberattack likely to cost company millions of dollars, expert says. Retrieved from: https://financialpost.com/commodities/energy/oil-gas/suncor-energy-cyber-attack.
[9] David Coletto. (11 March 2020). Co-operatives and Mutuals in the Age of Uncertainty. Retrieved from: https://abacusdata.ca/co-operatives-and-mutuals-in-the-age-of-uncertainty .
[10] Anon (2022) Introduction Of A Security Operation Center Soc [Tender documents: T479608547]. Camden: Disco Digital Media, Inc.
[11] Basta, A. (2025) Open-Source Security Operations Center (SOC): A Complete Guide to Establishing, Managing, and Maintaining a Modern SOC. First edition. Hoboken, New Jersey: John Wiley & Sons, Inc.


Great Post ! The FCL cyber-attack demonstrates the destructive potential of cyber incidents, especially for organizations with large supply chains and customer bases. The rapid spread of disruptions across Co-Op stores and fuel stations highlights the need for strong cybersecurity defenses and quick incident response to prevent widespread consumer impact. FCL’s impressive recovery within two weeks—despite ransomware attacks often taking months to resolve—shows the effectiveness of a well-prepared business continuity and disaster recovery plan. This reinforces the importance of proactive defense strategies to minimize financial and operational losses.
Thank you Krupali for your insights. Can’t agree more, it is essential having disaster recovery plan especially in such large organization where data size can be massive and the recovery time is cumbersome and lengthy process. There are solutions where IT can middle the data vault in an isolated air-gapped storage at the storage array level, this way there is not time switching from the active to passive recovery vault which could be less than an hour. This depends of course on the organization’s ability to invest on such recovery infrastructure, however, the more critical and the size of the data, the more complexity is the disaster recovery plan.
Great post!
This post gives a comprehensive look at the FCL cyberattack, focusing on how it affected operations and data safety. It is a very disturbing fact that the hacker was present in the system for 286 days without being detected. This underscores the advanced nature of today’s threats and also makes it more crucial to focus on proactive defenses like SOCs and penetration testing. This incident is a reminder for other large companies, especially those in critical sectors like food and fuel, to review and improve their cybersecurity measures.
Thank you, Akshar. Your point is correct. The attack’s impact existed for more than nine months without any detection. This was enough time for conducting penetration tests and disaster recovery evaluation. Normally, many organizations test the recovery plan and then discover it is invalid only when the impact happens. It is crucial to establish an active security defense strategy and validate it frequently.
Great topic, Tamer! In many recent cyberattacks worldwide, we see similar issues recurring to some extent. Most companies concentrate hard on their core business goals, neglecting the tech infrastructure needed to operate. While cybersecurity has made certain advancements and awareness of the need for strong, secure IT systems, policies, and standards have increased, there is still a shocking underestimation of the importance of robust, secure IT systems. Making matters worse are loyalty programs offered by those types of businesses, which store sensitive customer information under standard privacy agreements. These programs may also come with hidden risks. Customers may want to reconsider what information they share. At the same time it’s concerning that transparency rarely happens in the majority of attacks.
Much appreciated your insights, Firas. You raised a very good point about policies. It is correct, that keeping the light on is a priority to the business, but also having risk assessment and business continuity plan is not limited to business operation only. As you highlighted, IT operation and security risk analysis are indeed part of the business policy and mandatory processes.
Hackers are targeting companies with large financial backgrounds. Besides, the companies with a large scale of end users are more vulnerable. In most cases, bad people choose regular end users to enter the system. It is very concerning that a big association like Co-op is also facing cyber attacks, and they have failed to identify the attack in a short time. From my opinion, these types of companies should have an extra layer of security like an SOC, or security operation center, which is mentioned in the post. From my previous experience, I have seen that this 24-hour active team plays a very important role in security. Again, the institute should share everything about the cyber attacks they are facing instead of hiding it, which will be helpful for other companies to take preventive measures.
Great job, The FCL cyberattack actually shows that more frequent and vulnerability test should always be carried out as a great cybersecurity measures because it underscores the growing risks of cyber threats, particularly for large organizations with significant consumer bases. It emphasizes the need for a holistic and adaptive cybersecurity strategy that includes proactive defense measures, continuous monitoring, and effective recovery protocols to address evolving cyber threats. The importance of transparency in communicating with customers during a breach is also highlighted as critical for maintaining public trust.