Summary of attacks
On August 24, 2024, a ransomware attack led by the Rhysida ransomware organization took over the port of Seattle. This attack severely affected critical systems at Seattle-Tacoma International Airport, including facilities, check-in areas, ticketing, Wi-Fi, passenger transport identifies exhibits in conjunction with critical disruptive services: port website, TSA wait time information, SEA Visitor Pass system , subscription app. While many of these systems were rebuilt within a week, work is underway to restore all services.[2][3]

Fig 1[3]
Who Is Rhysida?
Released in May 2023, Rhysida Is a modern yet powerful ransomware-as-a-service (RaaS) team. Rhysidas is known for its incredible expansion, focusing primarily on government agencies, corporations and medical systems. Notable historical attacks by Racida included interceptions at the British Library, the Chilean National Army (Ejército de Chile), and the Columbus, Ohio FBI and Cybersecurity Services Security Agency (CISA) and the US. The Department of Health and Human Services (HHS) warned of Rhysida’s broad and widespread attacks and opportunities. Rhysida uses data smugglers to harass; If the ransom call fails, he threatens to reveal secrets on the dark web.[5]
fig 2
Refusing to Pay the Ransom
Rhysida Continued to offer money to pay to keep the thieves out, but the Port of Seattle refused. Executive Director Steve Metrack stressed that paying the ransom would contradict the port’s intent and responsibility to use public funds wisely. Instead, the port isolated the delicate system.
A Wake-Up Call for Public Infrastructure Security
This Port of Seattle proposal highlights the wide variety of ransomware incidents and their significant impact on critical public infrastructure. The increasing number of cases involving Rhysida , with numerous crook networks and widespread organizational involvement, highlights the need for robust cybersecurity measures, especially in public transport and healthcare. Security measures, which can be weakened, are becoming increasingly important as ransomware enterprises become large. Invade call places.
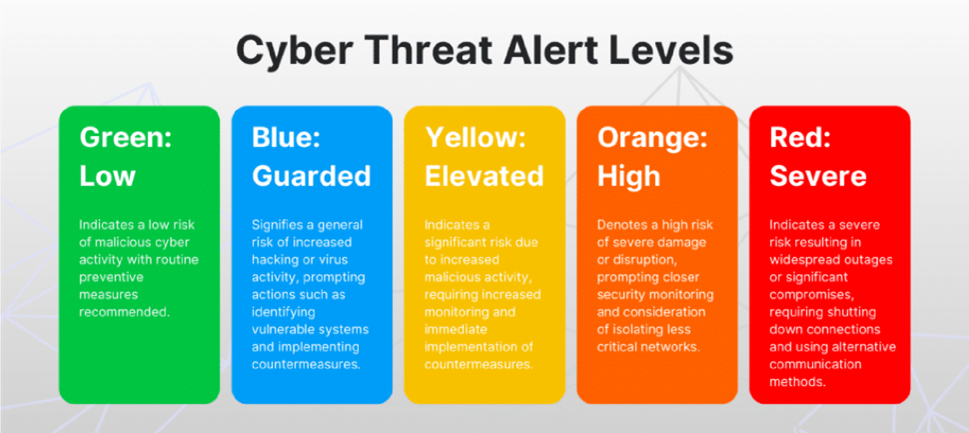
[Cybersecurity Alert System in Action]
For more information on Threat levels :
https://www.cisecurity.org/cybersecurity-threats/alert-level
Strengthening Cyber Security Protocols
Port of Seattle’s funding rejection highlights a desire to prevent ransomware attacks through resistance and treatment rather than supporting criminal games. With an emphasis on security and partnerships with other agencies, the port seeks to expand ransomware capabilities if the coping model is internalized for public coverage, putting safety measures in many places.
Conclusion
A landmark event in the global war on ransomware, the Port of Seattle breach highlights how public institutions can respond to undoubtedly damaging cyberattacks. The port’s response highlights the need for cybersecurity preparedness and resilience and the continued struggle with ransom payments. As enterprises deal with the context, the port approach introduces critical data analysis to restore and protect against cybercrime legal guidelines.
[3] https://www.porttechnology.org/news/port-of-seattle-shares-details-of-a-cyberattack/
[4]https://cyberscoop.com/ransomware-group-releases-screenshots-in-attempted-extortion-of-port-of-seattle/
[5] Rhysida, the new ransomware gang behind British Library cyber-attack
https://www.theguardian.com/technology/2023/nov/24/rhysida-the-new-ransomware-gang-behind-british-library-cyber-attack

Very Informative Post! Threats to ports are increasing and having a substantial impact on essential infrastructure. Rhysida ransomware attacks are carried out in a variety of ways, with the primary motive being profit, therefore organizations such as ports and airports are high-value targets that cannot afford interruptions. Sensitive information can be sold on the dark web for a significant price.
As part of the Port of Seattle’s intention to prevent ransomware attacks by resistance and treatment rather than enabling criminal games, employees should be informed on the hazards of ransomware, as well as how to identify and avoid phishing emails, malware attachments, and other threats. To avoid future attacks, devices, controllers, and other technologies used in port operations must be more secure.
The cyberattack on the Port of Seattle shows how advanced and dangerous ransomware groups like Rhysida have become, especially when targeting important public services. The incident underscores the difficult choices organizations face regarding ransom payments, highlighting the balance between immediate recovery and long-term security implications. With important services affected, the attack highlights the urgent need for strong cybersecurity tools and plans to handle problems quickly. The Port’s choice not to pay the ransom is an important example of standing up against cybercriminals.
The attack on the port of Seattle serves as a wake up call about the vulnerabilities in public infrastructure and the need for stronger cybersecurity measures. The importance of investing in layered security defenses, regular updates and the collaboration with security experts.
Very interesting post, Cynthia! This ransomware attack reminds us how vulnerable public infrastructure can be to sophisticated cyber threats like those from Rhysida. It is assuring to see that the port decided not to pay the ransom, further highlighting the urgency for the public and private sectors to reinforce cybersecurity defenses, especially given how quickly they are growing in scale and impact. This approach is a step in the right direction for sure!
Thank you, Krupali, for bringing attention to this attack on the Port of Seattle. This cyber-attack against Seattle airport networks just highlights how crucial cybersecurity is for public infrastructure. Rhysida’s brutal strategy reflects the grave threat to our transport systems and other vital services. The Port of Seattle deserves credit for a stand-in on their refusal to pay, a gamble that reaffirms how much we should build cyber defenses instead of succumbing to ransom requests. Port of Seattle’s refusal to pay the ransom is a strong position, but I imagine there were many hard choices with TSA data and Wi-Fi affected. Hopefully, their journey of recovery will help to remind us of the need for safer, stronger infrastructure in government offices all over the world. Ideally, other agencies are ready to emulate this!